感觉这比赛比较简单。。。花了一天时间做,直接ak逆向了
decription
弱智题,爆破就行
a = [ 0x12, 0x45, 0x10, 0x47, 0x19, 0x49, 0x49, 0x49, 0x1A, 0x4F,
0x1C, 0x1E, 0x52, 0x66, 0x1D, 0x52, 0x66, 0x67, 0x68, 0x67,
0x65, 0x6F, 0x5F, 0x59, 0x58, 0x5E, 0x6D, 0x70, 0xA1, 0x6E,
0x70, 0xA3]
b = []
for i in range(len(a)):
a[i] = a[i] ^0x23
for i in range(32):
for j in range(0x20,0x7f):
v7 = j
v6 = i
while(True):
v4 = 2*(v6&v7)
v7 ^= v6
v6 = v4
if(v4==0):
break
if(v7==a[i]):
b.append(chr(j))
break
print("".join(b))
obfu
加密混合。。罢了
from Crypto.Cipher import AES
from z3 import *
result = [ 0x21, 0x23, 0x2F, 0x29, 0x7A, 0x57, 0xA5, 0xA7, 0x43, 0x89,
0x4A, 0x0E, 0x4A, 0x80, 0x1F, 0xC3]
rc4_xor = [0xec,0xfb,0x41,0x59,0xf9,0xe7,0x8b,0x12,0x1b,0x3f,0x50,0x82,0xf0,0xa3,0x44,0x2b]
aeskey = b"\x8c\xe5\x1f\x93\x50\xf4\x45\x11\xa8\x54\xe1\xb5\xf0\xa3\xfb\xca"
aesiv = b"\x6e\xd6\xce\x61\xbb\x8f\xb7\xf3\x10\xb7\x70\x45\x9e\xfc\xe1\xb1"
data = b"\x21\x23\x2f\x29\x7a\x57\xa5\xa7\x43\x89\x4a\x0e\x4a\x80\x1f\xc3"
#data = b"\xae\xeb\xd4\x7a\xbd\xe5\x2d\x6c\xcb\xcd\x52\x56\x96\x98\xc4\x29"
aes = AES.new(aeskey,AES.MODE_CBC,aesiv)
data1 = aes.encrypt(data)
result = []
for i in range(16):
result.append(data1[i] ^ rc4_xor[i])
flag = [0]*16
for i in range(16):
flag[(15+i)%16] = ((result[(15+i)%16]<<3)&0xf8)| ((result[i]>>5)&0x07)
for i in range(16):
print(hex(flag[i]))
enigma
异常加虚拟机
最讨厌这两个组合了。。。setunhandle反调试,不怕爷有strongod直接绕,之后慢慢看就懂了
一共就移位,位运算,xor
exch = [0x11,0x02,0x13,0x04,0x15,0x06,0x17,0x08,0x19,0x0a,0x1b,0x0c,0x1d,0x0e,0x1f,0x10,0x01,0x12,0x03,0x14,0x05,0x16,0x07,0x18,0x09,0x1a,0x0b,0x1c,0x0d,0x1e,0x0f,0]
a =[0x93,0x8b,0x8f,0x43,0x12,0x68,0xf7,0x90,0x7a,0x4b,0x6e,0x42,0x13,0x01,0xb4,0x21,0x20,0x73,0x8d,0x68,0xcb,0x19,0xfc,0xf8,0xb2,0x6b,0xc4,0xab,0xc8,0x9b,0x8d,0x22]
b = [1,2,3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9,0,1,2,3,4,5,6,7,8,9,0,1,2]
Xor = "Bier"
for i in range(1,32,1):
a[i] = a[i]^ord(Xor[i%4]) ^ a[i-1]
for i in range(32):
print(hex(a[i]))
from z3 import *
flag = [BitVec("x%d"%i,8) for i in range(32)]
s = Solver()
for i in range(32):
s.add(((flag[i]&0x1f)<<3) | ((flag[(i+1)%32]&0xe0)>>5) == a[i])
if s.check()==sat:
m = s.model()
Str = [chr(m[flag[i]].as_long().real) for i in range(32)]
for i in range(0,32,2):
Str[exch[i]],Str[exch[i+1]] = Str[exch[i+1]],Str[exch[i]]
print("".join(Str))
#print(b)
babyre
内部加载dll,hook了驱动,这个出的蛮好的,加密就sm4
import pysm4,codecs
#解密 一次只能16字节 而且全部hex格式,呵呵 这个模块真恶心 32放进去,折腾了两小时
key = 0x457a5f354d345f433170484072212121
z = 0xea6358b78ce2a1e9c5298f53e8083259
z1 = 0xaf1b67aed9dacfc472ffb1ec7673f306
z = pysm4.decrypt(z,key)
z1 = pysm4.decrypt(z1,key)
z = str(hex(z)[2:-1])
z1 = str(hex(z1)[2:-1])
decode_hex = codecs.getdecoder("hex_codec")
decode_hex(z)[0]+decode_hex(z1)[0]
Child_protect
双进程保护,主进程启用子进程同时对子进程监控并对子进程做了修改,
修改如下
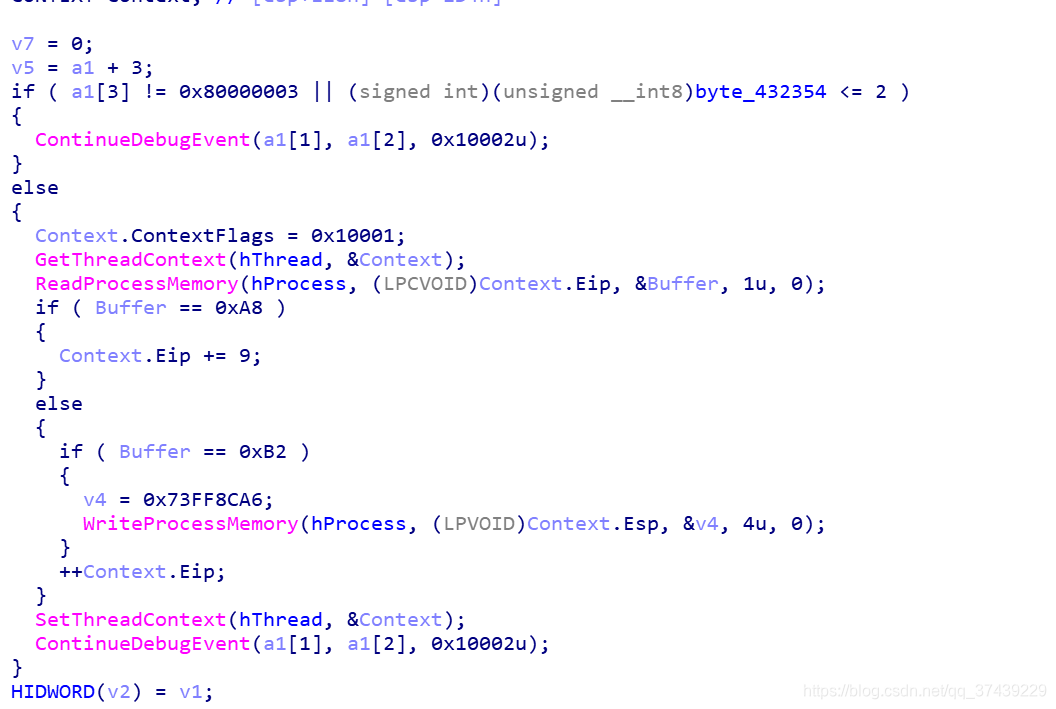
sub_413950对子进程监控修改
sub_413d10,sub_413670调用子进程
既然开启了子进程保护,那我直接跳过调用子进程的函数,再按照修改的函数,对程序patch就行,这道题出的满好的,玩的很nb ,算法就只有tea,xor
#include<stdio.h>
#define uint32_t unsigned int
void decode(unsigned int *v,unsigned int *k)
{
uint32_t v0=v[0], v1=v[1], sum=0xC6EF3720, i; //由加密轮数而算出
uint32_t delta=0x9e3779b9;
uint32_t k0=k[0], k1=k[1], k2=k[2], k3=k[3];
for (i=0; i<32; i++) { //核心解密算法
v1 -= ((v0<<4) + k2) ^ (v0 + sum) ^ ((v0>>5) + k3);
v0 -= ((v1<<4) + k0) ^ (v1 + sum) ^ ((v1>>5) + k1);
sum -= delta;
}
v[0]=v0; v[1]=v1;
}
void Xor(unsigned int * a1)
{
int v3 = 0x73ff8ca6;
int i;
for(i = 0 ; i < 8 ;++i)
{
a1[i] ^=v3;
v3-=0x50ffe544;
}
}
int main()
{
unsigned int v1[] = {0xede98b3b,0xd285e7eb};
unsigned int v2[] = {0x5116507a,0xb1dc5d09};
unsigned int v3[] = {0x45aeb915,0x4d8dff50};
unsigned int v4[] = {0xdee0bc8b,0x9bbcfee1};
unsigned int k[] = {0x82aba3fe,0xac1ddca8,0x87ec6b60,0xa2394568};
decode(v1,k);
decode(v2,k);
decode(v3,k);
decode(v4,k);
// printf("0x%x,0x%x,0x%x,0x%x,0x%x,0x%x,0x%x,0x%x",v1[0],v1[1],v2[0],v2[1],v3[0],v3[1],v4[0],v4[1]);
unsigned int result[] = {0x3e9affcb,0x478dce18,0xb891a541,0xc191b885,0x6b9a84ff,0xad61703e,0xeb5f6c7d,0x62772dbb};
Xor(result);
int i = 0 ;
for(i = 0 ; i < 8; ++i)
printf("%x",result[i]);
}





















 1310
1310











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








