闪讯拨号用户名核心算法
暑假开学回来后一直闲的无聊没事干,看到有人发的闪讯的路由器版本的插件,这个插件基于Pandora,去网上搜了搜发现了这个插件的源码https://github.com/miao1007/Openwrt-NetKeeper,于是赶紧下过来看看,这位大神是把闪讯APP用JAVA反编译得到用户名算法,于是我萌生了一个想法做一个Windows版的闪讯,不过他代码是Linux的不适用于Windows,于是我准备做一下移植。
用户名算法不算很复杂,主算法在\src\sxplugin.c中,附加的一部分在\src\md5.h,算法流程图如下
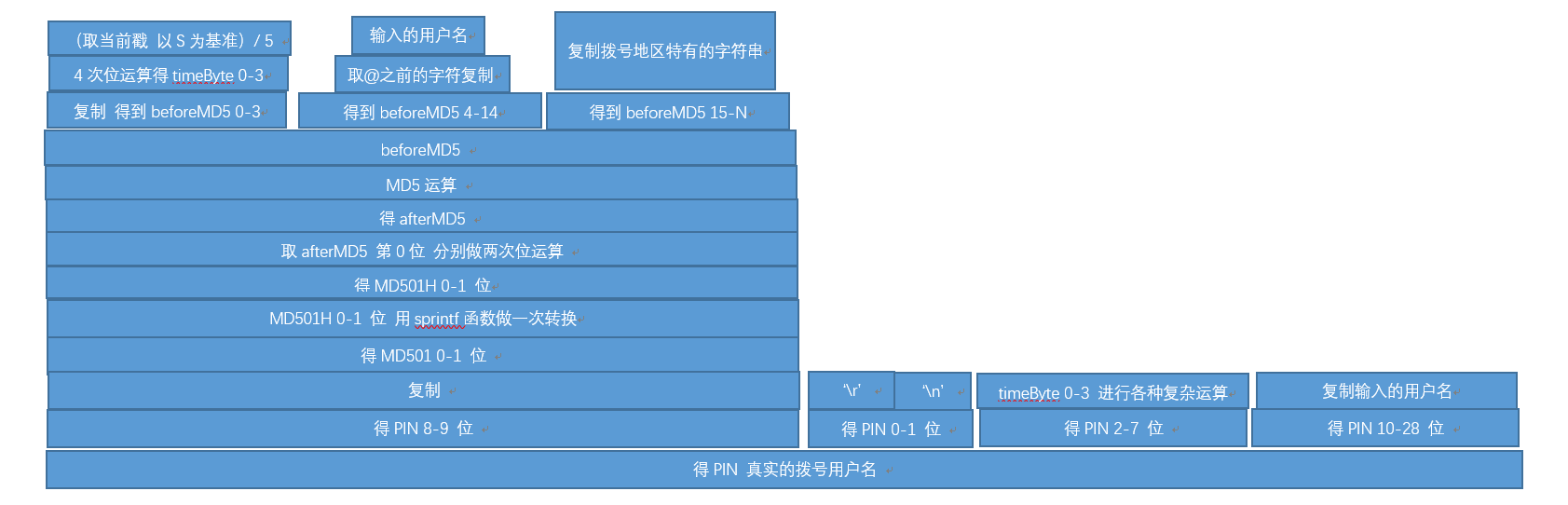
多说一下:对于这个算法中的PIN的2-9位数据貌似是可以乱填的,只是要多连几次就能连上,因为好多路由器断电是不能走时间的,用树莓派刷路由器版本,晚上寝室断电,第二天开机系统是昨晚的时间,系统日志显示连了3 4次后连上了,可见时间戳并不是很重要,大家可以去试试。
md5.h文件主要是定义了MD5算法中用到的一些参数类型,直接拿走即可。在这个算法中他的时间戳除以了5,也就是说你的真实用户名过5S就变一个,闪讯最坑的是真实用户名的0-1位字符,我相信许多人知道真实用户名都想用CMD手动拨号了,但正是这两位字符,你无论如何用手动的方法都拨不出去。
附上C的源代码
typedef unsigned long UINT4;
typedef long INT4;
#define _UINT4_T
typedef struct {
UINT4 i[2]; /* number of _bits_ handled mod 2^64 */
UINT4 buf[4]; /* scratch buffer */
unsigned char in[64]; /* input buffer */
unsigned char digest[16]; /* actual digest after MD5Final call */
} MD5_CTX;
typedef unsigned char byte;
static void Transform(UINT4 *buf, UINT4 *in);
static unsigned char PADDING[64] = {
0x80, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00
};
/* F, G, H and I are basic MD5 functions */
#define F(x, y, z) (((x) & (y)) | ((~x) & (z)))
#define G(x, y, z) (((x) & (z)) | ((y) & (~z)))
#define H(x, y, z) ((x) ^ (y) ^ (z))
#define I(x, y, z) ((y) ^ ((x) | (~z)))
/* ROTATE_LEFT rotates x left n bits */
#define ROTATE_LEFT(x, n) (((x) << (n)) | ((x) >> (32-(n))))
/* FF, GG, HH, and II transformations for rounds 1, 2, 3, and 4 */
/* Rotation is separate from addition to prevent recomputation */
#define FF(a, b, c, d, x, s, ac) \
{(a) += F ((b), (c), (d)) + (x) + (UINT4)(ac); \
(a) = ROTATE_LEFT ((a), (s)); \
(a) += (b); \
}
#define GG(a, b, c, d, x, s, ac) \
{(a) += G ((b), (c), (d)) + (x) + (UINT4)(ac); \
(a) = ROTATE_LEFT ((a), (s)); \
(a) += (b); \
}
#define HH(a, b, c, d, x, s, ac) \
{(a) += H ((b), (c), (d)) + (x) + (UINT4)(ac); \
(a) = ROTATE_LEFT ((a), (s)); \
(a) += (b); \
}
#define II(a, b, c, d, x, s, ac) \
{(a) += I ((b), (c), (d)) + (x) + (UINT4)(ac); \
(a) = ROTATE_LEFT ((a), (s)); \
(a) += (b); \
}
#ifdef __STDC__
#define UL(x) x##U
#else
#define UL(x) x
#endif
/* The routine MD5_Init initializes the message-digest context
mdContext. All fields are set to zero.
*/
void MD5_Init(MD5_CTX *mdContext)
{
mdContext->i[0] = mdContext->i[1] = (UINT4)0;
/* Load magic initialization constants.
*/
mdContext->buf[0] = (UINT4)0x67452301;
mdContext->buf[1] = (UINT4)0xefcdab89;
mdContext->buf[2] = (UINT4)0x98badcfe;
mdContext->buf[3] = (UINT4)0x10325476;
}
/* The routine MD5Update updates the message-digest context to
account for the presence of each of the characters inBuf[0..inLen-1]
in the message whose digest is being computed.
*/
void MD5_Update(MD5_CTX *mdContext, unsigned char *inBuf, unsigned int inLen)
{
UINT4 in[16];
int mdi;
unsigned int i, ii;
/* compute number of bytes mod 64 */
mdi = (int)((mdContext->i[0] >> 3) & 0x3F);
/* update number of bits */
if ((mdContext->i[0] + ((UINT4)inLen << 3)) < mdContext->i[0])
mdContext->i[1]++;
mdContext->i[0] += ((UINT4)inLen << 3);
mdContext->i[1] += ((UINT4)inLen >> 29);
while (inLen--) {
/* add new character to buffer, increment mdi */
mdContext->in[mdi++] = *inBuf++;
/* transform if necessary */
if (mdi == 0x40) {
for (i = 0, ii = 0; i < 16; i++, ii += 4)
in[i] = (((UINT4)mdContext->in[ii + 3]) << 24) |
(((UINT4)mdContext->in[ii + 2]) << 16) |
(((UINT4)mdContext->in[ii + 1]) << 8) |
((UINT4)mdContext->in[ii]);
Transform(mdContext->buf, in);
mdi = 0;
}
}
}
/* The routine MD5Final terminates the message-digest computation and
ends with the desired message digest in mdContext->digest[0...15].
*/
void MD5_Final(unsigned char hash[], MD5_CTX *mdContext)
{
UINT4 in[16];
int mdi;
unsigned int i, ii;
unsigned int padLen;
/* save number of bits */
in[14] = mdContext->i[0];
in[15] = mdContext->i[1];
/* compute number of bytes mod 64 */
mdi = (int)((mdContext->i[0] >> 3) & 0x3F);
/* pad out to 56 mod 64 */
padLen = (mdi < 56) ? (56 - mdi) : (120 - mdi);
MD5_Update(mdContext, PADDING, padLen);
/* append length in bits and transform */
for (i = 0, ii = 0; i < 14; i++, ii += 4)
in[i] = (((UINT4)mdContext->in[ii + 3]) << 24) |
(((UINT4)mdContext->in[ii + 2]) << 16) |
(((UINT4)mdContext->in[ii + 1]) << 8) |
((UINT4)mdContext->in[ii]);
Transform(mdContext->buf, in);
/* store buffer in digest */
for (i = 0, ii = 0; i < 4; i++, ii += 4) {
mdContext->digest[ii] = (unsigned char)(mdContext->buf[i] & 0xFF);
mdContext->digest[ii + 1] =
(unsigned char)((mdContext->buf[i] >> 8) & 0xFF);
mdContext->digest[ii + 2] =
(unsigned char)((mdContext->buf[i] >> 16) & 0xFF);
mdContext->digest[ii + 3] =
(unsigned char)((mdContext->buf[i] >> 24) & 0xFF);
}
memcpy(hash, mdContext->digest, 16);
}
/* Basic MD5 step. Transforms buf based on in.
*/
static void Transform(UINT4 *buf, UINT4 *in)
{
UINT4 a = buf[0], b = buf[1], c = buf[2], d = buf[3];
/* Round 1 */
#define S11 7
#define S12 12
#define S13 17
#define S14 22
FF(a, b, c, d, in[0], S11, UL(3614090360)); /* 1 */
FF(d, a, b, c, in[1], S12, UL(3905402710)); /* 2 */
FF(c, d, a, b, in[2], S13, UL(606105819)); /* 3 */
FF(b, c, d, a, in[3], S14, UL(3250441966)); /* 4 */
FF(a, b, c, d, in[4], S11, UL(4118548399)); /* 5 */
FF(d, a, b, c, in[5], S12, UL(1200080426)); /* 6 */
FF(c, d, a, b, in[6], S13, UL(2821735955)); /* 7 */
FF(b, c, d, a, in[7], S14, UL(4249261313)); /* 8 */
FF(a, b, c, d, in[8], S11, UL(1770035416)); /* 9 */
FF(d, a, b, c, in[9], S12, UL(2336552879)); /* 10 */
FF(c, d, a, b, in[10], S13, UL(4294925233)); /* 11 */
FF(b, c, d, a, in[11], S14, UL(2304563134)); /* 12 */
FF(a, b, c, d, in[12], S11, UL(1804603682)); /* 13 */
FF(d, a, b, c, in[13], S12, UL(4254626195)); /* 14 */
FF(c, d, a, b, in[14], S13, UL(2792965006)); /* 15 */
FF(b, c, d, a, in[15], S14, UL(1236535329)); /* 16 */
/* Round 2 */
#define S21 5
#define S22 9
#define S23 14
#define S24 20
GG(a, b, c, d, in[1], S21, UL(4129170786)); /* 17 */
GG(d, a, b, c, in[6], S22, UL(3225465664)); /* 18 */
GG(c, d, a, b, in[11], S23, UL(643717713)); /* 19 */
GG(b, c, d, a, in[0], S24, UL(3921069994)); /* 20 */
GG(a, b, c, d, in[5], S21, UL(3593408605)); /* 21 */
GG(d, a, b, c, in[10], S22, UL(38016083)); /* 22 */
GG(c, d, a, b, in[15], S23, UL(3634488961)); /* 23 */
GG(b, c, d, a, in[4], S24, UL(3889429448)); /* 24 */
GG(a, b, c, d, in[9], S21, UL(568446438)); /* 25 */
GG(d, a, b, c, in[14], S22, UL(3275163606)); /* 26 */
GG(c, d, a, b, in[3], S23, UL(4107603335)); /* 27 */
GG(b, c, d, a, in[8], S24, UL(1163531501)); /* 28 */
GG(a, b, c, d, in[13], S21, UL(2850285829)); /* 29 */
GG(d, a, b, c, in[2], S22, UL(4243563512)); /* 30 */
GG(c, d, a, b, in[7], S23, UL(1735328473)); /* 31 */
GG(b, c, d, a, in[12], S24, UL(2368359562)); /* 32 */
/* Round 3 */
#define S31 4
#define S32 11
#define S33 16
#define S34 23
HH(a, b, c, d, in[5], S31, UL(4294588738)); /* 33 */
HH(d, a, b, c, in[8], S32, UL(2272392833)); /* 34 */
HH(c, d, a, b, in[11], S33, UL(1839030562)); /* 35 */
HH(b, c, d, a, in[14], S34, UL(4259657740)); /* 36 */
HH(a, b, c, d, in[1], S31, UL(2763975236)); /* 37 */
HH(d, a, b, c, in[4], S32, UL(1272893353)); /* 38 */
HH(c, d, a, b, in[7], S33, UL(4139469664)); /* 39 */
HH(b, c, d, a, in[10], S34, UL(3200236656)); /* 40 */
HH(a, b, c, d, in[13], S31, UL(681279174)); /* 41 */
HH(d, a, b, c, in[0], S32, UL(3936430074)); /* 42 */
HH(c, d, a, b, in[3], S33, UL(3572445317)); /* 43 */
HH(b, c, d, a, in[6], S34, UL(76029189)); /* 44 */
HH(a, b, c, d, in[9], S31, UL(3654602809)); /* 45 */
HH(d, a, b, c, in[12], S32, UL(3873151461)); /* 46 */
HH(c, d, a, b, in[15], S33, UL(530742520)); /* 47 */
HH(b, c, d, a, in[2], S34, UL(3299628645)); /* 48 */
/* Round 4 */
#define S41 6
#define S42 10
#define S43 15
#define S44 21
II(a, b, c, d, in[0], S41, UL(4096336452)); /* 49 */
II(d, a, b, c, in[7], S42, UL(1126891415)); /* 50 */
II(c, d, a, b, in[14], S43, UL(2878612391)); /* 51 */
II(b, c, d, a, in[5], S44, UL(4237533241)); /* 52 */
II(a, b, c, d, in[12], S41, UL(1700485571)); /* 53 */
II(d, a, b, c, in[3], S42, UL(2399980690)); /* 54 */
II(c, d, a, b, in[10], S43, UL(4293915773)); /* 55 */
II(b, c, d, a, in[1], S44, UL(2240044497)); /* 56 */
II(a, b, c, d, in[8], S41, UL(1873313359)); /* 57 */
II(d, a, b, c, in[15], S42, UL(4264355552)); /* 58 */
II(c, d, a, b, in[6], S43, UL(2734768916)); /* 59 */
II(b, c, d, a, in[13], S44, UL(1309151649)); /* 60 */
II(a, b, c, d, in[4], S41, UL(4149444226)); /* 61 */
II(d, a, b, c, in[11], S42, UL(3174756917)); /* 62 */
II(c, d, a, b, in[2], S43, UL(718787259)); /* 63 */
II(b, c, d, a, in[9], S44, UL(3951481745)); /* 64 */
buf[0] += a;
buf[1] += b;
buf[2] += c;
buf[3] += d;
}
void Connect(int PPPOENumber, int UserName_1, int UserName_2, int UserName_3, int UserPassWard_1, int UserPassWard_2)
{
unsigned char *PIN = (unsigned char *)malloc(sizeof(unsigned char) * 29);
MD5_CTX md5;
unsigned char userName[64];
unsigned char userPassward[64];
userName[0] = UserName_1 / 100 + 48;
userName[1] = (UserName_1 / 10) % 10 + 48;
userName[2] = UserName_1 % 10 + 48;
userName[3] = UserName_2 / 1000 + 48;
userName[4] = (UserName_2 / 100) % 10 + 48;
userName[5] = (UserName_2 / 10) % 10 + 48;
userName[6] = UserName_2 % 10 + 48;
userName[7] = UserName_3 / 1000 + 48;
userName[8] = (UserName_3 / 100) % 10 + 48;
userName[9] = (UserName_3 / 10) % 10 + 48;
userName[10] = UserName_3 % 10 + 48;
userName[11] = '@';
userName[12] = 'D';
userName[13] = 'Z';
userName[14] = 'K';
userName[15] = 'D';
userName[16] = '.';
userName[17] = 'X';
userName[18] = 'Y';
userPassward[0] = UserPassWard_1 / 100 + 48;
userPassward[1] = (UserPassWard_1 / 10) % 10 + 48;
userPassward[2] = UserPassWard_1 % 10 + 48;
userPassward[3] = UserPassWard_2 / 100 + 48;
userPassward[4] = (UserPassWard_2 / 10) % 10 + 48;
userPassward[5] = UserPassWard_2 % 10 + 48;
time_t curtime = time(0);
tm tim;
localtime_s(&tim, &curtime);
int i;
byte temp[32];
long timedivbyfive;
byte timeByte[4];//time encryption from Linux Stamp
byte afterMD5[64];
byte beforeMD5[128] = { 0 };
byte MD501H[2];
char *MD501 = (char *)malloc(sizeof(unsigned char) * 3);
byte timeHash[4]; //time encryption from timeByte
byte PIN27[6]; //time encryption from timeHash
int seconds = time((time_t*)NULL);;
timedivbyfive = seconds / 5;
for (i = 0; i < 4; i++) {
timeByte[i] = (byte)(timedivbyfive >> (8 * (3 - i)) & 0xFF);
}
//beforeMD5
memcpy(beforeMD5, timeByte, 4);//array_copy
//locate character "@" in userName
i = 11;
memcpy(beforeMD5 + 4, userName, i);
i = i + 4;
//beforeMD5={time encryption(4)}+{user name(11)}+{RADIUS}+'\0';default length in ChongQing is 31
memcpy(beforeMD5 + i, "singlenet01", strlen("singlenet01"));
beforeMD5[26] = '\0';
//afterMD5
int length = 0;
while (beforeMD5[length] != '\0')
{
length++;
}
MD5_Init(&md5);
MD5_Update(&md5, beforeMD5, length);
MD5_Final(afterMD5, &md5);//generate MD5 sum
MD501H[0] = afterMD5[0] >> 4 & 0xF;//get MD5[0]
MD501H[1] = afterMD5[0] & 0xF;//get MD5[1]
sprintf(MD501, "%x%x", MD501H[0], MD501H[1]);
//PIN27
for (i = 0; i < 32; i++) {
temp[i] = timeByte[(31 - i) / 8] & 1;
timeByte[(31 - i) / 8] = timeByte[(31 - i) / 8] >> 1;
}
for (i = 0; i < 4; i++) {
timeHash[i] = temp[i] * 128 + temp[4 + i] * 64 + temp[8 + i]
* 32 + temp[12 + i] * 16 + temp[16 + i] * 8 + temp[20 + i]
* 4 + temp[24 + i] * 2 + temp[28 + i];
}
temp[1] = (timeHash[0] & 3) << 4;
temp[0] = (timeHash[0] >> 2) & 0x3F;
temp[2] = (timeHash[1] & 0xF) << 2;
temp[1] = (timeHash[1] >> 4 & 0xF) + temp[1];
temp[3] = timeHash[2] & 0x3F;
temp[2] = ((timeHash[2] >> 6) & 0x3) + temp[2];
temp[5] = (timeHash[3] & 3) << 4;
temp[4] = (timeHash[3] >> 2) & 0x3F;
for (i = 0; i < 6; i++) {
PIN27[i] = temp[i] + 0x020;
if (PIN27[i] >= 0x40) {
PIN27[i]++;
}
}
//PIN
PIN[0] = '\r';
PIN[1] = '\n';
memcpy(PIN + 2, PIN27, 6);
PIN[8] = MD501[0];
PIN[9] = MD501[1];
memcpy(PIN + 10, userName, 19);
char PIN_[29];
char userPassward_[6];
for (int count = 0; count < 29; count++)
{
int a = PIN[count];
PIN_[count] = a;
}
}这是从DLL代码上拉出来的 所以传入的变量都是INT型






















 9956
9956











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








