一、关于 Nessus 扫描工具
Nessus —系统漏洞扫描与分析软件!
Nessus 是全世界最多人使用的系统漏洞扫描与分析软件,总共有超过75,000个机构使用Nessus 作为扫描该机构电脑系统的软件。
Nessus对个人用户是免费的,只需要在官方网站上填邮箱,立马就能收到注册号了,对应商业用户是收费的。



二、扫描漏洞报错信息
源网页漏洞内容:
Vulnerabilities
51192 - SSL Certificate Cannot Be Trusted
-
Synopsis
The SSL certificate for this service cannot be trusted.
Description
The server's X.509 certificate cannot be trusted. This situation can occur in three different ways, in which the chain of trust can be broken, as stated below :
- First, the top of the certificate chain sent by the server might not be descended from a known public certificate authority. This can occur either when the top of the chain is an unrecognized, self-signed certificate, or when intermediate certificates are missing that would connect the top of the certificate chain to a known public certificate authority.
- Second, the certificate chain may contain a certificate that is not valid at the time of the scan. This can occur either when the scan occurs before one of the certificate's 'notBefore' dates, or after one of the certificate's 'notAfter' dates.
- Third, the certificate chain may contain a signature that either didn't match the certificate's information or could not be verified. Bad signatures can be fixed by getting the certificate with the bad signature to be re-signed by its issuer. Signatures that could not be verified are the result of the certificate's issuer using a signing algorithm that Nessus either does not support or does not recognize.
If the remote host is a public host in production, any break in the chain makes it more difficult for users to verify the authenticity and identity of the web server. This could make it easier to carry out man-in-the-middle attacks against the remote host.
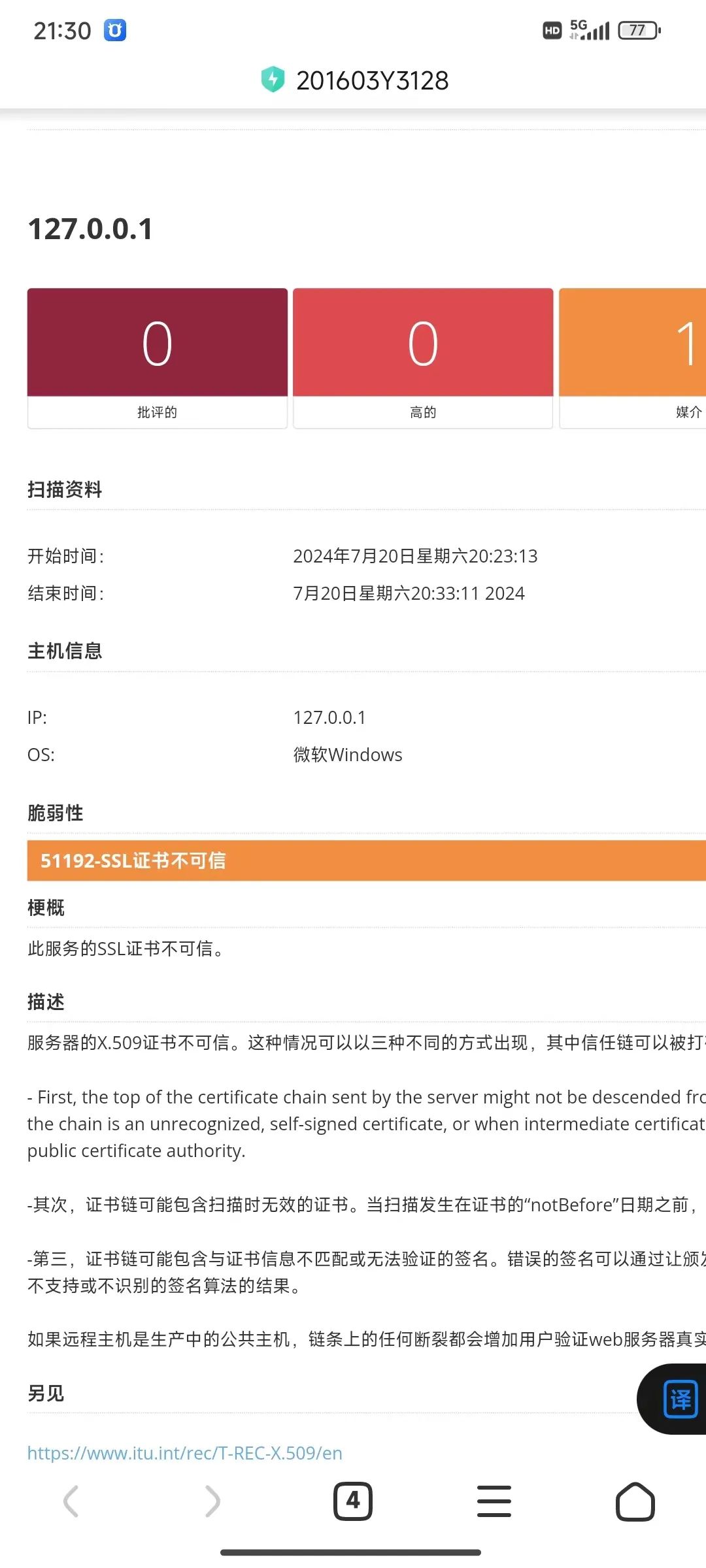
漏洞翻译后提示如下:
主机信息
IP:
127.0.0.1
OS:
微软Windows
脆弱性
51192-SSL证书不可信
梗概
此服务的SSL证书不可信。
描述
服务器的X.509证书不可信。这种情况可以以三种不同的方式出现,其中信任链可以被打
- First, the top of the certificate chain sent by the server might not be descended frc
the chain is an unrecognized, self-signed certificate, or when intermediate certificat
public certificate authority.
-其次,证书链可能包含扫描时无效的证书。当扫描发生在证书的"notBefore"日期之前,
-第三,证书链可能包含与证书信息不匹配或无法验证的签名。错误的签名可以通过让颁发
不支持或不识别的签名算法的结果。
如果远程主机是生产中的公共主机,链条上的任何断裂都会增加用户验证web服务器真实
三、漏洞修复解决方案
通过查阅资料并尝试测试,找到如下临时解决方案,生成CA证书文件,并设置为自定义CA证书文件!
方法如下,仅供参考:
1.用管理员身份运行命令程序 nessuscli.exe
nessuscli.exe 命令位于目录路径:C:\Program Files\Tenable\Nessus\
2.敲入命令生成证书
C:\Program Files\Tenable\Nessus\nessuscli.exe mkcert
生成后的证书文件位于 CA 文件夹,共有4个证书文件!
3.设置自定义CA证书文件
打开软件 setting 设置选项,将生成的 CA 文件夹中的第一个证书文件,打开,复制粘贴进 CustomCA


Nessus 扫描工具扫描后无该项漏洞风险提示,但http访问还是风险!
参考来源:
1.How To Resolve "51192 SSL Certificate Cannot Be Trusted" via certificate push
https://community.tenable.com/s/article/How-To-Resolve-51192-SSL-Certificate-Cannot-Be-Trusted-quick-Fix?language=en_US
2.Certificates and Certificate Authorities
https://docs.tenable.com/nessus/Content/Certificates.htm
3.Create a New Server Certificate and CA Certificate
https://docs.tenable.com/nessus/Content/CreateANewCustomCAAndServerCertificate.htm
·················END·················
你好,我是二大爷,
革命老区外出进城务工人员,
互联网非早期非专业站长,
喜好python,写作,阅读,英语
不入流程序,自媒体,seo . . .
公众号不挣钱,交个网友。
读者交流群已建立,找到我备注 “交流”,即可获得加入我们~
听说点 “在看” 的都变得更好看呐~
关注关注二大爷呗~给你分享python,写作,阅读的内容噢~
扫一扫下方二维码即可关注我噢~


关注我的都变秃了
说错了,都变强了!
不信你试试

扫码关注最新动态
公众号ID:eryeji























 2050
2050

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








