1. 劫持进程实现注入
今天我尝试对win10 x64上的计算器进程进行进程劫持注入。
劫持进程实现注入要执行如下步骤:
- 以挂起方式启动目标进程
- 采用其他注入方式将DLL注入目标进程
- 继续目标进程的主线程使目标进程继续运行
这种注入方式的优点: 被注入的进程来不及做任何防御就会被注入。
因为以挂起方式启动进程,该进程的地址空间内除了目标进程的exe模块和ntdll.dll模块外
还来不及解析导入表将所需dll全部导入,也就是说作为防护的dll模块或者线程可能也来不及导入和执行,这大大提高了注入成功率
直接来看代码:
#include <windows.h>
#include <iostream>
#include <cstdio>
using namespace std;
// 突破SESSION0进行远线程注入
BOOL PassSession0RemoteThreadInjection(DWORD dwProcessId, const char* pcszDllFileName)
{
HANDLE hProcess = NULL;
int iSize = 0;
LPVOID lpDllAddr = NULL;
FARPROC pFuncProcAddr = NULL;
HANDLE hRemoteThread = NULL;
DWORD dwStatus = 0;
HMODULE hntdll = NULL, hKrnl32 = NULL;
// 打开被注入进程
hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, dwProcessId);
if (NULL == hProcess)
{
cout << "OpenProcess错误" << GetLastError() << endl;
return(FALSE);
}
iSize = lstrlenA(pcszDllFileName) + 1;
lpDllAddr = VirtualAllocEx(hProcess, NULL, iSize, MEM_COMMIT, PAGE_READWRITE);
if (NULL == lpDllAddr)
{
return(FALSE);
}
if (FALSE == WriteProcessMemory(hProcess, lpDllAddr, pcszDllFileName, iSize, NULL))
{
return(FALSE);
}
// 加载ntdll.dll
hntdll = LoadLibraryA("ntdll.dll");
if (NULL == hntdll)
{
return(FALSE);
}
// 加载kernel32.dll
hKrnl32 = LoadLibraryA("kernel32.dll");
if (NULL == hKrnl32)
{
return(FALSE);
}
pFuncProcAddr = GetProcAddress(hKrnl32, "LoadLibraryA");
if (NULL == pFuncProcAddr)
{
return(FALSE);
}
#ifdef _WIN64
typedef DWORD(WINAPI* ZWCREATETHREADEX)(
PHANDLE ThreadHandle,
ACCESS_MASK DesiredAccess,
LPVOID ObjectAttributes,
HANDLE ProcessHandle,
LPTHREAD_START_ROUTINE lpStartAddress,
LPVOID lpParameter,
ULONG CreateThreadFlags,
SIZE_T ZeroBits,
SIZE_T StackSize,
SIZE_T MaximumStackSize,
LPVOID pUnkown);
#else
typedef DWORD(WINAPI* ZWCREATETHREADEX)(
PHANDLE ThreadHandle,
ACCESS_MASK DesiredAccess,
LPVOID ObjectAttributes,
HANDLE ProcessHandle,
LPTHREAD_START_ROUTINE lpStartAddress,
LPVOID lpParameter,
BOOL CreateSuspended,
DWORD dwStackSize,
DWORD dw1,
DWORD dw2,
LPVOID pUnkown);
#endif
ZWCREATETHREADEX ZwCreateThreadEx = (ZWCREATETHREADEX)GetProcAddress(hntdll, "ZwCreateThreadEx");
if (NULL == ZwCreateThreadEx)
{
return(FALSE);
}
dwStatus = ZwCreateThreadEx(&hRemoteThread,
PROCESS_ALL_ACCESS,
NULL,
hProcess,
(LPTHREAD_START_ROUTINE)pFuncProcAddr,
lpDllAddr, 0, 0, 0, 0,
NULL);
if (NULL == hRemoteThread)
{
return(FALSE);
}
CloseHandle(hProcess);
return(TRUE);
}
int main()
{
char szCmdLine[MAX_PATH] = "calc.exe";
STARTUPINFO stStartupInfo = { 0 };
PROCESS_INFORMATION stPi = { 0 };
BOOL fOk = FALSE;
__try
{
// 1. 以挂起方式创建进程
GetStartupInfo(&stStartupInfo);
fOk = CreateProcess(
NULL,
szCmdLine,
NULL,
NULL,
FALSE,
CREATE_SUSPENDED,
NULL,
NULL,
&stStartupInfo,
&stPi
);
if (!fOk)
{
cout << "创建进程失败!" << endl;
__leave;
}
// 2. 突破SESSION0进行远线程注入
fOk = PassSession0RemoteThreadInjection(stPi.dwProcessId, "D:\\MsgBoxDll64.dll");
if (!fOk)
{
cout << "远线程注入失败!" << endl;
__leave;
}
// 3. 继续挂起进程的主线程
ResumeThread(stPi.hThread);
}
__finally
{
if (!fOk && stPi.hProcess)
{
TerminateProcess(stPi.hProcess, 0);
}
}
system("pause");
return(0);
}接下来看一下演示:
首先以挂起方式开启进程, 可以看到目标进程的地址空间内只有2个模块

接下里实现远线程注入, 可以看到DLL已经被注入并且显示了弹窗代表注入成功, 这里来观察一下,calc.exe的PID是20704

来看一下继续运行进程后,目标进程的PID是22384,这是怎么回事? 这代表这之前的进程消亡了,并创建出了一个新进程。那这也代表了之前的注入运行一次后就没有效果了。

2. 分析calc.exe,寻找注入只成功一次的原因
来分析一下calc.exe, 将其拖入OD内后第一个进程就被启动了, 可以看到其第一个进程的PID是18192

首先找到OEP并进入:

继续往里面走发现:

发现了运行时函数_initterm

发现了,calc.exe内部执行了ShellExecute来调用了Calculator进程

calc.exe之后便调用了exit()即ExitProcess自杀了, 留下了Calculator.exe这个孤儿进程。

我好奇的地方在于既然calc.exe有对应的可执行文件如下:

那Calculator.exe是否有自己的可执行文件,结果发现是没有的。来看一下ShellExecute中传递的参数:
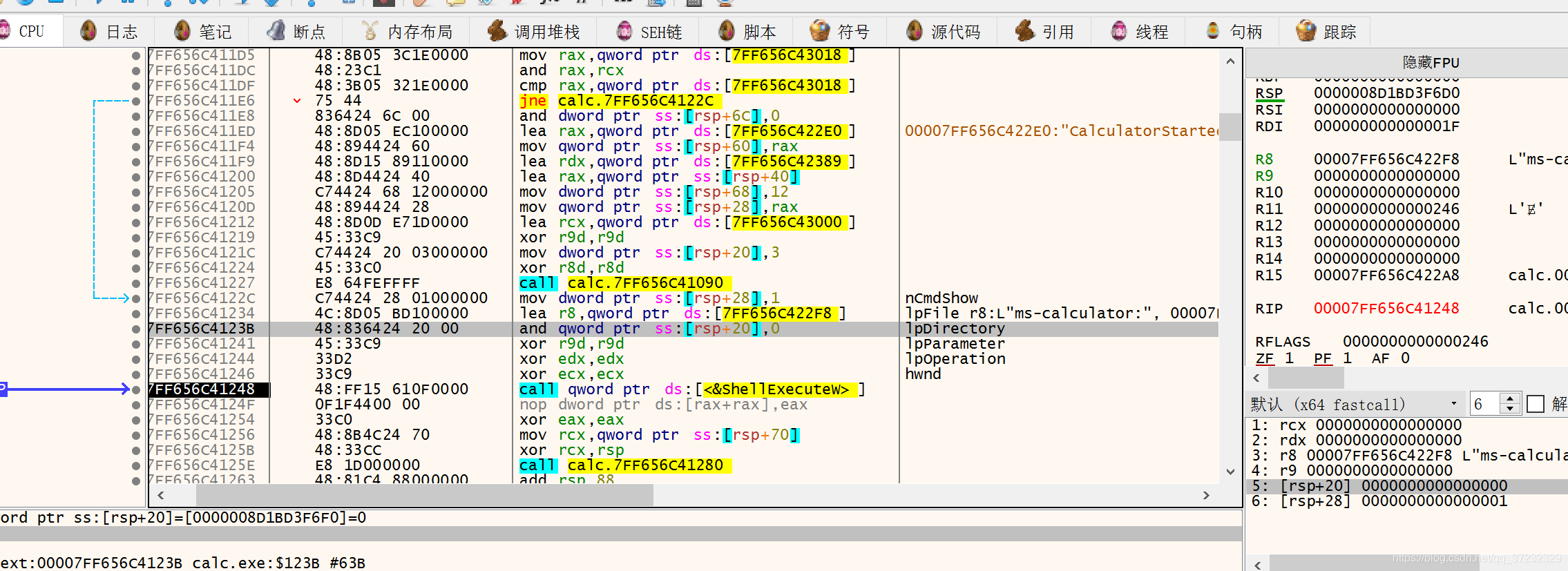
再看看IDA:

可以发现lpOperation传入的值是NULL,代表使用默认的打开方式open。其中lpFile是"ms-calculator:"。所以这种方法对于诸如calc.exe进程只能执行一次。
3. inline hook住ShellExecute来执行自己代码的思路
有了之前的分析,下面尝试一下另外一种思路。
这边采用inline hook的方式hook住ShellExecute。然后让其调用我们自己的代码, 先看一下源码:
// inline hook的dll
#include <windows.h>
// 保存原来ShellExecuteW的代码
BYTE g_bOldData[12] = { 0 };
typedef HINSTANCE (WINAPI *SHELLEXECUTEW)(
HWND hwnd,
LPCWSTR lpOperation,
LPCWSTR lpFile,
LPCWSTR lpParameters,
LPCWSTR lpDirectory,
INT nShowCmd
);
HINSTANCE NewShellExecuteW(
HWND hwnd,
LPCWSTR lpOperation,
LPCWSTR lpFile,
LPCWSTR lpParameters,
LPCWSTR lpDirectory,
INT nShowCmd
)
{
DWORD dwProtect = 0;
// 首先Unhook
VirtualProtect((PBYTE)ShellExecuteW, sizeof(g_bOldData), PAGE_EXECUTE_READWRITE, &dwProtect);
RtlCopyMemory((PBYTE)ShellExecuteW, g_bOldData, sizeof(g_bOldData));
VirtualProtect((PBYTE)ShellExecuteW, sizeof(g_bOldData), dwProtect, &dwProtect);
MessageBox(NULL, "通过挂钩来启动的MSGBOX", "标题", MB_OK);
// 执行原来的函数
return(ShellExecuteW(hwnd,
lpOperation,
lpFile,
lpParameters,
lpDirectory,
nShowCmd));
}
BOOL InlineHook()
{
HMODULE hMod = NULL;
SHELLEXECUTEW ShellExecuteW = NULL;
DWORD64 dwAddrOfFunc = 0;
DWORD dwProtect = 0;
BYTE bShellCode[12] = {0x48, 0xb8, 0, 0, 0, 0, 0, 0, 0, 0, 0xff, 0xe0};
// 加载Shell32.dll库
hMod = LoadLibrary("Shell32.dll");
if (NULL == hMod)
{
return(FALSE);
}
// 获取hook的函数地址
ShellExecuteW = (SHELLEXECUTEW)GetProcAddress(hMod, "ShellExecuteW");
if (NULL == ShellExecuteW)
{
return(FALSE);
}
dwAddrOfFunc = (DWORD64)NewShellExecuteW;
// 拷贝原本的内容到全局变量内保存
RtlCopyMemory(g_bOldData, (PBYTE)ShellExecuteW, sizeof(bShellCode));
// 把地址拷贝到jmp语句内
RtlCopyMemory(&bShellCode[2], &dwAddrOfFunc, sizeof(DWORD64));
// 修改页属性
VirtualProtect((PBYTE)ShellExecuteW,
sizeof(bShellCode),
PAGE_EXECUTE_READWRITE,
&dwProtect);
// 把jmp语句拷贝到ShellExecuteW的位置
RtlCopyMemory((PBYTE)ShellExecuteW, bShellCode, sizeof(bShellCode));
// 恢复页属性
VirtualProtect((PBYTE)ShellExecuteW,
sizeof(bShellCode),
dwProtect,
&dwProtect);
return(TRUE);
}
BOOL APIENTRY DllMain(_In_ HINSTANCE hInstance, _In_ DWORD fdwReason, _In_ LPVOID lpvReserved)
{
switch (fdwReason)
{
case DLL_PROCESS_ATTACH:
{
InlineHook();
break;
}
case DLL_PROCESS_DETACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
{
break;
}
}
return(TRUE);
}这里是注入代码:
#include <windows.h>
#include <iostream>
#include <cstdio>
using namespace std;
// 突破SESSION0进行远线程注入
BOOL PassSession0RemoteThreadInjection(DWORD dwProcessId, const char* pcszDllFileName)
{
HANDLE hProcess = NULL;
int iSize = 0;
LPVOID lpDllAddr = NULL;
FARPROC pFuncProcAddr = NULL;
HANDLE hRemoteThread = NULL;
DWORD dwStatus = 0;
HMODULE hntdll = NULL, hKrnl32 = NULL;
// 打开被注入进程
hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, dwProcessId);
if (NULL == hProcess)
{
cout << "OpenProcess错误" << GetLastError() << endl;
return(FALSE);
}
iSize = lstrlenA(pcszDllFileName) + 1;
lpDllAddr = VirtualAllocEx(hProcess, NULL, iSize, MEM_COMMIT, PAGE_READWRITE);
if (NULL == lpDllAddr)
{
return(FALSE);
}
if (FALSE == WriteProcessMemory(hProcess, lpDllAddr, pcszDllFileName, iSize, NULL))
{
return(FALSE);
}
// 加载ntdll.dll
hntdll = LoadLibraryA("ntdll.dll");
if (NULL == hntdll)
{
return(FALSE);
}
// 加载kernel32.dll
hKrnl32 = LoadLibraryA("kernel32.dll");
if (NULL == hKrnl32)
{
return(FALSE);
}
pFuncProcAddr = GetProcAddress(hKrnl32, "LoadLibraryA");
if (NULL == pFuncProcAddr)
{
return(FALSE);
}
#ifdef _WIN64
typedef DWORD(WINAPI* ZWCREATETHREADEX)(
PHANDLE ThreadHandle,
ACCESS_MASK DesiredAccess,
LPVOID ObjectAttributes,
HANDLE ProcessHandle,
LPTHREAD_START_ROUTINE lpStartAddress,
LPVOID lpParameter,
ULONG CreateThreadFlags,
SIZE_T ZeroBits,
SIZE_T StackSize,
SIZE_T MaximumStackSize,
LPVOID pUnkown);
#else
typedef DWORD(WINAPI* ZWCREATETHREADEX)(
PHANDLE ThreadHandle,
ACCESS_MASK DesiredAccess,
LPVOID ObjectAttributes,
HANDLE ProcessHandle,
LPTHREAD_START_ROUTINE lpStartAddress,
LPVOID lpParameter,
BOOL CreateSuspended,
DWORD dwStackSize,
DWORD dw1,
DWORD dw2,
LPVOID pUnkown);
#endif
ZWCREATETHREADEX ZwCreateThreadEx = (ZWCREATETHREADEX)GetProcAddress(hntdll, "ZwCreateThreadEx");
if (NULL == ZwCreateThreadEx)
{
return(FALSE);
}
dwStatus = ZwCreateThreadEx(&hRemoteThread,
PROCESS_ALL_ACCESS,
NULL,
hProcess,
(LPTHREAD_START_ROUTINE)pFuncProcAddr,
lpDllAddr, 0, 0, 0, 0,
NULL);
if (NULL == hRemoteThread)
{
return(FALSE);
}
CloseHandle(hProcess);
return(TRUE);
}
int main()
{
char szCmdLine[MAX_PATH] = "calc.exe";
STARTUPINFO stStartupInfo = { 0 };
PROCESS_INFORMATION stPi = { 0 };
BOOL fOk = FALSE;
__try
{
// 1. 以挂起方式创建进程
GetStartupInfo(&stStartupInfo);
fOk = CreateProcess(
NULL,
szCmdLine,
NULL,
NULL,
FALSE,
CREATE_SUSPENDED,
NULL,
NULL,
&stStartupInfo,
&stPi
);
if (!fOk)
{
cout << "创建进程失败!" << endl;
__leave;
}
// 2. 突破SESSION0进行远线程注入
fOk = PassSession0RemoteThreadInjection(stPi.dwProcessId, "C:\\Users\\Administrator\\Desktop\\作业\\APCInject\\x64\\Debug\\ShellHook.dll");
if (!fOk)
{
cout << "远线程注入失败!" << endl;
__leave;
}
// 3. 这里是为了防止来不及hook就已经执行了ShellExecute函数
Sleep(100);
// 4. 继续挂起进程的主线程
ResumeThread(stPi.hThread);
}
__finally
{
if (!fOk && stPi.hProcess)
{
TerminateProcess(stPi.hProcess, 0);
}
}
system("pause");
return(0);
}来看一下效果:

这里实现了inline hook, 可以看到,calc.exe进程启动了但却跳出了弹框,现在拿OD附着到进程上看一下ShellExecuteW的代码:

再来看看这个jmp跳转的位置, 其跳转到的正是我们的NewShellExecuteW函数

来看看里面内容:

(完)
























 2万+
2万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








