0x00 前言
这个是第十九台机子了, 不知不觉已经做了这么多东西了。
最后,我们来一个现学现用
Dear E-Commerce professional ; This letter was specially
selected to be sent to you . We will comply with all
removal requests ! This mail is being sent in compliance
with Senate bill 1621 ; Title 3 , Section 302 ! THIS
IS NOT MULTI-LEVEL MARKETING . Why work for somebody
else when you can become rich as few as 41 months .
Have you ever noticed nearly every commercial on television
has a .com on in it and people love convenience . Well,
now is your chance to capitalize on this ! We will
help you use credit cards on your website & deliver
goods right to the customer’s doorstep ! You can begin
at absolutely no cost to you . But don’t believe us
. Ms Simpson of North Carolina tried us and says “I
was skeptical but it worked for me” . We assure you
that we operate within all applicable laws ! We beseech
you - act now ! Sign up a friend and you’ll get a discount
of 50% ! Thanks . Dear Colleague ; Especially for you
- this cutting-edge intelligence . If you no longer
wish to receive our publications simply reply with
a Subject: of “REMOVE” and you will immediately be
removed from our mailing list . This mail is being
sent in compliance with Senate bill 2616 ; Title 2
; Section 306 ! This is different than anything else
you’ve seen ! Why work for somebody else when you can
become rich in 52 WEEKS . Have you ever noticed nobody
is getting any younger and nearly every commercial
on television has a .com on in it ! Well, now is your
chance to capitalize on this . WE will help YOU use
credit cards on your website and increase customer
response by 120% . You can begin at absolutely no cost
to you ! But don’t believe us ! Mr Ames of New Jersey
tried us and says “I was skeptical but it worked for
me” ! This offer is 100% legal ! Do not go to sleep
without ordering ! Sign up a friend and you’ll get
a discount of 30% . Thank-you for your serious consideration
of our offer .
链接
https://www.vulnhub.com/entry/hacknos-os-hax,389/
0x01 信息收集
ip
masscan --ping 192.168.0.1/24 --rate 1000000000000000000000000000000

端口扫描

0x02 攻击
端口
端口方向没有什么突破
web
访问之后,无果
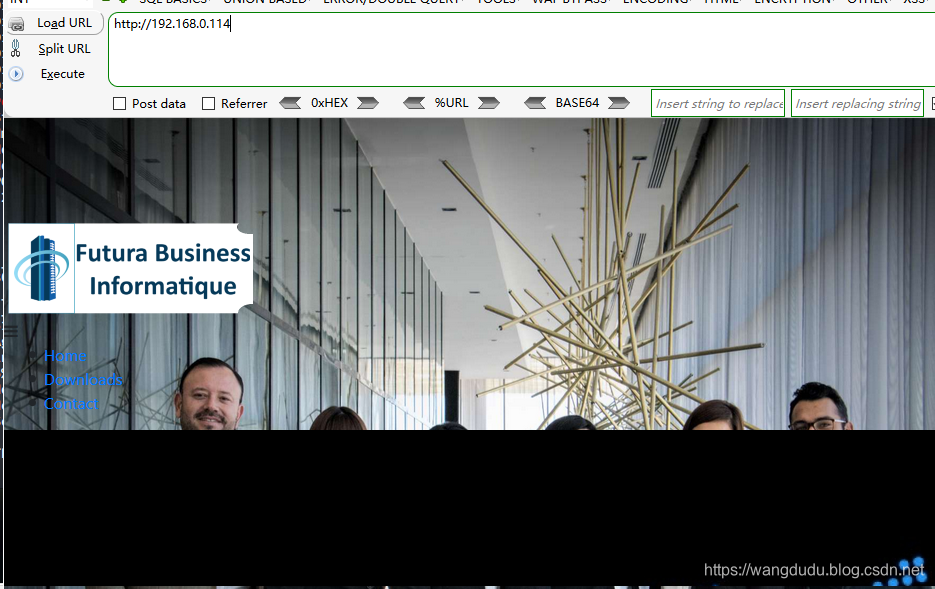
dirb目录扫描

此处看到wordpress,所以使用wpscan进行扫描

然后对web用户进行一个爆破,但是最后爆破未果
查看img文件,发现一个flaghost.png文件
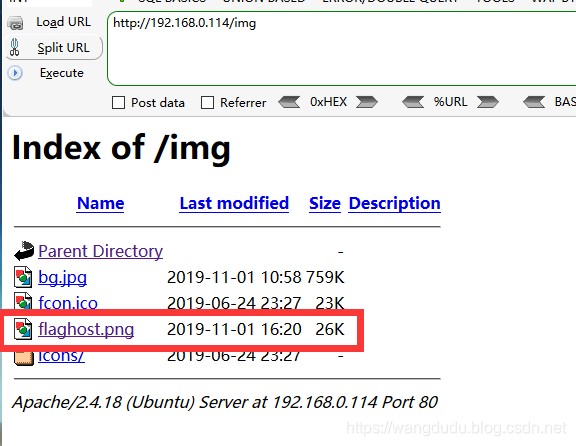
下载png使用Stegsolve进行查看,可以拿到一个密码 passw@45

然后这个东西看居然是一个目录!!!

打开这个flag

ok加密。。。真的是一道ctf的题啊

然后拿到了web:Hacker@4514,登录wp

反弹一个shell

然后监听,反弹shell

查一下home,发现web,su web 转换权限

获取一下pty

sudo -l 发现一个awk

网上查一下

直接提权
sudo awk ‘BEGIN {system("/bin/sh")}’

查看flag

最后事实证明可以直接ssh连接web即可。。。不需要中间的提权过程

0x03 总结
- 拿到的东西可能是一个目录
- 在走投无路的时候,每一个可以访问的文件目录都要去进行一个访问。








 本文记录了一次针对Hacknos OS Hax虚拟机的渗透测试过程,包括信息收集、端口扫描、Web应用漏洞利用、权限提升及最终flag获取。通过对WordPress的目录扫描和爆破尝试,发现了隐藏的flag文件,并成功通过多种技术手段获得系统权限。
本文记录了一次针对Hacknos OS Hax虚拟机的渗透测试过程,包括信息收集、端口扫描、Web应用漏洞利用、权限提升及最终flag获取。通过对WordPress的目录扫描和爆破尝试,发现了隐藏的flag文件,并成功通过多种技术手段获得系统权限。


















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










