漏洞描述
Log4j是Apache的一个开源项目,通过使用Log4j,可以控制日志信息输送的目的地是控制台、文件、GUI组件,甚至是套接口服务器、NT的事件记录器、UNIX Syslog守护进程等;也可以控制每一条日志的输出格式;通过定义每一条日志信息的级别,能够更加细致地控制日志的生成过程。这些可以通过一个配置文件来灵活地进行配置,而不需要修改应用的代码。Apache Log4j2是 Log4j的升级版本,据分析,该漏洞产生的原因在于Log4j在记录日志的过程中会对日志内容进行判断,如果内容中包含了${,则Log4j会认为此字符属于可替换的变量,并且Log4j支持JNDI远程加载的方式替换变量值。此漏洞的危害等级很大,只要是调用了Log4j的日志记录功能,并且有用户可控的输入,就可能导致JNDI注入。
漏洞原理
log4j2组件未正确处理用户输入,日志信息经过如下调用链后进入JndiLookup.lookup造成了典型的jndi注入问题:
logger.error()--->AbstractLogger.tryLogMessage.log()--->org.apache.logging.log4j.core.Loggger.log
---->DefaultReliabilityStrategy.log()--->LoggerConfig.log()--->appender.control.callAppender()
---->AppenderControl.tryCallAppender()--->AbstractOutputStreamAppender.append()--->PatternLayout.encode()
--->MessagePatternConverter.format()--->StrSubstitutor.replace()--->StrSubstitutor.subtute()--->resolveVariable()--->JndiManager.lookup()
解决方案
升级最新版Log4j组件。
TOP 受影响组件/应用
截至目前,微步已快速梳理出了400余款主流应用/组件的41000+个受此漏洞影响的版本,可用于快速批量发现受影响的资产。以下为公开的部分 Top 应用/组件,供企业依托此数据构建扫描器,统计可能受影响的资产。
| Apache Struts2 | 全版本 |
| ElasticSearch | 5.x,6.x,7.x,8.0.0beta1,8.0.0alpha1和8.0.0alpha2 |
| Logstash | 5.0.0至最新 |
| Apache Flink | 1.11.0-rc1 到 1.14.0 |
| Apache Druid | 0.7.x以上 |
| Hadoop Hive | 2.x和3.x |
| Apache Log4j SLF4J Binding | '2.14.1', '2.14.0', '2.13.3', '2.13.2', '2.13.1', '2.13.0', '2.12.1', '2.12.0', '2.11.2', '2.11.1', '2.11.0', '2.10.0', '2.9.1', '2.9.0', '2.8.2', '2.8.1', '2.8', '2.7', '2.6.2', '2.6.1', '2.6', '2.5', '2.4.1', '2.4', '2.3', '2.2', '2.1', '2.0.2', '2.0.1', '2.0', '2.0-rc2', '2.0-rc1', '2.0-beta9', '2.0-beta8', '2.0-beta7', '2.0-beta6', '2.0-beta5' |
| Spring Boot | '2.6.1', '2.6.0', '2.5.7', '2.5.6', '2.5.5', '2.5.4', '2.5.3', '2.5.2', '2.5.1', '2.5.0', '2.4.13', '2.4.12', '2.4.11', '2.4.10', '2.4.9', '2.4.8', '2.4.7', '2.4.6', '2.4.5', '2.4.4', '2.4.3', '2.4.2', '2.4.1', '2.4.0', '2.3.12.RELEASE', '2.3.11.RELEASE', '2.3.10.RELEASE', '2.3.9.RELEASE', '2.3.8.RELEASE', '2.3.7.RELEASE', '2.3.6.RELEASE', '2.3.5.RELEASE', '2.3.4.RELEASE', '2.3.3.RELEASE', '2.3.2.RELEASE', '2.3.1.RELEASE', '2.3.0.RELEASE', '2.2.13.RELEASE', '2.2.12.RELEASE', '2.2.11.RELEASE', '2.2.10.RELEASE', '2.2.9.RELEASE', '2.2.8.RELEASE', '2.2.7.RELEASE', '2.2.6.RELEASE', '2.2.5.RELEASE', '2.2.4.RELEASE', '2.2.3.RELEASE', '2.2.2.RELEASE', '2.2.1.RELEASE', '2.2.0.RELEASE', '2.1.18.RELEASE', '2.1.17.RELEASE', '2.1.16.RELEASE', '2.1.15.RELEASE', '2.1.14.RELEASE', '2.1.13.RELEASE', '2.1.12.RELEASE', '2.1.11.RELEASE', '2.1.10.RELEASE', '2.1.9.RELEASE', '2.1.8.RELEASE', '2.1.7.RELEASE', '2.1.6.RELEASE', '2.1.5.RELEASE', '2.1.4.RELEASE', '2.1.3.RELEASE', '2.1.2.RELEASE', '2.1.1.RELEASE', '2.1.0.RELEASE', '2.0.9.RELEASE', '2.0.8.RELEASE', '2.0.7.RELEASE', '2.0.6.RELEASE', '2.0.5.RELEASE', '2.0.4.RELEASE', '2.0.3.RELEASE', '2.0.2.RELEASE', '2.0.1.RELEASE', '2.0.0.RELEASE', '1.5.22.RELEASE', '1.5.21.RELEASE', '1.5.20.RELEASE', '1.5.19.RELEASE', '1.5.18.RELEASE', '1.5.17.RELEASE', '1.5.16.RELEASE', '1.5.15.RELEASE', '1.5.14.RELEASE', '1.5.13.RELEASE', '1.5.12.RELEASE', '1.5.11.RELEASE', '1.5.10.RELEASE', '1.5.9.RELEASE', '1.5.8.RELEASE', '1.5.7.RELEASE', '1.5.6.RELEASE', '1.5.5.RELEASE', '1.5.4.RELEASE', '1.5.3.RELEASE', '1.5.2.RELEASE', '1.5.1.RELEASE', '1.5.0.RELEASE', '1.4.7.RELEASE', '1.4.6.RELEASE', '1.4.5.RELEASE', '1.4.4.RELEASE', '1.4.3.RELEASE', '1.4.2.RELEASE', '1.4.1.RELEASE', '1.4.0.RELEASE', '1.3.8.RELEASE', '1.3.7.RELEASE', '1.3.6.RELEASE', '1.3.5.RELEASE', '1.3.4.RELEASE', '1.3.3.RELEASE', '1.3.2.RELEASE', '1.3.1.RELEASE', '1.3.0.RELEASE', '1.2.8.RELEASE', '1.2.7.RELEASE', '1.2.6.RELEASE', '1.2.5.RELEASE', '1.2.4.RELEASE', '1.2.3.RELEASE', '1.2.2.RELEASE', '1.2.1.RELEASE', '1.2.0.RELEASE', '1.1.12.RELEASE', '1.1.11.RELEASE', '1.1.10.RELEASE', '1.1.9.RELEASE', '1.1.8.RELEASE', '1.1.7.RELEASE', '1.1.6.RELEASE', '1.1.5.RELEASE', '1.1.4.RELEASE', '1.1.3.RELEASE', '1.1.2.RELEASE', '1.1.1.RELEASE', '1.1.0.RELEASE', '1.0.2.RELEASE', '1.0.1.RELEASE', '1.0.0.RELEASE' |
| Camel :: Core | '3.13.0', '3.12.0', '3.11.4', '3.11.3', '3.11.2', '3.11.1', '3.11.0', '3.10.0', '3.9.0', '3.8.0', '3.7.6', '3.7.5', '3.7.4', '3.7.3', '3.7.2', '3.7.1', '3.7.0', '3.6.0', '3.5.0', '3.4.6', '3.4.5', '3.4.4', '3.4.3', '3.4.2', '3.4.1', '3.4.0', '3.3.0', '3.2.0', '3.1.0', '3.0.1', '3.0.0', '2.25.4', '2.25.3', '2.25.2', '2.25.1', '2.25.0', '2.24.3', '2.24.2', '2.24.1', '2.24.0', '2.23.4', '2.23.3', '2.23.2', '2.23.1', '2.23.0', '2.22.5', '2.22.4', '2.22.3', '2.22.2', '2.22.1', '2.22.0', '2.21.5', '2.21.4', '2.21.3', '2.21.2', '2.21.1', '2.21.0', '2.20.4', '2.20.3', '2.20.2', '2.20.1', '2.20.0', '2.19.5', '2.19.4', '2.19.3', '2.19.2', '2.19.1', '2.19.0', '2.18.5', '2.18.4', '2.18.3', '2.18.2', '2.18.1', '2.18.0', '2.17.7', '2.17.6', '2.17.5', '2.17.4', '2.17.3', '2.17.2', '2.17.1', '2.17.0', '2.16.5', '2.16.4', '2.16.3', '2.16.2', '2.16.1', '2.16.0', '2.15.6', '2.15.5', '2.15.4', '2.15.3', '2.15.2', '2.15.1', '2.15.0', '2.14.4', '2.14.3', '2.14.2', '2.14.1', '2.14.0', '2.13.4', '2.13.3', '2.13.2', '2.13.1', '2.13.0', '2.12.5', '2.12.4', '2.12.3', '2.12.2', '2.12.1', '2.12.0', '2.11.4', '2.11.3', '2.11.2', '2.11.1', '2.11.0', '2.10.7', '2.10.6', '2.10.5', '2.10.4', '2.10.3', '2.10.2', '2.10.1', '2.10.0', '2.9.8', '2.9.7', '2.9.6', '2.9.5', '2.9.4', '2.9.3', '2.9.2', '2.9.1', '2.9.0', '2.8.6', '2.8.5', '2.8.4', '2.8.3', '2.8.2', '2.8.1', '2.8.0', '2.7.5', '2.7.4', '2.7.3', '2.7.2', '2.7.1', '2.7.0', '2.6.0', '2.5.0', '2.4.0', '2.3.0', '2.2.0', '2.1.0', '2.0.0', '1.6.4', '1.6.3', '1.6.2', '1.6.1', '1.6.0', '1.5.0', '1.4.0', '1.3.0', '1.2.0', '1.1.0', '1.0.0', '3.0.0-M4', '3.0.0-M3', '3.0.0-M2', '3.0.0-M1', '2.0-M3', '2.0-M2', '2.0-M1', '3.0.0-RC3', '3.0.0-RC2', '3.0.0-RC1', '2.9.0-RC1' |
| JUnit Vintage Engine | '5.8.2', '5.8.1', '5.8.0', '5.7.2', '5.7.1', '5.7.0', '5.6.3', '5.6.2', '5.6.1', '5.6.0', '5.5.2', '5.5.1', '5.5.0', '5.4.2', '5.4.1', '5.4.0', '5.3.2', '5.3.1', '5.3.0', '5.2.0', '5.1.1', '5.1.0', '4.12.3', '4.12.2', '4.12.1', '4.12.0', '5.8.0-M1', '5.7.0-M1', '5.6.0-M1', '5.5.0-M1', '5.4.0-M1', '5.3.0-M1', '5.2.0-M1', '5.1.0-M2', '5.1.0-M1', '4.12.0-M6', '4.12.0-M5', '4.12.0-M4', '4.12.0-M3', '4.12.0-M2', '4.12.0-M1', '5.8.0-RC1', '5.7.0-RC1', '5.6.0-RC1', '5.5.0-RC2', '5.5.0-RC1', '5.4.0-RC2', '5.4.0-RC1', '5.3.0-RC1', '5.2.0-RC1', '5.1.0-RC1', '4.12.0-RC3', '4.12.0-RC2', '4.12.0-RC1' |
| JBoss Logging 3 | '3.4.2.Final', '3.4.1.Final', '3.4.0.Final', '3.3.3.Final', '3.3.2.Final', '3.3.1.Final', '3.3.0.Final', '3.2.1.Final', '3.2.0.Final', '3.1.0.CR2', '3.1.0.CR1', '3.0.0.CR1', '3.3.0.Beta1', '3.2.0.Beta1', '3.1.0.Beta3', '3.1.0.Beta2', '3.1.0.Beta1', '3.0.0.Beta5', '3.0.0.Beta4', '3.0.0.Beta3', '3.0.0.Beta2', '3.0.0.Beta1' |
| HikariCP | '5.0.0', '4.0.3', '4.0.2', '4.0.1', '4.0.0', '3.4.5', '3.4.4', '3.4.3', '3.4.2', '3.4.1', '3.4.0', '3.3.1', '3.3.0', '3.2.0', '3.1.0', '3.0.0', '2.7.9', '2.7.8', '2.7.7', '2.7.6', '2.7.5', '2.7.4', '2.7.3', '2.7.2', '2.7.1', '2.7.0', '2.6.3', '2.6.2', '2.6.1', '2.6.0', '2.5.1', '2.5.0', '2.4.7', '2.4.6', '2.4.5', '2.4.4', '2.4.3', '2.4.2', '2.4.1', '2.4.0', '2.3.13', '2.3.12', '2.3.11', '2.3.10', '2.3.9', '2.3.8', '2.3.7', '2.3.6', '2.3.5', '2.3.4', '2.3.3', '2.3.2', '2.3.1', '2.3.0', '2.2.5', '2.2.4', '2.2.3', '2.2.2', '2.2.1', '2.2.0', '2.1.0', '2.0.1', '2.0.0', '1.4.0', '1.3.9', '1.3.8', '1.3.7', '1.3.6', '1.3.5', '1.3.4', '1.3.3', '1.3.2', '1.3.1', '1.3.0', '1.2.9', '1.2.8', '1.2.7', '1.2.6', '1.2.5', '1.2.4', '1.2.3', '1.2.2', '1.2.1', '1.1.9', '1.1.8', '1.1.7', '1.1.6', '1.1.5', '1.1.4', '1.1.3' |
| Logging | '1.1.0', '1.0.0', '0.6.0', '0.5.0', '0.4.1', '0.4.0', '0.3.1', '0.3.0', '0.2.6', '0.2.4', '0.2.3', '0.2.2', '0.2.0', '0.1.2', '0.1.1', '0.1.0', '0.5.0-alpha.1', '0.5.0-alpha' |
| Jedis | '3.7.0', '3.6.3', '3.6.2', '3.6.1', '3.6.0', '3.5.2', '3.5.1', '3.5.0', '3.4.1', '3.4.0', '3.3.0', '3.2.0', '3.1.0', '3.0.1', '3.0.0', '2.10.2', '2.10.1', '2.10.0', '2.9.3', '2.9.2', '2.9.1', '2.9.0', '2.8.2', '2.8.1', '2.8.0', '2.7.3', '2.7.2', '2.7.1', '2.7.0', '2.6.3', '2.6.2', '2.6.1', '2.6.0', '2.5.2', '2.5.1', '2.5.0', '2.4.2', '2.4.1', '2.4.0', '2.3.1', '2.3.0', '2.2.1', '2.2.0', '2.1.0', '2.0.0', '1.5.2', '1.5.1', '1.5.0', '1.4.0', '1.3.1', '1.3.0', 'jedis-3.6.2', '3.1.0-m4', '3.1.0-m3', '3.1.0-m2', '3.1.0-m1', '3.0.0-m1', '2.10.0-m1', '3.7.0-RC1', '3.6.0-RC1', '3.1.0-rc2', '3.1.0-rc', '3.0.1-rc1', '3.0.0-rc1', '2.10.0-rc1', '1.5.0-RC2', '1.5.0-RC1', '4.0.0-beta4', '4.0.0-beta3', '4.0.0-beta2', '4.0.0-beta1' |
| WSO2 Carbon Kernel Core | '5.2.13', '5.2.8', '5.2.7', '5.2.6', '5.2.5', '5.2.4', '5.2.3', '5.2.2', '5.2.1', '4.6.2', '4.6.1', '4.6.0', '4.5.1', '4.4.37', '4.4.36', '4.4.35', '4.4.34', '4.4.33', '4.4.32', '4.4.31', '4.4.30', '4.4.29', '4.4.28', '4.4.27', '4.4.26', '4.4.25', '4.4.24', '4.4.23', '4.4.22', '4.4.21', '4.4.20', '4.4.19', '4.7.0-m6', '4.7.0-m5', '4.7.0-m4', '4.7.0-m3', '4.7.0-m2', '4.7.0-m1', '4.6.3-m5', '4.6.3-m4', '4.6.3-m3', '4.6.3-m2', '4.6.3-m1', '4.6.2-m9', '4.6.2-m8', '4.6.2-m7', '4.6.2-m6', '4.6.2-m5', '4.6.2-m4', '4.6.2-m3', '4.6.2-m2', '4.6.2-m1', '4.6.1-m8', '4.6.1-m7', '4.6.1-m6', '4.6.1-m5', '4.6.1-m4', '4.6.1-m3', '4.6.1-m2', '4.6.1-m1', '4.6.1-beta2', '4.6.1-beta', '4.6.0-beta2', '4.6.1-alpha3', '4.6.1-alpha2', '4.6.1-alpha', '4.6.0-alpha2', '4.6.0-alpha' |
IOC披露
1. IP信誉类情报:表示相关ip曾试图利用此次Log4j2漏洞进行攻击,建议根据自身安全防护等级和策略进行封禁,不建议全部长时间封禁。
| 139.59.175.24 |
| 47.114.37.227 |
| 213.164.204.146 |
| 185.10.68.168 |
| 195.123.247.209 |
| 20.71.156.146 |
| 206.189.20.141 |
| 209.141.34.232 |
| 23.129.64.132 |
| 23.129.64.137 |
| 23.129.64.135 |
| 35.76.31.198 |
| 45.153.160.133 |
| 51.15.43.205 |
| 51.77.52.216 |
| 64.113.32.29 |
| 138.197.193.220 |
| 138.197.72.76 |
| 165.232.84.228 |
| 178.62.32.211 |
| 68.183.33.144 |
| 116.89.189.30 |
| 115.151.228.18 |
| 112.74.185.158 |
| 101.71.38.231 |
| 101.71.37.47 |
| 67.207.93.79 |
| 45.64.75.134 |
| 39.102.236.51 |
| 221.226.159.22 |
| 212.102.50.89 |
| 194.110.84.93 |
| 194.110.84.39 |
| 182.99.247.122 |
| 37.19.212.88 |
| 23.129.64.138 |
| 37.187.122.82 |
| 45.153.160.139 |
| 209.97.133.112 |
| 217.138.208.92 |
| 219.100.36.177 |
| 23.128.248.13 |
| 23.129.64.136 |
| 23.129.64.143 |
| 31.171.154.132 |
| 35.232.163.113 |
| 52.140.215.233 |
| 54.146.233.218 |
| 78.31.71.247 |
| 92.38.178.27 |
| 128.14.102.187 |
| 45.83.66.86 |
| 45.83.66.36 |
| 45.83.67.183 |
| 111.205.62.212 |
| 16.162.192.45 |
| 185.135.81.158 |
| 45.83.66.228 |
| 217.68.181.100 |
| 58.247.209.203 |
| 5.254.101.169 |
| 45.83.67.0 |
| 128.199.24.9 |
| 106.92.114.249 |
| 101.35.199.152 |
| 45.83.67.64 |
| 49.36.231.105 |
| 113.17.41.134 |
| 121.31.247.58 |
| 206.189.29.232 |
| 52.175.18.172 |
| 167.99.188.167 |
| 45.83.65.82 |
| 64.188.16.142 |
| 114.246.35.153 |
| 114.254.20.186 |
| 203.175.13.14 |
| 95.141.35.15 |
| 45.83.67.234 |
| 15.165.232.131 |
| 45.83.67.75 |
| 45.83.65.40 |
| 155.94.151.218 |
| 143.110.229.254 |
| 47.102.205.237 |
| 185.243.41.202 |
| 13.231.10.223 |
| 172.105.194.253 |
| 101.91.94.183 |
| 111.206.179.155 |
| 111.206.179.154 |
| 172.255.242.100 |
| 172.255.242.105 |
| 172.255.242.115 |
| 172.255.242.121 |
| 172.255.242.123 |
| 172.255.242.124 |
| 172.255.242.66 |
| 172.255.242.67 |
| 172.255.242.77 |
| 74.120.175.173 |
| 45.63.94.142[ |
| 195.19.192.26 |
| 45.155.205.233 |
| 45.137.21.9 |
| 134.122.34.28 |
| 167.99.172.58 |
| 185.232.23.46 |
| 20.205.104.227 |
| 209.127.17.242 |
| 209.141.45.189 |
| 23.129.64.131 |
| 23.129.64.146 |
| 94.230.208.147 |
| 139.59.182.104 |
| 165.227.37.189 |
| 68.183.36.244 |
| 112.74.34.48 |
| 86.109.208.194 |
| 58.100.164.147 |
| 61.178.32.114 |
| 49.7.224.217 |
| 41.203.140.114 |
| 218.89.222.71 |
| 212.102.50.103 |
| 209.141.58.146 |
| 199.249.230.119 |
| 23.108.92.140 |
| 45.33.120.240 |
| 137.184.111.180 |
| 91.245.81.65 |
| 185.220.103.116 |
| 209.141.46.203 |
| 209.141.59.180 |
| 212.102.40.36 |
| 219.159.77.109 |
| 35.193.211.95 |
| 37.19.213.148 |
| 46.58.195.62 |
| 68.183.44.164 |
| 80.67.172.162 |
| 139.59.4.192 |
| 45.83.66.100 |
| 51.15.244.188 |
| 111.127.128.136 |
| 13.213.127.204 |
| 103.112.31.26 |
| 199.249.230.84 |
| 194.87.236.154 |
| 107.189.11.228 |
| 172.106.16.74 |
| 45.83.64.235 |
| 172.105.59.246 |
| 167.71.67.189 |
| 45.83.67.22 |
| 185.193.125.249 |
| 157.245.111.173 |
| 45.83.67.77 |
| 107.189.14.27 |
| 118.112.74.218 |
| 83.97.20.151 |
| 205.185.125.45 |
| 23.154.177.6 |
| 77.199.38.33 |
| 45.83.67.134 |
| 157.245.102.218 |
| 49.118.75.38 |
| 167.172.69.175 |
| 23.105.194.3 |
| 45.83.65.76 |
| 115.60.103.185 |
| 45.83.65.94 |
| 45.83.67.38 |
| 45.83.67.203 |
| 110.40.158.125 |
| 111.222.1.161 |
| 117.139.166.157 |
| 113.23.25.97 |
| 116.239.33.15 |
| 172.255.242.101 |
| 172.255.242.112 |
| 172.255.242.117 |
| 172.255.242.118 |
| 172.255.242.119 |
| 172.255.242.122 |
| 172.255.242.68 |
| 172.255.242.73 |
| 172.255.242.79 |
| 172.255.242.78 |
| 172.255.242.83 |
| 172.255.242.85 |
| 172.255.242.86 |
| 172.255.242.90 |
| 172.255.242.92 |
| 172.255.242.91 |
| 172.255.242.96 |
| 172.255.242.99 |
| 62.182.80.168 |
| 109.237.96.124 |
| 107.189.31.195 |
| 109.70.100.25 |
| 139.59.97.205 |
| 185.220.101.128 |
| 198.98.60.19 |
| 199.195.250.77 |
| 204.8.156.142 |
| 209.127.17.234 |
| 211.154.194.21 |
| 23.129.64.145 |
| 23.129.64.149 |
| 37.123.163.58 |
| 45.153.160.131 |
| 45.153.160.140 |
| 51.15.76.60 |
| 62.102.148.69 |
| 66.220.242.222 |
| 68.183.44.143 |
| 82.221.131.71 |
| 85.93.218.204 |
| 89.249.63.3 |
| 167.99.221.249 |
| 167.99.88.151 |
| 67.205.170.85 |
| 68.183.207.73 |
| 68.183.35.171 |
| 68.183.41.150 |
| 121.36.213.142 |
| 52.231.93.116 |
| 218.29.217.234 |
| 217.112.83.246 |
| 180.149.231.197 |
| 36.155.14.163 |
| 23.129.64.144 |
| 23.129.64.142 |
| 185.213.155.168 |
| 81.30.157.43 |
| 78.31.71.248 |
| 199.195.252.18 |
| 207.246.101.221 |
| 217.138.200.150 |
| 217.138.208.94 |
| 217.79.189.13 |
| 23.82.194.166 |
| 36.4.92.53 |
| 37.19.213.149 |
| 45.140.168.37 |
| 46.194.138.182 |
| 5.254.101.167 |
| 51.105.55.17 |
| 91.207.173.123 |
| 91.221.57.179 |
| 45.83.67.190 |
| 180.140.163.156 |
| 218.28.128.14 |
| 45.83.67.33 |
| 112.103.102.184 |
| 45.83.65.93 |
| 167.99.164.183 |
| 45.76.176.24 |
| 45.83.65.61 |
| 188.166.26.105 |
| 185.4.132.135 |
| 222.128.62.127 |
| 221.222.155.240 |
| 164.90.159.39 |
| 45.83.66.65 |
| 137.184.98.160 |
| 222.211.205.179 |
| 213.173.34.93 |
| 45.83.64.129 |
| 223.89.64.12 |
| 172.105.57.210 |
| 103.13.220.57 |
| 192.144.236.164 |
| 137.184.109.130 |
| 103.145.22.103 |
| 183.160.4.88 |
| 49.93.83.226 |
| 66.112.213.87 |
| 45.76.191.147 |
| 125.33.172.90 |
| 172.105.97.149 |
| 45.83.67.180 |
| 45.83.64.45 |
| 194.195.112.76 |
| 192.42.116.16 |
| 167.99.219.41 |
| 119.160.234.68 |
| 1.209.47.241 |
| 182.118.237.234 |
| 120.228.88.232 |
| 171.218.53.30 |
| 103.37.3.122 |
| 110.185.172.206 |
| 172.255.242.102 |
| 172.255.242.107 |
| 172.255.242.113 |
| 172.255.242.114 |
| 62.76.41.46 |
| 212.193.57.225 |
| 104.244.72.129 |
| 122.161.50.23 |
| 138.68.167.19 |
| 143.198.32.72 |
| 167.99.164.201 |
| 185.220.101.137 |
| 188.166.122.43 |
| 205.185.117.149 |
| 221.199.187.100 |
| 23.129.64.133 |
| 23.129.64.141 |
| 45.12.134.108 |
| 46.105.95.220 |
| 45.154.255.147 |
| 46.166.139.111 |
| 5.157.38.50 |
| 60.31.180.149 |
| 61.19.25.207 |
| 81.17.18.59 |
| 91.207.174.157 |
| 89.238.178.213 |
| 86.106.103.29 |
| 49.234.81.169 |
| 42.192.69.45 |
| 221.228.87.37 |
| 211.218.126.140 |
| 172.241.167.37 |
| 37.19.213.150 |
| 31.6.19.41 |
| 23.129.64.130 |
| 197.246.171.111 |
| 1.209.249.188 |
| 147.182.213.12 |
| 36.227.164.189 |
| 198.98.62.150 |
| 199.195.248.29 |
| 20.73.161.16 |
| 209.141.54.195 |
| 217.146.83.136 |
| 23.82.194.113 |
| 23.82.194.114 |
| 37.187.96.183 |
| 37.19.213.10 |
| 37.19.212.103 |
| 37.19.213.200 |
| 58.241.61.242 |
| 68.183.2.123 |
| 80.57.9.110 |
| 89.163.249.192 |
| 91.250.242.12 |
| 103.149.248.27 |
| 45.83.65.148 |
| 37.120.189.247 |
| 185.220.102.247 |
| 118.112.74.135 |
| 157.122.61.12 |
| 211.138.191.69 |
| 91.243.81.71 |
| 112.10.117.77 |
| 185.113.128.30 |
| 114.24.19.243 |
| 185.220.101.130 |
| 47.102.199.233 |
| 38.143.9.76 |
| 45.83.66.183 |
| 116.206.103.246 |
| 172.105.194.173 |
| 18.177.59.255 |
| 121.229.219.55 |
| 23.234.200.135 |
| 103.130.166.234 |
| 45.83.64.108 |
| 45.83.65.141 |
| 45.83.66.29 |
| 42.159.91.12 |
| 45.83.66.134 |
| 122.161.48.150 |
| 185.14.47.20 |
| 116.246.0.93 |
| 84.53.225.118 |
| 101.206.168.120 |
| 54.199.27.97 |
| 216.24.191.27 |
| 180.102.206.209 |
| 203.218.252.81 |
| 103.149.162.116 |
| 45.83.64.223 |
| 198.98.59.65 |
| 101.89.239.166 |
| 119.167.231.51 |
| 123.56.241.236 |
| 120.244.198.234 |
| 172.255.242.104 |
| 172.255.242.109 |
| 172.255.242.110 |
| 172.255.242.126 |
| 89.163.144.156 |
| 119.91.216.192 |
| 104.244.76.44 |
| 185.220.102.8 |
| 199.249.230.110 |
| 209.141.41.103 |
| 23.129.64.140 |
| 45.129.56.200 |
| 45.153.160.2 |
| 62.102.148.68 |
| 68.183.198.247 |
| 46.101.223.115 |
| 68.183.192.239 |
| 68.183.198.36 |
| 124.224.87.11 |
| 115.151.228.146 |
| 68.183.37.10 |
| 61.175.202.154 |
| 23.129.64.134 |
| 120.24.23.84 |
| 34.247.50.189 |
| 159.65.43.94 |
| 199.249.230.163 |
| 209.58.146.134 |
| 37.120.204.142 |
| 37.19.213.168 |
| 37.19.213.198 |
| 37.19.213.170 |
| 37.19.213.199 |
| 37.221.66.128 |
| 45.133.194.118 |
| 49.233.62.251 |
| 49.74.65.69 |
| 113.68.61.30 |
| 54.144.8.103 |
| 54.254.58.27 |
| 147.182.188.183 |
| 45.83.67.58 |
| 182.99.246.138 |
| 223.104.67.7 |
| 174.138.9.117 |
| 5.254.43.59 |
| 167.71.14.192 |
| 117.89.128.117 |
| 45.83.64.153 |
| 8.209.212.37 |
| 134.209.153.239 |
| 45.83.64.43 |
| 122.225.220.134 |
| 45.83.64.148 |
| 116.206.231.53 |
| 103.47.48.65 |
| 178.62.222.131 |
| 113.207.68.47 |
| 167.99.216.68 |
| 110.191.179.149 |
| 45.83.66.130 |
| 45.61.184.239 |
| 165.22.222.120 |
| 103.194.184.98 |
| 45.83.66.175 |
| 152.70.110.78 |
| 101.89.19.197 |
| 117.139.38.130 |
| 121.24.8.114 |
| 45.83.67.48 |
| 120.239.67.147 |
| 117.36.0.131 |
| 211.148.73.182 |
| 185.220.101.13 |
| 45.83.65.151 |
| 182.118.237.42 |
| 101.93.86.68 |
| 18.204.199.0 |
| 94.230.208.148 |
| 45.83.64.164 |
| 123.122.133.12 |
| 122.119.22.37 |
| 122.119.22.38 |
| 172.255.242.103 |
| 172.255.242.108 |
| 172.255.242.106 |
| 172.255.242.111 |
| 172.255.242.81 |
| 172.255.242.80 |
| 172.255.242.97 |
| 172.255.78.132 |
| 172.255.78.133 |
| 172.255.78.137 |
| 172.255.78.138 |
| 172.255.78.141 |
| 172.255.78.147 |
| 172.255.78.150 |
| 172.255.78.157 |
| 172.255.78.158 |
| 172.255.78.159 |
| 172.255.78.160 |
| 172.255.78.162 |
| 172.255.78.170 |
| 172.255.78.180 |
| 172.255.242.75 |
| 172.255.242.84 |
| 172.255.242.89 |
| 172.255.242.94 |
| 172.255.242.98 |
| 172.255.78.134 |
| 172.255.78.140 |
| 172.255.78.144 |
| 172.255.78.146 |
| 172.255.78.151 |
| 172.255.78.155 |
| 172.255.78.166 |
| 172.255.78.164 |
| 172.255.78.168 |
| 172.255.78.171 |
| 172.255.78.172 |
| 172.255.78.174 |
| 172.255.78.188 |
| 172.255.78.189 |
| 172.255.79.198 |
| 172.255.79.202 |
| 172.255.79.200 |
| 172.255.79.208 |
| 172.255.79.219 |
| 172.255.79.221 |
| 172.255.79.227 |
| 172.255.79.231 |
| 172.255.79.245 |
| 172.255.79.251 |
| 172.255.79.254 |
| 173.208.92.13 |
| 173.208.92.27 |
| 173.208.92.32 |
| 173.208.92.36 |
| 173.208.92.39 |
| 173.208.92.40 |
| 173.208.92.45 |
| 173.208.92.46 |
| 173.208.92.5 |
| 173.208.92.49 |
| 173.208.92.54 |
| 173.208.92.62 |
| 173.208.92.7 |
| 202.99.51.154 |
| 210.3.53.109 |
| 23.19.74.95 |
| 218.28.128.10 |
| 39.148.24.162 |
| 45.83.64.140 |
| 45.83.64.144 |
| 45.83.64.175 |
| 45.83.64.190 |
| 45.83.64.53 |
| 45.83.64.49 |
| 45.83.64.55 |
| 45.83.64.83 |
| 45.83.64.94 |
| 45.83.64.97 |
| 45.83.65.25 |
| 45.83.65.56 |
| 45.83.65.97 |
| 45.83.66.102 |
| 45.83.66.132 |
| 45.83.66.192 |
| 45.83.66.214 |
| 45.83.66.60 |
| 45.83.66.78 |
| 45.83.66.80 |
| 45.83.67.129 |
| 45.83.67.127 |
| 45.83.67.133 |
| 45.83.67.145 |
| 45.83.67.236 |
| 45.83.67.249 |
| 45.83.67.43 |
| 45.83.67.8 |
| 45.83.67.94 |
| 96.45.166.101 |
| 185.100.87.202 |
| 18.27.197.252 |
| 104.244.72.115 |
| 104.244.72.136 |
| 104.244.73.85 |
| 104.244.75.225 |
| 107.189.10.137 |
| 107.189.11.153 |
| 107.189.28.100 |
| 107.189.28.241 |
| 107.189.29.41 |
| 107.189.3.244 |
| 116.24.67.213 |
| 135.148.43.32 |
| 128.31.0.13 |
| 143.198.45.117 |
| 147.182.154.100 |
| 151.115.60.113 |
| 162.142.125.194 |
| 162.142.125.196 |
| 162.142.125.43 |
| 162.247.74.202 |
| 162.247.74.7 |
| 164.90.199.216 |
| 167.248.133.116 |
| 167.248.133.44 |
| 167.94.138.60 |
| 178.17.170.23 |
| 178.176.202.121 |
| 178.176.203.190 |
| 178.20.55.16 |
| 181.214.39.2 |
| 185.100.87.139 |
| 185.107.47.171 |
| 185.220.100.247 |
| 185.220.100.252 |
| 185.220.101.133 |
| 185.220.101.139 |
| 185.220.101.140 |
| 185.220.101.141 |
| 185.220.101.145 |
| 185.220.101.144 |
| 185.220.101.159 |
| 185.220.101.158 |
| 185.220.101.161 |
| 185.220.101.160 |
| 185.220.101.162 |
| 185.220.101.167 |
| 185.220.101.174 |
| 185.220.101.172 |
| 185.220.101.177 |
| 185.220.101.183 |
| 185.220.101.184 |
| 185.220.101.38 |
| 185.220.101.40 |
| 185.220.101.41 |
| 185.220.101.43 |
| 185.220.101.48 |
| 185.220.101.58 |
| 185.220.101.57 |
| 185.220.101.61 |
| 185.220.101.60 |
| 185.220.102.245 |
| 185.220.101.9 |
| 185.220.102.250 |
| 185.220.103.4 |
| 185.220.103.5 |
| 185.38.175.132 |
| 193.110.95.34 |
| 192.160.102.169 |
| 194.163.133.36 |
| 193.239.232.101 |
| 194.135.33.152 |
| 198.144.121.43 |
| 198.98.51.189 |
| 199.217.117.92 |
| 205.185.115.217 |
| 23.129.64.139 |
| 23.154.177.4 |
| 37.120.232.51 |
| 45.153.160.130 |
| 45.153.160.135 |
| 46.182.21.248 |
| 47.254.127.78 |
| 5.182.210.216 |
| 5.2.72.73 |
| 81.17.18.60 |
| 89.35.30.236 |
| 91.203.5.146 |
| 94.142.241.194 |
| 134.209.82.14 |
| 139.59.108.31 |
| 142.93.157.150 |
| 143.198.183.66 |
| 147.182.187.229 |
| 147.182.179.141 |
| 157.245.129.50 |
| 159.223.61.102 |
| 159.89.94.219 |
| 178.128.232.114 |
| 188.166.102.47 |
| 64.227.67.110 |
| 167.71.4.81 |
| 159.48.55.216 |
| 131.100.148.7 |
| 120.195.30.152 |
| 115.151.228.83 |
| 191.101.132.152 |
| 182.99.247.181 |
| 182.99.234.208 |
| 172.83.40.103 |
| 118.27.36.56 |
| 1.179.247.182 |
| 159.65.146.60 |
| 185.51.76.187 |
| 104.244.74.121 |
| 111.59.85.209 |
| 112.27.199.180 |
| 124.224.87.29 |
| 122.117.91.144 |
| 134.122.33.6 |
| 137.184.137.242 |
| 14.177.141.126 |
| 147.182.195.250 |
| 157.245.105.213 |
| 164.90.196.7 |
| 172.83.40.124 |
| 185.170.114.25 |
| 185.236.200.116 |
| 188.241.156.207 |
| 192.40.57.54 |
| 193.122.108.228 |
| 198.54.128.94 |
| 67.205.191.102 |
| 193.3.19.159 |
| 207.180.202.75 |
| 89.163.143.8 |
| 178.128.229.113 |
| 165.227.209.202 |
| 195.176.3.23 |
| 80.71.158.12 |
| 188.241.156.221 |
| 139.28.219.110 |
| 40.64.92.153 |
| 62.181.147.15 |
| 85.10.195.175 |
| 89.187.162.98 |
| 95.216.226.236 |
| 156.146.35.73 |
| 138.199.21.9 |
| 115.151.229.27 |
| 115.151.228.95 |
| 115.151.228.64 |
| 109.70.150.139 |
| 103.4.30.79 |
| 101.71.38.179 |
| 89.38.69.136 |
| 89.38.69.99 |
| 82.102.25.253 |
| 82.102.31.170 |
| 84.17.39.201 |
| 185.202.220.75 |
| 182.253.160.196 |
| 182.99.247.75 |
| 178.239.173.228 |
| 159.89.180.119 |
| 147.182.199.94 |
| 109.70.100.28 |
| 101.35.154.34 |
| 172.255.78.178 |
| 172.255.78.182 |
| 172.255.78.183 |
| 172.255.79.199 |
| 172.255.79.205 |
| 172.255.79.207 |
| 172.255.79.210 |
| 172.255.79.223 |
| 172.255.79.235 |
| 172.255.79.240 |
| 172.255.79.247 |
| 172.255.79.249 |
| 172.255.79.253 |
| 173.208.92.16 |
| 173.208.92.17 |
| 173.208.92.26 |
| 173.208.92.28 |
| 173.208.92.31 |
| 173.208.92.43 |
| 173.208.92.44 |
| 173.208.92.47 |
| 173.208.92.53 |
| 173.208.92.56 |
| 173.208.92.59 |
| 173.208.92.60 |
| 183.220.31.71 |
| 183.216.210.247 |
| 23.226.49.42 |
| 39.100.155.32 |
| 42.81.61.12 |
| 45.83.64.107 |
| 45.83.64.11 |
| 45.83.64.116 |
| 45.83.64.134 |
| 45.83.64.142 |
| 45.83.64.152 |
| 45.83.64.230 |
| 45.83.64.224 |
| 45.83.64.68 |
| 45.83.64.86 |
| 45.83.65.130 |
| 45.83.65.138 |
| 45.83.65.206 |
| 45.83.65.64 |
| 45.83.65.91 |
| 45.83.66.10 |
| 45.83.66.135 |
| 45.83.66.139 |
| 45.83.66.186 |
| 45.83.66.193 |
| 45.83.66.172 |
| 45.83.66.20 |
| 45.83.66.219 |
| 45.83.66.221 |
| 45.83.66.5 |
| 45.83.66.49 |
| 45.83.67.107 |
| 45.83.67.12 |
| 45.83.67.171 |
| 45.83.67.172 |
| 45.83.67.220 |
| 45.83.67.224 |
| 45.83.67.233 |
| 45.83.67.70 |
| 45.83.67.83 |
| 45.83.67.96 |
| 58.187.172.182 |
| 62.210.130.250 |
| 185.220.100.242 |
| 104.244.74.57 |
| 104.244.76.173 |
| 104.244.77.235 |
| 104.244.78.213 |
| 107.189.14.76 |
| 109.70.100.22 |
| 137.184.106.119 |
| 140.246.171.141 |
| 143.110.221.204 |
| 147.182.150.124 |
| 147.182.219.9 |
| 157.230.32.67 |
| 159.223.9.17 |
| 159.65.194.103 |
| 159.65.155.208 |
| 162.142.125.193 |
| 162.142.125.60 |
| 163.172.157.143 |
| 167.248.133.42 |
| 167.248.133.60 |
| 167.94.138.43 |
| 167.94.138.58 |
| 167.94.145.60 |
| 178.17.170.135 |
| 185.100.87.41 |
| 185.129.61.4 |
| 185.220.100.243 |
| 185.220.100.246 |
| 185.220.100.254 |
| 185.220.101.1 |
| 185.220.101.132 |
| 185.220.101.138 |
| 185.220.101.142 |
| 185.220.101.143 |
| 185.220.101.152 |
| 185.220.101.156 |
| 185.220.101.166 |
| 185.220.101.171 |
| 185.220.101.170 |
| 185.220.101.181 |
| 185.220.101.2 |
| 185.220.101.3 |
| 185.220.101.34 |
| 185.220.101.49 |
| 185.220.101.52 |
| 185.220.101.50 |
| 185.220.101.56 |
| 185.220.101.59 |
| 185.220.102.241 |
| 185.220.102.243 |
| 185.220.102.6 |
| 185.220.103.119 |
| 188.166.225.104 |
| 192.99.152.200 |
| 193.189.100.202 |
| 193.218.118.183 |
| 193.31.24.154 |
| 195.176.3.19 |
| 199.195.253.162 |
| 205.185.126.167 |
| 212.192.246.95 |
| 213.202.216.189 |
| 213.95.149.22 |
| 216.218.134.12 |
| 23.154.177.2 |
| 23.184.48.209 |
| 45.61.185.54 |
| 46.4.51.212 |
| 5.199.143.202 |
| 54.173.99.121 |
| 68.79.17.59 |
| 81.17.18.62 |
| 88.80.20.86 |
| 89.163.154.91 |
| 128.199.222.221 |
| 134.209.24.42 |
| 138.197.106.234 |
| 138.197.9.239 |
| 138.68.155.222 |
| 159.89.48.173 |
| 164.92.254.33 |
| 165.22.201.45 |
| 167.99.221.217 |
| 178.62.23.146 |
| 51.195.45.190 |
| 160.238.38.196 |
| 159.89.85.91 |
| 154.65.28.250 |
| 146.56.148.181 |
| 143.244.184.81 |
| 139.59.224.7 |
| 139.59.99.80 |
| 139.59.96.42 |
| 114.112.161.155 |
| 182.99.246.183 |
| 167.99.164.160 |
| 103.90.239.209 |
| 137.184.105.192 |
| 137.184.138.79 |
| 138.199.21.199 |
| 144.217.86.109 |
| 157.245.107.6 |
| 157.245.108.40 |
| 157.245.96.165 |
| 159.65.60.100 |
| 167.172.69.97 |
| 167.172.71.96 |
| 167.99.172.111 |
| 178.159.3.167 |
| 180.136.188.219 |
| 185.255.79.72 |
| 192.150.9.201 |
| 195.201.175.217 |
| 142.93.148.12 |
| 159.223.81.193 |
| 34.124.226.216 |
| 161.97.138.227 |
| 107.189.6.166 |
| 107.189.5.206 |
| 5.22.208.77 |
| 52.232.211.163 |
| 172.111.48.30 |
| 146.70.75.54 |
| 146.70.75.21 |
| 138.199.21.10 |
| 123.60.215.208 |
| 122.155.174.180 |
| 115.151.229.39 |
| 103.232.137.187 |
| 89.187.161.35 |
| 49.234.43.244 |
| 45.248.77.142 |
| 217.146.83.229 |
| 209.58.146.160 |
| 193.32.210.125 |
| 185.216.74.114 |
| 185.7.33.36 |
| 185.199.100.233 |
| 182.99.246.172 |
| 23.82.194.167 |
| 212.193.30.142 |
| 159.65.175.123 |
| 62.171.142.3 |
| 172.255.242.70 |
| 172.255.242.71 |
| 172.255.242.74 |
| 172.255.242.76 |
| 172.255.242.82 |
| 172.255.242.87 |
| 172.255.242.88 |
| 172.255.78.135 |
| 172.255.78.148 |
| 172.255.78.154 |
| 172.255.78.169 |
| 172.255.78.176 |
| 172.255.78.179 |
| 172.255.79.195 |
| 172.255.79.196 |
| 172.255.79.197 |
| 172.255.79.201 |
| 172.255.79.216 |
| 172.255.79.217 |
| 172.255.79.225 |
| 172.255.79.233 |
| 172.255.79.239 |
| 172.255.79.238 |
| 172.255.79.241 |
| 172.255.79.243 |
| 172.255.79.246 |
| 172.255.79.250 |
| 173.208.92.14 |
| 173.208.92.21 |
| 173.208.92.2 |
| 173.208.92.19 |
| 173.208.92.3 |
| 173.208.92.37 |
| 173.208.92.48 |
| 173.208.92.52 |
| 173.208.92.58 |
| 173.208.92.9 |
| 173.208.92.8 |
| 203.27.106.141 |
| 223.72.73.238 |
| 212.115.53.28 |
| 36.112.138.181 |
| 42.81.61.13 |
| 45.83.64.135 |
| 45.83.64.154 |
| 45.83.64.168 |
| 45.83.64.178 |
| 45.83.64.180 |
| 45.83.64.201 |
| 45.83.64.63 |
| 45.83.64.78 |
| 45.83.65.10 |
| 45.83.65.121 |
| 45.83.65.111 |
| 45.83.65.13 |
| 45.83.65.157 |
| 45.83.65.188 |
| 45.83.65.192 |
| 45.83.65.207 |
| 45.83.65.249 |
| 45.83.65.242 |
| 45.83.65.254 |
| 45.83.65.49 |
| 45.83.65.95 |
| 45.83.66.105 |
| 45.83.66.158 |
| 45.83.66.224 |
| 45.83.66.51 |
| 45.83.67.100 |
| 45.83.67.112 |
| 45.83.67.153 |
| 45.83.67.146 |
| 45.83.67.156 |
| 45.83.67.191 |
| 45.83.67.205 |
| 45.83.67.196 |
| 45.83.67.245 |
| 45.83.67.3 |
| 45.83.67.30 |
| 45.83.67.4 |
| 45.83.67.45 |
| 45.83.67.44 |
| 92.242.40.21 |
| 171.25.193.20 |
| 178.17.171.102 |
| 171.25.193.25 |
| 1.14.17.89 |
| 103.103.0.141 |
| 103.103.0.142 |
| 104.244.72.7 |
| 104.244.73.93 |
| 104.244.75.74 |
| 104.244.76.13 |
| 107.189.1.178 |
| 107.189.31.241 |
| 109.70.100.34 |
| 121.4.56.143 |
| 137.184.28.58 |
| 142.93.151.166 |
| 147.182.167.165 |
| 147.182.215.36 |
| 152.89.239.12 |
| 154.94.7.88 |
| 159.65.3.102 |
| 161.35.119.60 |
| 159.65.58.66 |
| 162.142.125.42 |
| 162.142.125.195 |
| 162.142.125.58 |
| 162.247.74.201 |
| 162.247.74.206 |
| 162.247.74.27 |
| 167.248.133.114 |
| 167.248.133.115 |
| 167.248.133.41 |
| 166.70.207.2 |
| 167.248.133.59 |
| 167.71.13.196 |
| 167.94.138.114 |
| 167.94.138.115 |
| 167.94.138.44 |
| 167.99.172.213 |
| 175.6.210.66 |
| 178.62.79.49 |
| 185.107.47.215 |
| 185.129.61.1 |
| 185.107.70.56 |
| 185.130.44.108 |
| 185.220.100.240 |
| 185.220.100.244 |
| 185.220.100.249 |
| 185.220.100.250 |
| 185.220.100.255 |
| 185.220.100.253 |
| 185.220.101.129 |
| 185.220.101.14 |
| 185.220.101.147 |
| 185.220.101.155 |
| 185.220.101.168 |
| 185.220.101.180 |
| 185.220.101.19 |
| 185.220.101.191 |
| 185.220.101.32 |
| 185.220.101.33 |
| 185.220.101.36 |
| 185.220.101.42 |
| 185.220.101.46 |
| 185.220.101.54 |
| 185.220.102.253 |
| 185.220.102.254 |
| 185.220.102.4 |
| 185.38.175.130 |
| 185.56.80.65 |
| 191.232.38.25 |
| 192.42.116.19 |
| 193.189.100.195 |
| 193.189.100.203 |
| 193.218.118.231 |
| 194.48.199.78 |
| 195.251.41.139 |
| 195.206.105.217 |
| 199.249.230.158 |
| 205.185.115.45 |
| 209.141.45.227 |
| 212.47.237.67 |
| 23.183.83.71 |
| 23.154.177.7 |
| 3.94.114.30 |
| 31.42.186.101 |
| 45.137.184.31 |
| 45.153.160.134 |
| 45.153.160.138 |
| 46.173.218.146 |
| 5.2.70.140 |
| 72.223.168.73 |
| 81.17.18.61 |
| 87.118.110.27 |
| 138.68.250.214 |
| 139.59.101.242 |
| 147.182.216.21 |
| 159.89.122.19 |
| 165.232.80.22 |
| 165.227.32.109 |
| 167.99.172.99 |
| 174.138.6.128 |
| 188.166.105.150 |
| 188.166.86.206 |
| 167.99.44.32 |
| 159.65.59.77 |
| 147.182.242.241 |
| 147.182.242.144 |
| 110.42.200.96 |
| 104.248.144.120 |
| 103.107.198.109 |
| 101.204.24.28 |
| 188.166.170.135 |
| 182.99.247.253 |
| 182.99.247.67 |
| 178.62.61.47 |
| 195.54.160.149 |
| 109.70.100.19 |
| 109.201.133.100 |
| 112.215.172.64 |
| 114.32.82.82 |
| 156.146.57.41 |
| 164.90.199.212 |
| 183.134.110.75 |
| 185.129.61.5 |
| 185.202.220.27 |
| 185.175.25.50 |
| 185.220.102.248 |
| 185.236.200.118 |
| 185.245.86.85 |
| 185.65.205.10 |
| 192.145.118.127 |
| 195.144.21.219 |
| 195.133.40.15 |
| 185.250.148.157 |
| 93.189.42.8 |
| 45.146.164.160 |
| 103.104.73.155 |
| 3.26.198.32 |
| 185.117.118.15 |
| 209.97.147.103 |
| 194.163.44.188 |
| 68.183.45.190 |
| 185.191.32.198 |
| 40.64.92.159 |
| 52.200.111.193 |
| 52.232.211.160 |
| 52.232.211.166 |
| 52.232.211.167 |
| 52.95.72.73 |
| 172.245.14.50 |
| 45.83.64.1 |
| 146.70.75.53 |
| 139.28.218.133 |
| 139.28.218.132 |
| 117.192.11.154 |
| 116.89.189.19 |
| 104.200.138.39 |
| 91.207.173.119 |
| 212.102.50.87 |
| 203.27.106.142 |
| 185.245.86.86 |
| 185.202.220.109 |
| 182.99.246.187 |
| 182.99.246.106 |
| 37.120.158.20 |
| 23.82.194.168 |
| 5.181.235.45 |
| 5.135.141.139 |
| 35.170.71.122 |
| 5.101.145.41 |
| 172.255.78.136 |
| 172.255.78.143 |
| 172.255.78.145 |
| 172.255.78.149 |
| 172.255.78.152 |
| 172.255.78.153 |
| 172.255.78.156 |
| 172.255.78.161 |
| 172.255.78.163 |
| 172.255.78.165 |
| 172.255.78.173 |
| 172.255.78.177 |
| 172.255.78.187 |
| 172.255.78.186 |
| 172.255.78.190 |
| 172.255.79.194 |
| 172.255.79.204 |
| 172.255.79.212 |
| 172.255.79.214 |
| 172.255.79.215 |
| 172.255.79.218 |
| 172.255.79.222 |
| 172.255.79.224 |
| 172.255.79.226 |
| 172.255.79.232 |
| 172.255.79.236 |
| 172.255.79.237 |
| 172.255.79.244 |
| 172.255.79.252 |
| 173.208.92.18 |
| 173.208.92.15 |
| 173.208.92.20 |
| 173.208.92.22 |
| 173.208.92.25 |
| 173.208.92.29 |
| 173.208.92.30 |
| 173.208.92.35 |
| 173.208.92.33 |
| 173.208.92.4 |
| 173.208.92.38 |
| 173.208.92.41 |
| 173.208.92.50 |
| 173.208.92.61 |
| 45.83.64.128 |
| 45.83.64.131 |
| 45.83.64.194 |
| 45.83.64.205 |
| 45.83.64.211 |
| 45.83.64.24 |
| 45.83.64.238 |
| 45.83.64.61 |
| 45.83.64.70 |
| 45.83.64.72 |
| 45.83.64.77 |
| 45.83.64.93 |
| 45.83.65.115 |
| 45.83.65.135 |
| 45.83.65.174 |
| 45.83.65.160 |
| 45.83.65.176 |
| 45.83.65.196 |
| 45.83.65.222 |
| 45.83.65.212 |
| 45.83.65.47 |
| 45.83.65.54 |
| 45.83.65.67 |
| 45.83.65.78 |
| 45.83.65.77 |
| 45.83.66.1 |
| 45.83.66.43 |
| 45.83.66.91 |
| 45.83.67.104 |
| 45.83.67.114 |
| 45.83.67.160 |
| 45.83.67.174 |
| 45.83.67.206 |
| 45.83.67.242 |
| 45.83.67.248 |
| 45.83.67.25 |
| 45.83.67.253 |
| 45.83.67.26 |
| 45.83.67.55 |
| 45.83.67.91 |
| 45.83.67.95 |
| 60.247.159.170 |
| 107.172.214.23 |
| 45.130.229.168 |
| 185.220.101.146 |
| 171.25.193.77 |
| 104.244.79.6 |
| 1.116.59.211 |
| 103.214.5.13 |
| 104.244.73.126 |
| 104.244.73.43 |
| 104.244.74.211 |
| 104.244.74.55 |
| 104.244.76.170 |
| 107.189.12.135 |
| 107.189.14.98 |
| 109.70.100.23 |
| 109.70.100.31 |
| 109.70.100.26 |
| 109.70.100.36 |
| 133.18.201.195 |
| 137.184.102.82 |
| 137.184.104.73 |
| 137.184.99.8 |
| 142.93.34.250 |
| 146.56.131.161 |
| 147.182.131.229 |
| 147.182.198.103 |
| 154.39.255.195 |
| 167.248.133.113 |
| 167.248.133.57 |
| 167.248.133.58 |
| 167.94.138.116 |
| 167.94.138.41 |
| 167.94.138.59 |
| 170.210.45.163 |
| 176.10.99.200 |
| 180.149.231.245 |
| 185.165.169.18 |
| 185.220.100.248 |
| 185.220.100.251 |
| 185.220.101.10 |
| 185.220.101.131 |
| 185.220.101.148 |
| 185.220.101.149 |
| 185.220.101.153 |
| 185.220.101.154 |
| 185.220.101.16 |
| 185.220.101.165 |
| 185.220.101.164 |
| 185.220.101.169 |
| 185.220.101.175 |
| 185.220.101.176 |
| 185.220.101.178 |
| 185.220.101.182 |
| 185.220.101.185 |
| 185.220.101.187 |
| 185.220.101.189 |
| 185.220.101.190 |
| 185.220.101.21 |
| 185.220.101.37 |
| 185.220.101.44 |
| 185.220.101.45 |
| 185.220.101.47 |
| 185.220.101.51 |
| 185.220.101.55 |
| 185.220.101.63 |
| 185.220.102.242 |
| 185.220.102.249 |
| 185.236.200.117 |
| 185.83.214.69 |
| 188.166.92.228 |
| 193.239.232.102 |
| 194.163.45.31 |
| 197.246.171.83 |
| 198.98.57.207 |
| 198.96.155.3 |
| 209.141.36.206 |
| 212.109.197.1 |
| 212.192.216.30 |
| 213.61.215.54 |
| 23.120.182.121 |
| 37.19.212.104 |
| 45.15.16.70 |
| 5.183.209.217 |
| 51.15.59.15 |
| 51.75.161.78 |
| 92.223.89.187 |
| 128.199.15.215 |
| 138.197.108.154 |
| 138.197.216.230 |
| 139.59.163.74 |
| 159.203.45.181 |
| 159.89.115.238 |
| 159.89.150.150 |
| 161.35.155.230 |
| 165.232.80.166 |
| 167.172.94.250 |
| 167.99.186.227 |
| 167.99.36.245 |
| 188.166.45.93 |
| 165.22.213.246 |
| 144.48.37.78 |
| 120.211.140.116 |
| 113.141.64.14 |
| 111.28.189.51 |
| 188.166.7.245 |
| 182.99.247.188 |
| 182.99.246.199 |
| 177.131.174.12 |
| 122.161.53.44 |
| 141.98.83.139 |
| 104.244.79.234 |
| 112.74.52.90 |
| 115.151.228.235 |
| 119.84.170.84 |
| 128.199.48.147 |
| 146.70.38.48 |
| 157.245.108.125 |
| 159.223.75.133 |
| 162.253.71.51 |
| 167.71.218.228 |
| 182.99.246.192 |
| 185.220.103.120 |
| 192.145.118.111 |
| 192.145.118.177 |
| 193.29.60.202 |
| 194.110.84.182 |
| 185.233.100.23 |
| 142.93.36.237 |
| 119.28.91.153 |
| 107.189.28.84 |
| 82.118.18.201 |
| 40.64.92.157 |
| 165.227.239.108 |
| 160.238.38.212 |
| 139.28.219.109 |
| 116.62.20.122 |
| 115.151.229.16 |
| 115.151.229.14 |
| 115.151.228.92 |
| 111.193.180.158 |
| 103.107.198.108 |
| 101.71.37.219 |
| 42.98.70.127 |
| 37.120.158.22 |
| 213.152.188.4 |
| 213.203.177.219 |
| 210.217.18.76 |
| 203.27.106.165 |
| 185.245.87.245 |
| 185.245.86.84 |
| 182.99.246.141 |
| 180.149.231.196 |
| 167.99.251.87 |
| 18.116.198.193 |
| 172.255.242.116 |
| 172.255.242.120 |
| 172.255.242.125 |
| 172.255.242.69 |
| 172.255.242.72 |
| 172.255.242.93 |
| 172.255.242.95 |
| 172.255.78.130 |
| 172.255.78.131 |
| 172.255.78.139 |
| 172.255.78.142 |
| 172.255.78.167 |
| 172.255.78.175 |
| 172.255.78.181 |
| 172.255.78.184 |
| 172.255.78.185 |
| 172.255.79.206 |
| 172.255.79.203 |
| 172.255.79.209 |
| 172.255.79.211 |
| 172.255.79.213 |
| 172.255.79.220 |
| 172.255.79.228 |
| 172.255.79.229 |
| 172.255.79.230 |
| 172.255.79.234 |
| 172.255.79.242 |
| 172.255.79.248 |
| 173.208.92.10 |
| 173.208.92.11 |
| 173.208.92.12 |
| 173.208.92.23 |
| 173.208.92.24 |
| 173.208.92.34 |
| 173.208.92.42 |
| 173.208.92.55 |
| 173.208.92.57 |
| 37.120.204.140 |
| 45.83.64.112 |
| 45.83.64.111 |
| 45.83.64.138 |
| 45.83.64.214 |
| 45.83.64.221 |
| 45.83.64.245 |
| 45.83.64.247 |
| 45.83.64.250 |
| 45.83.64.32 |
| 45.83.64.39 |
| 45.83.64.47 |
| 45.83.64.57 |
| 45.83.64.75 |
| 45.83.64.90 |
| 45.83.65.154 |
| 45.83.65.20 |
| 45.83.65.50 |
| 45.83.65.59 |
| 45.83.65.6 |
| 45.83.66.119 |
| 45.83.66.13 |
| 45.83.66.141 |
| 45.83.66.206 |
| 45.83.66.212 |
| 45.83.66.201 |
| 45.83.66.226 |
| 45.83.66.52 |
| 45.83.66.7 |
| 45.83.66.71 |
| 45.83.67.117 |
| 45.83.67.119 |
| 45.83.67.154 |
| 45.83.67.170 |
| 45.83.67.186 |
| 45.83.67.221 |
| 45.83.67.238 |
| 45.83.67.247 |
| 45.83.67.251 |
| 45.83.67.47 |
| 45.83.67.52 |
| 94.61.25.201 |
| 80.71.158.44 |
| 185.220.101.39 |
| 171.25.193.78 |
| 104.244.77.139 |
| 107.189.1.160 |
| 107.189.10.143 |
| 107.189.13.143 |
| 107.189.14.182 |
| 107.189.29.107 |
| 107.189.8.65 |
| 109.70.100.27 |
| 121.5.219.20 |
| 139.59.8.39 |
| 145.220.24.19 |
| 147.182.169.254 |
| 150.158.189.96 |
| 151.80.148.159 |
| 157.245.109.75 |
| 159.203.8.145 |
| 162.142.125.44 |
| 162.142.125.59 |
| 162.255.202.246 |
| 163.172.213.212 |
| 167.248.133.43 |
| 167.94.138.113 |
| 167.94.138.42 |
| 167.94.138.57 |
| 172.106.17.218 |
| 178.17.174.14 |
| 179.43.187.138 |
| 185.100.86.128 |
| 185.100.87.174 |
| 185.14.97.147 |
| 185.220.100.241 |
| 185.220.100.245 |
| 185.220.101.134 |
| 185.220.101.135 |
| 185.220.101.136 |
| 185.220.101.150 |
| 185.220.101.151 |
| 185.220.101.157 |
| 185.220.101.163 |
| 185.220.101.173 |
| 185.220.101.179 |
| 185.220.101.186 |
| 185.220.101.188 |
| 185.220.101.35 |
| 185.220.101.53 |
| 185.220.101.62 |
| 185.220.101.7 |
| 185.220.102.246 |
| 185.220.102.252 |
| 185.220.102.7 |
| 185.220.103.117 |
| 185.220.103.7 |
| 185.220.103.8 |
| 185.38.175.131 |
| 185.4.132.183 |
| 188.166.223.38 |
| 188.120.246.215 |
| 188.166.74.97 |
| 188.166.48.55 |
| 192.81.130.207 |
| 193.189.100.196 |
| 193.189.100.201 |
| 195.176.3.24 |
| 195.254.135.76 |
| 198.98.57.191 |
| 205.185.127.35 |
| 209.141.49.232 |
| 23.129.64.148 |
| 23.160.193.176 |
| 31.42.184.34 |
| 37.228.129.109 |
| 45.13.104.179 |
| 45.153.160.136 |
| 45.61.186.225 |
| 51.15.180.36 |
| 51.255.106.85 |
| 79.146.170.248 |
| 89.163.252.230 |
| 89.163.252.30 |
| 91.219.237.21 |
| 95.214.54.97 |
| 137.184.98.176 |
| 138.197.167.229 |
| 139.59.103.254 |
| 139.59.188.119 |
| 143.198.180.150 |
| 143.110.221.219 |
| 159.203.187.141 |
| 159.223.42.182 |
| 159.203.58.73 |
| 159.89.133.216 |
| 159.89.146.147 |
| 159.89.154.102 |
| 159.89.154.185 |
| 159.89.154.77 |
| 159.89.154.64 |
| 161.35.156.13 |
| 165.232.84.226 |
| 167.99.204.151 |
| 178.128.226.212 |
| 188.166.76.204 |
| 167.71.1.144 |
| 164.52.53.163 |
| 139.28.218.134 |
| 113.98.224.68 |
| 177.185.117.129 |
| 171.221.235.43 |
| 137.184.96.216 |
| 103.232.136.12 |
| 103.244.80.194 |
| 107.189.7.88 |
| 109.73.65.32 |
| 115.151.228.4 |
| 164.90.199.206 |
| 164.90.200.6 |
| 165.22.210.174 |
| 167.172.65.15 |
| 167.172.85.73 |
| 167.86.70.252 |
| 172.98.66.221 |
| 180.149.125.139 |
| 182.99.246.166 |
| 182.99.246.190 |
| 183.13.106.232 |
| 185.202.220.29 |
| 185.207.249.87 |
| 185.245.87.246 |
| 194.110.84.243 |
| 185.154.53.140 |
| 139.59.175.247 |
| 45.83.193.150 |
| 194.59.165.21 |
| 5.2.69.50 |
| 159.65.189.107 |
| 81.6.43.167 |
| 89.163.243.88 |
| 133.130.120.176 |
| 172.105.42.5 |
| 173.234.27.143 |
| 18.64.115.100 |
| 185.244.214.217 |
| 40.64.92.158 |
| 92.151.52.150 |
| 134.209.163.248 |
| 160.238.38.207 |
| 147.135.6.221 |
| 146.59.45.142 |
| 121.5.113.11 |
| 89.40.183.205 |
| 84.17.42.118 |
| 78.110.164.45 |
| 42.193.8.97 |
| 42.192.17.155 |
| 37.120.203.182 |
| 37.120.199.196 |
| 194.163.163.20 |
| 193.32.210.182 |
| 185.218.127.47 |
| 182.99.247.145 |
| 182.99.246.179 |
| 178.239.167.180 |
| 172.107.194.186 |
| 5.101.145.43 |
| 185.165.168.77 |
| 159.89.113.255 |
| 134.56.204.191 |
| 178.17.171.150 |
2. 远控/恶意软件类情报:表示漏洞利用的攻击载荷(Payload)中所包含的,被攻击者用于漏洞利用成功后回连通信或验证的相关资产,建议结合流量或终端日志及相关工具进行排查处置。
| Domain | bvprzqhoz7j2ltin.onion.ws |
| Domain | agent.apacheorg.top |
| Domain | resolv.network |
| Domain | 300gsyn.it |
| Domain | kryptoslogic-cve-2021-44228.com |
| Domain | log.exposedbotnets.ru |
| Domain | li466-34.members.linode.com |
| Domain | wdnmdnmsl.xyz |
| Domain | haibara.cyou |
| Domain | bvprzqhoz7j2ltin.tor2web.su |
| Domain | nmsl.run |
| Domain | viperdns.xyz |
| Domain | nazi.uy |
| Domain | cwj.bslab.xyz |
| Domain | exposedbotnets.ru |
| IP | 159.223.106.56 |
| IP | 164.52.212.196 |
| IP | 163.172.157.143 |
| IP | 167.172.44.255 |
| IP | 45.137.155.55 |
| IP | 67.205.191.102 |
| IP | 194.163.133.36 |
| IP | 139.162.20.98 |
| IP | 205.185.115.217 |
| IP | 3.85.59.114 |
| IP | 146.112.61.110 |
| IP | 193.3.19.159 |
| IP | 154.82.110.5 |
| IP | 80.71.158.12 |
| IP | 18.228.7.109 |
| IP | 159.89.182.117 |
| IP | 172.105.241.146 |
| IP | 162.55.90.26 |
| IP | 5.255.97.172 |
| IP | 66.23.227.195 |
| IP | 45.76.99.222 |
| IP | 205.185.113.59 |
| IP | 129.226.180.53 |
| IP | 170.178.196.41 |
| IP | 141.98.83.139 |
| IP | 157.230.189.52 |
| IP | 45.155.205.233 |
| IP | 45.130.229.168 |
| IP | 195.19.192.28 |
| IP | 185.165.171.78 |
| IP | 210.141.105.67 |
| IP | 138.197.206.223 |
| IP | 141.105.65.94 |
| IP | 185.244.158.212 |
| IP | 134.209.163.248 |
| IP | 81.30.157.43 |
| IP | 80.71.158.44 |
| IP | 139.59.175.247 |
| IP | 31.220.58.29 |
| IP | 79.172.214.11 |
| IP | 155.94.154.170 |
| IP | 54.210.230.186 |
| IP | 47.243.78.246 |
| IP | 114.132.231.19 |
| IP | 131.153.4.122 |
| IP | 109.237.96.124 |
| IP | 62.182.158.156 |
| IP | 195.54.160.149 |
| IP | 92.242.40.21 |
| IP | 45.146.164.160 |
| IP | 93.189.42.8 |
| IP | 185.250.148.157 |
| IP | 135.125.217.87 |
| IP | 121.41.109.54 |
| IP | 89.234.182.139 |
| IP | 110.42.239.3 |
| IP | 62.76.41.46 |
| IP | 34.221.40.237 |
| URL | 92.242.40.21/lh2.sh |
| URL | 80.71.158.44/lh.sh |
| URL | 80.71.158.12/kinsing |
| URL | 195.19.192.28/kinsing |
| URL | 18.228.7.109/.log/log |
| URL | 62.210.130.250/lh.sh |
| URL | 62.210.130.250/web/admin/x86_64 |
| URL | 62.210.130.250/web/admin/x86_g |
| URL | 62.210.130.250/web/admin/x86 |
| URL | 18.228.7.109/.log/pty2 |
| URL | 18.228.7.109/.log/pty4 |
| URL | 18.228.7.109/.log/pty5 |
| URL | 210.141.105.67:80/wp-content/themes/twentythirteen/m8 |
| URL | 34.221.40.237/.x/pty10 |
| URL | 138.197.206.223/.x/xmra64 |
| URL | 34.221.40.237/.x/pty3 |
| URL | 34.221.40.237/.x/pty2 |
| URL | 34.221.40.237/.x/pty11 |
| URL | 18.228.7.109/.log/pty1 |
| URL | 34.221.40.237/.x/pty4 |
| URL | 34.221.40.237/.x/pty5 |
| URL | 164.52.212.196/logback.exe |
| URL | 185.191.32.198/lh.sh |
| URL | 92.242.40.21/lh.sh |
| URL | 45.130.229.168:9999/Exploit.class |
| URL | 18.228.7.109/.log/pty3 |
| URL | 159.89.182.117/wp-content/themes/twentyseventeen/ldm |
| URL | 34.221.40.237/.x/pty1 |
检测规则披露
1. Snort检测规则
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http ldap) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldap|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034647; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http rmi) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|rmi|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034648; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp ldap) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldap|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034649; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp rmi) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|rmi|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034650; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp rmi) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|rmi|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034652; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp ldap) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|ldap|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034651; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp dns) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|dns|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034653; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp dns) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|dns|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034654; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http dns) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|dns|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034655; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp ldaps) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|ldaps|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034656; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp ldaps) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldaps|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034657; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http ldaps) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldaps|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034658; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - lower/upper TCP Bypass (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|"; nocase; fast_pattern; pcre:"/^(l|r|d|${(lower|upper):(l|r|d)})(d|n|m|${(lower|upper):(d|n|m)})(a|i|s|${(lower|upper):(a|i|s)})(p|${(lower|upper):(p)})/Ri"; content:"|3a 2f 2f|"; distance:0; reference:cve,2021-44228; classtype:attempted-admin; sid:2034659; rev:1; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_11;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - lower/upper UDP Bypass (CVE-2021-44228)"; content:"|24 7b|jndi|3a|"; nocase; fast_pattern; pcre:"/^(l|r|d|${(lower|upper):(l|r|d)})(d|n|m|${(lower|upper):(d|n|m)})(a|i|s|${(lower|upper):(a|i|s)})(p|${(lower|upper):(p)})/Ri"; content:"|3a 2f 2f|"; distance:0; reference:cve,2021-44228; classtype:attempted-admin; sid:2034660; rev:2; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_11;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp iiop) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|iiop|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034667; rev:2; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_11;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp iiop) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|iiop|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034668; rev:2; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_11;) |
| alert udp $HOME_NET any -> any 53 (msg:"ET POLICY dnslog .cn Observed in DNS Query"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|06|dnslog|02|cn|00|"; nocase; distance:0; fast_pattern; classtype:trojan-activity; sid:2034669; rev:2; metadata:attack_target Client_Endpoint, created_at 2021_12_11, deployment Perimeter, deployment Internal, performance_impact Low, signature_severity Informational, updated_at 2021_12_11;) |
| alert udp $HOME_NET any -> any 53 (msg:"ET ATTACK_RESPONSE DNS Query for Observed CVE-2121-44228 Payload Domain"; content:"|01|"; offset:2; depth:1; content:"|00 01 00 00 00 00 00|"; distance:1; within:7; content:"|0d|bingsearchlib|03|com|00|"; nocase; distance:0; fast_pattern; reference:url,twitter.com/sans_isc/status/1469305954835521539; reference:cve,2121-44228; classtype:trojan-activity; sid:2034670; rev:2; metadata:attack_target Client_and_Server, created_at 2021_12_11, cve CVE_2121_44228, deployment Perimeter, performance_impact Low, signature_severity Major, updated_at 2021_12_11;) |
2. Suricata规则
| alert tcp $EXTERNAL_NET any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET ATTACK_RESPONSE Possible CVE-2021-44228 Payload via LDAPv3 Response"; flow:established,to_client; content:"|30 81|"; startswith; content:"|02 01|"; distance:1; within:2; content:"|64|"; distance:1; within:1; content:"|04|"; distance:2; within:1; byte_jump:1,0,relative; content:"|04 0d|javaClassName"; within:20; fast_pattern; content:"|04|"; distance:2; within:1; byte_jump:1,0,relative; content:"|04 0c|javaCodeBase"; within:19; content:"|04|"; distance:2; within:1; byte_jump:1,0,relative; content:"|04 0b|objectClass"; within:18; content:"|04|"; distance:2; within:1; byte_jump:1,0,relative; content:"|04 0b|javaFactory"; within:18; reference:url,ldap.com/ldapv3-wire-protocol-reference-ldap-result/; reference:url,ldapv3-wire-protocol-reference-search/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034722; rev:1; metadata:attack_target Client_and_Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, former_category ATTACK_RESPONSE, signature_severity Major, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - Nested lower (tcp) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b 24 7b|lower|3a 24 7b|lower|3a|jndi"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034706; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - Nested lower (udp) (CVE-2021-44228)"; content:"|24 7b 24 7b|lower|3a 24 7b|lower|3a|jndi"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034707; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - Nested upper (tcp) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b 24 7b|upper|3a 24 7b|upper|3a|jndi"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034708; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - Nested upper (udp) (CVE-2021-44228)"; content:"|24 7b 24 7b|upper|3a 24 7b|upper|3a|jndi"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034709; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt (tcp nis) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|nis|3a|"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034710; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt (udp nis) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|nis|3a|"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034711; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt (tcp nds) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|nds|3a|"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034712; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt (udp nds) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|nds|3a|"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034713; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt (tcp corba) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|corba|3a|"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034714; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt (udp corba) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|corba|3a|"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034715; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt - Base64 jndi (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|base64|3a|JHtqbmRp"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034716; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt - Base64 jndi (CVE-2021-44228)"; content:"|24 7b|base64|3a|JHtqbmRp"; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034717; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - lower/upper TCP Bypass M1 (CVE-2021-44228)"; flow:established,to_server; content:"%7bjndi%3a"; nocase; fast_pattern; pcre:"/^(l|r|d|($|%24)({|%7b)(lower|upper)(:|%3a)(l|r|d)(}|%7d))(d|n|m|($|%24)({|%24)(lower|upper)(:|%3a)(d|n|m)(}|%7d))(a|i|s|($|%24)({|%7b)(lower|upper)(:|%3a)(a|i|s)(}|%7d))(p|($|%24)({|%7b)(lower|upper)(:|%3a)p(}|%7d))/Ri"; reference:cve,2021-44228; classtype:attempted-admin; sid:2034659; rev:2; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - lower/upper UDP Bypass M1 (CVE-2021-44228)"; content:"%7bjndi%3a"; nocase; fast_pattern; pcre:"/^(l|r|d|($|%24)({|%7b)(lower|upper)(:|%3a)(l|r|d)(}|%7d))(d|n|m|($|%24)({|%7b)(lower|upper)(:|%3a)(d|n|m)(}|%7d))(a|i|s|($|%24)({|%7b)(lower|upper)(:|%3a)(a|i|s)(}|%7d))(p|($|%24)({|%7b)(lower|upper)(:|%3a)p(}|%7d))/Ri"; reference:cve,2021-44228; classtype:attempted-admin; sid:2034660; rev:3; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - lower/upper TCP Bypass M2 (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|"; nocase; fast_pattern; pcre:"/^(l|r|d|${(lower|upper):(l|r|d)})(d|n|m|${(lower|upper):(d|n|m)})(a|i|s|${(lower|upper):(a|i|s)})(p|${(lower|upper):(p)})/Ri"; content:"|3a 2f 2f|"; distance:0; reference:cve,2021-44228; classtype:attempted-admin; sid:2034700; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - lower/upper UDP Bypass M2 (CVE-2021-44228)"; content:"|24 7b|jndi|3a|"; nocase; fast_pattern; pcre:"/^(l|r|d|${(lower|upper):(l|r|d)})(d|n|m|${(lower|upper):(d|n|m)})(a|i|s|${(lower|upper):(a|i|s)})(p|${(lower|upper):(p)})/Ri"; content:"|3a 2f 2f|"; distance:0; reference:cve,2021-44228; classtype:attempted-admin; sid:2034701; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt - AWS Access Key Disclosure (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|"; pcre:"/^(j|${(lower|upper):j}|${::-j})(n|${(lower|upper):n}|${::-n})/Ri"; content:"|3a|"; distance:0; content:"|24 7b|env|3a|AWS_ACCESS_KEY_ID"; distance:0; reference:cve,2021-44228; classtype:attempted-admin; sid:2034699; rev:1; metadata:attack_target Server, created_at 2021_12_14, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_14;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt - 2021/12/13 Obfuscation Observed (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|"; pcre:"/^(j|${(lower|upper):j}|${::-j})(n|${(lower|upper):n}|${::-n})/Ri"; content:"|3a|"; distance:0; content:"|24 7b|env|3a|"; distance:0; reference:cve,2021-44228; classtype:attempted-admin; sid:2034676; rev:1; metadata:attack_target Server, created_at 2021_12_13, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_13;) |
| alert dns $HOME_NET any -> any any (msg:"ET ATTACK_RESPONSE DNS Query for Observed CVE-2021-44228 Payload Domain"; dns.query; dotprefix; content:".bingsearchlib.com"; nocase; endswith; reference:url,twitter.com/sans_isc/status/1469305954835521539; reference:cve,2021-44228; classtype:domain-c2; sid:2034670; rev:1; metadata:attack_target Client_and_Server, created_at 2021_12_11, cve CVE_2121_44228, deployment Perimeter, former_category ATTACK_RESPONSE, performance_impact Low, signature_severity Major, updated_at 2021_12_11;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt - 2021/12/12 Obfuscation Observed M2 (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|"; content:"|24 7b 3a 3a|"; distance:0; within:300; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034673; rev:1; metadata:attack_target Server, created_at 2021_12_12, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_12;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Possible Apache log4j RCE Attempt - 2021/12/12 Obfuscation Observed M2 (CVE-2021-44228)"; content:"|24 7b|"; content:"|24 7b 3a 3a|"; distance:0; within:300; fast_pattern; reference:cve,2021-44228; classtype:attempted-admin; sid:2034674; rev:1; metadata:attack_target Server, created_at 2021_12_12, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_12;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp iiop) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|iiop|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034667; rev:2; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_11;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp iiop) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|iiop|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034668; rev:2; metadata:attack_target Server, created_at 2021_12_11, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_11;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp rmi) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|rmi|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034650; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp rmi) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|rmi|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034652; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp ldap) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|ldap|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034651; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp dns) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|dns|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034653; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp dns) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|dns|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034654; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert http any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http dns) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|dns|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034655; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert udp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (udp ldaps) (CVE-2021-44228)"; content:"|24 7b|jndi|3a|ldaps|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034656; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp ldaps) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldaps|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034657; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert http any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http ldaps) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldaps|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034658; rev:2; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert http any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http ldap) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldap|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034647; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert http any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (http rmi) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|rmi|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034648; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
| alert tcp any any -> [$HOME_NET,$HTTP_SERVERS] any (msg:"ET EXPLOIT Apache log4j RCE Attempt (tcp ldap) (CVE-2021-44228)"; flow:established,to_server; content:"|24 7b|jndi|3a|ldap|3a 2f 2f|"; nocase; fast_pattern; reference:url,lunasec.io/docs/blog/log4j-zero-day/; reference:cve,2021-44228; classtype:attempted-admin; sid:2034649; rev:1; metadata:attack_target Server, created_at 2021_12_10, cve CVE_2021_44228, deployment Perimeter, deployment Internal, former_category EXPLOIT, signature_severity Major, tag Exploit, updated_at 2021_12_10;) |
系列漏洞分析
一、 时间线概览
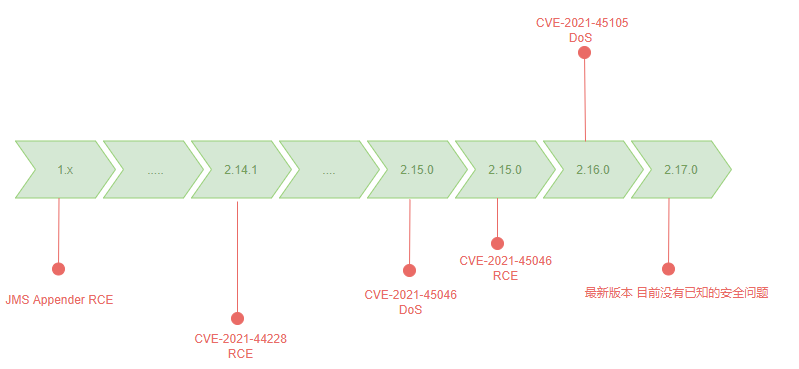
二、 时间线详情分析
- Log4j1.x
相关分析报告:震惊!Log4j1.x也能被利用吗?
漏洞概述:造成该漏洞的功能点是 Log4j 提供的 JMS Appender 功能,该功能允许用户将日志信息发送给 JMS broker。该漏洞的触发条件较为苛刻,需要开启JMS Appender功能和Log4j配置文件可控。
修复方案:由于Log4j已经停止维护了,所以最好的修复方式是尽快升级到2.17.0。但如果升级存在困难,可以自查是否开启了JMS Appender功能,如果开启,请尽快关闭该功能。
- < Log4j2.15.0
相关分析报告:起床!史诗级Log4j漏洞已引起大规模入侵,猛击查看快速检测技巧
相关修复方式:https://mp.weixin.qq.com/s/IM6ye8FtQgjcmTvDZHfyOw
相关检测方式:快速远程批量检测Log4j2互联网暴露面
漏洞概述:此次漏洞是用于 Log4j2 提供的 lookup 功能造成的,该功能允许开发者通过一些协议去读取相应环境中的配置。但在实现的过程中,并未对输入进行严格的判断,从而造成漏洞的发生。
修复方式:
i. 代码中设置属性:System.setProperty("log4j2.formatMsgNoLookups","True");
ii. 设置JVM启动参数:-Dlog4j2.formatMsgNoLookups=True
iii. 在应用程序的 classpath 下添加 log4j2.component.properties 配置文件,文件内容为: log4j2.formatMsgNoLookups=True
iv. 设置系统环境变量:LOG4J_formatMsgNoLookups=True
上述的修复方案只是针对JNDI lookup的修复。
检测方案:https://x.threatbook.cn/v5/feature_vul/apache_log4j2
- Log4j2.15.0
相关分析报告:https://mp.weixin.qq.com/s/5Zs7SONUSpLQokkDQFNdOw
漏洞概述:该漏洞分为两个部分,一个是上面提到的JNDI lookup功能修复的绕过,另一个部分是对IP和协议限制的绕过。在Log4j2.15.0的修复中增加了对IP地址和协议的限制,所以在刚开始的时候,官方将该CVE定位为拒绝服务攻击。但随着安全人员进一步的研究,提出了bypass的方法,并将其报告给官方后,随即官方更改了该CVE为远程代码执行。与此同时,网上还存在一些说法,称该漏洞为信息泄露,但所谓的信息泄露只是可以通过该漏洞配合着dnslog的带外注入来获取环境变量等敏感信息。
修复方案:升级到Log4j2.17.0
- <=Log4j2.16.0
相关分析报告:警惕!Log4j 2.16 已失守!漏洞详情曝光
漏洞概述:该漏洞是由于StrSubstitutor.java中的substitute函数递归解析数据造成的,当攻击者构造恶意的payload传入时,该解析函数会抛出异常,从而导致拒绝服务攻击。
修复方案:升级到Log4j2.17.0






















 2530
2530











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








