SM2是国家密码管理局于2010年12月17日发布的椭圆曲线公钥密码算法,在我们国家商用密码体系中被用来替换RSA算法。
国产SM2算法,是基于ECC的,但二者在签名验签、加密解密过程中或许有些许区别。
普通的软密钥,在签名验签、加密解密时,使用的0009规范;
如果是硬密钥,例如密码钥匙是0016规范(SKF),密码设备是0018规范(SDF);
SM2基于椭圆曲线,公钥是曲线上的一点(x,y),即公钥由x和y分量组成
SM2
推荐的椭圆曲线、参数
椭圆曲线方程:y2 = x3 + ax + b
p= FFFFFFFE FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF 00000000 FFFFFFFF FFFFFFFF
a= FFFFFFFE FFFFFFFF FFFFFFFF FFFFFFFF FFFFFFFF 00000000 FFFFFFFF FFFFFFFC
b= 28E9FA9E 9D9F5E34 4D5A9E4B CF6509A7 F39789F5 15AB8F92 DDBCBD41 4D940E93
n= FFFFFFFE FFFFFFFF FFFFFFFF FFFFFFFF 7203DF6B 21C6052B 53BBF409 39D54123
Gx= 32C4AE2C 1F198119 5F990446 6A39C994 8FE30BBF F2660BE1 715A4589 334C74C7
Gy= BC3736A2 F4F6779C 59BDCEE3 6B692153 D0A9877C C62A4740 02DF32E5 2139F0A0
测试数据:
private_key_str:
16c96638efcde957f612ed51b743512ce28d2b87b0b8263c3a7113e8d8ff7030
public_key_bytes:
afdd188ac76ba7fa13f64744f7901501a39f92eb22ca38ce21940061b29a316efbdcb9b2cda6126976f8dda063023014f21b9b50c346b498e8de23e82d2c3501
public_key_x_bytes:
afdd188ac76ba7fa13f64744f7901501a39f92eb22ca38ce21940061b29a316e
public_key_y_bytes:
fbdcb9b2cda6126976f8dda063023014f21b9b50c346b498e8de23e82d2c3501
ID:
b’ALICE123@YAHOO.COM’
ENTL:
b’\x00\x90’
a_str:
fffffffeffffffffffffffffffffffffffffffff00000000fffffffffffffffc
b_str:
28e9fa9e9d9f5e344d5a9e4bcf6509a7f39789f515ab8f92ddbcbd414d940e93
p_str:
fffffffeffffffffffffffffffffffffffffffff00000000ffffffffffffffff
n_str:
fffffffeffffffffffffffffffffffff7203df6b21c6052b53bbf40939d54123
g_x_str:
32c4ae2c1f1981195f9904466a39c9948fe30bbff2660be1715a4589334c74c7
g_y_str:
bc3736a2f4f6779c59bdcee36b692153d0a9877cc62a474002df32e52139f0a0
在进行hash运算前需要组成以下格式:
ENTL + ID + a + b + x_g + y_g + x_a + y_a:
0090414c494345313233405941484f4f2e434f4dfffffffeffffffffffffffffffffffffffffffff00000000fffffffffffffffc28e9fa9e9d9f5e344d5a9e4bcf6509a7f39789f515ab8f92ddbcbd414d940e9332c4ae2c1f1981195f9904466a39c9948fe30bbff2660be1715a4589334c74c7bc3736a2f4f6779c59bdcee36b692153d0a9877cc62a474002df32e52139f0a0afdd188ac76ba7fa13f64744f7901501a39f92eb22ca38ce21940061b29a316efbdcb9b2cda6126976f8dda063023014f21b9b50c346b498e8de23e82d2c3501
经过hash运算后的结果:
digst_ZA_str:
82b1d4908140c211320b552dc9daaec5325413fc2b3a96bcd94a2be4d447ab37
对原数据进行签名:
SM2签名结果 r||s
长度应该是(r:32字节)+(s:32字节)64字节,就算加个04头字节,也是65个字节。
r:随机数
s:签名值
digst_M_str:
07c1bb190619fad10d8fe0e4bfcda1ba43519a0d2239ad14fe0ca14caf95cab9
s_sign_r: 3bcebff61314d7337b85184bb332c1ecef5d2cde82e14f85a80ccd20b7cf22e5
s_sign_s: d1cedd5f3897a372cb486f87019cbb3d4a773d561bc19f2c5be9d1e832ce2dae


网上测试工具:(测试是可以的)
SM2加解密
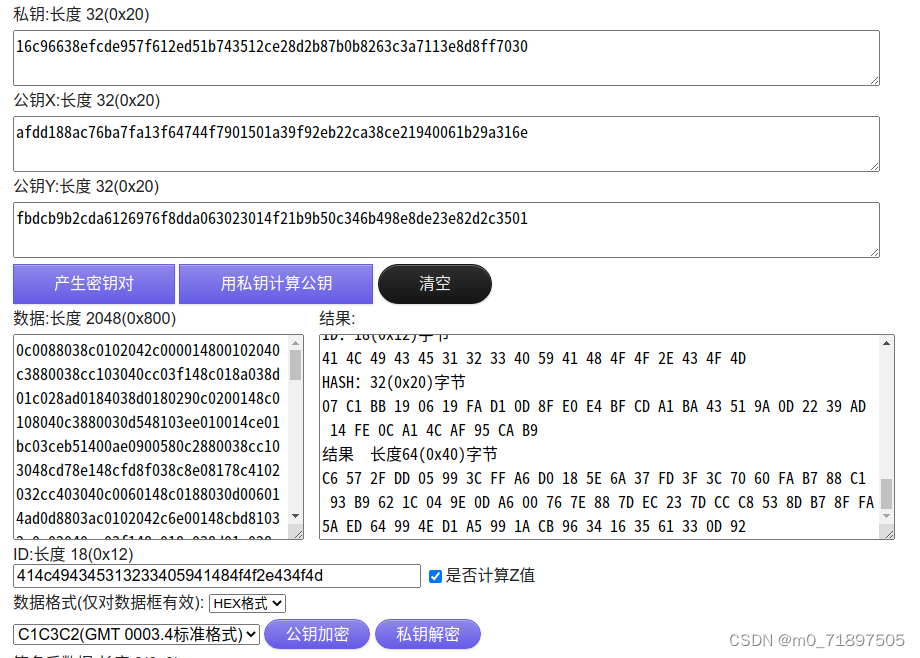
私钥
16c96638efcde957f612ed51b743512ce28d2b87b0b8263c3a7113e8d8ff7030
公钥x:
afdd188ac76ba7fa13f64744f7901501a39f92eb22ca38ce21940061b29a316e
公钥y:
fbdcb9b2cda6126976f8dda063023014f21b9b50c346b498e8de23e82d2c3501
ID:414c494345313233405941484f4f2e434f4d
私钥签名
算法: SM2私钥签名
数据 长度2048(0x800)字节
0C 00 88 03 8C 01 02 04 2C 00 00 14 80 01 02 04 0C 38 80 03 8C C1 03 04 0C C0 3F 14 8C 01 8A 03 8D 01 C0 28 AD 01 84 03 8D 01 80 29 0C 02 00 14 8C 01 08 04 0C 38 80 03 0D 54 81 03 EE 01 00 14 CE 01 BC 03 CE B5 14 00 AE 09 00 58 0C 28 80 03 8C C1 03 04 8C D7 8E 14 8C FD 8F 03 8C 8E 08 17 8C 41 02 03 2C C4 03 04 0C 00 60 14 8C 01 88 03 0D 00 60 14 AD 0D 88 03 AC 01 02 04 2C 6E 00 14 8C BD 81 03 2C 0C 02 04 0C C0 3F 14 8C 01 8A 03 8D 01 C0 28 AD 0D 87 03 8D 01 C0 29 0C 04 80 03 8C 01 20 03 2C 00 06 04 0C 44 80 03 8C 01 24 03 2C 04 06 04 0C 80 00 04 8D 1D 40 03 0E E0 BF 02 CE FD 47 03 CE B1 14 00 C0 1D 01 44 05 00 15 00 AD 14 01 5C A5 88 40 00 0D 3C 80 03 A5 15 17 00 04 C0 3F 14 84 40 87 03 85 00 80 29 0F 02 00 14 8D BC 10 00 A0 01 80 29 11 04 80 03 10 04 80 03 11 1A 00 58 0E B2 41 00 8E 38 15 00 C0 01 80 29 10 06 C0 02 11 F2 FF 63 04 C0 3F 14 84 00 94 03 84 00 20 03 85 30 80 28 06 80 80 03 A5 18 15 00 A5 98 15 00 85 20 80 29 85 00 80 28 A5 18 15 00 A5 98 15 00 85 00 80 29 85 10 80 28 A5 18 15 00 A5 98 15 00 85 10 80 29 0C C0 3F 14 8C 01 94 03 8C 01 20 03 8D 31 80 28 0E 40 81 03 AD 39 15 00 8D 21 80 29 8D 01 80 28 AD 39 15 00 AD B9 15 00 8D 01 80 29 8D 11 80 28 AD 39 15 00 AD B9 15 00 8D 11 80 29 04 C0 3F 14 84 00 94 03 84 00 20 03 85 30 80 28 46 00 00 14 A5 18 15 00 A5 98 15 00 85 20 80 29 85 00 80 28 A5 18 15 00 A5 98 15 00 85 00 80 29 85 10 80 28 A5 18 15 00 A5 98 15 00 85 10 80 29 0C C0 3F 14 8C C1 87 03 0D 9C 80 03 8D 11 00 29 0C 0E 00 14 80 11 00 04 2C 00 38 14 2C 30 00 04 2C 00 38 14 2C 20 02 04 0C 10 80 03 80 01 00 04 03 06 00 1C 63 30 C0 28 02 06 00 1C 42 50 FF 28 0D 00 24 03 00 04 00 54 2C 30 C0 02 AC 31 15 00 80 01 00 4C 0C C0 82 03 2C 00 00 04 17 06 00 1C F7 E2 C0 28 04 00 38 14 84 00 20 03 F7 92 11 00 04 FE FF 15 04 00 00 16 F7 92 14 00 03 06 00 1C 63 00 FF 28 02 06 00 1C 42 20 FE 28 0C 80 00 04 8C FD 47 03 8D 0D 40 03 8E F1 47 03 CE 35 10 00 0D 04 80 03 AD B9 18 00 EF 01 00 14 EF 01 BC 03 EF B5 14 00 E0 11 00 44 0E 00 15 00 8E 0D 15 5C 00 0C 00 50 00 80 48 06 FF FF FF 53 04 C0 3F 14 84 80 87 03 84 00 20 03 00 74 18 54 04 06 00 1C 84 C0 F5 28 00 C0 18 54 04 06 00 1C 84 B0 F5 28 00 B4 18 54 0C C0 3F 14 8C 01 20 03 8E 01 D0 28 4D 00 00 14 CE 35 15 00 8E 01 D0 29 00 04 0F 54 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 0C C0 3F 14 8C 01 20 03 8D 01 86 28 0E BC B7 02 AD B9 14 00 0F 80 90 03 AD 3D 15 00 8D 01 86 29 00 00 72 38 0C C0 3F 14 8C 01 90 03 8C 01 20 03 8D 11 80 28 0E 00 82 03 AD B9 16 00 8D 11 80 29 00 00 72 38 0C E0 1F 14 0C 80 00 16 8C 01 20 03 2D 00 00 14 AD 21 8C 03 8D 35 0C 38 0E FC 83 03 AD 39 15 00 2E 00 00 14 CE 21 8C 03 8D 39 1C 38 00 00 72 38 0C E0 1F 14 0C A0 00 16 8C 01 20 03 2D 00 00 14 AD 21 8C 03 8D 35 0C 38 0E FC 83 03 AD 39 15 00 2E 00 00 14 CE 21 8C 03 8D 39 1C 38 00 00 72 38 8C 00 00 14 8C FD BF 02 9F FD FF 47 0C 1A 20 14 0C C0 01 16 8C 01 20 03 8D B1 80 28 EF 01 00 14 EF 01 B4 03 AD 3D 15 00 8D B1 80 29 8D A1 80 28 EF 01 00 14 EF FD BF 03 8F A1 80 29 8D 31 80 28 EF 01 00 14 EF FD BF 03 8F 31 80 29 8D 11 80 28 0F 00 82 03 AD 3D 15 00 8D 11 80 29 8D 11 80 28 4F 00 00 14 EF 01 A0 03 AD 3D 15 00 CF 01 00 14 EF FD BF 03 AD BD 14 00 8D 11 80 29 04 4C 81 03 00 34 15 54 04 CC 80 03 00 2C 15 54 6F 00 00 14 EF 01 90 03 8F 51 80 29 0C 08 00 14 8C FD BF 02 9F FD FF 47 00 00 00 50 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
ID:18(0x12)字节
41 4C 49 43 45 31 32 33 40 59 41 48 4F 4F 2E 43 4F 4D
HASH:32(0x20)字节
07 C1 BB 19 06 19 FA D1 0D 8F E0 E4 BF CD A1 BA 43 51 9A 0D 22 39 AD 14 FE 0C A1 4C AF 95 CA B9
结果 长度64(0x40)字节
97 4F A8 A7 A0 DE 7A EF 7F 52 97 FF A3 D4 68 BE 32 B8 BC 1F 9A E3 5B 6A DA 27 C9 8A 64 4E 1F A5 3C 2B 78 45 DB DE 1E 9C 96 17 E9 88 2B C7 95 9A BE 11 25 11 AD 02 BB 20 EB D6 7E D3 9B 03 E9 3E





















 332
332











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








