k8s问题排查:kubernetes-dashboard crashloopbackoff 状态
现象
[root@k18-5 ~]# kubectl get pod -n kubernetes-dashboard
NAMESPACE NAME READY STATUS RESTARTS AGE
kubernetes-dashboard dashboard-metrics-scraper-856586f554-927js 1/1 Running 0 8m49s
kubernetes-dashboard kubernetes-dashboard-7b9b87bb74-mjns7 0/1 CrashLoopBackOff 5 8m50s
kubernetes-dashboard启动后,通过浏览器访问不了。发现dashboard过一阵就从Running变为CrashLoopBackOff状态。
查看日志
kubectl logs -f -n kubernetes-dashboard kubernetes-dashboard-7b9b87bb74-mjns7
[root@k18-5 ~]# kubectl logs -f -n kubernetes-dashboard kubernetes-dashboard-7b9b87bb74-mjns7
2023/07/30 09:10:00 Starting overwatch
2023/07/30 09:10:00 Using namespace: kubernetes-dashboard
2023/07/30 09:10:00 Using in-cluster config to connect to apiserver
2023/07/30 09:10:00 Using secret token for csrf signing
2023/07/30 09:10:00 Initializing csrf token from kubernetes-dashboard-csrf secret
panic: Get "https://10.20.0.1:443/api/v1/namespaces/kubernetes-dashboard/secrets/kubernetes-dashboard-csrf": dial tcp 10.20.0.1:443: i/o timeout
goroutine 1 [running]:
github.com/kubernetes/dashboard/src/app/backend/client/csrf.(*csrfTokenManager).init(0xc00017b540)
/home/runner/work/dashboard/dashboard/src/app/backend/client/csrf/manager.go:41 +0x413
github.com/kubernetes/dashboard/src/app/backend/client/csrf.NewCsrfTokenManager(...)
/home/runner/work/dashboard/dashboard/src/app/backend/client/csrf/manager.go:66
github.com/kubernetes/dashboard/src/app/backend/client.(*clientManager).initCSRFKey(0xc000379300)
/home/runner/work/dashboard/dashboard/src/app/backend/client/manager.go:502 +0xc6
github.com/kubernetes/dashboard/src/app/backend/client.(*clientManager).init(0xc000379300)
/home/runner/work/dashboard/dashboard/src/app/backend/client/manager.go:470 +0x47
github.com/kubernetes/dashboard/src/app/backend/client.NewClientManager(...)
/home/runner/work/dashboard/dashboard/src/app/backend/client/manager.go:551
main.main()
/home/runner/work/dashboard/dashboard/src/app/backend/dashboard.go:95 +0x21c
根据日志分析,dashboard部署到了非master节点,网络原因无法正常运行。需要把kubernetes-dashboard部署到master节点,修改dashboard.yaml配置文件添加nodeName: master节点名,如下:
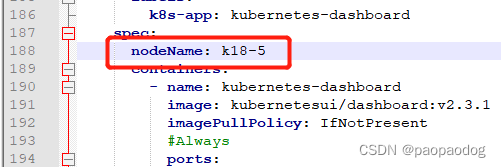
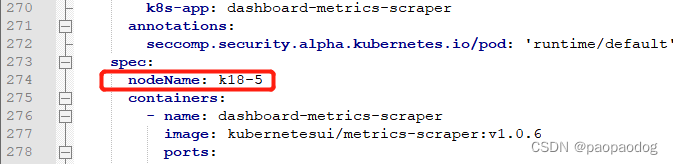
删除dashboard重新创建后查看结果
kubectl delete -f dashboard.yaml
kubectl apply -f dashboard.yaml
[root@k18-5 ~]# kubectl get pod -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-568998bfdd-4q4hh 1/1 Running 0 125m
kubernetes-dashboard-76bc846b7b-52v55 1/1 Running 0 125m
[root@k18-5 ~]# kubectl get svc -A
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard dashboard-metrics-scraper ClusterIP 10.20.89.131 <none> 8000/TCP 133m
kubernetes-dashboard kubernetes-dashboard ClusterIP 10.20.24.98 <none> 443/TCP 133m
访问 https://10.20.24.98/,成功























 1429
1429











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










