https://help.aliyun.com/document_detail/160093.html
1双向认证过程:
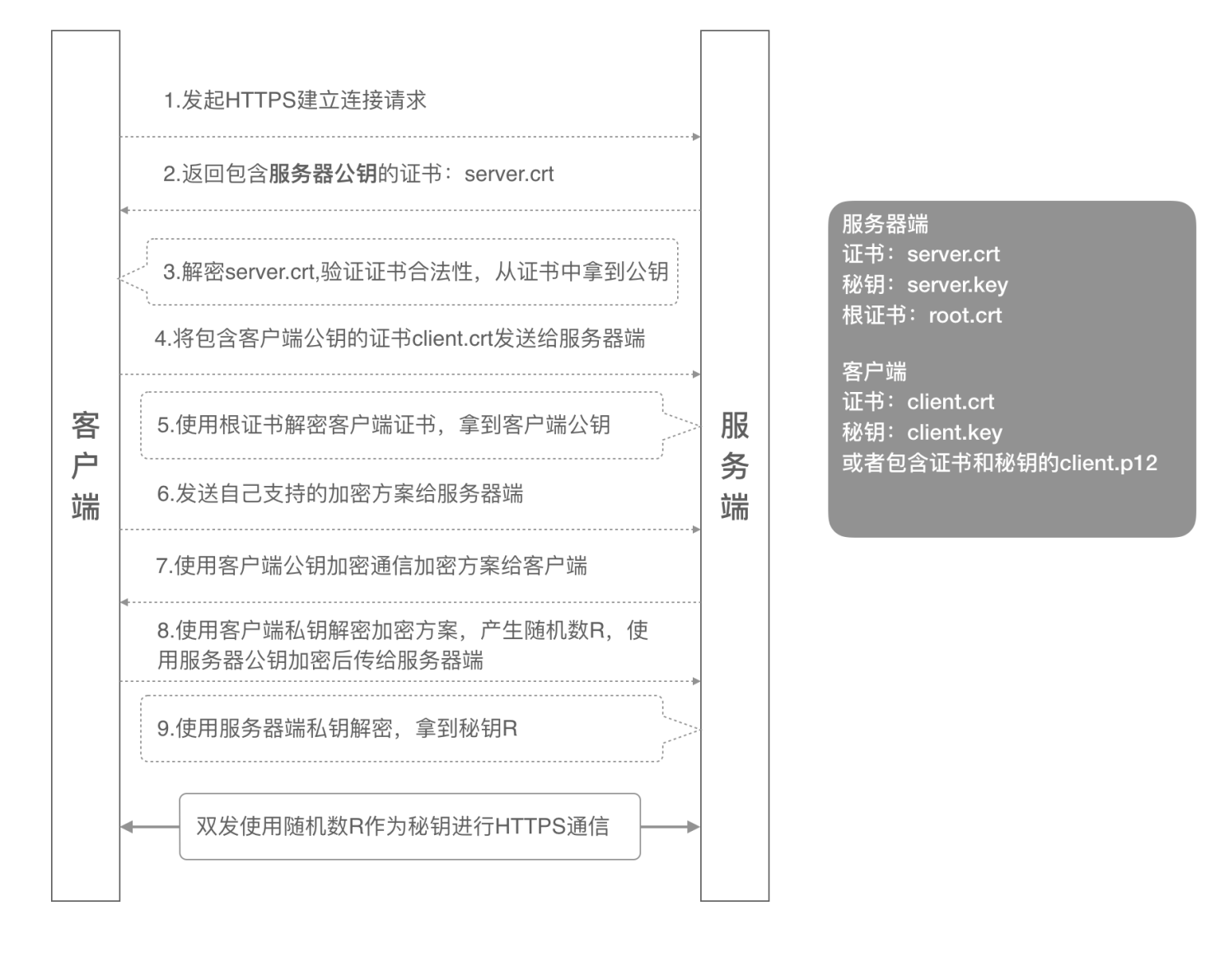
从图中可知,整个双向认证的流程需要六个证书文件:
-
服务器端公钥证书:server.crt
-
服务器端私钥文件:server.key
-
根证书:root.crt
-
客户端公钥证书:client.crt
-
客户端私钥文件:client.key
-
客户端集成证书(包括公钥和私钥,用于浏览器访问场景):client.p12
证书生成的内在逻辑示意图:

2、证书生成流程
以下是相对与自签证书
===生成根证书===
生成根私钥
openssl genrsa -out root.key 3072
生成根的csr文件
openssl req -new -out root.csr -key root.key
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Guangdong
Locality Name (eg, city) [Default City]:Shenzhen
Organization Name (eg, company) [Default Company Ltd]:3w
Organizational Unit Name (eg, section) []:Dev
Common Name (eg, your name or your servers hostname) []:root
Email Address []:123@qq.com
A challenge password []:
An optional company name []:
根据csr文件和私钥生成证书
openssl x509 -req -in root.csr -out root.crt -signkey root.key -CAcreateserial -days 3650
=================================================================================
=============================server============================================
===生成服务端证书===
openssl genrsa -out server.key 3072
openssl req -new -out server.csr -key server.key
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Guangdong
Locality Name (eg, city) [Default City]:Shenzhen
Organization Name (eg, company) [Default Company Ltd]:3w
Organizational Unit Name (eg, section) []:Dev
Common Name (eg, your name or your servers hostname) []:server
Email Address []:123@qq.com
A challenge password []:
An optional company name []:
//服务端证书 使用根证书进行签名认证
openssl x509 -req -in server.csr -out server.crt -signkey server.key -CA root.crt -CAkey root.key -CAcreateserial -days 3650
=================================================================================
=============================client============================================
===生成客户端证书===
openssl genrsa -out client.key 3072
openssl req -new -out client.csr -key client.key
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Guangdong
Locality Name (eg, city) [Default City]:Shenzhen
Organization Name (eg, company) [Default Company Ltd]:3w
Organizational Unit Name (eg, section) []:Dev
Common Name (eg, your name or your servers hostname) []:client
Email Address []:123@qq.com
A challenge password []:
An optional company name []:
//客户端证书 使用根证书进行签名认证
openssl x509 -req -in client.csr -out client.crt -signkey client.key -CA root.crt -CAkey root.key -CAcreateserial -days 3650
=================================================================================
生成pfx文件:
openssl pkcs12 -export -in test.pem -inkey server.key -out test.pfx -passout pass:123456
PS:
单向认证流程中,服务器端保存着公钥证书和私钥两个文件,整个握手过程如下:








 该文详细介绍了双向认证的过程,涉及六个关键证书文件:server.crt,server.key,root.crt,client.crt,client.key,client.p12。并提供了生成根证书、服务器端证书和客户端证书的openssl命令行步骤。
该文详细介绍了双向认证的过程,涉及六个关键证书文件:server.crt,server.key,root.crt,client.crt,client.key,client.p12。并提供了生成根证书、服务器端证书和客户端证书的openssl命令行步骤。

















 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








