Kubernetes Dashboard 是基于 Kubernetes 集群的通用的、基于 Web 的 UI。它允许用户管理集群中运行的应用程序并对其进行故障排除,以及管理集群。
由于公司网络原因在rancher及KubeSphere的部署过程中都遇到了无法解决的问题,所以最终选择部署Kubernetes Dashboard来通过web页面管理集群。总的来说Kubernetes Dashboard的部署较为简单。
1、下载官网yaml文件
| Bash
wget https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml |
由于网络环境的原因,我这边也是无法成功下载的,大家可以通过手机或者其他外网机器直接访问网址,来复制出yaml文件中的信息,以下是我复制出来的yaml文件信息。我下载的是2.7.0,如果需要其他版本可以去官网查看,官网:https://github.com/kubernetes/dashboard
| Bash
# Copyright 2017 The Kubernetes Authors.
#
# Licensed under the Apache License, Version 2.0 (the "License");
# you may not use this file except in compliance with the License.
# You may obtain a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS,
# WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
# See the License for the specific language governing permissions and
# limitations under the License.
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.7.0
imagePullPolicy: IfNotPresent
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
spec:
securityContext:
seccompProfile:
type: RuntimeDefault
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.8
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {} |
2、修改recommended.yaml
在Kubernetes Dashboard中默认创建名为 "kubernetes-dashboard“ 的service 是ClusterIP 类型,而我们需要的是从外部网络进行访问,所以我们需要更改名为 "kubernetes-dashboard“ 的service为NodePort,在第40行的位置添加一行 type:
NodePort,上面的文件是我已经修改完成的,具体情况如下:
| Bash
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort #新增属性
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
--- |
3、使用k8s创建资源
| Bash
kubectl@ubuntu:/opt$ kubectl apply -f recommended.yaml
namespace/kubernetes-dashboard created
serviceaccount/kubernetes-dashboard created
service/kubernetes-dashboard created
secret/kubernetes-dashboard-certs created
secret/kubernetes-dashboard-csrf created
secret/kubernetes-dashboard-key-holder created
configmap/kubernetes-dashboard-settings created
role.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrole.rbac.authorization.k8s.io/kubernetes-dashboard created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
deployment.apps/kubernetes-dashboard created
service/dashboard-metrics-scraper created
deployment.apps/dashboard-metrics-scraper created
#到此需要的资源都已经创建完成。 |
4、查看资源是否已就绪
| Bash
kubectl@ubuntu:/opt$ kubectl get all -n kubernetes-dashboard -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
pod/dashboard-metrics-scraper-5657497c4c-n6gqj 1/1 Running 0 3h14m 10.42.0.12 ubuntu <none> <none>
pod/kubernetes-dashboard-5b749d9495-svr85 1/1 Running 0 145m 10.42.0.16 ubuntu <none> <none>
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE SELECTOR
service/kubernetes-dashboard NodePort 10.43.163.105 <none> 443:32237/TCP 3h14m k8s-app=kubernetes-dashboard
service/dashboard-metrics-scraper ClusterIP 10.43.19.61 <none> 8000/TCP 3h14m k8s-app=dashboard-metrics-scraper
NAME READY UP-TO-DATE AVAILABLE AGE CONTAINERS IMAGES SELECTOR
deployment.apps/dashboard-metrics-scraper 1/1 1 1 3h14m dashboard-metrics-scraper kubernetesui/metrics-scraper:v1.0.8 k8s-app=dashboard-metrics-scraper
deployment.apps/kubernetes-dashboard 1/1 1 1 3h14m kubernetes-dashboard kubernetesui/dashboard:v2.7.0 k8s-app=kubernetes-dashboard
NAME DESIRED CURRENT READY AGE CONTAINERS IMAGES SELECTOR
replicaset.apps/dashboard-metrics-scraper-5657497c4c 1 1 1 3h14m dashboard-metrics-scraper kubernetesui/metrics-scraper:v1.0.8 k8s-app=dashboard-metrics-scraper,pod-template-hash=5657497c4c
replicaset.apps/kubernetes-dashboard-5b749d9495 1 1 1 3h14m kubernetes-dashboard kubernetesui/dashboard:v2.7.0 k8s-app=kubernetes-dashboard,pod-template-hash=5b749d9495 |
注意查看pod及svc的状态,如果都已经是runing的状态,就证明已经起来了,因为我部署k8s的服务器属于离线环境,属于我将yaml文件中所用到的两个镜像都上传到镜像仓库中,并且在我的k8s指定了镜像仓库地址。
5、测试访问
查看service/kubernetes-dashboard 的端口号,因为yaml文件中说明了使用的是https协议,使用使用https://IP+端口进行访问。
访问到以下页面就代表参成功了。
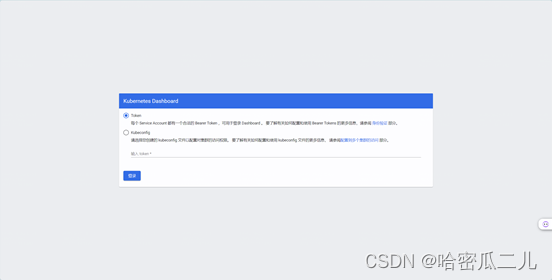
6、获取 ServiceAccount 的长期持有者令牌
以下是官方文档https://github.com/kubernetes/dashboard/blob/master/docs/user/access-control/creating-sample-user.md
手动为 ServiceAccount 创建 API 令牌
假设您有一个名为“build-robot”的现有服务帐户,如前所述。
您可以使用以下命令获取该 ServiceAccount 的限时 API 令牌:kubectl
| Bash
kubectl create token build-robot |
该命令的输出是一个令牌,可用于进行身份验证 ServiceAccount。您可以使用命令行参数请求特定的令牌持续时间,以(颁发的实际持续时间 令牌可能更短,甚至可能更长)。--durationkubectl create token
为 ServiceAccount 手动创建长期 API 令牌
如果要获取 ServiceAccount 的 API 令牌,请创建一个新的 Secret 带有特殊注释,.kubernetes.io/service-account.name
| Bash
kubectl apply -f - <<EOF
apiVersion: v1
kind: Secret
metadata:
name: build-robot-secret
annotations:
kubernetes.io/service-account.name: build-robot
type: kubernetes.io/service-account-token
EOF |
如果您使用以下命令查看密钥:
| Bash
kubectl get secret/build-robot-secret -o yaml |
您可以看到 Secret 现在包含“build-robot”ServiceAccount 的 API 令牌。
由于您设置了注释,控制平面会自动为其生成令牌 ServiceAccounts,并将它们存储到关联的 Secret 中。控制平面也会清理 已删除 ServiceAccounts 的令牌。
| Bash
kubectl describe secrets/build-robot-secret |
输出类似于以下内容:
| Bash
Name: build-robot-secret
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: build-robot
kubernetes.io/service-account.uid: da68f9c6-9d26-11e7-b84e-002dc52800da
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1338 bytes
namespace: 7 bytes
token: ... |
注意:
此处省略了 的内容。token
注意不要在旁观者可以看到您的终端/计算机屏幕的地方显示 Secret 的内容。kubernetes.io/service-account-token
删除具有关联 Secret 的 ServiceAccount 时,Kubernetes 控制平面会自动从该密钥中清除长期存在的令牌。
注意:
如果使用以下方法查看 ServiceAccount:
kubectl get serviceaccount build-robot -o yaml
在 ServiceAccount API 对象 .secrets 字段中看不到密钥 因为该字段仅填充了自动生成的密钥。build-robot-secret
实际操作
上面是官方文档中对这部分的说明,咱们一切从简,因为默认创建的serviceaccount/kubernetes-dashboard 不是所有权限,所以我们要创建一个所有权限的账号。
| Bash
#cat dashboard-admin.yaml
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: dashboard-admin
namespace: kubernetes-dashboard
annotations:
kubernetes.io/service-account.name: "dashboard-admin"
type: kubernetes.io/service-account-token
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: dashboard-admin-cluster-role
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kubernetes-dashboard |
然后查看一下secrets 类型的资源中是否存在名为kubernetes-dashboard的资源
| Bash
#kubectl get secrets --all-namespaces
NAMESPACE NAME TYPE DATA AGE
kube-system k3s-serving kubernetes.io/tls 2 4d2h
kube-system ubuntu.node-password.k3s Opaque 1 4d2h
kube-system chart-values-traefik Opaque 1 4d2h
kube-system chart-values-traefik-crd Opaque 0 4d2h
kube-system ubuntu2.node-password.k3s Opaque 1 4d2h
kube-system sh.helm.release.v1.traefik-crd.v1 helm.sh/release.v1 1 4d2h
kube-system sh.helm.release.v1.traefik.v1 helm.sh/release.v1 1 4d2h
kubernetes-dashboard kubernetes-dashboard-certs Opaque 0 3h32m
kubernetes-dashboard kubernetes-dashboard-csrf Opaque 1 3h32m
kubernetes-dashboard kubernetes-dashboard-key-holder Opaque 2 3h32m
kubernetes-dashboard dashboard-admin kubernetes.io/service-account-token 3 64s |
如果已经存在的话就用命名查看tekon
| Bash
kubectl describe secret/dashboard-admin -n kubernetes-dashboard
Name: dashboard-admin
Namespace: kubernetes-dashboard
Labels: k8s-app=kubernetes-dashboard
Annotations: kubernetes.io/service-account.name: dashboard-admin
kubernetes.io/service-account.uid: fcc80ca9-b820-4956-abc0-38245a56d645
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 570 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IkNpX1hBZVY2N3FqWWhWTnJYZUhvOTBXbzRkMG9TeWdQOWpWdVVVSkhRbTQifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdG9rZW4tbmJ2YzIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGFzaGJvYXJkLWFkbWluIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZXJ2aWNlLWFjY291bnQudWlkIjoiNzE2NmEyMTQtYTQ0Zi00MDlkLTk4ZjAtYWU3M2EwYTcyYmFjIiwic3ViIjoic3lzdGVtOnNlcnZpY2VhY2NvdW50Omt1YmVybmV0ZXMtZGFzaGJvYXJkOmRhc2hib2FyZC1hZG1pbiJ9.TPxLPW6en5Elq54viOIiabIsnQIWWqIIFDqGpzTruu3ULKsjvbkiQiuYEdL2_95lDPBb_JwLgGuFnE2Nk5_X00TGuBSRPU2cEj00_RLT-dyWlvW-kY-H0lNAlpzUnjn_j2pMSb7i_HgUDxWKQDz6zbXGT0c03nxGlI22HUx6jq_Yb05wYaudZlG-f14EFIm1iBZL85AMxx6uLSIpRNOXLDnX7rXAxUsep1k3HBO61-ST011URNPOHX83N2-PlfF8lb8dQaZl7tzY9i58Tq-Ux0ZwAvYJxdOBQQaSWQlSDmuteiRSIrbQoMqDfkcKw82DMXCyyF2wakf-ZgeOBrlCMw
root@ubuntu:/opt# mv dashboard-damin.yaml dashboard-admin.yaml
root@ubuntu:/opt# cat dashboard-admin.yaml
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: dashboard-admin
namespace: kubernetes-dashboard
annotations:
kubernetes.io/service-account.name: "dashboard-admin"
type: kubernetes.io/service-account-token
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: dashboard-admin-cluster-role
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: dashboard-admin
namespace: kubernetes-dashboard |
复制最后这一长串 token的值登录dashboard即可看到资源情况。成功访问如下图:
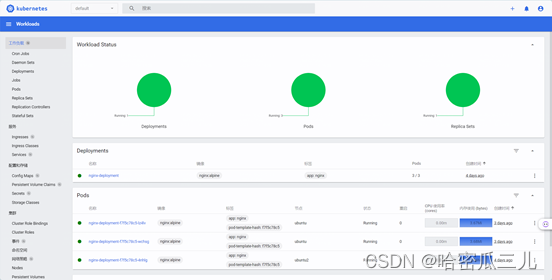























 765
765











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








