SECTION I.
Introduction
In recent decades, the smart city technologies [1], [2] has received significant attention due to its competence in improving the quality of life expectancy and safety of urban citizens. In smart city systems, different communication technologies are used to manage both the network and data, including big data, cloud computing, and networking systems [3], [4], [5], [6]. The general smart city applications are depicted in Fig 1, which comprises smart street lighting, smart grid, traffic management, and health systems. Here, the criticality level of each system is assessed based on its working operations and functionalities. Nevertheless, the most challenging issues in the smart city systems [7], [8], [9] are data transmission/delivery to many sensors and actuators deployed in the network, such as vehicles, infrastructures, and buildings. To solve this problem, the Internet of Vehicles (IoV) [10], [11] is integrated with an Internet of Things (IoT) [12] to improve the communication strategies in smart city networks. Because it provides the most suitable features [13], [14] of reduced cost consumption, congestion elimination, and safety assurance. The IoV is a communication model that establishes reliable and safe communication between vehicles and infrastructures.
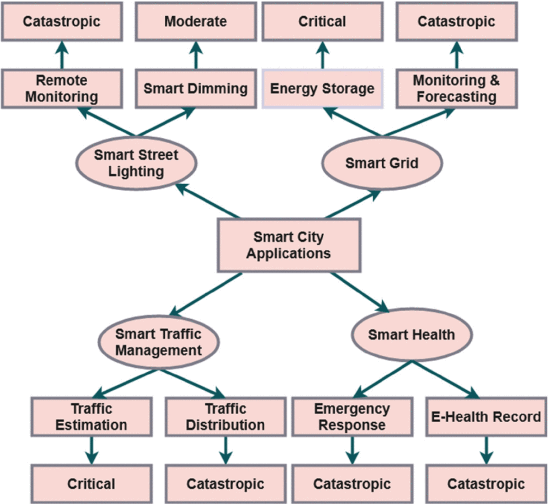
FIGURE 1.
Illustration of smart city applications.
Moreover, the different types of security requirements [15], [16], [17], [18] must be satisfied to ensure the secured communication in smart city architecture, which includes the followings:
-
Integrity – This property can be satisfied by detecting the manipulations done on the message.
-
Confidentiality – Data confidentiality can be guaranteed only if the authorised vehicles receive the message.
-
Mutual Authentication – The receiver vehicle should be definite that the message is transferred only by the authorized source.
-
Secrecy – The forward secrecy can be maintained based on the key exchange between the sender and receiver sides with a specific time limit.
A. Contributions
The significant contributions behind this work are as follows:
-
Mutual authentication and critical agreement processes ensure increased security and privacy of an open network.
-
Data transmission confidentiality and integrity are guaranteed using the session key generation and agreement controlling policies.
-
A meta-heuristic-based machine learning classifier is utilized to spot the other attacking users in the network.
-
Reliable and secured data communication is established between the V2V and V2I entities with proper registration, authentication, and key agreement phases.
B. Objectives
An intelligent security framework establishes reliable and secured communications between the vehicle to vehicle (V2V) and vehicle to infrastructure (V2I) entities in smart city networks. Also, a Collaborative Mutual Authentication (CMA) model is deployed for properly authenticating the login requested vehicle users or infrastructure entities. In addition, the smart city network is protected against outside attackers by using the hybrid Meta-heuristic Genetic Algorithm – Random Forest (MGA-RF) based machine learning classification algorithm. The MGA optimization technique selects the optimal features based on the best solution. Then, the RF classifier predicts the attack in the network by using the selected features. Here, an integrated CMA-MGA-RF mechanism is deployed to ensure security and reliable data transmission between the entities of smart city systems. Moreover, the proposed security framework’s performance and effectiveness are validated and compared using various evaluation measures.
C. Organisation
The remaining portions of this paper are structuralised as follows: Section II reviews some of the existing security architectures used in smart city applications with their advantages and disadvantages. Then, Section III presents a clear description of the proposed security framework for smart city development with its algorithmic steps and flow illustration. Section IV has validated the experimental and comparative analysis of existing and proposed security architectures. Finally, the overall paper is summarized with its obtainments and future scope in Section V.
SECTION II.
Related Works
This Section investigates the working modules and functionalities of different approaches to improve smart city systems’ security. Also, it discusses the advantages and disadvantages of each technique based on its functionalities and performance outcomes.
[19] designed a deep learning model-based IoT framework for increasing the security of smart cities with increased scalability, reduced latency and cost consumption. The main intention of this work was to establish a secured communication infrastructure in smart cities based on the factors of anonymity, privacy, confidentiality, authentication, repudiation and sensitivity. Also, this architecture comprises three different layers connection, conversion and application, where the blockchain was utilized to ensure security and privacy. The key benefits of this work were reduced storage problems, computational cost, and high quality of service. Still, it lacks the issues of high design complexity and reduced performance efficiency. However, it has the significant limitations of reduced trustworthiness and lack of social control. Reference [20] developed a hybridized network architecture to ensure both the privacy and security of the smart city environment. Here, the emerging Software Defined Networking (SDN) architecture was integrated with the blockchain technologies to obtain the benefits of both distributed and centralised systems. Moreover, this work investigates the major challenging tasks in the smart city systems, which include the followings:
-
Reduced latency
-
High mobility
-
Bandwidth limitations
-
Fault tolerance
-
Stability maintenance
Also, the Proof of Work (PoW) scheme was deployed, enhancing the security of distributed smart city network architecture. One of the blockchain methodologies helps find the most suitable solution based on the hash function. Still, this work is limited by central issues of high complexity in architecture designing and reduced performance efficiency. Reference [21] investigated the problems such as increased network latency, traffic, and sand security breaches related to the smart city application systems. Also, some of the essential requirements used for improving the architecture of the smart city systems [22] have been discussed in this work, which was network route updation, communication delay, fast data processing, security against attacks, ensuring both user and data privacy requirements, and time-sensitive applications. Reference [23] conducted a detailed review of the recent technologies to design an efficient smart city architecture with security enhancement and crime reduction factors. This work studied the key elements used for improving the communication capability and security of smart city networking architecture.
Reference [24] intended to ensure the trustworthiness of the smart city networking architecture by analyzing the impacts of malicious users and anchors in a crowdsensing system. The main intention of this work was to develop a vote-based crowdsensing system for improving the framework of smart city applications with the help of public sensor data, vote required for communication establishment, built-in sensors and readings. Reference [25] conducted a comprehensive review of the functionalities of SDN for establishing secure data communication at varying scales. The different types of smart city energy, health, and transportation applications have been categorized here. In addition, the critical components of smart city systems were explored in this paper, including smart education, the Internet of Things (IoT), agriculture, mobility, health, etc. Reference [26] developed a new traffic classification model based on an IoT architecture to improve smart city application QoS. The main intention of this work was to incorporate the functionalities of feature extraction, optimization, and classification models for traffic analysis in smart cities. The major stages involved in this network design were capsule network formation with a dynamic routing mechanism and traffic classification based on Convolutional Neural Network (CNN) model. Here, the dynamic routing algorithm was deployed to establish the data transformation in the capsule network by estimating the coupling coefficients and weight matrix. Then, the CNN model was utilized to categorize the traffic as benign or malware. The significant advantages of this work were high classification accuracy and better performance outcomes. However, it has the limitations of reduced security and privacy measures, which degrades the effectiveness of the overall network communication system.
Reference [6] intended to increase the security of smart city networks using the Multi-Access Mobile Edge Computing (MA-MEC) model. This paper aimed to incorporate the functionalities of a heterogeneous IoT framework for constructing a smart city. The types of attacks concentrated in this work were replay attacks, spoofing attacks, eavesdropping, node capturing, and side-channel attacks. This work has performed wiretap coding, resource allocation, key generation, and authentication to detect these attacks. The key benefits of this paper were reduced complexity, minimized resource consumption, ensured secrecy, and improved adaptation capability. Yet, it has the significant drawbacks of key generation overhead, high redundancy and network overhead. Reference [5] deployed a Reconfigurable Intelligent Surfaces (RIS) assisted networking architecture in increasing intelligent city communications’ flexibility. The symbiotic relationship was estimated between the communication architecture and smart cities to establish RIS-supported communication. Also, it intended to obtain the parameters of improved QoS, security, and resource exploitation in the smart city network. The disadvantages behind this system were high sensitivity, more energy consumption, and reduced performance outcomes.
Reference [27] implemented an enhanced traffic classification model for identifying the DDoS attacks in the SDN-enabled smart city network. Also, it intends to minimize the load and increase the flexibility of SDN architecture against harmful DDoS attacks. For this purpose, a Random Forest (RF) classification model was incorporated with the backtracking methodology for accurately identifying the attacks by computing the conditional entropy. Reference [28] employed an Elliptic Curve Cryptography (ECC) technique to increase smart city networks’ security by ensuring secure message communication. Here, an Automated Validation of Internet Security Protocols and Applications (AVISPA) tool was utilized to perform an authentication-based security verification against attacks like replay, man-in-middle, and brute force [29].
Moreover, the session key generation and validation were performed to maintain the message secrecy. However, the critical limitations behind this paper were increased computational complexity, cost and time consumption measures. Reference [30] investigated various issues and challenges related to deploying security in smart city architecture. Here, the importance of using blockchain methodology was discussed to guarantee the properties of transparency, democracy, security, automation, and trust in smart city networks. Based on this scrutiny, it was studied that the blockchain methodology could be more helpful in improving smart city applications due to its significant properties of energy efficiency, cost-effectiveness, security, data storage and regulation.
Reference [31] developed a policy-based security mechanism to detect the malicious and untrustworthy nodes in the smart city networking architecture. To improve the security of the smart system, the IoT framework was incorporated into this design, which helps to perform policy management based on contextual information. The major stages involved in this structure were data collection, policy management, malicious identification, data fusion, and trust management. The main advantage of this work was increased attack detection rate, reduced false positives, and time consumption. Yet, the effectiveness of this security architecture needs to be improved by analyzing the attacking patterns accurately. Reference [32] recommended a deep learning model for increasing the security of smart city networking systems. The main intention of this paper was to detect replay attacks with improved accuracy using the deep convolution neural network model. For this purpose, this work utilised a real-time benchmark smart city dataset, which helps evaluate the suggested model’s performance.
This review studies ensuring privacy and security measures in innovative city applications. Also, the different types of architectures deployed in the conventional works to enhance the effectiveness of smart city systems are analyzed, which can be more helpful for designing the proposed system architecture. Though the significant drawbacks that exist in the existing methodologies are as follows:
-
Minimized fault tolerance capability
-
Inefficient network controlling and management
-
High-cost consumption for maintenance
-
Reduced scalability and vulnerability
-
Incompetent security on user data access control
The proposed work aims to develop an intelligent security framework for smart city networks to solve these problems.
Blockchain model is used to efficiently manage and understand the network by resolving the security risks. The purpose of the proposed work is to develop a lightweight distributed ledger blockchain based machine learning protocol for strengthening the security of smart city networks. The algorithms used in this framework are Collaborative Mutual Authentication (CMA) based blockchain model, and Meta-Heuristic Genetic Algorithm (MGA) – Random Forest (RF) machine learning approach, which are implemented by using the Network Simulator tool. In this framework, the smart city network is constructed with the set of wireless nodes, where the nodes are treated as the vehicles. Once the network is created, each and every node participated in this architecture are need to be properly registered and authenticated for enabling the data communication or transmission, which is performed with the help of blockchain methodology. Also, the malicious/attacking vehicle nodes are identified and detected from the network by using the MGA-RF machine learning model. This framework is highly secured with the modules of network initialization, registration, login, mutual authentication, topology management, and attack analysis
SECTION III.
Research Methodology
This Section presents a detailed description of the proposed Collaborative Mutual Authentication (CMA) with Meta-Heuristic Genetic Algorithm – Random Forest (MGA-RF) based security framework for smart city networks. This work’s main intention is to ensure the privacy and security measures of smart city systems by establishing a secured communication between vehicle to vehicle (V2V) and vehicle to infrastructure (V2I). The overall architecture of the proposed smart city environment model is depicted in Fig 3 (a), and its corresponding working flow representation is illustrated in Fig 2. In this framework, the Internet of Vehicles (IoV) model is utilized to establish the communication between V2V and V2I. Implementing an IoV architecture model benefits secured data sharing, control, interaction, and maintenance in a smart city environment. Here, the vehicles can gather the traffic information related to the location and speed and transmits those data to other vehicles or infrastructures.
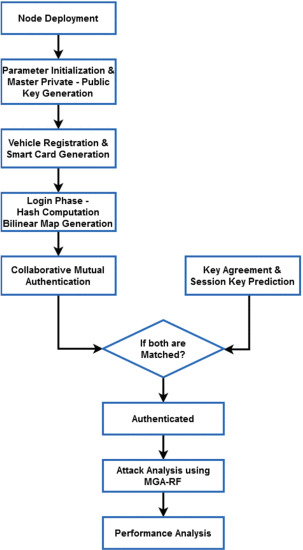
FIGURE 2.
The flow of the proposed system.

FIGURE 3.
Model and layered architecture of smart city environment.
Similarly, the infrastructure can provide vehicle drivers and travellers with beneficial services and traffic information. The layered architecture model of the proposed smart city networks is shown in Fig 3 (b). The major stages involved in this design are as follows:
-
Initialization phase
-
Registration phase
-
Login phase
-
Authentication and critical agreement phase
-
Attack analysis
As shown in Fig 3 (b), the proposed architecture comprises the layers of application, transport, network and perception. The machine learning-based attack detection is performed in the application layer. Then, the vehicle node registration, login, authentication, and key agreement processes are performed in the transport layer. The topology management and sensor data transmission are performed in network and perception layers. The main contribution of this work is to ensure the security of smart city by implementing a collaborative authentication-based machine learning methodology. During authentication, each vehicle entered in the smart city should register with a centralized server for participating in the transportation. In this work, the general data protection laws based on the Information Technology Act (IT Act) 2000 [33] are referred for constructing the smart city environment. In the future, this environment can be implemented in real-time to ensure smart city security.
A. Overall Working Methodology
The significant problems of the smart city framework are collecting and transmitting the information to the different actuators and sensors integrated with smart objects like vehicles, infrastructure, buildings, etc. To solve this problem, the Internet of Vehicle (IoV) incorporated with VANET and IoT systems is utilised in this work, which helps avoid congestion operating costs and ensures safety measures. In an IoV environment, the vehicle and other entities’ communication is established using a vehicle to Vehicle (V2V) and Vehicle to Infrastructure (V2I) communications. Here, the vehicles can collect traffic information like speed and location and transmit it to the other vehicles or infrastructure units. The infrastructure provides the required services and traffic information to the drivers or passengers of the vehicles. Despite the advantages, the IoV has some serious issues due to the insecure data transmission between the entities. Because the malicious users intend to access the authenticated users’ private information, which leads to vehicular accidents due to the wrong traffic status updation, it is essential to develop an intelligent and advanced security model to ensure smart city networks’ security.
Thus, the proposed work proposes implementing a novel Collaborative Mutual Authentication (CMA) scheme incorporated with the Meta-heuristic Genetic Algorithm – Random Forest (MGA-RF) technique to ensure security and reliable data transmission between the entities of smart city systems. Data communication and transmission are established between the V2V and V2I components in the proposed framework, where the vehicles are considered vehicle users. During the initialization setup, the cyclic additive group-based bilinear mapping is performed for generating the master private and public key pair.
Here, the Smart city Vehicle Information System (SVIS) server selects the parameters for generating the keys, including the chosen randomly sizeable prime number, cyclic additive group member functions, bilinear mapping function, generator of cyclic group, and hash function. Based on these, the keys are generated, and the set of values is considered the system parameters, which can be used for further communications. After setting the network topology, all users and infrastructures must register with the Road Side Unit (RSU) server, and only the authenticated vehicle users and infrastructures are allowed for communication. In the registration phase, the remote user, user identity, unique password, and user biometric information are considered for registering vehicle users and infrastructure entities. In this environment, fingerprint-based biometric information is gathered from the vehicle users for registration. Then, the collected information is stored in the cloud system, and the centralized server provides access to the data. Here, the blockchain security model is used to secure the private credentials of the users. The constant values are generated according to the specifications of requested vehicle users or infrastructure entities. The corresponding user shares their generated information with the SVIS server unit.
Consequently, the server checks the identity of the requested user by matching it with the database system; if it is a new user, the server device can store the new user’s information in the 0th array; otherwise, it can append the information in the existing collection. After this process, the server can generate the corresponding user’s verification ID and weight value using the hash function set, user identity, master public key, and constant value. Based on these values, the smart card can be generated for the registration requested user, and consequently, other entities are registered with the server unit. The smart card is a kind of electronic authorization card used to check the validity and authenticity of the vehicle users. So, all vehicles participating in the smart city environment should register with the centralized server to obtain the smart card. Also, the vehicle user or infrastructure with this smart card is considered the authenticated participants, and the registered participants are allowed further data transmission and communications. Here, the blockchain data storage system is used to securely store the information of vehicle users. Typically, the blockchain is defined as a kind of digital ledger technology used primarily to store transactional information. The data are stored as signed blocks linked with each other. For instance, the sample blocks of information are shown below:
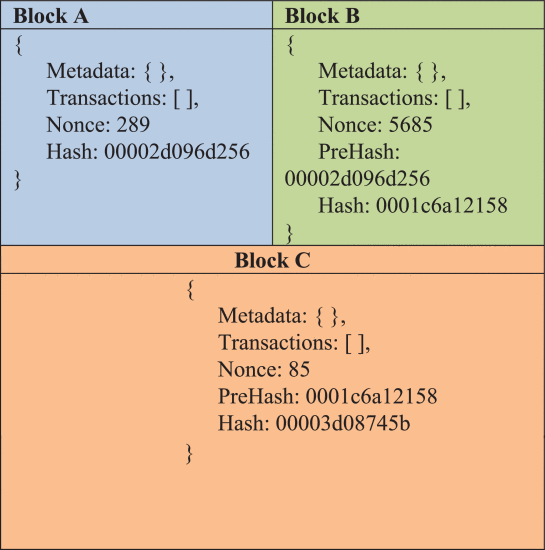
Moreover, the blockchain is immutable, so there is no possibility of changing the information in the data blocks. The primary advantage of using blockchain databases is that they provide an efficient way to store the data securely. After successful registration, the vehicle users or infrastructure must log in to participate in the communication. The authenticated entities needed to provide their smart card, unique identity, password, and biometric information during this process. After that, these parameters were validated based on the hash value. If the generated hash value of the smart card is invalid, the session can be automatically aborted; otherwise, the pseudo-random number and timestamp values are generated for the requested smart card vehicle user/infrastructure entity. Then, the login parameters are transmitted to the server unit for proper authentication and validation. Here, the Collaborative Mutual Authentication (CMA) mechanism is implemented for validating the authenticity of the login requested vehicle user/infrastructure. During this process, the server validates the session of the login requested entity; if the condition is valid, the blockchain integrated bilinear mapping model generates the session key based on the public key’s parameters, identity, password, and biometric information.
Finally, the server can transmit the authenticated message to the requested user/infrastructure entity. The key agreement policy has been utilized to verify the time stamp validity on the user side. The authenticated users can only extract the session key for further data transmission with other entities. In addition, the security analysis is performed to detect other attacking activities in the smart city networks, which is accomplished by using the hybrid Meta-heuristic Genetic Algorithm integrated with Random Forest (MGA-RF) technique. This framework’s novel contribution ensures the security of data transmission and communication between the entities at each system module like registration, login, proper authentication, session key generation, and key agreement controlling policy validation.
Moreover, other attacking activities are also detected and classified using the optimization-based machine learning classification mechanism. Hence, this framework guarantees reliable and secured communication between the V2V and V2I entities in the smart city networks. It filters the malicious users and outside attackers based on proper authentication and key agreement functions. The key advantages of this work are high security, robustness, reliability, reduced cost consumption, minimized time consumption, and increased efficiency. Table 1 shows the list of symbols used in the proposed methodology with its descriptions.
TABLE 1 Symbols and Descriptions
B. Initialization
In this phase, the Smart city Vehicle Information System (SVIS) server defines the set of parameters at first, which includes the large prime number qp , cyclic additive group M1&M2 , bilinear map bm , hash function hashfun , and updated hash function Hfun . Then, the master private MasterPK and public keys MasterBK are generated and integrated with the predefined parameters, which helps to secure the server database. The algorithmic steps involved in the initialization process are illustrated Algorithm 1.
Algorithm 1 Initialization
Step 1:
Smart city Vehicle Information System (SVIS) server HS sets up its parameters.
Step 2:
HS selects the public parameters {qp , M1 , M2 , bm , P, hashfun , Hfun } qp – large prime number, M1&M2 are the cyclic additive group which is generated by P , and bm is the bilinear map, P is the generator of M1&M2 , hashfun - hash function which is computed from Zq , and Hfun – computed hash function.
Step 3:
Generate the master private key as follows, MasterPK=sm∈Zq where, sm indicates the master private key.
Step 4:
Generate the master public key as follows, MasterBK=smP
Step 5:
Announces their generated information as system parameters, param={qp,M1,M2,bm,P,hashfun,Hfun,MasterBK}
C. Registration
After initialization, the registration process can be mainly performed to allow the vehicles for accessing and exchanging traffic information from/to the other objects in an IoV architecture. During this process, the remote user RU , user identity, password, and biometric information BMU are taken as the inputs for registration. Then, the constant value CU is generated for both infrastructure and vehicle with the password parameters and hash function Hfun of biometric information. Consequently, the user can transmit generated message to the server, which validates the identity of the infrastructure/vehicle based on the database entries. If the entry is new to the server HS , it can automatically store the record at the initial array; otherwise, it adds the record in the existing array. After this process, the server can estimate the verification ID VU and weight factor WtU of the user concerning the generated hash function, user identity, master key MasterBK and the computed constant value. At last, it forms the smart card sm with this information and forwards it to the desired remote user of the network.
D. Login Phase
After registration, the user can enter their details to log in into the system with the smart card information SCU , password PWU and biometric information BMU . Then, the defined parameters have been validated with the stored record VU based on the hash function hashfun . If the generated hash value for the given information of IDU,PWUandBMU are not valid, the session gets automatically terminated. Otherwise, the pseudo-random number has been generated for SCU with the initialization of time stamp of TU . Consequently, the log in parameters like NU , Nsm , KU , and AuthU are estimated based on the generated hash function, pseudo random number, master public key, time stamp and an encrypted symmetric key. The login request can be formed and transferred to the remote server based on this information.
E. Collaborative Mutual Authentication
Here, the collaborative mutual authentication mechanism is implemented in this system to validate the users’ identity to ensure security. After getting the login request, the RSU server HS can validate the session time for the request received from the user. If the condition is satisfied, the blockchain-based bilinear mapping model is utilized for computing the parameters of sm and RUP . Consequently, the AuthU is decrypted for getting the encrypted information of IDU , TU , and rpU . Then, the hash function is computed for IDU that helps to validate the remote vehicle user as whether authorized or unauthorised. If the session time mismatches for the requested user, the RSU server HS can generate the random number for the particular request. At that time, it computes the login parameters of the user for obtaining the authenticated smart card Authsm . Based on the parameters of TU,RU , Rsm , Tsm and loginsm , the session key is generated by computing the hash function of these measures. Finally, the authenticated message is transferred to the remote vehicle user with Rsm,Tsm , and Authsm .
Algorithm 2 Registration Phase
Input: Remote User RU , User Identity IDU , password PWU , User Biometric information BMU ;
Step 1:
Generate constant value for the user (i.e. vehicle/infrastructure), CU=PWU⊕Hfun(BMU)
Step 2:
User sends this generated message to RSU server HS .
Step 3:
Server HS checks the identity IDU in its database.
Step 4:
If (the identity is new)
The server can store the record at 0th array;
Step 5:
Else
The record can be appended in the existing array;
Step 6:
Then, the server HS computes and stores the verification ID VU and weight for the user WtU as shown in below, VU=hashfun(IDU||CU)WtU=CU⊕hashfun(IDU||sm)
Step 7:
Finally, the server HS adapts smart card and forwards to the remote user.
SCU={VU,WtU,MasterBK,hashfun,Hfun
View Source
Registration
Remote User RU SVIS RSU server HS
Compute CU=PWU⊕Hfun(BMU) Sends 〈CU,IDU〉 to RSU server HS
RSU Server HS checks its identity IDU in its database.
If it is new, store the records at 0th array; Otherwise, append the records into existing array.
Then, HS adapts smart card SCU={VU,WtU , MasterBK,hashfun,Hfun Send smart card to RU securely.
Once the authentication is accomplished at the server side, the key agreement process can be performed at the remote vehicle user side. During this phase, the user can validate the time stamp value, if it is match with the login parameters, the authenticated message is verified based on the hash value of TU , RU , Tsm , Rsm , loginsm , and KU . Consequently, the session key verification is also performed at the user side by the updated hash value.
Algorithm 3 Login Phase
Step 1:
User can use their smart card SCU with card reader for inserting their Identity IDU , password PWU , Biometric information BMU
Step 2:
Then, the following parameters have been validated for SCU as shown in below:
hashfun(IDU||PWU⊕Hfun(BMU))
View Source
Check its value with the stored VU .
Step 3:
If the computed hash value of SCU is invalid, Session got aborted;
Step 4:
Then, the pseudo random number rpU∈Zq is generated for SCU and time stamp TU is initiated.
Step 5:
After that, the following log in parameters are computed,
NU=Hfun(IDU)
Nsm=Hfun(IDS)
RU=rpUNUKU=bm(MasterBK,rpUNHS)
AuthU=Eski(IDU||TU||rpU)//Eski encrypted symmetric key
Step 6:
Finally, the generated information is organized as follows:
loginReqU=RU,TU,AuthU to server HS
This login request can be transmitted to the server.
Login
Remote Vehicle User RU SVIS RSU server HS
User inserts SCU into card reader with IDU , PWU , and BMU . Then, SCU estimates hashfun(IDU||PWU⊕Hfun(BMU)) .
If hash(SCU ) is invalid, Session aborted; Otherwise, SCU generates the number rpU∈Zq and initiates the time stamp TU .
Compute the values of NU , Nsm , RU , KU and AuthU . Then, the transfer the login request loginReqU .
Based on the receiving loginReqU from remote vehicle user RU , the authentication can be performed.
Algorithm 4 Collaborative Mutual Authentication
Step 1:
RSU server HS verifies the session time validity once it received the login request for requested user.
ΔT≤Tsm−TU
View Source
Step 2:
If the above the condition is valid,
- Then, the following parameters are estimated by using the block chain based bilinear map model;
Ksm=bm(sm,RUP)
View Source -
Decrypt AuthU and obtain the encrypted information IDU||TU||rpU ;
-
Compute NU=Hfun(IDU) and Verify RU=rpUNU
Step 3:
Else
The RSU server HS generates a random number rpsm∈Zq ;
Step 4:
Compute the following parameters:
Nsm=Hfun(IDS) ,
Rsm=rpsmNsm ,
loginsm=rpsmRU ,
Authsm=hashfun(TU||RU||Tsm||Rsm||loginsm||Ksm)
Step 5:
Then, the session key is generated as follows;
sesssmKey=hashfun(TU||RU||Tsm||Rsm||loginsm)
View Source
Step 6:
At last, transfer the authentication message to user RUMA=(Rsm,Tsm,Authsm)
F. Topology Management
As mentioned in the layered architecture Fig 3 (b), the topology management is performed in this environment to maintain the network connectivity. Also, it helps to reduce the network overhead with increased operating efficiency. Here, the cluster optimization problem is considered as the Governing Set (GS), which comprises the subset of nodes. The processes involved in the network topology management process is illustrated as follows, and its variable descriptions are listed in Table 1.
Input: Neighbor information of node D
InitCHset=NCHAd
Gd=(Vd,Ed)
//Where,
Vd=UCHj∈NCH(h)dψCHjUD
{Ud,Vd∈EdifUd∈Ndv
[CHset,ClMemSet]
=FormationClusterGS(Gd,D,|InitCHset|)
if |CHset|<|InitCHset| then
reconClusters(ClMemSet)
end
function [CHset,ClMemSet]
=FormationClusterGS(Gd,D|InitCHset|)
t′=argmaxt∈(ID)(|NdID(t)∩Vd∩ID|)
S=Vd/NdID(t′)∩ID
while S≠0 and |CHset|≤CHno do
foreach nj∈S do
Nighj=maxt∈(ID)(|Ndnj(t)∩S|)
tj=argmaxt∈(ID)(|Ndnj(t)∩S|)
end for
j=argmaxj|nj∈SNighj
CHset←nj
ClMemSet←{CH:nj ,
Primary Channel tj , Members: Ndnj(tj)∩S∪nj}
S=SNdnj(tj)∩S∪nj
end while
return
Algorithm 5 Key Agreement
Step 1:
User RU verifies its time stamp validity, ΔT≤Tsm−TU
Step 2:
If valid user estimates, loginU=rpURsm
Step 3:
Verifies the following equation, Authsm=hashfun(TU||RU||Tsm||Rsm||loginsm||KU)
Step 4:
If equation holds computes the common session key as, sessUKey=hashfun(TU||RU||Tsm||Rsm||loginsm)
Authentication & Key Agreement
Remote Vehicle User RU SVIS RSU server HS
Verifies the session time validity ΔT≤Tsm−TU ;
If (Valid)
Ksm=bm(sm,RUP)
IDU||TU||rpU
NU=Hfun(IDU)
RU=rpUNU
Else
RU=rpUNU
Compute Nsm , Rsm , loginsm , and Authsm ;
Generate sesssmKey and send message to RU .
User RU verifies the time stamp validity, ΔT≤Tsm−TU
If (the user is valid)
loginU=rpURsm ;
Authsm=hashfun
(TU||RU||Tsm||Rsm||loginsm||KU)
Estimate the common session key sessUKey=hashfun
(TU||RU||Tsm||Rsm||loginsm)
G. Attack Analysis
In addition, the proposed work implements the machine learning classification model for identifying the attacks in the smart city systems, which is considered a supplementary security module used for guaranteeing reliable network communication. In this work, a separate database has been maintained for storing the previous history of data communications, which comprises the information related to the vehicles and infrastructures that participated in the touch. Then, the characteristics of those entities are stored in the form of features to avoid malicious attacks in future data communications. Based on the learning of these features, the attacks are identified and classified using the Meta-Heuristic Genetic Algorithm – Random Forest (MGA-RF) technique is implemented in this phase, which is used to increase the overall security of networking systems. The main intention of using this approach is to minimize the complexity of the training model with improved attack detection accuracy. In this mechanism, the MGA is utilized to select the best optimal solution for improving the recognition accuracy of the attack detection system. For this purpose, the crossover, mutation and selection functions are computed, which are used to construct the classification model. The RF is a bootstrap resampling model mainly used to extract more samples from the given dataset. The technique’s significant benefits are increased computational efficiency, reduced designing complexity, improved accuracy, and a high recognition rate. The number of classes cap U sub cap C in the labelled data is computed in this method. Based on this, the tree is constructed with the root node Nrt and training data Dtr , the training data is considered the chromosomes.
Consequently, the chromosome selection is performed based on the root node, and the objective function is estimated for constructing the tree with the root node. Then, the possible splitting features are randomly selected concerning the fitness values of chromosomes. After that, the crossover and mutation functions are estimated and based on this value, the child node is created with the highest possible gain value. Finally, all instances are matched with the test data to accurately predict the corresponding label class. The algorithmic steps involved in this technique are illustrated in Algorithm 6.
Algorithm 6 Meta-Heuristic Genetic Algorithm – Random Forest (MGA-RF)
Step 1:
To compute the number of classes in the labelled data
UC=unique(LN)
// UC – number of classes in labeled data
LN− Number of labels
Step 2:
Create root node Nrt containing training data Dtr about the presented users.
Step 3:
Consider the training data Dtr as chromosomes.
Step 4:
Perform a selection of chromosomes based on the root node Nrt
Step 5:
Compute objective function to construct a tree with respect to Nrt
Step 6:
Randomly select y% of possible splitting features in NL by
NL is the number of samples presented in each class.
if Fitchr<Fitprechrsplitprob=NL(UC)∗y%end if
//Where, Fitchr – fitness value for chromosome and Fitprechr - fitness value for previous chromosome.
Step 7:
The crossover and mutation probability is computed with respect to crossover rate and mutation rate.
Step 8:
Create child node Nch with highest information gain to split on possible values.
Step 9:
Predict corresponding class for test data Dte by matching all instances. predcls=NL(Nch)
Fig 4 (a) shows the network deployment framework, where the set of nodes are positioned in different locations with the RSU, and Fig 4 (b) depicts the detection of malicious users on the network region. Consequently, Fig 4(c) shows the number of requested users in the network, and the overall requested, authenticated, and malicious users are depicted in Fig 4(d). As shown in Fig 4 (a), the smart city network is constructed by using the simulation, and the network comprises the group of vehicle nodes and RSUs. When the vehicle crosses the RSU, it can update the details to RSU. In the deployed network, there may be a possibility for the malicious users highlighted in black, as shown in Fig 4 (b). Here, the machine learning technique named, MGA-RF is used to detect malicious users by analyzing the features, which are the information of vehicle users. In this framework, the security is strengthened in two phases, which include the proper vehicle registration & authentication, and attack analysis using MGA-RF. Then, the vehicle users can request the RSU to enable the data transmission/communication with the neighborhood vehicle users. As shown in Fig 4 (c), the requested vehicle users are highlighted in red color, where the RSU can authenticate the requested vehicle users for communication. After that, the data transmission/communication is established between the authenticated vehicles in a certain range, as shown in Fig 4 (d).
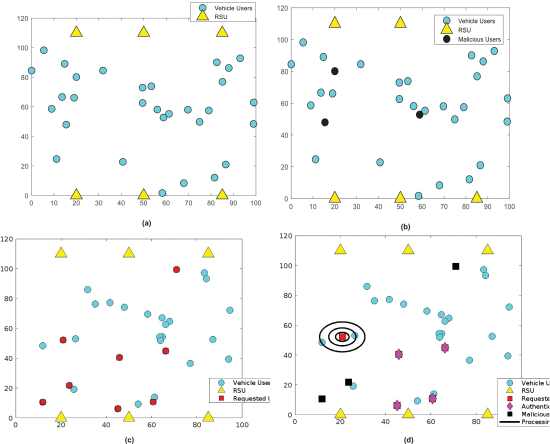
FIGURE 4.
Network deployment with (a) Set of vehicle users and RSU (b) Detection of malicious users (c) Requested nodes (d) Requested, authenticated and malicious nodes.
H. Security Analysis
Table 2 depicts the proposed CMA-MGA-RF model-based smart city networking architecture’s security and privacy analysis. Here, the different types of security features and their related issues are evaluated for the proposed system. The proposed model’s security analysis is assessed concerning varying security issues and their corresponding features. The properties that must be satisfied are resiliency, digital ledger, efficiency, anonymity, smart contract, persistency, and decentralization to ensure better performance and increased security of the system. These properties are assessed under security problems like third-party accessibility, eavesdropping, controlling access, frequent availability, data honesty, single-point failure, trustfulness, invariability, and data privacy. According to this analysis, it is identified that the proposed framework could efficiently satisfy all these properties with guaranteed network security. Due to incorporating the MGA-RF with the security framework, the reliable data transmission and communication of smart city networks are highly improved. The proposed framework satisfies the properties of resiliency, digital ledger, efficiency, anonymity, smart contract, persistency, and decentralization.
TABLE 2 Security and Privacy Analysis

SECTION IV.
Results and Discussion
This section validates the performance analysis of existing and proposed techniques using various evaluation indicators. Some conventional security architectures have been compared with the proposed framework based on latency, computational time, True Positive Rate (TPR), and False Positive Rate (FPR). Typically, the overall effectiveness of the networking framework is determined by increased scalability and reduced latency measures. Figures 5 and 6 show the total latency of both existing and proposed approaches concerning the industrial data source and the number of sources. The results show that the total latency of the proposed CMA-MGA-RF model is efficiently reduced compared to the conventional approaches for both numbers services and industrial sources.

FIGURE 5.
Total latency vs industrial data source.
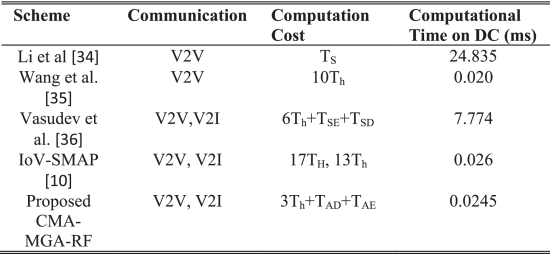
Table 3 presents the comparative analysis of both existing [10] and proposed techniques based on the computational time of Desktop Computer (DC) (ms). Here, the computational time is measured by the time required for designing the security architecture with minimized complexity. Moreover, computational cost and time are the most extensively used performance indicators for validating the overall effectiveness of the networking systems. The analysis proves that the proposed CMA-MGA-RF model requires reduced computational time for processing the security functions and detecting the attacking events on the smart city networks. Compared to conventional techniques, the proposed model provides less computational time for both DC and RP in milliseconds.
TABLE 3 Computational Time Analysis
Consequently, Table 4 and Table 5 compares the communication cost and storage overhead of conventional and proposed security schemes based on the communications of V2V and V2I respectively. Here, the TAE represents the asymmetric encryption, TAD indicates the asymmetric decryption, TS is the signing operation, TSE denotes the symmetric encryption, TSD symmetric decryption, and Th indicates the hash function. The obtained results depict that the proposed security model requires reduced communication cost and storage overhead, when compared to the other techniques.
TABLE 4 Analysis of Communication Cost
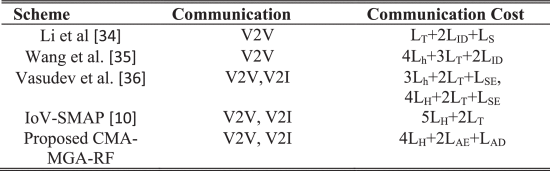
TABLE 5 Analysis of Storage Overhead
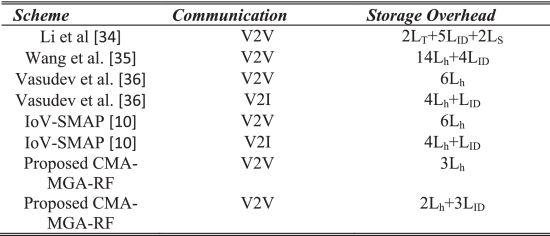
Fig 7 illustrates the TPR and FPR analysis of both existing [27] and proposed classification systems, which includes the models of center line, RL-RF, SVM, RF, and Bayes Net. Typically, the TPR and FPR measures are used to validate that how effectively the classifier predicts the attacking labels as normal or attack, which are computed as follows:
TPR=FPR=TPTP+FNFPFP+TN(1)(2)
View Source
where, TP indicates the True Positives, TN indicates the True Negatives, FP is the False Positives, and FN is the False Negatives (FN). Based on this evaluation, it is analyzed that the proposed CMA-MGA-RF model provides an increased TPR by accurately classifying the attacking labels compared to the other approaches. The accuracy is one of the essential measures used for validating the performance of overall security systems, which is calculated as follows:
Accuracy=TP+TNTP+TN+FP+FN(3)
View SourceAlso, the attack detection mechanism’s effectiveness depends on the measure of accuracy. It is calculated based on the percentage of accurately detected flows concerning the total number of predictions. Table 6 and Fig 8 show the accuracy analysis of existing and proposed security mechanisms, including RL-RF, Bayes Net, RF, SVM, and proposed CMA-MGA-RF mechanisms. From the results, it is evident that the proposed technique outperforms the other methods with increased accuracy. Precision, recall, and TPR are the performance measures mainly used to determine that how the classification technique could actually predict the exact values at the time of attack detection. Also, the relevancy level of both actual and predicted class labels are estimated with respect to the classified outcomes, which ensures an improved performance of the proposed technique with reduced training level.
Precision=Recall=TPTP+FPTPTP+FN(4)(5)
View Source
TABLE 6 Analysis of Accuracy
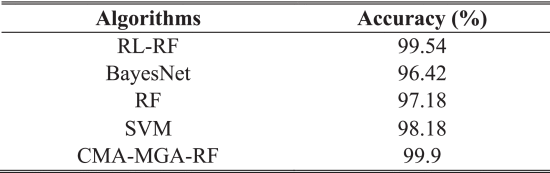
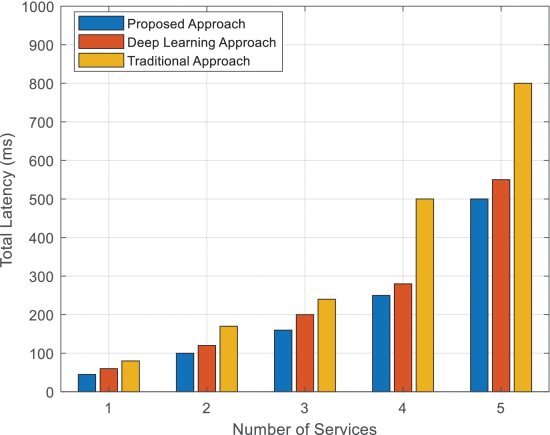
FIGURE 6.
Total latency vs number of services.
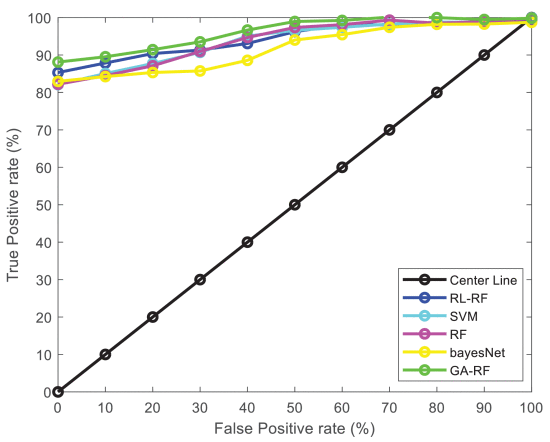
FIGURE 7.
TPR vs FPR.
Table 7 compares the existing and proposed security mechanisms based on accuracy, precision, recall, and TPR measures. The techniques considered for this analysis are Bayes Net, C4.5, Naïve Bayes (NB), Random Forest (RF), Random Tree (RT), and proposed CMA-MGA-RF. Then, its corresponding graphical representations are presented in Fig 9 and Fig 10. Based on this comparative analysis, it is stated that the proposed CMA-MGA-RF technique provides improved results compared to the other techniques. Because it ensures the security of smart city networks by the key generation, authentication, and key agreement processes, these modules help to strict the authorized access on the network with increased privacy and security measures. Also, it detects the attacking activities by accurately predicting the classified labels based on the optimal fitness computation of MGA. Table 8 presents the Time Taken to Build Model (TTBM) analysis of existing and proposed mechanisms. These results also indicate that the proposed technique consumes less time for constructing the security framework. Compared to the other models, the TTBM of the proposed CMA-MGA-RF model takes less time to design the networking system.
TABLE 7 Overall Performance Analysis of Existing and Proposed Techniques
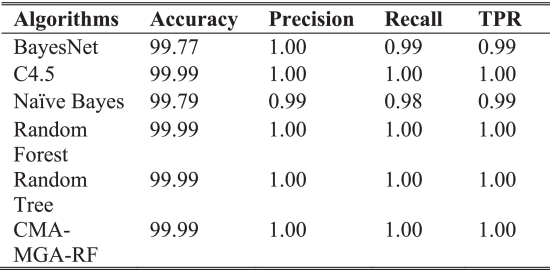
TABLE 8 Analysis of TTB

FIGURE 8.
Accuracy analysis of existing and proposed security mechanisms.
FIGURE 9.
Accuracy of existing and proposed classification techniques.
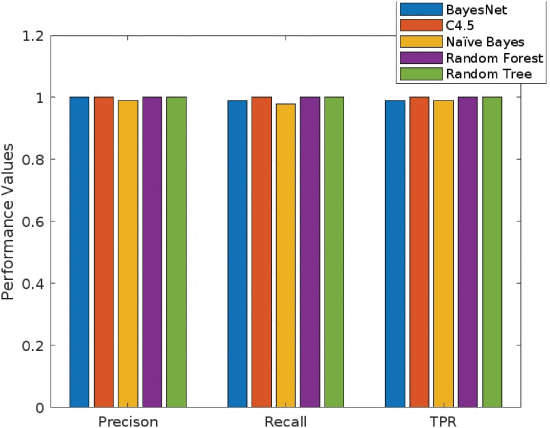
FIGURE 10.
Accuracy of existing and proposed classification techniques.
SECTION V.
Conclusion
This paper proposed intelligent network architecture to ensure the privacy and security of smart city networks. The key focus of this work is to establish secure and valid network communication by applying the proper authentication mechanism. The major stages involved in this system design are the registration phase, login phase, authentication phase, key agreement phase, and attack analysis. At first, the smart card generation is carried out during the registration process based on the hash function value. Then, the user can log in to the system with their smart card, authentication key, identity, and passwords. Once the remote server receives a request from the appropriate user, it validates the authenticity of the user by using the session key.
Similarly, the user can validate the corresponding session key with the authenticated message for key agreement. The user can be considered an authenticated party if both keys are matched. To detect malicious activities on the network, the MGA-RF-based machine learning algorithm is employed to improve the security of smart city networks. Furthermore, the performance results of both existing and proposed techniques are evaluated and compared using the latency, TPR, accuracy, precision, recall and TTBM. Based on the obtained results, it is proved that the proposed CMA-MGA-RF outperforms the other techniques with improved performance values.
In the present work, the Collaborative Mutual Authentication (CMA) based blockchain mechanism is mainly developed to guarantee the security of smart city networks with proper registration, login, and authentication modules. It helps to filter the unauthenticated/malicious vehicle nodes in the network. In addition, an optimization integrated machine learning methodology, named as, MGA-RF is implemented to ensure the reliable data communication in the network by detecting the attacks in the network. In the proposed system, the distributed ledger– machine learning protocol is used to strengthen the security of smart city network. In future, the proposed distributed ledger blockchain framework can be implemented in a real-time scenario by getting funds.
ACKNOWLEDGMENT
The authors, therefore, acknowledge with thanks the Deanship of Scientific Research for technical and financial support.





















 273
273











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








