原文链接:(华为配置篇)防火墙USG6000实现服务器的负载均衡
实验拓扑
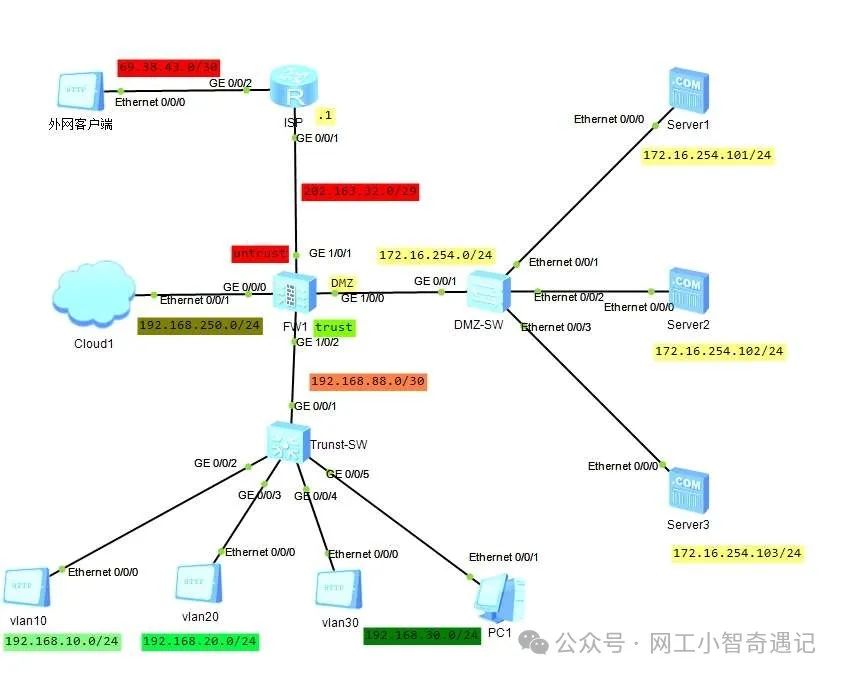
实验需求
小智公司内建设了一个网站,由于网站的访问量很大,为了实现访问的可靠性,在内部部署了三台同等性能的服务器做负载均衡,内网及外网所有用户均可通过企业申请的公网地址访问。
VLAN与IP地址规划
| 区域 | 项目 | VLAN | IP地址 | 备注 |
| Trust区域 | 内网用户1 | 10 | 192.168.10.0/24 | 网关:192.168.10.254 |
| 内网用户2 | 20 | 192.168.20.0/24 | 网关:192.168.20254 | |
| 内网用户3 | 30 | 192.168.30.0/24 | 网关:192.168.30.254 | |
| 内网核心交换机与防火墙对接 | 88 | 192.168.88.0/30 | 防火墙:192.168.88.1/30 交换机:192.168.88.2/30 | |
| 防火墙管理 | N/A | 192.168.250.0/24 | 账号:admin 密码:Qw!@123123 | |
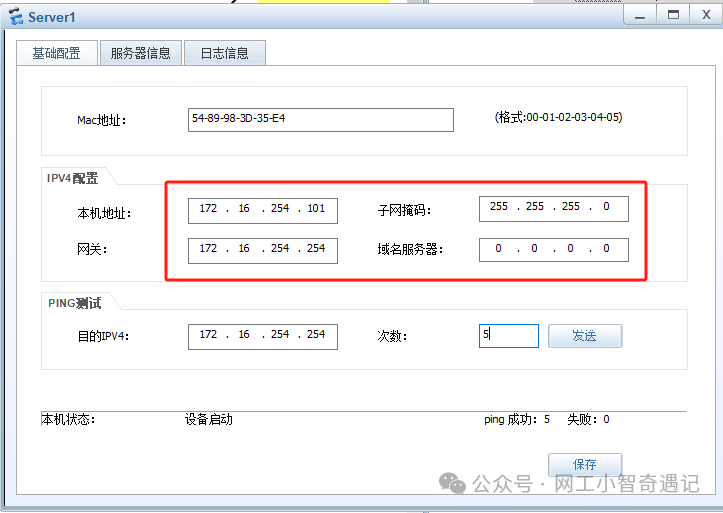
| DMZ区域 | Server1 | N/A | 172.16.254.101/24 | 网关:172.168.254.254 虚拟IP:202.163.32.3/29 |
| Server2 | N/A | 172.16.254.102/24 | ||
| Server3 | N/A | 172.16.254.103/24 | ||
| Untrust区域 | 防火墙与运营商ISP对接 | N/A | 202.163.32.0/29 | 防火墙:202.163.32.2/29 ISP:202.163.32.1/26 |
| ISP | N/A | 69.38.43.0/30 | 模拟外网客户端地址,loopback0:114.114.114.114 |
配置过程
配置防火墙接口地址并加入安全区域
| 接口 | G0/0/0 | G1/0/0 | G1/0/1 | G1/0/2 |
| 安全区域 | Trust | DMZ | Untrust | Trust |
| IP地址 | 192.168.250.100/24 | 172.16.254.254/24 | 202.163.32.2/29 | 192.168.88.1/30 |
#
interface GigabitEthernet0/0/0
ip address 192.168.250.100 255.255.255.0
alias GE0/METH
service-manage all permit
#
interface GigabitEthernet1/0/0
description DMZ
ip address 172.16.254.254 255.255.255.0
service-manage ping permit
#
interface GigabitEthernet1/0/1
description untrust
ip address 202.163.32.2 255.255.255.248
gateway 202.163.32.1
#
interface GigabitEthernet1/0/2
description trust
ip address 192.168.88.1 255.255.255.252
service-manage ping permit
#
#
firewall zone trust
add interface GigabitEthernet0/0/0
add interface GigabitEthernet1/0/2
#
firewall zone untrust
add interface GigabitEthernet1/0/1
#
firewall zone dmz
add interface GigabitEthernet1/0/0
#
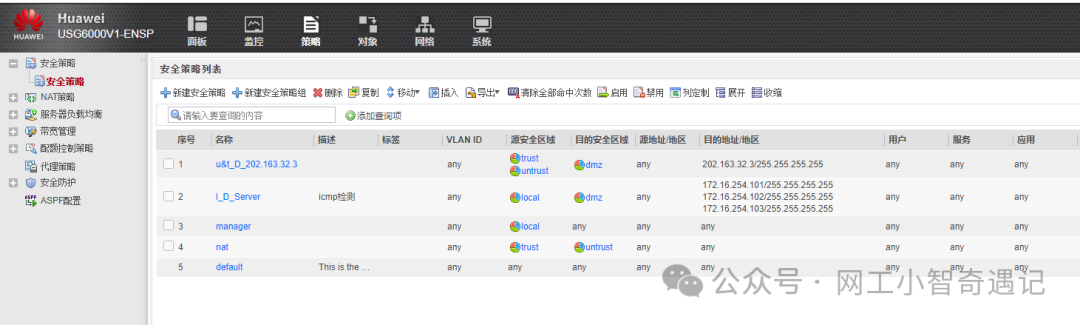
配置防火墙安全策略
内外网用户trust/untrust区域到服务器集群DMZ的安全策略
允许Internet用户访问内网的Web服务器,策略的目的地址为虚拟服务器的IP地址202.163.32.3/29。
配置local到任意区域的安全策略
用于管理员管理调试;
用于防火墙向实际服务器发送健康探测icmp报文。
配置内网用户上网的安全策略
允许用内网户访问Internet。
| 策略规则名 | u&t_D_202.163.32.3 | manager | nat |
| 源区域 | Untrust/trust | local | trust |
| 源地址/地区 | any | any | any |
| 目的区域 | DMZ | any | any |
| 目的地址/地区 | 202.163.32.3/32 | any | Untrust |
| 动作 | permit | permit | permit |
#
security-policy
rule name u&t_D_202.163.32.3
source-zone trust
source-zone untrust
destination-zone dmz
destination-address 202.163.32.3 mask 255.255.255.255
action permit
rule name l_D_Server
description icmp
source-zone local
destination-zone dmz
destination-address 172.16.254.101 mask 255.255.255.255
destination-address 172.16.254.102 mask 255.255.255.255
destination-address 172.16.254.103 mask 255.255.255.255
action permit
rule name manager
source-zone local
action permit
rule name nat
source-zone trust
destination-zone untrust
action permit
#
配置实服务器组/虚拟服务器
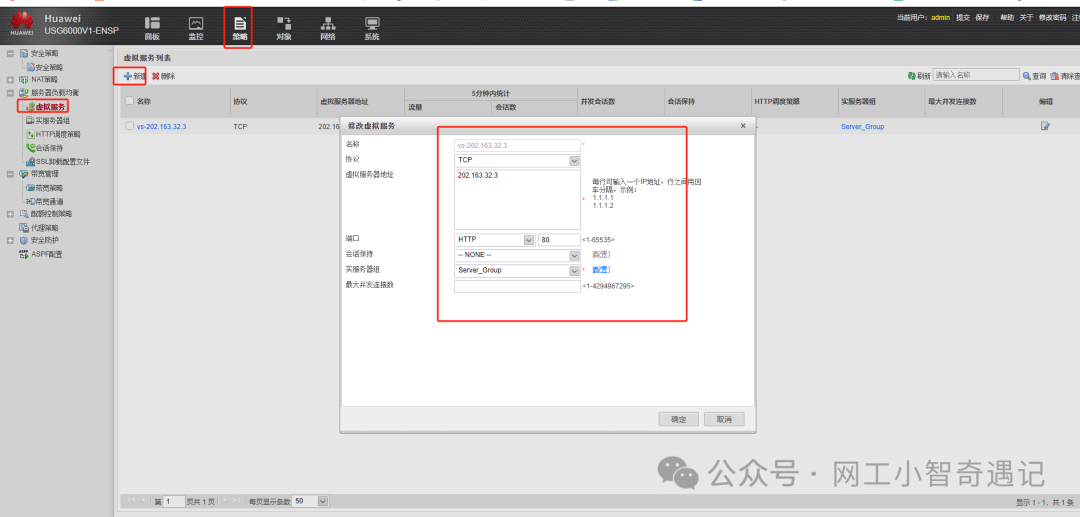
#
slb
group 0 Server_Group
metric weight-roundrobin
health-check type icmp
rserver 0 rip 172.16.254.101 port 80 weight 1
rserver 1 rip 172.16.254.102 port 80 weight 1
rserver 2 rip 172.16.254.103 port 80 weight 1
action optimize
vserver 0 vs-202.163.32.3
vip 0 202.163.32.3
protocol tcp
vport 80
group Server_Group
#
服务器配置IP地址及开启HTTP服务
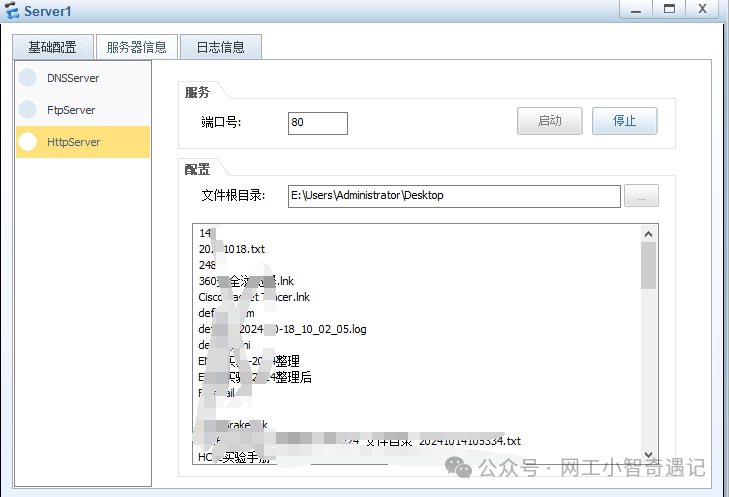
ISP及外网客户端配置
#
interface GigabitEthernet0/0/1
ip address 202.163.32.1 255.255.255.248
#
interface GigabitEthernet0/0/2
ip address 69.38.43.1 255.255.255.252
#
interface LoopBack0
ip address 114.114.114.114 255.255.255.255
#
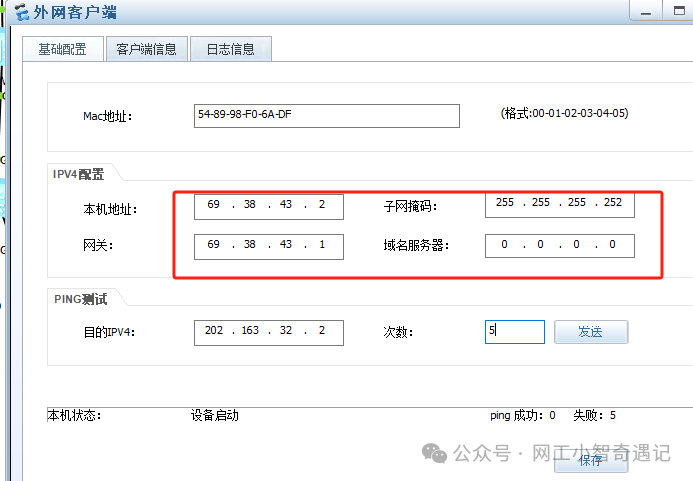
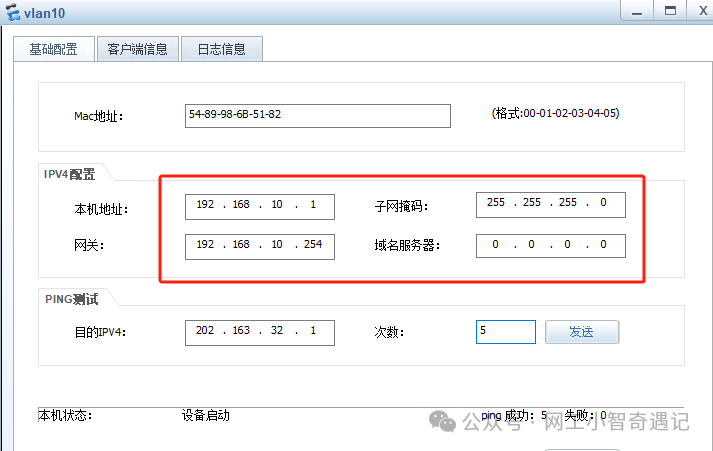
内网设备交换机及路由配置
内网交换机
#
sysname Trust-SW
#
vlan batch 10 20 30 88
#
interface Vlanif10
ip address 192.168.10.254 255.255.255.0
#
interface Vlanif20
ip address 192.168.20.254 255.255.255.0
#
interface Vlanif30
ip address 192.168.30.254 255.255.255.0
#
interface Vlanif88
ip address 192.168.88.2 255.255.255.252
#
interface GigabitEthernet0/0/1
port link-type access
port default vlan 88
#
interface GigabitEthernet0/0/2
port link-type access
port default vlan 10
#
interface GigabitEthernet0/0/3
port link-type access
port default vlan 20
#
interface GigabitEthernet0/0/4
port link-type access
port default vlan 30
#
interface GigabitEthernet0/0/5
port link-type access
port default vlan 30
#
ip route-static 0.0.0.0 0.0.0.0 192.168.88.1
#
防火墙
#
ip route-static 192.168.10.0 255.255.255.0 192.168.88.2
ip route-static 192.168.20.0 255.255.255.0 192.168.88.2
ip route-static 192.168.30.0 255.255.255.0 192.168.88.2
#
内网终端
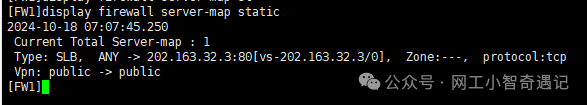
配置完成后测试
查看静态Server-map表
存在相应表项证明服务器负载均衡功能配置成功。
外网客户端访问服务器
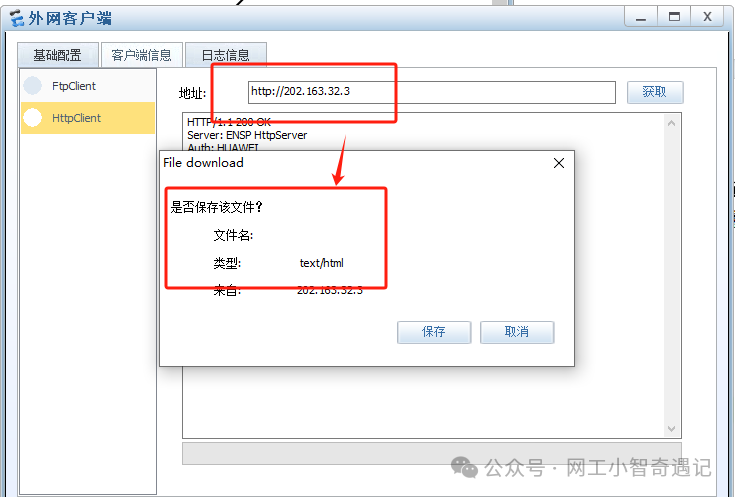
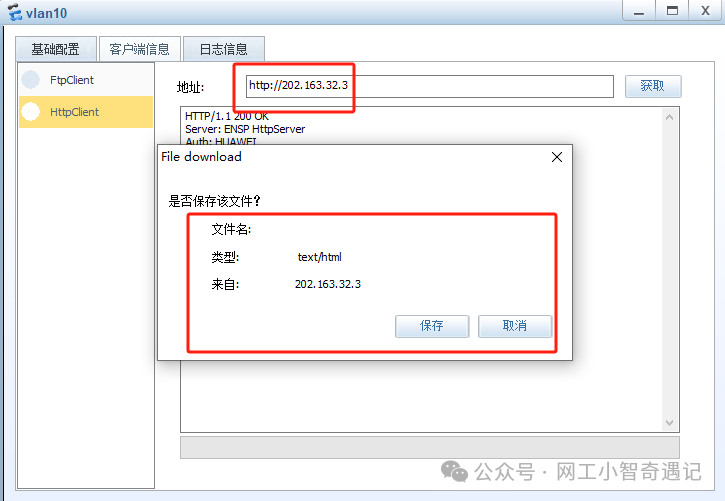
内网终端访问服务器
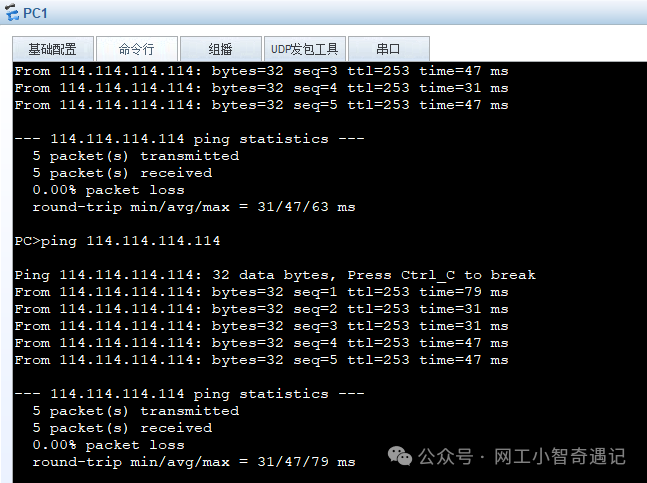
内网终端访问互联网
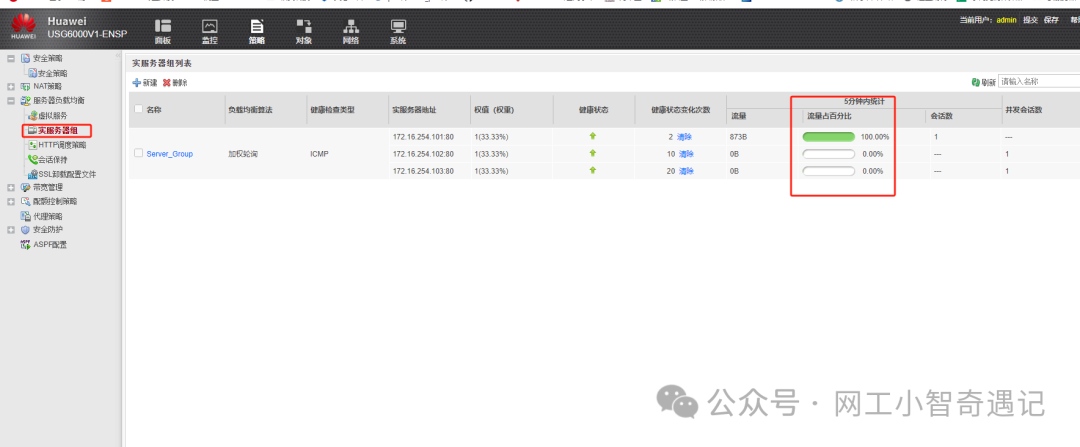
查看服务器流量占比
测试一段时间后,在实服务器组列表中看到流量占百分比。

























 351
351

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










