httpd虚拟主机
1.虚拟主机
虚拟主机有三类:
- 相同IP不同端口
- 不同IP相同端口
- 相同IP相同端口不同域名
[root@hwf ~]# find / -name *vhosts.conf //查找到虚拟主机的文件
/usr/share/doc/httpd/httpd-vhosts.conf
[root@hwf ~]# cd /etc/httpd/conf.d
[root@hwf conf.d]# cp /usr/share/doc/httpd/httpd-vhosts.conf . //将他复制到当前目录下
[root@hwf conf.d]# ls
autoindex.conf httpd-vhosts.conf README userdir.conf welcome.conf
1.1相同ip不同端口虚拟主机
[root@hwf conf.d]# vim httpd-vhosts.conf //编辑我们要的虚拟主机
[root@hwf conf.d]# cat httpd-vhosts.conf | tail -15
<VirtualHost *:80>
DocumentRoot "/var/www/html/zhuawawa" //网站根目录
ServerName www.zhuawawa.com //域名
ErrorLog "/var/log/httpd/www.zhuawawa.com-error_log" //错误日志
CustomLog "/var/log/httpd/dummy-host2.example.com-access_log" common //访问日志
</VirtualHost>
Listen 81 //添加81监听端口
<VirtualHost *:81>
DocumentRoot "/var/www/html/tankedazhan"
ServerName www.tankedazhan.com
ErrorLog "/var/log/httpd/www.tankedazhan.com-error_log"
CustomLog "/var/log/httpd/www.tankedazhan.com-access_log" common
</VirtualHost>
[root@hwf conf.d]#
[root@hwf ~]# cd /var/www/html/
[root@hwf html]# ls
[root@hwf html]# mkdir zhuawawa //创建抓娃娃的目录
[root@hwf html]# mkdir tankedazhan //创建坦克大战的目录
[root@hwf html]# ls
tankedazhan zhuawawa
[root@hwf html]# cd zhuawawa
[root@hwf zhuawawa]# ls //将抓娃娃和坦克大战传到虚拟机来
zhuawawaji.zip 坦克.zip
[root@hwf zhuawawa]# mv 坦克.zip /var/www/html/tankedazhan/ //将坦克大战移动到坦克大战目录里去
[root@hwf zhuawawa]# ls
zhuawawaji.zip
[root@hwf zhuawawa]# dnf -y install zip* //安装zip解压工具
[root@hwf zhuawawa]# unzip zhuawawaji.zip //解压抓娃娃
[root@hwf zhuawawa]# rm -f zhuawawaji.zip //删除抓娃娃压缩包
[root@hwf zhuawawa]# ls
jQuery抓娃娃机游戏代码
[root@hwf zhuawawa]# mv 'jQuery抓娃娃机游戏代码'/* . //将文件里的程序移动到当前目录
[root@hwf zhuawawa]# ls
images img index.html jQuery抓娃娃机游戏代码 js
[root@hwf zhuawawa]# rm -rf jQuery抓娃娃机游戏代码/ //移出来后删除目录
[root@hwf zhuawawa]# ls
images img index.html js
[root@hwf html]# cd tankedazhan/
[root@hwf tankedazhan]# ls
坦克.zip
[root@hwf tankedazhan]# unzip 坦克.zip
[root@hwf tankedazhan]# ls
Battle_City 坦克.zip
[root@hwf tankedazhan]# rm -f 坦克.zip
[root@hwf tankedazhan]# ls
Battle_City
[root@hwf tankedazhan]# cd Battle_City/
[root@hwf Battle_City]# ls
audio css images index.html js
[root@hwf Battle_City]# cd ..
[root@hwf tankedazhan]# mv 'Battle_City'/* .
[root@hwf tankedazhan]# ls
audio Battle_City css images index.html js
[root@hwf html]# httpd -t //检查语法有没有错误
Syntax OK
[root@hwf html]# systemctl restart httpd //重启httpd服务
//测试访问
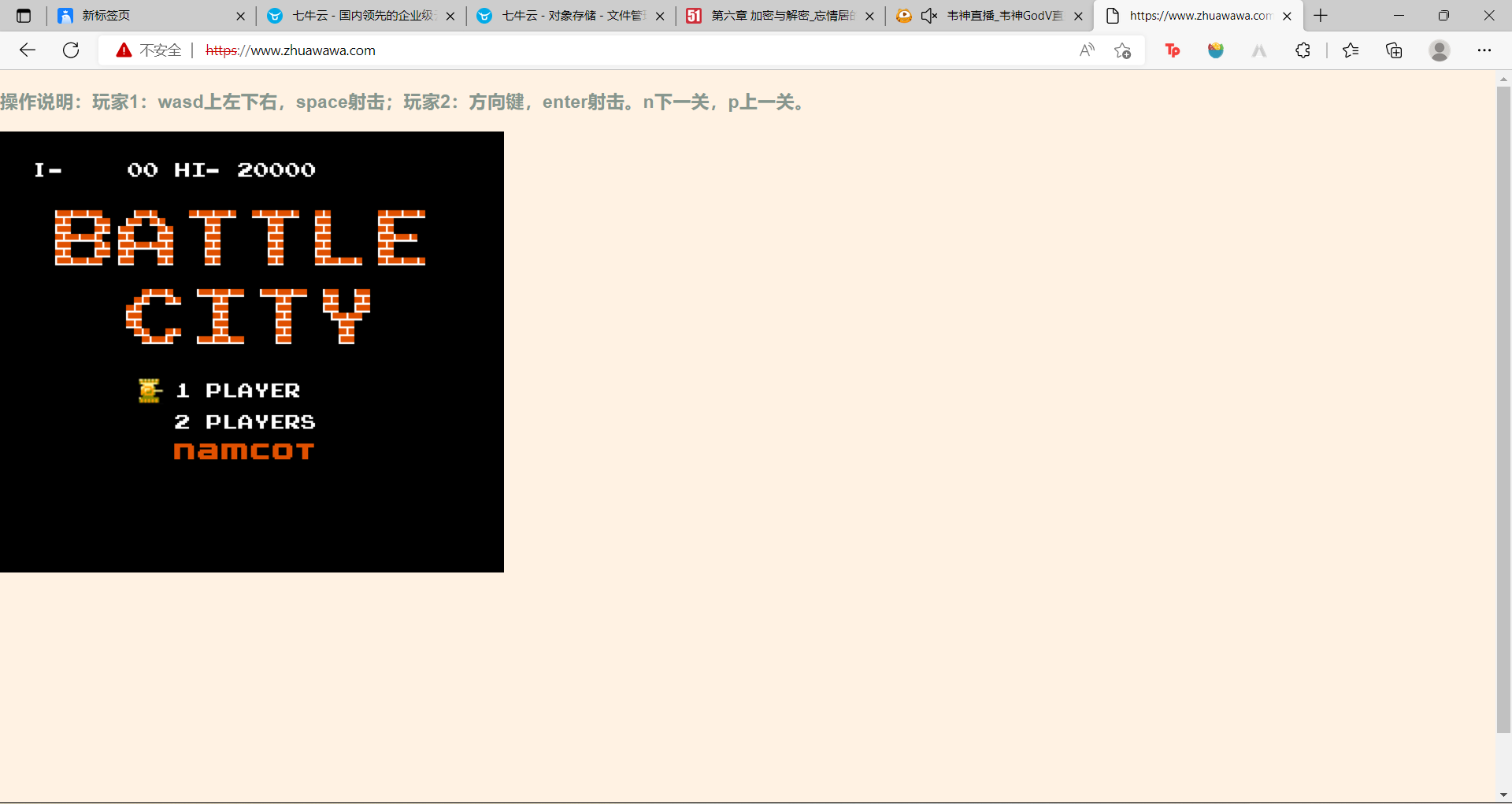
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-rhZPKjY2-1658494795527)(http://re6nm1tjj.bkt.clouddn.com/tankedazhan.png)]

1.2不同ip相同端口
[root@hwf html]# ip addr add 192.168.159.102/24 dev eth0
[root@hwf html]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:1e:f5:09 brd ff:ff:ff:ff:ff:ff
inet 192.168.159.100/24 brd 192.168.159.255 scope global noprefixroute eth0
valid_lft forever preferred_lft forever
inet 192.168.159.102/24 scope global secondary eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe1e:f509/64 scope link
valid_lft forever preferred_lft forever
[root@hwf html]# cat /etc/httpd/conf.d/httpd-vhosts.conf
<VirtualHost 192.168.159.100:80>
DocumentRoot "/var/www/html/zhuawawa"
ServerName www.zhuawawa.com
ErrorLog "/var/log/httpd/www.zhuawawa.com-error_log"
CustomLog "/var/log/httpd/dummy-host2.example.com-access_log" common
</VirtualHost>
<VirtualHost 192.168.159.102:80>
DocumentRoot "/var/www/html/tankedazhan"
ServerName www.tankedazhan.com
ErrorLog "/var/log/httpd/www.tankedazhan.com-error_log"
CustomLog "/var/log/httpd/www.tankedazhan.com-access_log" common
</VirtualHost>
[root@hwf html]# httpd -t
Syntax OK
[root@hwf html]# systemctl restart httpd
//测试访问


1.3相同ip相同端口不同域名
[root@hwf html]# vim /etc/httpd/conf.d/httpd-vhosts.conf
[root@hwf html]# cat /etc/httpd/conf.d/httpd-vhosts.conf
<VirtualHost 192.168.159.100:80>
DocumentRoot "/var/www/html/zhuawawa"
ServerName www.zhuawawa.com
ErrorLog "/var/log/httpd/www.zhuawawa.com-error_log"
CustomLog "/var/log/httpd/dummy-host2.example.com-access_log" common
</VirtualHost>
<VirtualHost 192.168.159.100:80>
DocumentRoot "/var/www/html/tankedazhan"
ServerName www.tankedazhan.com
ErrorLog "/var/log/httpd/www.tankedazhan.com-error_log"
CustomLog "/var/log/httpd/www.tankedazhan.com-access_log" common
</VirtualHost>
[root@hwf html]# httpd -t
Syntax OK
[root@hwf html]# systemctl restart httpd
//映射域名
去本地主机里找到对应的文件C盘/windows/system32/drivers/etc/hosts_lg_bak 文件做域名映射



1.4设置访问控制全都能访问
[root@hwf html]# vim /etc/httpd/conf.d/httpd-vhosts.conf
[root@hwf html]# cat /etc/httpd/conf.d/httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot "/var/www/html/zhuawawa"
ServerName www.zhuawawa.com
ErrorLog "/var/log/httpd/www.zhuawawa.com-error_log"
CustomLog "/var/log/httpd/dummy-host2.example.com-access_log" common
<Directory /var/www/html/zhuawawa>
<RequireAll>
Require all granted
</RequireAll>
</Directory>
</VirtualHost>
<VirtualHost *:80>
DocumentRoot "/var/www/html/tankedazhan"
ServerName www.tankedazhan.com
ErrorLog "/var/log/httpd/www.tankedazhan.com-error_log"
CustomLog "/var/log/httpd/www.tankedazhan.com-access_log" common
<Directory /var/www/html/tankedazhan>
<RequireAll>
Require all granted
</RequireAll>
</Directory>
</VirtualHost>
[root@hwf html]# httpd -t
Syntax OK
[root@hwf html]# systemctl restart httpd
1.5修改属主属组
//让apache用户也能有权限访问修改
[root@hwf html]# ls
tankedazhan zhuawawa
[root@hwf html]# ll
total 0
drwxr-xr-x 7 root root 91 Jul 22 17:53 tankedazhan
drwxr-xr-x 5 root root 59 Jul 22 17:51 zhuawawa
[root@hwf html]# chown -R apache.apache tankedazhan
[root@hwf html]# chown -R apache.apache zhuawawa
[root@hwf html]# ll
total 0
drwxr-xr-x 7 apache apache 91 Jul 22 17:53 tankedazhan
drwxr-xr-x 5 apache apache 59 Jul 22 17:51 zhuawawa
//也要给他们的日志文件的属主和属组修改为apache,让apache用户也能有读写权限
[root@hwf html]# cd /var/log/httpd/
[root@hwf httpd]# ll
total 28
-rw-r--r-- 1 root root 0 Jul 22 17:24 access_log
-rw-r--r-- 1 root root 3767 Jul 22 19:30 dummy-host2.example.com-access_log
-rw-r--r-- 1 root root 8319 Jul 22 19:28 error_log
-rw-r--r-- 1 root root 6959 Jul 22 19:02 www.tankedazhan.com-access_log
-rw-r--r-- 1 root root 0 Jul 22 18:02 www.tankedazhan.com-error_log
-rw-r--r-- 1 root root 187 Jul 22 19:25 www.zhuawawa.com-error_log
[root@hwf httpd]# cd
[root@hwf ~]# chown -R apache.apache /var/log/httpd/
[root@hwf ~]# ll /var/log/httpd/
total 28
-rw-r--r-- 1 apache apache 0 Jul 22 17:24 access_log
-rw-r--r-- 1 apache apache 3767 Jul 22 19:30 dummy-host2.example.com-access_log
-rw-r--r-- 1 apache apache 8319 Jul 22 19:28 error_log
-rw-r--r-- 1 apache apache 6959 Jul 22 19:02 www.tankedazhan.com-access_log
-rw-r--r-- 1 apache apache 0 Jul 22 18:02 www.tankedazhan.com-error_log
-rw-r--r-- 1 apache apache 187 Jul 22 19:25 www.zhuawawa.com-error_log
2.https配置
https(全称:Hyper Text Transfer Protocol over SecureSocket Layer),是以安全为目标的 http 通道,在 http 的基础上通过传输加密和身份认证保证了传输过程的安全性。
启用模块:编辑/etc/httpd/conf.modules.d/00-base.conf文件,添加下面这行,如果已经有了但是注释了,则取消注释即可
LoadModule ssl_module modules/mod_ssl.so
[root@hwf ~]# yum -y install mod_ssl //安装mod_ssl模块
[root@hwf ~]# httpd -t
Syntax OK
[root@hwf ~]# systemctl restart httpd
[root@hwf ~]# httpd -M |grep ssl
ssl_module (shared)
[root@hwf ~]# cd /etc/pki
[root@hwf pki]#
[root@hwf pki]# mkdir CA
[root@hwf pki]# cd CA/
[root@hwf CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) //生成一堆密钥在private目录下
Generating RSA private key, 2048 bit long modulus (2 primes)
.......................................................................................+++++
...........+++++
e is 65537 (0x010001)
[root@hwf CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365 //生成自签证书
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn //国家
State or Province Name (full name) []:hb //省份
Locality Name (eg, city) [Default City]:wh //城市
Organization Name (eg, company) [Default Company Ltd]:runtime //工作单位
Organizational Unit Name (eg, section) []:xuesheng //职位
Common Name (eg, your name or your server's hostname) []:www.zhuawawa.com //域名
Email Address []:1@3.com //邮箱
[root@hwf CA]# mkdir certs newcerts crl //创建目录
[root@hwf CA]# ls
cacert.pem certs crl newcerts private
[root@hwf CA]# touch index.txt && echo 01 > serial //创建文件往里面写入01
[root@hwf CA]# ls
cacert.pem certs crl index.txt newcerts private serial
[root@hwf CA]# cat serial
01
[root@hwf CA]# cd /etc/httpd && mkdir ssl && cd ssl
[root@hwf ssl]# (umask 077;openssl genrsa -out httpd.key 2048) //客户端生成密钥
Generating RSA private key, 2048 bit long modulus (2 primes)
.....................................................+++++
..........................................................................................................................+++++
e is 65537 (0x010001)
[root@hwf ssl]# openssl req -new -key httpd.key -days 365 -out httpd.csr //客户端生成证书签署请求
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:hb
Locality Name (eg, city) [Default City]:wh
Organization Name (eg, company) [Default Company Ltd]:runtime
Organizational Unit Name (eg, section) []:xuesheng
Common Name (eg, your name or your server's hostname) []:www.zhuawawa.com
Email Address []:1@3.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@hwf ssl]# openssl ca -in /etc/httpd/ssl/httpd.csr -out httpd.crt -days 365 //CA签署客户端提交上来的证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jul 22 12:36:08 2022 GMT
Not After : Jul 22 12:36:08 2023 GMT
Subject:
countryName = cn
stateOrProvinceName = hb
organizationName = runtime
organizationalUnitName = xuesheng
commonName = www.zhuawawa.com
emailAddress = 1@3.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
93:FA:F6:41:68:AD:5F:60:4B:73:EE:74:FF:70:0C:82:22:A6:50:B2
X509v3 Authority Key Identifier:
keyid:A1:C9:D3:7E:3D:D9:EB:48:FA:2C:79:08:37:C6:C9:DA:FC:39:FB:29
Certificate is to be certified until Jul 22 12:36:08 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@hwf conf.d]# vim ssl.conf //修改配置文件
<VirtualHost _default_:443>
DocumentRoot "/var/www/html/tankedazhan"
ServerName www.tankedazhan.com:443
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key

conf.d]# vim ssl.conf //修改配置文件
DocumentRoot “/var/www/html/tankedazhan”
ServerName www.tankedazhan.com:443
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
[外链图片转存中...(img-zha45HwT-1658494795535)]






















 1326
1326

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










