1、Kubectl suddenly stops responding to your commands. Check it out! Someone recently modified the /etc/kubernetes/manifests/etcd.yaml file
You are asked to investigate and fix the issue. Once you fix the issue wait for sometime for kubectl to respond. Check the logs of the ETCD container.
A:
The certificate file used here is incorrect. It is set to /etc/kubernetes/pki/etcd/server-certificate.crt which does not exist. As we saw in the previous questions the correct path should be /etc/kubernetes/pki/etcd/server.crt.
>root@controlplane:~# ls -l /etc/kubernetes/pki/etcd/server* | grep .crt
-rw-r--r-- 1 root root 1188 May 20 00:41 /etc/kubernetes/pki/etcd/server.crt
root@controlplane:~#
Update the YAML file with the correct certificate path and wait for the ETCD pod to be recreated. wait for the kube-apiserver to get to a Ready state.
NOTE: It may take a few minutes for the kubectl commands to work again so please be patient.
2、The kube-api server stopped again! Check it out. Inspect the kube-api server logs and identify the root cause and fix the issue.
Run docker ps -a command to identify the kube-api server container. Run docker logs container-id command to view the logs.
A:
如果我们在控制面上检查kube-apiserver容器,我们可以看到它经常退出
root@controlplane:~# docker ps -a | grep kube-apiserver
8af74bd23540 ca9843d3b545 "kube-apiserver --ad…" 39 seconds ago Exited (1) 17 seconds ago k8s_kube-apiserver_kube-apiserver-controlplane_kube-system_f320fbaff7813586592d245912262076_4
c9dc4df82f9d k8s.gcr.io/pause:3.2 "/pause" 3 minutes ago Up 3 minutes k8s_POD_kube-apiserve-controlplane_kube-system_f320fbaff7813586592d245912262076_1
root@controlplane:~#
如果我们现在检查这个退出的容器的日志,我们将看到以下错误:
root@controlplane:~# docker logs 8af74bd23540 --tail=2
W0520 01:57:23.333002 1 clientconn.go:1223] grpc: addrConn.createTransport failed to connect to {https://127.0.0.1:2379 <nil> 0 <nil>}. Err :connection error: desc = "transport: authentication handshake failed: x509: certificate signed by unknown authority". Reconnecting...
Error: context deadline exceeded
root@controlplane:~#
这说明kube-apiserver使用的ETCD CA证书有问题。修改为使用/etc/kubernetes/pki/etcd/ca.crt文件
保存YAML文件之后,等待kube-apiserver pod准备就绪。这可能需要几分钟
3、I would like to use the dev-user to access test-cluster-1. Set the current context to the right one so I can do that.
Once the right context is identified, use the kubectl config use-context command.
oot@controlplane ~ ➜ kubectl config --kubeconfig=/root/my-kube-config use-context research #设置
Switched to context "research".
root@controlplane ~ ➜ kubectl config --kubeconfig=/root/my-kube-config current-context #查看
research
4、What are the resources the kube-proxy role in the kube-system namespace is given access to?
root@controlplane ~ ➜ kubectl describe role -n kube-system kube-proxy
Name: kube-proxy
Labels: <none>
Annotations: <none>
PolicyRule:
Resources Non-Resource URLs Resource Names Verbs
--------- ----------------- -------------- -----
configmaps [] [kube-proxy] [get]
5、Which account is the kube-proxy role assigned to?
root@controlplane ~ ➜ kubectl describe rolebinding kube-proxy -n kube-system
Name: kube-proxy
Labels: <none>
Annotations: <none>
Role:
Kind: Role
Name: kube-proxy
Subjects:
Kind Name Namespace
---- ---- ---------
Group system:bootstrappers:kubeadm:default-node-token
6、A user dev-user is created. User’s details have been added to the kubeconfig file. Inspect the permissions granted to the user. Check if the user can list pods in the default namespace.
Use the --as dev-user option with kubectl to run commands as the dev-user.
root@controlplane ~ ➜ kubectl get pods --as dev-user
Error from server (Forbidden): pods is forbidden: User "dev-user" cannot list resource "pods" in API group "" in the namespace "default"
7、Create the necessary roles and role bindings required for the dev-user to create, list and delete pods in the default namespace.
Use the given spec:
Role: developer
Role Resources: pods
Role Actions: list
Role Actions: create
Role Actions: delete
RoleBinding: dev-user-binding
RoleBinding: Bound to dev-user
root@controlplane ~ ➜ kubectl create role developer --verb=list,create,delete --resource=pods
role.rbac.authorization.k8s.io/developer created
root@controlplane ~ ➜ kubectl create rolebinding dev-user-binding --role=developer --user=dev-user
rolebinding.rbac.authorization.k8s.io/dev-user-binding created
注:创建了证书之后,为了让这个用户能访问 Kubernetes 集群资源,现在就要创建 Role 和 RoleBinding 了。
下面是为这个新用户创建 Role 的示例命令:
kubectl create role developer --verb=list,create,delete --resource=pods
下面是为这个新用户创建 RoleBinding 的示例命令
kubectl create rolebinding dev-user-binding --role=developer --user=dev-user
8、How many network policies do you see in the environment?
root@controlplane ~ ➜ kubectl get networkpolicies
NAME POD-SELECTOR AGE
payroll-policy name=payroll 2m58s
9、Create a network policy to allow traffic from the Internal application only to the payroll-service and db-service.
Use the spec given below. You might want to enable ingress traffic to the pod to test your rules in the UI.
CheckCompleteIncomplete
Policy Name: internal-policy
Policy Type: Egress
Egress Allow: payroll
Payroll Port: 8080
Egress Allow: mysql
MySQL Port: 3306
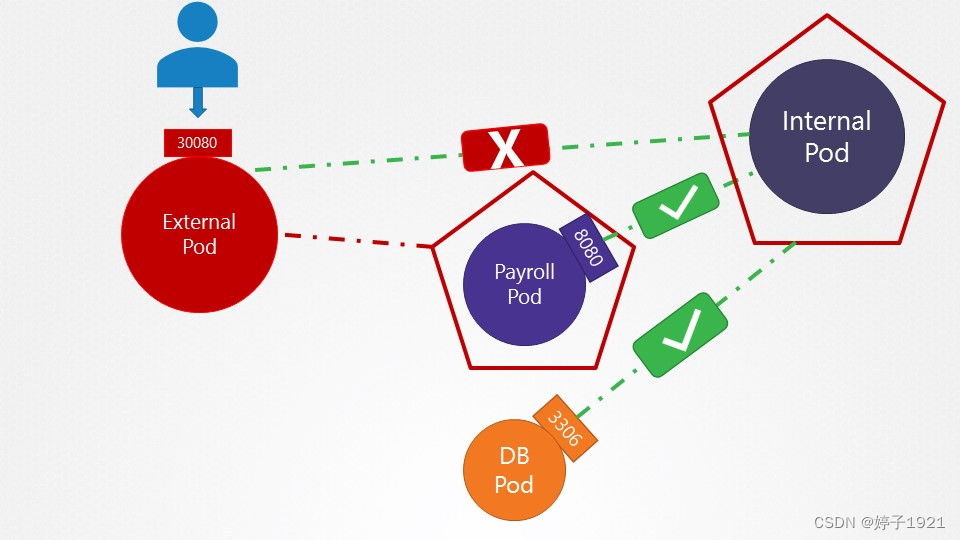
vim internal-policy.yaml
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: internal-policy
namespace: default
spec:
podSelector:
matchLabels:
role: internal
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
name: payroll
ports:
- protocol: TCP
port: 8080
- to:
- podSelector:
matchLabels:
name: mysql
ports:
- protocol: TCP
port: 3306




















 1375
1375











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








