IPSEC VPNp配置实验一:
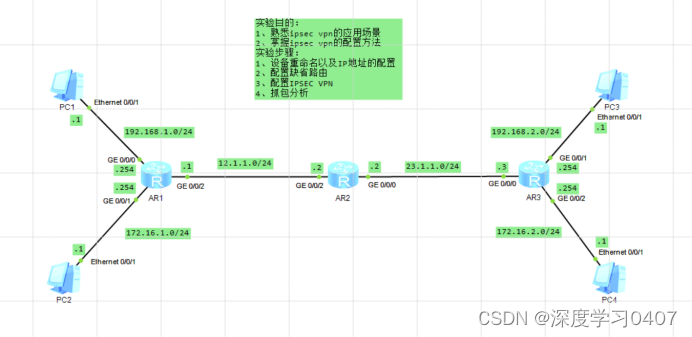
在AR1和AR3上配置静态路由
AR1:ip route-static 0.0.0.0 0.0.0.0 12.1.1.2
AR3:ip route-static 0.0.0.0 0.0.0.0 23.1.1.2
AR1:
#
acl number 3000
rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
ipsec proposal 1
#
ipsec policy hcip 1 manual
security acl 3000
proposal 1
tunnel local 12.1.1.1
tunnel remote 23.1.1.3
sa spi inbound esp 4321
sa string-key inbound esp simple test
sa spi outbound esp 1234
sa string-key outbound esp simple test
#
interface GigabitEthernet0/0/2
ip address 12.1.1.1 255.255.255.0
ipsec policy hcip
AR3:
#
acl number 3000
rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
#
ipsec proposal 1
#
ipsec policy hcip 1 manual
security acl 3000
proposal 1
tunnel local 23.1.1.3
tunnel remote 12.1.1.1
sa spi inbound esp 1234
sa string-key inbound esp simple test
sa spi outbound esp 4321
sa string-key outbound esp simple test
#
interface GigabitEthernet0/0/0
ip address 23.1.1.3 255.255.255.0
ipsec policy hcip
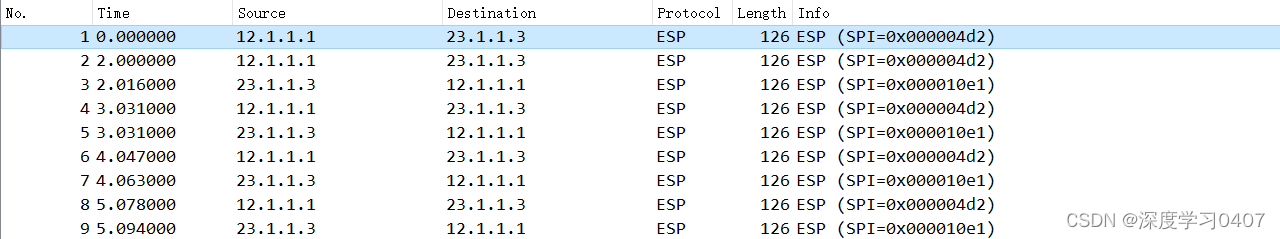
整体配置:
<AR1>dis current-configuration
[V200R003C00]
#
sysname AR1
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
acl number 3000
rule 10 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.25
5
#
ipsec proposal 1
#
ipsec policy hcip 1 manual
security acl 3000
proposal 1
tunnel local 12.1.1.1
tunnel remote 23.1.1.3
sa spi inbound esp 4321
sa string-key inbound esp simple test
sa spi outbound esp 1234
sa string-key outbound esp simple test
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 192.168.1.254 255.255.255.0
#
interface GigabitEthernet0/0/1
ip address 172.16.1.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 12.1.1.1 255.255.255.0
ipsec policy hcip
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 12.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR2>dis cu
[V200R003C00]
#
sysname AR2
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 23.1.1.2 255.255.255.0
#
interface GigabitEthernet0/0/1
#
interface GigabitEthernet0/0/2
ip address 12.1.1.2 255.255.255.0
#
interface NULL0
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
<AR3>dis cu
[V200R003C00]
#
sysname AR3
#
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
#
clock timezone China-Standard-Time minus 08:00:00
#
portal local-server load portalpage.zip
#
drop illegal-mac alarm
#
undo info-center enable
#
set cpu-usage threshold 80 restore 75
#
acl number 3000
rule 10 permit ip source 192.168.2.0 0.0.0.255 destination 192.168.1.0 0.0.0.25
5
#
ipsec proposal 1
#
ipsec policy hcip 1 manual
security acl 3000
proposal 1
tunnel local 23.1.1.3
tunnel remote 12.1.1.1
sa spi inbound esp 1234
sa string-key inbound esp simple test
sa spi outbound esp 4321
sa string-key outbound esp simple test
#
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher %$%$K8m.Nt84DZ}e#<0`8bmE3Uw}%$%$
local-user admin service-type http
#
firewall zone Local
priority 15
#
interface GigabitEthernet0/0/0
ip address 23.1.1.3 255.255.255.0
ipsec policy hcip
#
interface GigabitEthernet0/0/1
ip address 192.168.2.254 255.255.255.0
#
interface GigabitEthernet0/0/2
ip address 172.16.2.254 255.255.255.0
#
interface NULL0
#
ip route-static 0.0.0.0 0.0.0.0 23.1.1.2
#
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
#
wlan ac
#
return
IPSEC VPNp配置实验二:
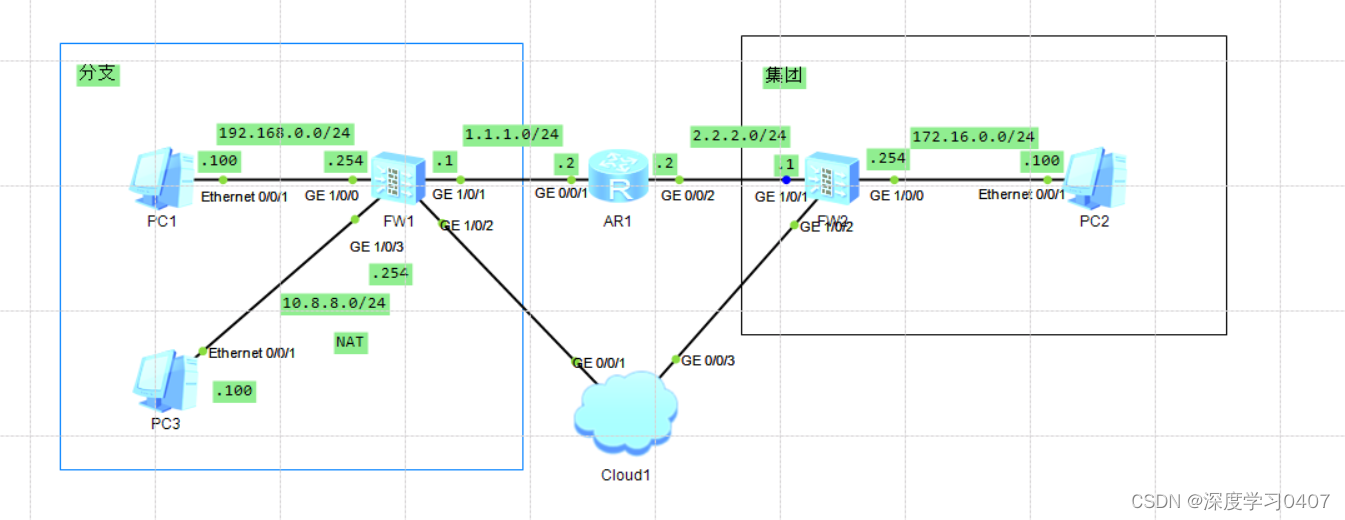























 5012
5012











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










