gitee源码:https://gitee.com/antia11/spring-security-demos/tree/master/security-dynamic
搭建一个简单 SpringSecurity 环境
secruity.sql
/*
SQLyog Ultimate v13.1.1 (64 bit)
MySQL - 5.7.19 : Database - security
*********************************************************************
*/
/*!40101 SET NAMES utf8 */;
/*!40101 SET SQL_MODE=''*/;
/*!40014 SET @OLD_UNIQUE_CHECKS=@@UNIQUE_CHECKS, UNIQUE_CHECKS=0 */;
/*!40014 SET @OLD_FOREIGN_KEY_CHECKS=@@FOREIGN_KEY_CHECKS, FOREIGN_KEY_CHECKS=0 */;
/*!40101 SET @OLD_SQL_MODE=@@SQL_MODE, SQL_MODE='NO_AUTO_VALUE_ON_ZERO' */;
/*!40111 SET @OLD_SQL_NOTES=@@SQL_NOTES, SQL_NOTES=0 */;
CREATE DATABASE /*!32312 IF NOT EXISTS*/`security` /*!40100 DEFAULT CHARACTER SET utf8mb4 COLLATE utf8mb4_unicode_ci */;
USE `security`;
/*Table structure for table `menu` */
DROP TABLE IF EXISTS `menu`;
CREATE TABLE `menu` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`pattern` varchar(255) COLLATE utf8mb4_unicode_ci DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=4 DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci;
/*Data for the table `menu` */
insert into `menu`(`id`,`pattern`) values
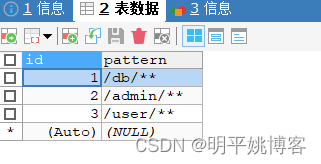
(1,'/db/**'),
(2,'/admin/**'),
(3,'/user/**');
/*Table structure for table `menu_role` */
DROP TABLE IF EXISTS `menu_role`;
CREATE TABLE `menu_role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`mid` int(11) DEFAULT NULL,
`rid` int(11) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=4 DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_unicode_ci;
/*Data for the table `menu_role` */
insert into `menu_role`(`id`,`mid`,`rid`) values
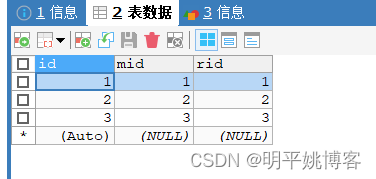
(1,1,1),
(2,2,2),
(3,3,3);
/*Table structure for table `role` */
DROP TABLE IF EXISTS `role`;
CREATE TABLE `role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`name` varchar(32) DEFAULT NULL,
`nameZh` varchar(32) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=4 DEFAULT CHARSET=utf8;
/*Data for the table `role` */
insert into `role`(`id`,`name`,`nameZh`) values
(1,'ROLE_dba','数据库管理员'),
(2,'ROLE_admin','系统管理员'),
(3,'ROLE_user','用户');
/*Table structure for table `user` */
DROP TABLE IF EXISTS `user`;
CREATE TABLE `user` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`username` varchar(32) DEFAULT NULL,
`password` varchar(255) DEFAULT NULL,
`enabled` tinyint(1) DEFAULT NULL,
`locked` tinyint(1) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=4 DEFAULT CHARSET=utf8;
/*Data for the table `user` */
insert into `user`(`id`,`username`,`password`,`enabled`,`locked`) values
(1,'root','$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq',1,0),
(2,'admin','$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq',1,0),
(3,'sang','$2a$10$RMuFXGQ5AtH4wOvkUqyvuecpqUSeoxZYqilXzbz50dceRsga.WYiq',1,0);
/*Table structure for table `user_role` */
DROP TABLE IF EXISTS `user_role`;
CREATE TABLE `user_role` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`uid` int(11) DEFAULT NULL,
`rid` int(11) DEFAULT NULL,
PRIMARY KEY (`id`)
) ENGINE=InnoDB AUTO_INCREMENT=5 DEFAULT CHARSET=utf8;
/*Data for the table `user_role` */
insert into `user_role`(`id`,`uid`,`rid`) values
(1,1,1),
(2,1,2),
(3,2,2),
(4,3,3);
/*!40101 SET SQL_MODE=@OLD_SQL_MODE */;
/*!40014 SET FOREIGN_KEY_CHECKS=@OLD_FOREIGN_KEY_CHECKS */;
/*!40014 SET UNIQUE_CHECKS=@OLD_UNIQUE_CHECKS */;
/*!40111 SET SQL_NOTES=@OLD_SQL_NOTES */;
pom.xml
<dependency>
<groupId>com.alibaba</groupId>
<artifactId>druid-spring-boot-starter</artifactId>
<version>1.2.6</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.mybatis.spring.boot</groupId>
<artifactId>mybatis-spring-boot-starter</artifactId>
<version>2.1.4</version>
</dependency>
<dependency>
<groupId>mysql</groupId>
<artifactId>mysql-connector-java</artifactId>
<scope>runtime</scope>
</dependency>
静态资源过滤
<resources>
<resource>
<directory>src/main/java</directory>
<includes>
<include>**/*.xml</include>
</includes>
</resource>
<resource>
<directory>src/main/resources</directory>
</resource>
</resources>
bean.User.java
package com.zhuantai.securitydynamic.bean;
import lombok.Data;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.security.core.authority.SimpleGrantedAuthority;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import java.util.ArrayList;
import java.util.Collection;
import java.util.List;
/**
* @author ANTIA1
* @date 2021/7/10 1:10
*/
@Data
public class User implements UserDetails {
private Integer id;
private String username;
private String password;
private Boolean enabled;
private Boolean locked;
private List<Role> roles;
@Override
public Collection<? extends GrantedAuthority> getAuthorities() {
List<SimpleGrantedAuthority> authorities = new ArrayList<>();
for (Role role : roles) {
authorities.add(new SimpleGrantedAuthority(role.getName()));
}
return authorities;
}
@Override
public boolean isAccountNonExpired() {
return true;
}
@Override
public boolean isAccountNonLocked() {
return !locked;
}
@Override
public boolean isCredentialsNonExpired() {
return true;
}
@Override
public boolean isEnabled() {
return enabled;
}
}
bean.Role.java
package com.zhuantai.securitydynamic.bean;
import lombok.Data;
/**
* @author ANTIA1
* @date 2021/7/10 1:17
*/
@Data
public class Role {
private Integer id;
private String name;
private String nameZh;
}
bean.Menu.java
package com.zhuantai.securitydynamic.bean;
import lombok.Data;
/**
* @author ANTIA1
* @date 2021/7/10 11:48
*/
@Data
public class Menu {
private Integer id;
private String pattern;
}
service.UserService.java
package com.zhuantai.securitydynamic.service;
import com.zhuantai.securitydynamic.bean.User;
import com.zhuantai.securitydynamic.mapper.UserMapper;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.core.userdetails.UsernameNotFoundException;
import org.springframework.stereotype.Service;
/**
* @author ANTIA1
* @date 2021/7/10 11:51
*/
@Service
public class UserService implements UserDetailsService {
@Autowired
UserMapper userMapper;
@Override
public UserDetails loadUserByUsername(String s) throws UsernameNotFoundException {
User user = userMapper.loadUserByUsername(s);
if (user == null){
throw new UsernameNotFoundException("用户不存在!");
}
user.setRoles(userMapper.getRolesById(user.getId()));
return user;
}
}
mapper.UserMapper.java
package com.zhuantai.securitydynamic.mapper;
import com.zhuantai.securitydynamic.bean.Role;
import com.zhuantai.securitydynamic.bean.User;
import java.util.List;
/**
* @author ANTIA1
* @date 2021/7/10 11:49
*/
public interface UserMapper {
User loadUserByUsername(String username);
List<Role> getRolesById(Integer id);
}
mapper.UserMapper.xml
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="com.zhuantai.securitydynamic.mapper.UserMapper">
<select id="loadUserByUsername" resultType="User">
select *
from user where username = #{username};
</select>
<select id="getRolesById" resultType="Role">
select *
from role where id in (select rid from user_role where uid = #{id});
</select>
</mapper>
controller.HelloController.java
package com.zhuantai.securitydynamic.controller;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
/**
* @author ANTIA1
* @date 2021/7/10 12:05
*/
@RestController
public class HelloController {
@GetMapping("/hello")
public String hello(){
return "hello";
}
}
config.SecurityConfig.java
package com.zhuantai.securitydynamic.config;
import com.zhuantai.securitydynamic.service.UserService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
/**
* @author ANTIA1
* @date 2021/7/10 12:02
*/
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
UserService userService;
@Bean
PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService);
}
@Override
protected void configure(HttpSecurity http) throws Exception {
super.configure(http);
}
}
application.properties
# 应用名称
spring.application.name=security-dynamic
# 应用服务 WEB 访问端口
server.port=8080
#下面这些内容是为了让MyBatis映射
#指定Mybatis的Mapper文件
mybatis.mapper-locations=classpath:mappers/*xml
#指定Mybatis的实体目录
mybatis.type-aliases-package=com.zhuantai.securitydynamic.bean
# 数据库驱动:
spring.datasource.driver-class-name=com.mysql.cj.jdbc.Driver
# 数据源名称
spring.datasource.name=defaultDataSource
# 数据库连接地址
spring.datasource.url=jdbc:mysql://localhost:3306/security?serverTimezone=UTC
# 数据库用户名&密码:
spring.datasource.username=root
spring.datasource.password=123
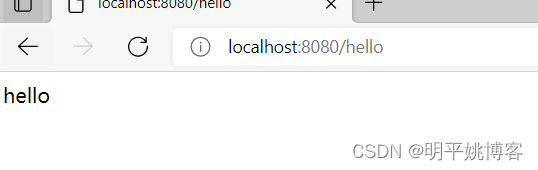
启动程序,在浏览器中访问 http://localhost:8080/hello 输入用户名 root 密码 123 点击登陆,显示 hello 表示环境搭建成功。
配置动态权限
配置动态权限也就是将权限放在数据库中进行管理,方便之后对其的更改。
menu.table
menu_role.table
如果想要访问某个pattern,会要求有权限。
ok,那么在项目中如何去具体实现呢?
创建一个 Filter 实现 FilterInvocationSecurityMetadataSource 接口
这一步的作用是:根据你请求的地址,分析出你请求的地址需要哪些角色。
MyFilter.java
package com.zhuantai.securitydynamic.config;
import com.zhuantai.securitydynamic.bean.Menu;
import com.zhuantai.securitydynamic.bean.Role;
import com.zhuantai.securitydynamic.service.MenuService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.access.ConfigAttribute;
import org.springframework.security.access.SecurityConfig;
import org.springframework.security.web.FilterInvocation;
import org.springframework.security.web.access.intercept.FilterInvocationSecurityMetadataSource;
import org.springframework.stereotype.Component;
import org.springframework.util.AntPathMatcher;
import java.util.Collection;
import java.util.List;
/**
* @author ANTIA1
* @date 2021/7/10 12:38
*/
@Component
public class MyFilter implements FilterInvocationSecurityMetadataSource {
//Java自带的路径匹配工具
AntPathMatcher pathMatcher = new AntPathMatcher();
@Autowired
MenuService menuService;
/**
* 根据你请求的地址,进而分析出你请求的地址需要哪些角色
* @param o FilterInvocation
* @return 该路径所需要的的角色
* @throws IllegalArgumentException
*/
@Override
public Collection<ConfigAttribute> getAttributes(Object o) throws IllegalArgumentException {
String requestUrl = ((FilterInvocation) o).getRequestUrl();//获取请求地址
List<Menu> allMenus = menuService.getAllMenus();
for (Menu menu : allMenus) {
if (pathMatcher.match(menu.getPattern(),requestUrl)){//查看当前请求地址是否和menu中pattern存在匹配
//如果匹配上
List<Role> roles = menu.getRoles();//获取该地址需要哪些角色
//将角色名存入一个String[]中,return出去
String[] rolesStr = new String[roles.size()];
for (int i = 0; i < roles.size(); i++) {
rolesStr[i] = roles.get(i).getName();
}
return SecurityConfig.createList(rolesStr);
}
}
//ROLE_login 标记为该路径不需要角色,只要登录就可以访问
return SecurityConfig.createList("ROLE_login");//默认返回值,如果没有匹配上,做额外处理
}
@Override
public Collection<ConfigAttribute> getAllConfigAttributes() {
return null;
}
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}
ok,获取到访问这个地址需要具备哪些角色后,我们继续来看
创建MyAccessDecisionManager 实现 AccessDecisionManager
上一步我们获取到了访问这个地址需要具备哪些角色权限后,这一步的作用是,判断当前用户是否具备所要求的角色权限。
package com.zhuantai.securitydynamic.config;
import org.springframework.security.access.AccessDecisionManager;
import org.springframework.security.access.AccessDeniedException;
import org.springframework.security.access.ConfigAttribute;
import org.springframework.security.authentication.AnonymousAuthenticationToken;
import org.springframework.security.authentication.InsufficientAuthenticationException;
import org.springframework.security.core.Authentication;
import org.springframework.security.core.GrantedAuthority;
import org.springframework.stereotype.Component;
import java.util.Collection;
/**
* @author ANTIA1
* @date 2021/7/10 13:02
*/
@Component
public class MyAccessDecisionManager implements AccessDecisionManager {
/**
*
* @param authentication 当前登录用户的信息
* @param o FilterInvocation 当前请求的信息
* @param collection MyFilter中的返回值;当前请求所需要的的角色
* @throws AccessDeniedException
* @throws InsufficientAuthenticationException
*/
@Override
public void decide(Authentication authentication, Object o, Collection<ConfigAttribute> collection) throws AccessDeniedException, InsufficientAuthenticationException {
for (ConfigAttribute attribute : collection) {
if ("ROLE_login".equals(attribute.getAttribute())){//说明和之前那些地址都没匹配上
//说明不需要以上那些权限,登录就可以访问,那么需要判断是否登录了。
if (authentication instanceof AnonymousAuthenticationToken){ //判断是不是匿名用户
throw new AccessDeniedException("非法请求!");//匿名用户未登录直接抛异常
}else{
return;//否则说明不是匿名用户,已经登录,可以访问该资源路径
}
}
//我现在具备的角色
Collection<? extends GrantedAuthority> authorities = authentication.getAuthorities();
for (GrantedAuthority authority : authorities) {
if (authority.getAuthority().equals(attribute.getAttribute())){//如果具备所需要的角色
return;
}
}
}
//如果都没匹配上,那就还是一个非法请求
throw new AccessDeniedException("非法请求!");//匿名用户未登录直接抛异常
}
@Override
public boolean supports(ConfigAttribute configAttribute) {
return true;
}
@Override
public boolean supports(Class<?> aClass) {
return true;
}
}
配置SecurityConfig
两步配置完成后,需要将他们配置到SecurityConfig中让他们生效
package com.zhuantai.securitydynamic.config;
import com.zhuantai.securitydynamic.service.UserService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.ObjectPostProcessor;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.web.access.intercept.FilterSecurityInterceptor;
/**
* @author ANTIA1
* @date 2021/7/10 12:02
*/
@Configuration
public class SecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
UserService userService;
@Autowired
MyFilter myFilter;
@Autowired
MyAccessDecisionManager myAccessDecisionManager;
@Bean
PasswordEncoder passwordEncoder(){
return new BCryptPasswordEncoder();
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService);
}
@Override
protected void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
.withObjectPostProcessor(new ObjectPostProcessor<FilterSecurityInterceptor>() {
@Override
public <O extends FilterSecurityInterceptor> O postProcess(O o) {
o.setAccessDecisionManager(myAccessDecisionManager);
o.setSecurityMetadataSource(myFilter);
return o;
}
})
.and()
.formLogin()
.permitAll()
.and()
.csrf().disable();
}
}
修改bean.Menu.java
修改menu对象,menu中需要具备角色权限,所以一个menu可能对应多个权限,那我们需要在其中添加一个Listroles的属性。
package com.zhuantai.securitydynamic.bean;
import lombok.Data;
import java.util.List;
/**
* @author ANTIA1
* @date 2021/7/10 11:48
*/
@Data
public class Menu {
private Integer id;
private String pattern;
private List<Role> roles;
}
补充代码
MenuService.java
package com.zhuantai.securitydynamic.service;
import com.zhuantai.securitydynamic.bean.Menu;
import com.zhuantai.securitydynamic.mapper.MenuMapper;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.stereotype.Service;
import java.util.List;
/**
* @author ANTIA1
* @date 2021/7/10 12:43
*/
@Service
public class MenuService {
@Autowired
MenuMapper menuMapper;
public List<Menu> getAllMenus(){
return menuMapper.getAllMenus();
}
}
MenuMapper.java
package com.zhuantai.securitydynamic.mapper;
import com.zhuantai.securitydynamic.bean.Menu;
import java.util.List;
/**
* @author ANTIA1
* @date 2021/7/10 12:43
*/
public interface MenuMapper {
List<Menu> getAllMenus();
}
MenuMapper.xml
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE mapper
PUBLIC "-//mybatis.org//DTD Mapper 3.0//EN"
"http://mybatis.org/dtd/mybatis-3-mapper.dtd">
<mapper namespace="com.zhuantai.securitydynamic.mapper.MenuMapper">
<resultMap id="BaseResultMap" type="Menu">
<id property="id" column="id"/>
<result property="pattern" column="pattern"/>
<collection property="roles" ofType="com.zhuantai.securitydynamic.bean.Role">
<id column="rid" property="id"/>
<result property="name" column="rname"/>
<result column="rnameZh" property="nameZh"/>
</collection>
</resultMap>
<select id="getAllMenus" resultMap="BaseResultMap">
SELECT
menu.*,r.`id`AS rid,r.`name` AS rname ,r.`nameZh` AS rnameZh
FROM
menu LEFT JOIN menu_role mr ON menu.id = mr.`mid` LEFT JOIN role r ON mr.`rid` = r.`id`
</select>
</mapper>
HelloController.java
package com.zhuantai.securitydynamic.controller;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
/**
* @author ANTIA1
* @date 2021/7/10 12:05
*/
@RestController
public class HelloController {
@GetMapping("/hello")
public String hello(){
return "hello";
}
@GetMapping("/db/hello")
public String db(){
return "hello db";
}
@GetMapping("/admin/hello")
public String admin(){
return "hello admin";
}
@GetMapping("/user/hello")
public String user(){
return "hello user";
}
}
运行测试结果
我们先使用root登录,密码是123,访问:
http://localhost:8080/hello
http://localhost:8080/admin/hello
http://localhost:8080/db/hello
http://localhost:8080/user/hello
如果1、2、3可以访问,4不能访问结果为403,那就说明成功了。
/hello - ok
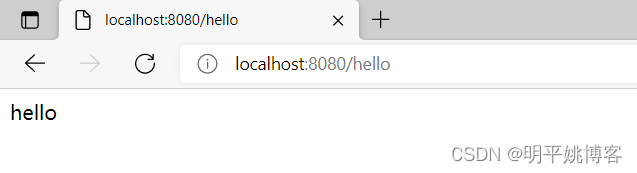
/admin/hello - ok
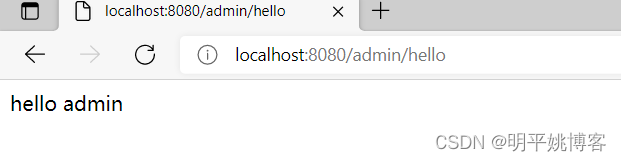
/db/hello - ok
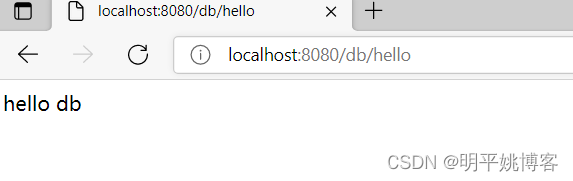
/user/hello - 403
ok,运行成功。基于数据库的动态配置权限验证梳理完毕。






















 504
504











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








