文章目录
- Investigating Windows
- Whats the version and year of the windows machine?
- Which user logged in last?
- When did John log onto the system last?
- What IP does the system connect to when it first starts?
- What two accounts had administrative privileges (other than the Administrator user)?
- Whats the name of the scheduled task that is malicous.
- What file was the task trying to run daily?
- What port did this file listen locally for?
- When did Jenny last logon?
- At what date did the compromise take place?
- At what time did Windows first assign special privileges to a new logon?
- What tool was used to get Windows passwords?
- What was the attackers external control and command servers IP?
- What was the extension name of the shell uploaded via the servers website?
- What was the last port the attacker opened?
- Check for DNS poisoning, what site was targeted?
- 参考文章
Investigating Windows
tryhackme的一个房间,一个windows应急响应案例.
我们登陆到一台被入侵的windows机器,要对他进行溯源取证.
Whats the version and year of the windows machine?
systeminfo

Which user logged in last?
查找用户登陆记录
1.运行,输入: gpedit.msc
2.“计算机配置”→“Windows设置”→“安全设置”→“本地策略”→“审核策略”,双击其中的“审核帐户登陆事件”
==>审核登录事件–>勾上成功/失败–>点击应用–>点击确定
3.控制面板–>系统和安全–>查看事件日志–>事件查看器–>windows日志–>安全,便可以看到用户的登录和注销以及账户名等信息
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-CoB5St7M-1649849388982)(Investigat%20fff07/Untitled%201.png)]](https://i-blog.csdnimg.cn/blog_migrate/6a4cb2dda90d3f1a71e6da4236cd9ba2.png)
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-mU90gpV5-1649849388983)(Investigat%20fff07/Untitled%202.png)]](https://i-blog.csdnimg.cn/blog_migrate/775cb29881759c03ca35baf71a2ca3f0.png)
When did John log onto the system last?
net user John 可以查看这个用户的信息
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-IUlYBNl0-1649849388983)(Investigat%20fff07/Untitled%203.png)]](https://i-blog.csdnimg.cn/blog_migrate/db2db6972512c6e4a44ccab1ad97c786.png)
What IP does the system connect to when it first starts?
这个容易忽略了,刚开始开机的时候有个窗口,不要轻易关掉
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-i7VNRo0s-1649849388983)(Investigat%20fff07/Untitled%204.png)]](https://i-blog.csdnimg.cn/blog_migrate/6bd89ceed4ee633b7d2a36befb2b9d0b.png)
What two accounts had administrative privileges (other than the Administrator user)?
Jenny,Guest

Whats the name of the scheduled task that is malicous.
查看计划任务
命令行:taskschd.msc

What file was the task trying to run daily?
nc.ps1
What port did this file listen locally for?
1348 -l参数就是指定本地监听端口
When did Jenny last logon?
net user Jenny查看
At what date did the compromise take place?
什么时候被入侵的…这个怎么看呀.要看通过什么漏洞打进来的?
根据账号Jenny的创建时间 还有呢?
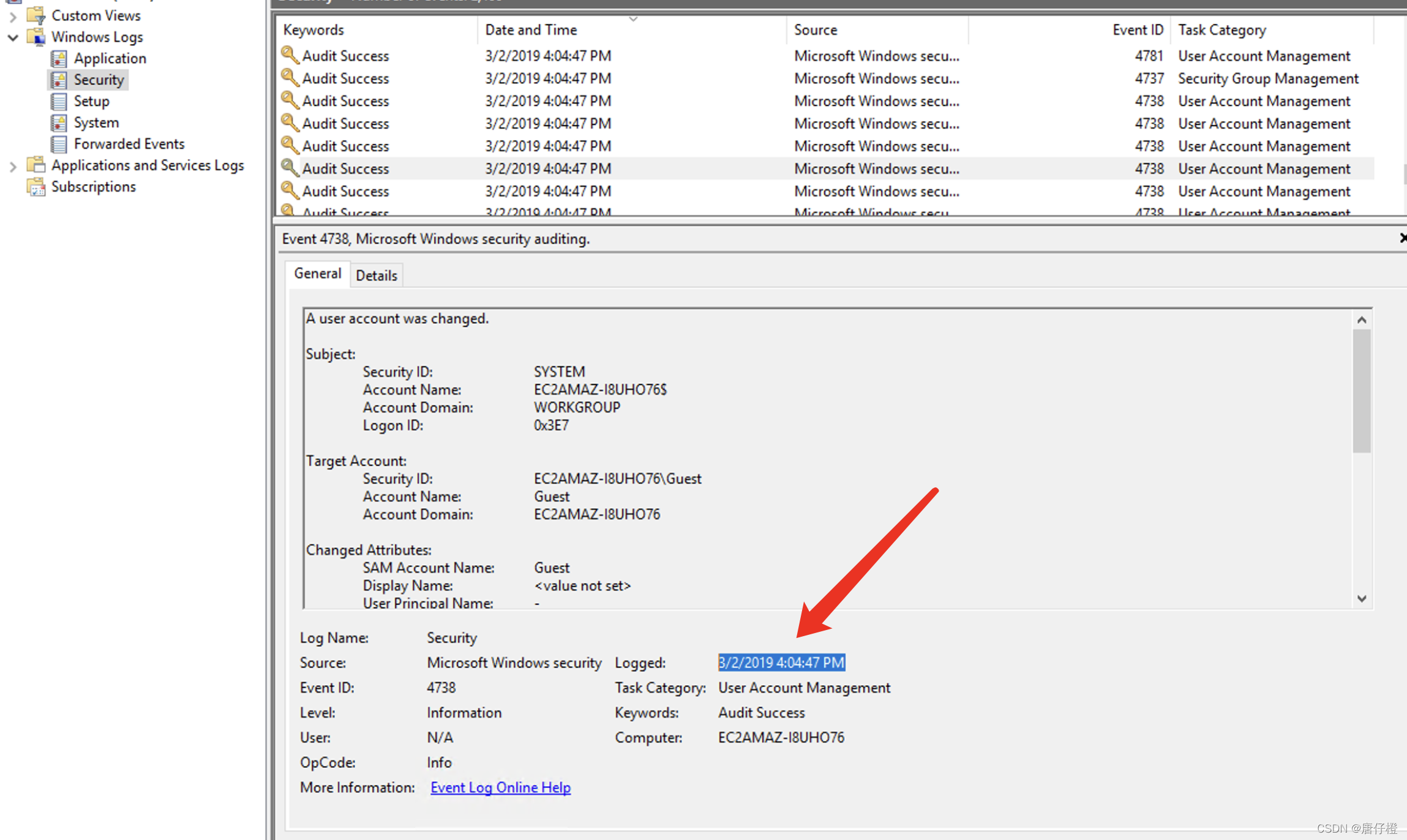
At what time did Windows first assign special privileges to a new logon?
这个意思是什么时候给普通用户 管理员权限的,这个应该可以看日志吧.
![[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-me53sbra-1649849388984)(Investigat%20fff07/Untitled%207.png)]](https://i-blog.csdnimg.cn/blog_migrate/8ac779d3b2a6128d09f327ef7d2488e3.png)
What tool was used to get Windows passwords?
在攻击者留下的目录中寻找
mimikatz

What was the attackers external control and command servers IP?
找攻击者的c2ip地址
C:\Windows\System32\drivers\etc\hosts
将google的ip替换成了攻击者自己的

What was the extension name of the shell uploaded via the servers website?
上传的webshell的后缀名.
找到web目录就会发现

What was the last port the attacker opened?
查看最后开放的端口
防火墙里可以查看开放的端口,默认按照时间排序吗??

Check for DNS poisoning, what site was targeted?
hosts文件中,google.com被替换了
参考文章
https://blog.csdn.net/CSNDRYL/article/details/77194060
https://shamsher-khan-404.medium.com/investigating-windows-tryhackme-writeup-65d0ceeaca90











 本文详细描述了如何在InvestigatingWindows TryHackMe挑战中追踪Windows系统入侵痕迹,包括检查系统版本、用户登录、恶意任务、权限分配、密码获取、C2服务器IP、恶意文件、DNS污染等关键步骤。
本文详细描述了如何在InvestigatingWindows TryHackMe挑战中追踪Windows系统入侵痕迹,包括检查系统版本、用户登录、恶意任务、权限分配、密码获取、C2服务器IP、恶意文件、DNS污染等关键步骤。
















 337
337

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








