文章目录
【Spring Cloud Alibaba】Oauth2 授权认证服务
1、Spring Cloud Oauth2
Spring 提供的 Spring Security oAuth2 能搭建一套验证授权及资源访问服务,帮助大家在实现企业微服务架构时能够有效的控制多个服务的统一登录、授权及资源保护工作
(1)什么是 oAuth?
oAuth 协议为用户资源的授权提供了一个安全的、开放而又简易的标准。与以往的授权方式不同之处是 oAuth 的授权不会使第三方触及到用户的帐号信息(如用户名与密码),即第三方无需使用用户的用户名与密码就可以申请获得该用户资源的授权,因此 oAuth 是安全的
(2)Spring Security
Spring Security 是一个安全框架,前身是 Acegi Security,能够为 Spring 企业应用系统提供声明式的安全访问控制。Spring Security 基于 Servlet 过滤器、IoC 和 AOP,为 Web 请求和方法调用提供身份确认和授权处理,避免了代码耦合,减少了大量重复代码工作
| 名词 | 英文 | 说明 |
|---|---|---|
| 第三方应用程序 | Third-party application | 又称之为客户端(client),比如上节中提到的设备(PC、Android、iPhone、TV、Watch),我们会在这些设备中安装我们自己研发的 APP。又比如我们的产品想要使用 QQ、微信等第三方登录。对我们的产品来说,QQ、微信登录是第三方登录系统。我们又需要第三方登录系统的资源(头像、昵称等)。对于 QQ、微信等系统我们又是第三方应用程序 |
| HTTP 服务提供商 | HTTP service | QQ、微信等都可以称之为“服务提供商” |
| 资源所有者 | Resource Owner | 又称之为用户(user) |
| 用户代理 | User Agent | 比如浏览器,代替用户去访问这些资源 |
| 认证服务器 | Authorization server | 即服务提供商专门用来处理认证的服务器,简单点说就是登录功能(验证用户的账号密码是否正确以及分配相应的权限) |
| 资源服务器 | Resource server | 即服务提供商存放用户生成的资源的服务器。它与认证服务器,可以是同一台服务器,也可以是不同的服务器。简单点说就是资源的访问入口 |
(3)交互过程
oAuth 在 “客户端” 与 “服务提供商” 之间,设置了一个授权层(authorization layer)。“客户端” 不能直接登录 “服务提供商”,只能登录授权层,以此将用户与客户端区分开来
“客户端” 登录授权层所用的令牌(token),与用户的密码不同。用户可以在登录的时候,指定授权层令牌的权限范围和有效期。“客户端” 登录授权层以后,“服务提供商” 根据令牌的权限范围和有效期,向 “客户端” 开放用户储存的资料

(4)Oauth2 授权认证服务
- 网关采用的是 Spring Cloud Gateway
- spring-cloud-alibaba-oauth2-gateway:8083,网关服务
- spring-cloud-alibaba-oauth2-server:8084,授权认证服务
- spring-cloud-alibaba-oauth2-provider:8085,服务提供者
2、搭建网关服务
基于 Spring Cloud Gateway 搭建网关,创建 spring-cloud-alibaba-oauth2-gateway 模块
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-discovery</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-gateway</artifactId>
<version>${spring-cloud-starter-gateway.version}</version>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
<exclusions>
<exclusion>
<groupId>org.junit.vintage</groupId>
<artifactId>junit-vintage-engine</artifactId>
</exclusion>
</exclusions>
</dependency>
${spring-cloud-starter-gateway.version}
版本是
<spring-cloud-starter-gateway.version>2.2.1.RELEASE</spring-cloud-starter-gateway.version>
修改 application.properties 配置文件
server.port=8003
spring.application.name=spring-cloud-alibaba-oauth2-gateway
management.server.port=9003
management.endpoints.jmx.exposure.include=*
management.endpoints.web.exposure.include=*
management.endpoint.health.show-details=always
# Nacos注册信息
spring.cloud.nacos.discovery.server-addr=localhost:8848
spring.cloud.nacos.discovery.username=nacos
spring.cloud.nacos.discovery.password=nacos
spring.cloud.nacos.discovery.namespace=sandbox-configuration
# gateway配置
spring.cloud.gateway.discovery.locator.enabled=true
spring.cloud.gateway.routes[0].id=spring-cloud-alibaba-oauth2-server
spring.cloud.gateway.routes[0].uri=lb://spring-cloud-alibaba-oauth2-server
spring.cloud.gateway.routes[0].predicates[0]=Path=/oauth/**
spring.cloud.gateway.routes[1].id=spring-cloud-alibaba-oauth2-provider
spring.cloud.gateway.routes[1].uri=lb://spring-cloud-alibaba-oauth2-provider
spring.cloud.gateway.routes[1].predicates[0]=Path=/provider/**
启动类增加注解
@EnableDiscoveryClient
然后启动注册到 Nacos,网关搭建完成了
3、搭建授权认证服务
创建 spring-cloud-alibaba-oauth2-server 模块,核心依赖 spring-cloud-starter-oauth2
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-discovery</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-oauth2</artifactId>
<version>${spring-cloud-starter-oauth2.version}</version>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
<exclusions>
<exclusion>
<groupId>org.junit.vintage</groupId>
<artifactId>junit-vintage-engine</artifactId>
</exclusion>
</exclusions>
</dependency>
修改 application.properties 配置文件
server.port=8004
spring.application.name=spring-cloud-alibaba-oauth2-server
management.server.port=9004
management.endpoints.jmx.exposure.include=*
management.endpoints.web.exposure.include=*
management.endpoint.health.show-details=always
# Nacos注册信息
spring.cloud.nacos.discovery.server-addr=localhost:8848
spring.cloud.nacos.discovery.username=nacos
spring.cloud.nacos.discovery.password=nacos
spring.cloud.nacos.discovery.namespace=sandbox-configuration
增加认证服务器配置
package cn.tellsea.config;
import lombok.AllArgsConstructor;
import org.springframework.context.annotation.Configuration;
import org.springframework.http.HttpMethod;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerSecurityConfigurer;
import org.springframework.security.oauth2.provider.ClientDetailsService;
import org.springframework.security.oauth2.provider.code.AuthorizationCodeServices;
import org.springframework.security.oauth2.provider.token.AuthorizationServerTokenServices;
import org.springframework.security.oauth2.provider.token.DefaultTokenServices;
import org.springframework.security.oauth2.provider.token.TokenEnhancerChain;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import java.util.Arrays;
/**
* oauth认证服务器配置
*
* @author Tellsea
* @date 2021/12/25
*/
@Configuration
@AllArgsConstructor
@EnableAuthorizationServer
public class AuthorizationServerConfig extends AuthorizationServerConfigurerAdapter {
/**
* 令牌持久化配置
*/
private final TokenStore tokenStore;
/**
* 客户端详情服务
*/
private final ClientDetailsService clientDetailsService;
/**
* 认证管理器
*/
private final AuthenticationManager authenticationManager;
/**
* 授权码服务
*/
private final AuthorizationCodeServices authorizationCodeServices;
/**
* jwtToken解析器
*/
private final JwtAccessTokenConverter jwtAccessTokenConverter;
/**
* 客户端详情服务配置 (demo采用本地内存存储)
*/
@Override
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients
// 使用本地内存存储
.inMemory()
// 客户端id
.withClient("client_1")
// 客户端密码
.secret(new BCryptPasswordEncoder().encode("123456"))
// 该客户端允许授权的类型
.authorizedGrantTypes("authorization_code", "password", "client_credentials", "implicit", "refresh_token")
// 该客户端允许授权的范围
.scopes("all")
// false跳转到授权页面,true不跳转,直接发令牌
.autoApprove(false);
}
/**
* 配置访问令牌端点
*/
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) {
endpoints
// 认证管理器
.authenticationManager(authenticationManager)
// 授权码服务
.authorizationCodeServices(authorizationCodeServices)
// 令牌管理服务
.tokenServices(tokenServices())
.allowedTokenEndpointRequestMethods(HttpMethod.GET, HttpMethod.POST);
}
/**
* 配置令牌端点安全约束
*/
@Override
public void configure(AuthorizationServerSecurityConfigurer security) {
security
// oauth/check_token公开
.checkTokenAccess("permitAll()")
// oauth/token_key 公开密钥
.tokenKeyAccess("permitAll()")
// 允许表单认证
.allowFormAuthenticationForClients();
}
/**
* 令牌服务配置
*
* @return 令牌服务对象
*/
public AuthorizationServerTokenServices tokenServices() {
DefaultTokenServices tokenServices = new DefaultTokenServices();
tokenServices.setTokenStore(tokenStore);
tokenServices.setSupportRefreshToken(true);
// 令牌增强
TokenEnhancerChain tokenEnhancerChain = new TokenEnhancerChain();
tokenEnhancerChain.setTokenEnhancers(Arrays.asList(jwtAccessTokenConverter));
tokenServices.setTokenEnhancer(tokenEnhancerChain);
// 令牌默认有效期2小时
tokenServices.setAccessTokenValiditySeconds(7200);
// 刷新令牌默认有效期3天
tokenServices.setRefreshTokenValiditySeconds(259200);
return tokenServices;
}
}
增加安全相关配置类
package cn.tellsea.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.authentication.AuthenticationProvider;
import org.springframework.security.authentication.dao.DaoAuthenticationProvider;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.oauth2.provider.code.AuthorizationCodeServices;
import org.springframework.security.oauth2.provider.code.InMemoryAuthorizationCodeServices;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.InMemoryTokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import org.springframework.security.provisioning.InMemoryUserDetailsManager;
/**
* security 安全相关配置类
*
* @author Tellsea
* @date 2021/12/25
*/
@Configuration
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
/**
* 安全拦截机制
*/
@Override
protected void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
// 放行
.antMatchers("/auth/**")
.permitAll()
// 其他请求必须认证通过
.anyRequest().authenticated()
.and()
.formLogin() // 允许表单登录
// .successForwardUrl("/login-success") //自定义登录成功跳转页
.and()
.csrf().disable();
}
/**
* token持久化配置
*/
@Bean
public TokenStore tokenStore() {
// 本地内存存储令牌
return new InMemoryTokenStore();
}
/**
* 密码加密器
*/
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
/**
* 认证管理器配置
*/
@Bean
@Override
protected AuthenticationManager authenticationManager() {
return authentication -> daoAuthenticationProvider().authenticate(authentication);
}
/**
* 认证是由 AuthenticationManager 来管理的,但是真正进行认证的是 AuthenticationManager 中定义的 AuthenticationProvider,用于调用userDetailsService进行验证
*/
@Bean
public AuthenticationProvider daoAuthenticationProvider() {
DaoAuthenticationProvider daoAuthenticationProvider = new DaoAuthenticationProvider();
daoAuthenticationProvider.setUserDetailsService(userDetailsService());
daoAuthenticationProvider.setHideUserNotFoundExceptions(false);
daoAuthenticationProvider.setPasswordEncoder(passwordEncoder());
return daoAuthenticationProvider;
}
/**
* 用户详情服务
*/
@Bean
@Override
protected UserDetailsService userDetailsService() {
// 测试方便采用内存存取方式
InMemoryUserDetailsManager userDetailsService = new InMemoryUserDetailsManager();
userDetailsService.createUser(User.withUsername("user_1").password(passwordEncoder().encode("123456")).authorities("ROLE_USER").build());
userDetailsService.createUser(User.withUsername("user_2").password(passwordEncoder().encode("1234567")).authorities("ROLE_USER").build());
return userDetailsService;
}
/**
* 设置授权码模式的授权码如何存取,暂时采用内存方式
*/
@Bean
public AuthorizationCodeServices authorizationCodeServices() {
return new InMemoryAuthorizationCodeServices();
}
/**
* jwt token解析器
*/
@Bean
public JwtAccessTokenConverter accessTokenConverter() {
JwtAccessTokenConverter converter = new JwtAccessTokenConverter();
// 对称密钥,资源服务器使用该密钥来验证
converter.setSigningKey("YoCiyy");
return converter;
}
}
然后启动服务,注册到 Nacos,采用密码模式访问测试,访问地址
(1)采用密码模式访问测试
http://localhost:8004/oauth/token?username=user_1&password=123456&grant_type=password&client_id=client_1&client_secret=123456

(2)校验 Token
http://localhost:8004/oauth/check_token?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDM5NzIsInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiJmYmVjNmYwMC1kZTFiLTRhZTQtOWM2YS1mNzRiYjJmNDRhMzciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.W_quiWQJG5sIL4XzzqeYhsfgOdtPbbF1rxQGzbVer3E

4、搭建服务提供者
创建 spring-cloud-alibaba-oauth2-provider 模块
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-actuator</artifactId>
</dependency>
<dependency>
<groupId>com.alibaba.cloud</groupId>
<artifactId>spring-cloud-starter-alibaba-nacos-discovery</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-starter-oauth2</artifactId>
<version>${spring-cloud-starter-oauth2.version}</version>
</dependency>
<dependency>
<groupId>org.projectlombok</groupId>
<artifactId>lombok</artifactId>
</dependency>
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-test</artifactId>
<scope>test</scope>
<exclusions>
<exclusion>
<groupId>org.junit.vintage</groupId>
<artifactId>junit-vintage-engine</artifactId>
</exclusion>
</exclusions>
</dependency>
修改 application.properties 配置文件
server.port=8005
spring.application.name=spring-cloud-alibaba-oauth2-provider
management.server.port=9005
management.endpoints.jmx.exposure.include=*
management.endpoints.web.exposure.include=*
management.endpoint.health.show-details=always
# Nacos注册信息
spring.cloud.nacos.discovery.server-addr=localhost:8848
spring.cloud.nacos.discovery.username=nacos
spring.cloud.nacos.discovery.password=nacos
spring.cloud.nacos.discovery.namespace=sandbox-configuration
启动类增加注解
@EnableDiscoveryClient
增加资源服务配置
package cn.tellsea.config;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.context.annotation.Primary;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth2.config.annotation.web.configuration.ResourceServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configurers.ResourceServerSecurityConfigurer;
import org.springframework.security.oauth2.provider.token.RemoteTokenServices;
import org.springframework.security.oauth2.provider.token.ResourceServerTokenServices;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JwtAccessTokenConverter;
import org.springframework.security.oauth2.provider.token.store.JwtTokenStore;
/**
* 资源服务配置
*
* @author Tellsea
* @date 2021/12/25
*/
@Configuration
@EnableResourceServer
public class ResourceServerConfig extends ResourceServerConfigurerAdapter {
/**
* token服务配置
*/
@Override
public void configure(ResourceServerSecurityConfigurer resources) throws Exception {
resources.tokenServices(tokenServices());
}
/**
* 路由安全认证配置
*/
@Override
public void configure(HttpSecurity http) throws Exception {
http.authorizeRequests()
// 配置/provider/oauth打头的路由需要安全认证,order无配置无需认证
.antMatchers("/provider/oauth/**").authenticated()
.and().csrf().disable();
}
/**
* jwt token 校验解析器
*/
@Bean
public TokenStore tokenStore() {
return new JwtTokenStore(accessTokenConverter());
}
/**
* Token转换器必须与认证服务一致
*/
@Bean
public JwtAccessTokenConverter accessTokenConverter() {
JwtAccessTokenConverter accessTokenConverter = new JwtAccessTokenConverter();
accessTokenConverter.setSigningKey("YoCiyy");
return accessTokenConverter;
}
/**
* 资源服务令牌解析服务
*/
@Bean
@Primary
public ResourceServerTokenServices tokenServices() {
RemoteTokenServices remoteTokenServices = new RemoteTokenServices();
remoteTokenServices.setCheckTokenEndpointUrl("http://localhost:8004/oauth/check_token");
remoteTokenServices.setClientId("client_1");
remoteTokenServices.setClientSecret("123456");
return remoteTokenServices;
}
}
增加测试的控制层
package cn.tellsea.controller;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.PathVariable;
import org.springframework.web.bind.annotation.RestController;
/**
* @author Tellsea
* @date 2021/12/25
*/
@RestController
public class MessageController {
/**
* 测试服务调用-需要授权
*
* @param message
* @return
*/
@GetMapping("/provider/oauth/{message}")
public String oauth(@PathVariable("message") String message) {
return "[服务调用成功]:" + message;
}
/**
* 测试服务调用-无需授权
*
* @param message
* @return
*/
@GetMapping("/provider/message/{message}")
public String message(@PathVariable("message") String message) {
return "[服务调用成功]:" + message;
}
}
然后启动服务

(1)请求消费提供者-无需授权
http://localhost:8005/provider/message/Tellsea
调用成功

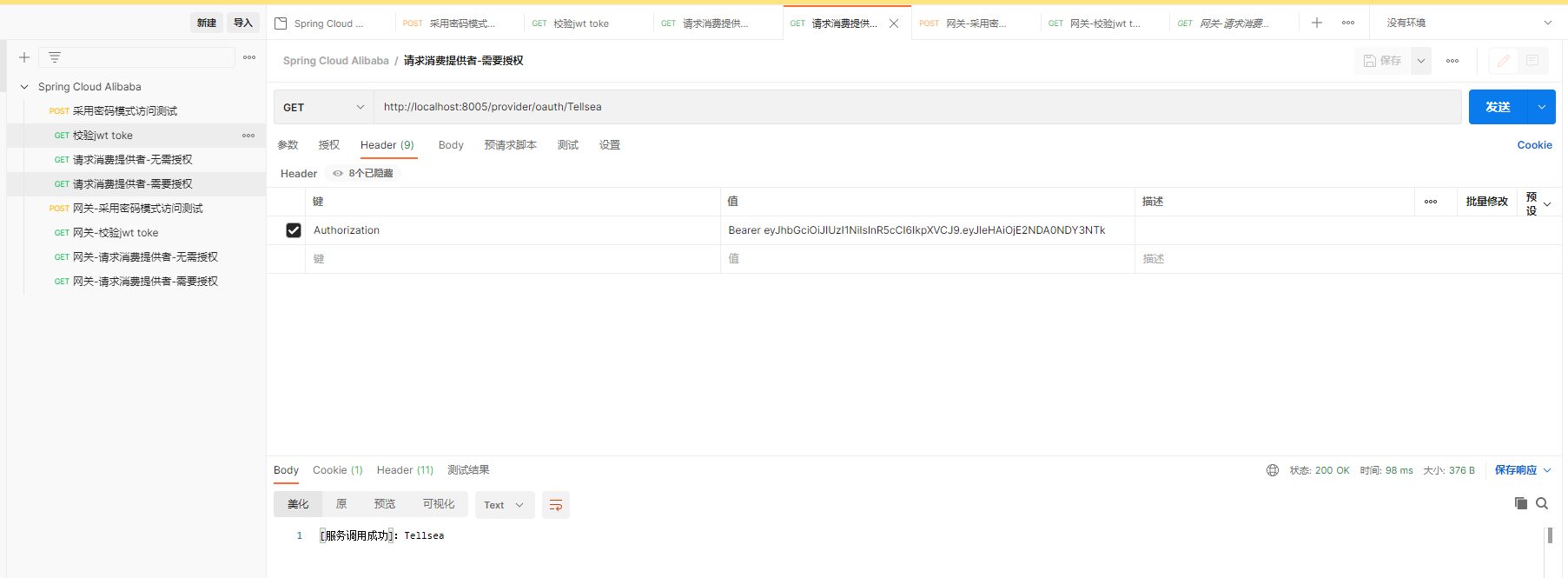
(2)请求消费提供者-需要授权
http://localhost:8005/provider/oauth/Tellsea
头部增加 Authorization 参数,参数前面增加Bearer格式
5、通过网关访问统一访问
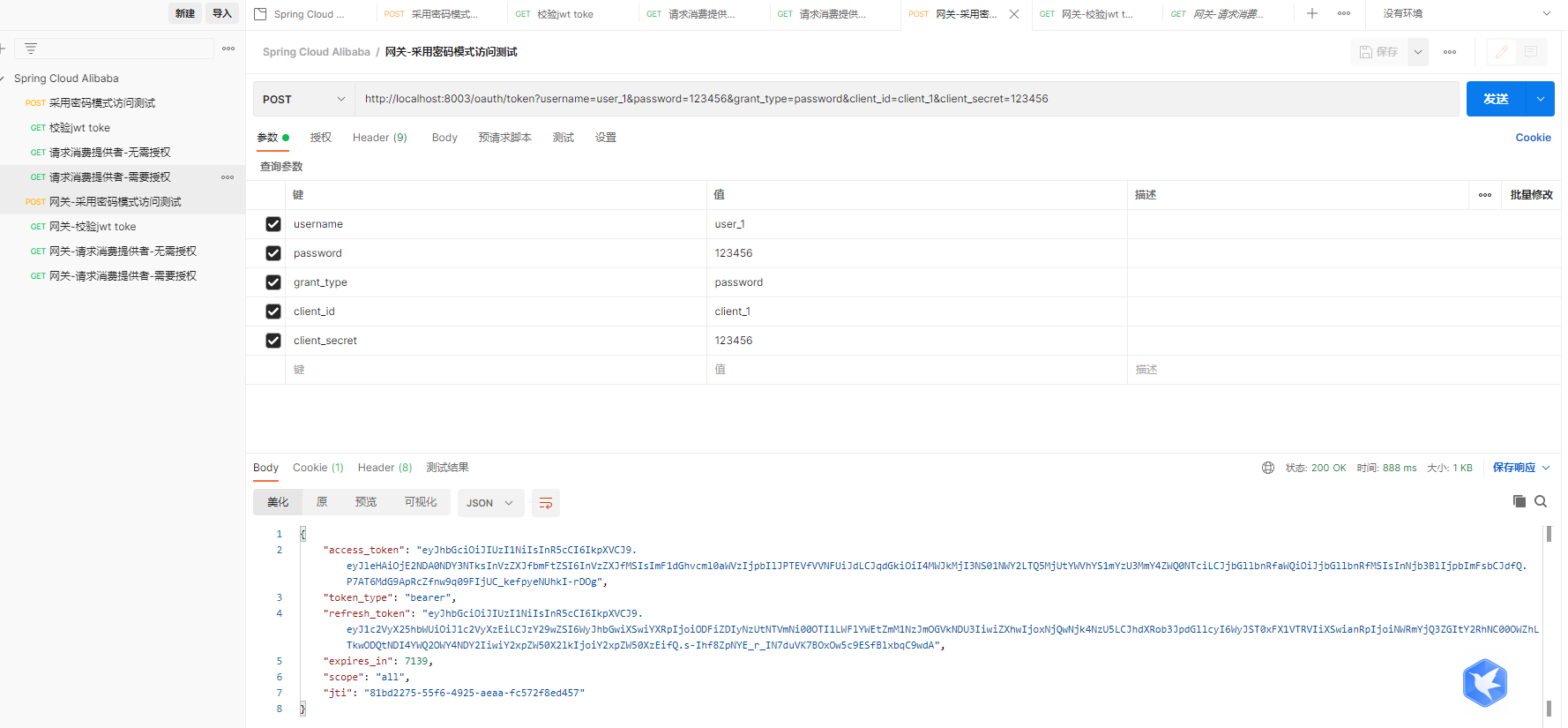
(1)网关-采用密码模式访问测试
http://localhost:8003/oauth/token?username=user_1&password=123456&grant_type=password&client_id=client_1&client_secret=123456
(2)网关-校验 jwt toke
http://localhost:8003/oauth/check_token?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDY3NTksInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiI4MWJkMjI3NS01NWY2LTQ5MjUtYWVhYS1mYzU3MmY4ZWQ0NTciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.P7AT6MdG9ApRcZfnw9q09FIjUC_kefpyeNUhkI-rDOg

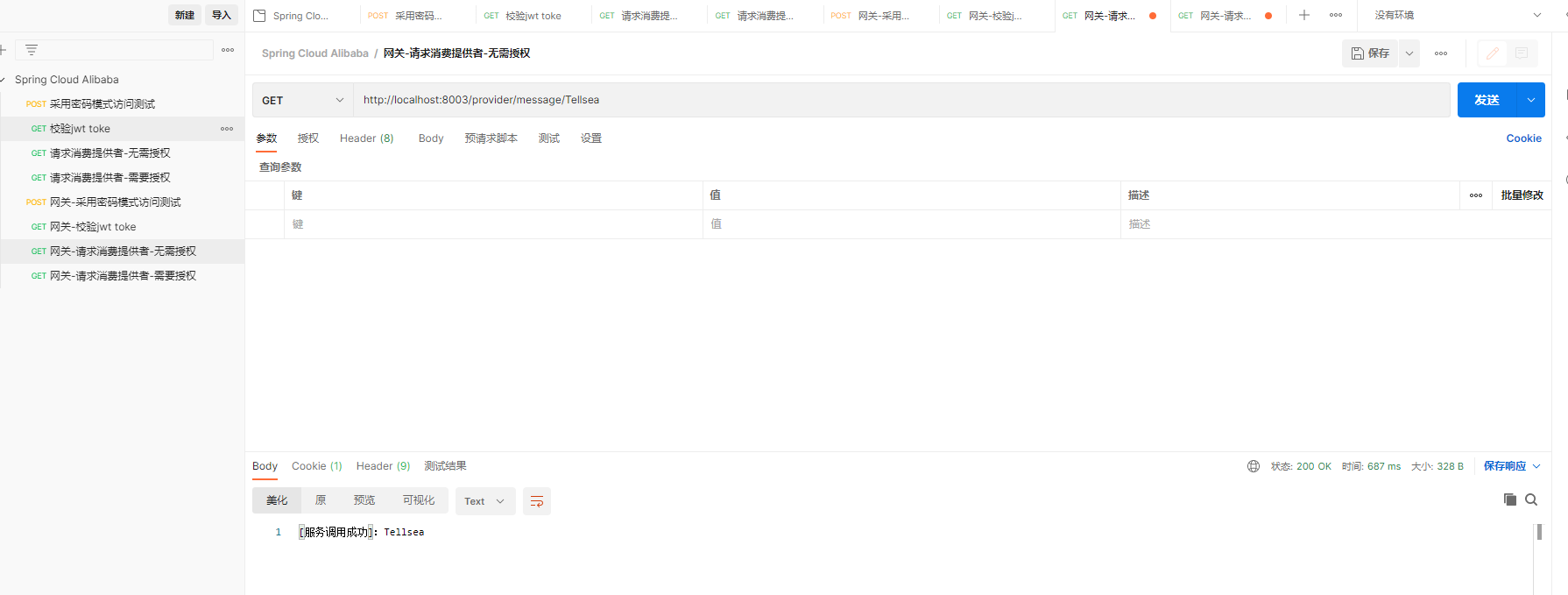
(3)网关-请求消费提供者-无需授权
http://localhost:8003/provider/message/Tellsea
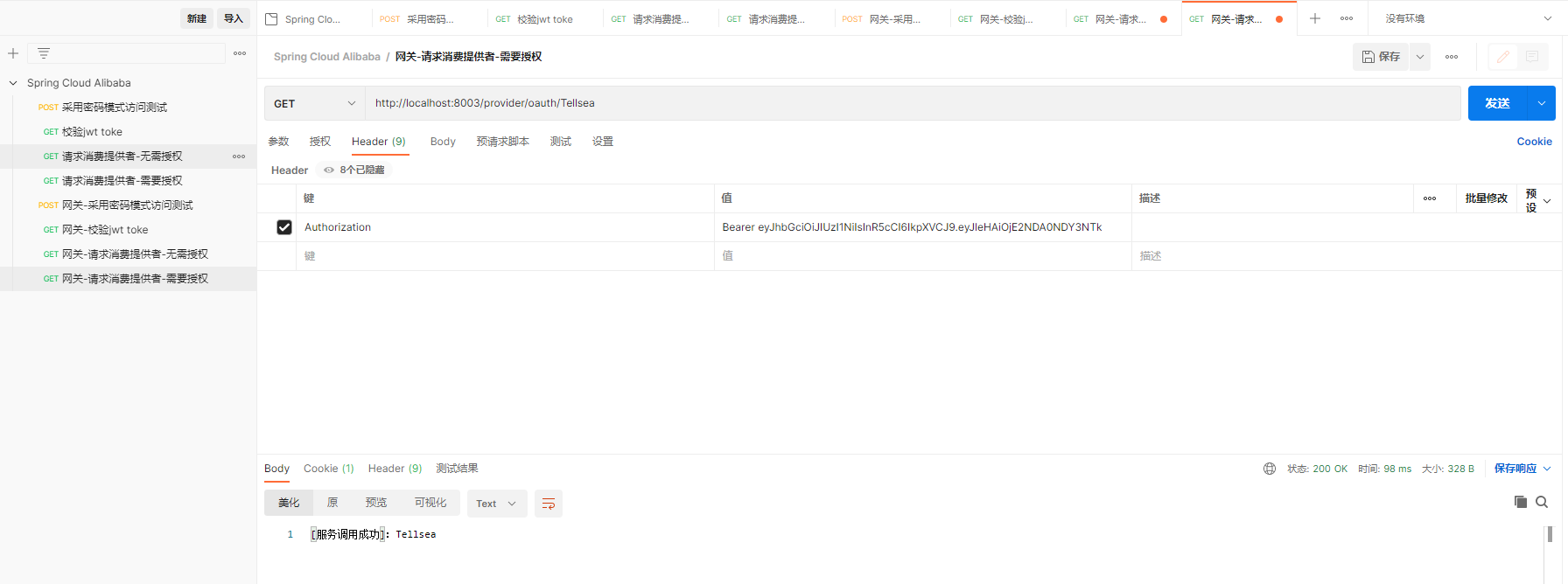
(4)网关-请求消费提供者-需要授权
http://localhost:8005/provider/oauth/Tellsea
6、Postman 测试数据
为了方便大家测试,我这里导出了 Postman 的测试数据,你们直接导入到 Postman 就可以了哟
{
"info": {
"_postman_id": "21b6178d-8464-4a1b-ab19-326f1989e5e7",
"name": "Spring Cloud Alibaba",
"schema": "https://schema.getpostman.com/json/collection/v2.1.0/collection.json"
},
"item": [
{
"name": "采用密码模式访问测试",
"request": {
"method": "POST",
"header": [],
"url": {
"raw": "http://localhost:8004/oauth/token?username=user_1&password=123456&grant_type=password&client_id=client_1&client_secret=123456",
"protocol": "http",
"host": [
"localhost"
],
"port": "8004",
"path": [
"oauth",
"token"
],
"query": [
{
"key": "username",
"value": "user_1"
},
{
"key": "password",
"value": "123456"
},
{
"key": "grant_type",
"value": "password"
},
{
"key": "client_id",
"value": "client_1"
},
{
"key": "client_secret",
"value": "123456"
}
]
}
},
"response": []
},
{
"name": "校验jwt toke",
"request": {
"method": "GET",
"header": [],
"url": {
"raw": "http://localhost:8004/oauth/check_token?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDM5NzIsInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiJmYmVjNmYwMC1kZTFiLTRhZTQtOWM2YS1mNzRiYjJmNDRhMzciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.W_quiWQJG5sIL4XzzqeYhsfgOdtPbbF1rxQGzbVer3E",
"protocol": "http",
"host": [
"localhost"
],
"port": "8004",
"path": [
"oauth",
"check_token"
],
"query": [
{
"key": "token",
"value": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDM5NzIsInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiJmYmVjNmYwMC1kZTFiLTRhZTQtOWM2YS1mNzRiYjJmNDRhMzciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.W_quiWQJG5sIL4XzzqeYhsfgOdtPbbF1rxQGzbVer3E"
}
]
}
},
"response": []
},
{
"name": "请求消费提供者-无需授权",
"request": {
"method": "GET",
"header": [],
"url": {
"raw": "http://localhost:8005/provider/message/Tellsea",
"protocol": "http",
"host": [
"localhost"
],
"port": "8005",
"path": [
"provider",
"message",
"Tellsea"
]
}
},
"response": []
},
{
"name": "请求消费提供者-需要授权",
"request": {
"method": "GET",
"header": [
{
"key": "Authorization",
"value": "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDY3NTksInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiI4MWJkMjI3NS01NWY2LTQ5MjUtYWVhYS1mYzU3MmY4ZWQ0NTciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.P7AT6MdG9ApRcZfnw9q09FIjUC_kefpyeNUhkI-rDOg",
"type": "text"
}
],
"url": {
"raw": "http://localhost:8005/provider/oauth/Tellsea",
"protocol": "http",
"host": [
"localhost"
],
"port": "8005",
"path": [
"provider",
"oauth",
"Tellsea"
]
}
},
"response": []
},
{
"name": "网关-采用密码模式访问测试",
"request": {
"method": "POST",
"header": [],
"url": {
"raw": "http://localhost:8003/oauth/token?username=user_1&password=123456&grant_type=password&client_id=client_1&client_secret=123456",
"protocol": "http",
"host": [
"localhost"
],
"port": "8003",
"path": [
"oauth",
"token"
],
"query": [
{
"key": "username",
"value": "user_1"
},
{
"key": "password",
"value": "123456"
},
{
"key": "grant_type",
"value": "password"
},
{
"key": "client_id",
"value": "client_1"
},
{
"key": "client_secret",
"value": "123456"
}
]
}
},
"response": []
},
{
"name": "网关-校验jwt toke",
"request": {
"method": "GET",
"header": [],
"url": {
"raw": "http://localhost:8003/oauth/check_token?token=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDY3NTksInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiI4MWJkMjI3NS01NWY2LTQ5MjUtYWVhYS1mYzU3MmY4ZWQ0NTciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.P7AT6MdG9ApRcZfnw9q09FIjUC_kefpyeNUhkI-rDOg",
"protocol": "http",
"host": [
"localhost"
],
"port": "8003",
"path": [
"oauth",
"check_token"
],
"query": [
{
"key": "token",
"value": "eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDY3NTksInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiI4MWJkMjI3NS01NWY2LTQ5MjUtYWVhYS1mYzU3MmY4ZWQ0NTciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.P7AT6MdG9ApRcZfnw9q09FIjUC_kefpyeNUhkI-rDOg"
}
]
}
},
"response": []
},
{
"name": "网关-请求消费提供者-无需授权",
"request": {
"method": "GET",
"header": [],
"url": {
"raw": "http://localhost:8003/provider/message/Tellsea",
"protocol": "http",
"host": [
"localhost"
],
"port": "8003",
"path": [
"provider",
"message",
"Tellsea"
]
}
},
"response": []
},
{
"name": "网关-请求消费提供者-需要授权",
"request": {
"method": "GET",
"header": [
{
"key": "Authorization",
"value": "Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJleHAiOjE2NDA0NDY3NTksInVzZXJfbmFtZSI6InVzZXJfMSIsImF1dGhvcml0aWVzIjpbIlJPTEVfVVNFUiJdLCJqdGkiOiI4MWJkMjI3NS01NWY2LTQ5MjUtYWVhYS1mYzU3MmY4ZWQ0NTciLCJjbGllbnRfaWQiOiJjbGllbnRfMSIsInNjb3BlIjpbImFsbCJdfQ.P7AT6MdG9ApRcZfnw9q09FIjUC_kefpyeNUhkI-rDOg",
"type": "text"
}
],
"url": {
"raw": "http://localhost:8003/provider/oauth/Tellsea",
"protocol": "http",
"host": [
"localhost"
],
"port": "8003",
"path": [
"provider",
"oauth",
"Tellsea"
]
}
},
"response": []
}
]
}
如下两种模式,直接调用服务的,和通过网关访问的

微信公众号























 3899
3899











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










