前言
Apache Ranger是什么,它是一个为Hadoop平台提供了全面的数据安全访问控制及监控的集中式管理框架,Apache顶级项目。不废话了,其实本篇没那么高大上,就是一步步教你如何将Ranger源码导入到IDEA,并运行调试其web模块。
环境说明
| 环境 | 版本 | 备注 |
| system | Mac Intel Chip | |
| java | 1.8.0_292 | |
| mysql | 5.7.35 | |
| mysql-connector-java | 5.1.31 | |
| maven | 3.8.1 | |
| tomcat | 8.5.69 | 1,适用于ranger 2.2 2,需要保证tomcat的安装目录有足够的权限,笔者简单的执行了 chmod -R 777 apache-tomcat-8.5.69 |
| tomcat | 7.0.109 | 1,适用于ranger release-ranger-2.1.0 2,需要保证tomcat的安装目录有足够的权限,笔者简单的执行了 chmod -R 777 apache-tomcat-7.0.109 3,旧版本的tomcat可以移步寻找:http://archive.apache.org/dist/tomcat/tomcat-7/v7.0.109/bin/ -> apache-tomcat-7.0.109.zip |
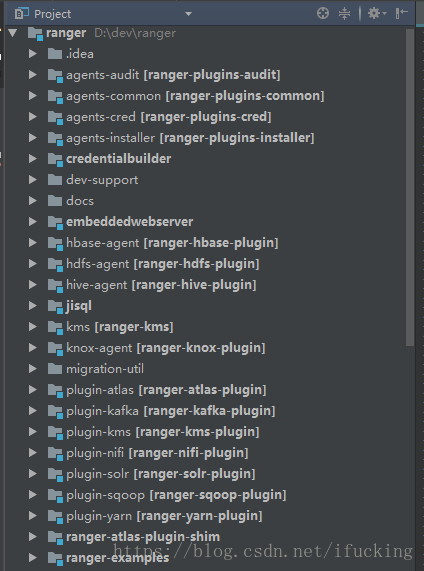
导入源码
1.第一步当然是下载源码,这里选用了最新版2.2
git clone https://github.com/apache/ranger.git
git checkout ranger-2.22.编译,这里选择编译全部,当然也可以选择具体模块进行编译,耗时会比较长
mvn -DskipTests=true clean compile package install assembly:assembly如笔者注释了storm、solr、tagsync、atlas、sqoop、kylin等模块:

3.添加idea相关配置及依赖
mvn idea:idea4.直接导入就行了,what?你不会连导入都不会吧
运行调试security-admin web模块
先初始化数据库,这里推荐选用MySQL,PostgreSQL我初始化的时候报了N多错,直接放弃了。
配置Ranger Admin
以下更改的文件路径:security-admin/src/main/resources/conf.dist/ranger-admin-site.xml
配置审计日志,没有装solr可以不用管
<property>
<name>ranger.audit.solr.urls</name>
<value>http://localhost:6083/solr/ranger_audits</value>
<description></description>
</property>
<property>
<name>ranger.audit.source.type</name>
<value>solr</value>
<description></description>
</property> 配置Ranger数据库及用户名密码
<property>
<name>ranger.jpa.jdbc.url</name>
<value>jdbc:log4jdbc:mysql://localhost:3306/ranger</value>
<description></description>
</property>
<property>
<name>ranger.jpa.jdbc.user</name>
<value>admin</value>
<description></description>
</property>
<property>
<name>ranger.jpa.jdbc.password</name>
<value>admin</value>
<description></description>
</property>配置web
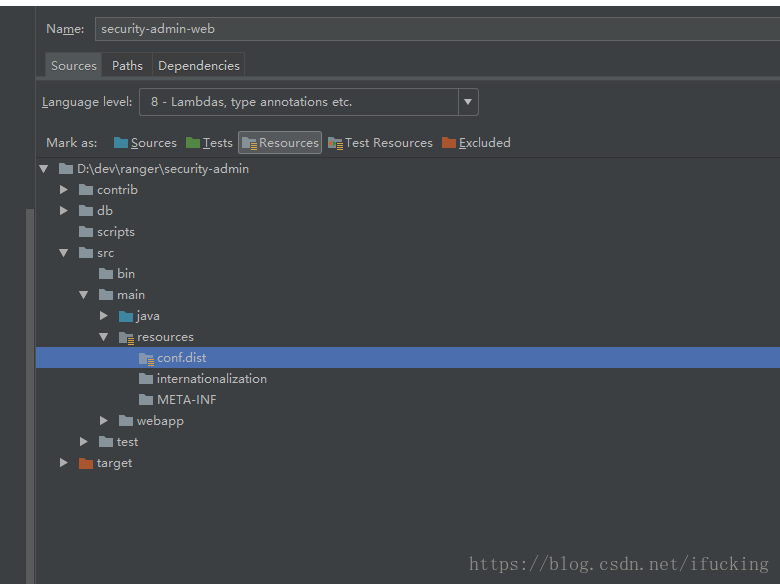
这里有二种方式:
第一种 将security-admin/src/main/resources/conf.dist 设置为resources目录
修改security-admin/src/main/webapp/WEB-INF/web.xml
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>META-INF/applicationContext.xml
WEB-INF/classes/security-applicationContext.xml
META-INF/scheduler-applicationContext.xml</param-value>
</context-param>修改security-admin/src/main/webapp/META-INF/applicationContext.xml
<property name="locations">
<list>
<!-- <value>classpath:xa_default.properties</value> -->
<!-- <value>classpath:xa_system.properties</value> -->
<!-- <value>classpath:xa_custom.properties</value> -->
<!-- <value>classpath:xa_ldap.properties</value> -->
<!-- <value>classpath:core-site.xml</value> -->
<value>classpath:ranger-admin-default-site.xml</value>
<value>classpath:ranger-admin-site.xml</value>
</list>
</property>第二种 只修改配置文件
修改security-admin/src/main/webapp/WEB-INF/web.xml
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>META-INF/applicationContext.xml
WEB-INF/classes/conf.dist/security-applicationContext.xml
META-INF/scheduler-applicationContext.xml</param-value>
</context-param>修改security-admin/src/main/webapp/META-INF/applicationContext.xml
<property name="locations">
<list>
<!-- <value>classpath:xa_default.properties</value> -->
<!-- <value>classpath:xa_system.properties</value> -->
<!-- <value>classpath:xa_custom.properties</value> -->
<!-- <value>classpath:xa_ldap.properties</value> -->
<!-- <value>classpath:conf.dist/core-site.xml</value> -->
<value>classpath:conf.dist/ranger-admin-default-site.xml</value>
<value>classpath:conf.dist/ranger-admin-site.xml</value>
</list>
</property>数据库配置
1.新建ranger数据库
create database ranger character set utf8;2.执行两个初始化sql文件
mysql_core_file=db/mysql/optimized/current/ranger_core_db_mysql.sql
mysql_audit_file=db/mysql/xa_audit_db.sql3.正常执行完第2步,可跳过该步骤;如果报错:“Specified key was too long; max key length is 767 bytes”,则先执行(具体原因google)
set global innodb_file_format = BARRACUDA;
set global innodb_large_prefix = ON;4.执行sql的时候要留意是否报错
ERROR 1418 (HY000) at line 1599 in file: 'ranger_core_db_mysql.sql':
This function has none of DETERMINISTIC, NO SQL, or READS SQL DATA in its declaration and binary logging is enabled
(you *might* want to use the less safe log_bin_trust_function_creators variable)
Query OK, 0 rows affected, 1 warning (0.00 sec)
ERROR 1418 (HY000) at line 1609 in file: 'ranger_core_db_mysql.sql':
This function has none of DETERMINISTIC, NO SQL, or READS SQL DATA in its declaration and binary logging is enabled
(you *might* want to use the less safe log_bin_trust_function_creators variable)
Query OK, 1 row affected (0.01 sec) 如果出现这个报错,那么代表 getXportalUIdByLoginId 方法创建失败,后续通过getXportalUIdByLoginId 拿数据的dml都将报错,导致数据插入失败。
笔者整理了执行失败的dml语句(直接用getXportalUIdByLoginId结果代入):
INSERT INTO x_portal_user_role (id, create_time, update_time, added_by_id, upd_by_id, user_id, user_role, status) VALUES (1, '2021-09-29 11:39:15', '2021-09-29 11:39:15', null, null, 1, 'ROLE_SYS_ADMIN', 1);
INSERT INTO x_portal_user_role (id, create_time, update_time, added_by_id, upd_by_id, user_id, user_role, status) VALUES (2, '2021-09-29 11:39:15', '2021-09-29 11:39:15', null, null, 2, 'ROLE_SYS_ADMIN', 1);
INSERT INTO x_portal_user_role (id, create_time, update_time, added_by_id, upd_by_id, user_id, user_role, status) VALUES (3, '2021-09-29 11:39:15', '2021-09-29 11:39:15', null, null, 3, 'ROLE_KEY_ADMIN', 1);
INSERT INTO x_portal_user_role (id, create_time, update_time, added_by_id, upd_by_id, user_id, user_role, status) VALUES (4, '2021-09-29 11:39:15', '2021-09-29 11:39:15', null, null, 4, 'ROLE_SYS_ADMIN', 1);
INSERT INTO x_group (id, create_time, update_time, added_by_id, upd_by_id, group_name, descr, status, group_type, cred_store_id, group_src, is_visible, other_attributes) VALUES (1, '2021-09-29 11:39:15', '2021-09-29 11:39:15', 1, 1, 'public', 'public group', 0, 0, null, 0, 1, null);
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (1, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Resource Based Policies', '');
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (2, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Users/Groups', '');
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (3, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Reports', '');
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (4, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Audit', '');
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (5, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Key Manager', '');
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (6, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Tag Based Policies', '');
INSERT INTO x_modules_master (id, create_time, update_time, added_by_id, upd_by_id, module, url) VALUES (7, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 'Security Zone', '');
INSERT INTO x_security_zone (id, create_time, update_time, added_by_id, upd_by_id, version, name, jsonData, description) VALUES (1, '2021-09-29 11:39:16', '2021-09-29 11:39:16', 1, 1, 1, ' ', '', 'Unzoned zone');
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (1, 1, 3, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (2, 1, 1, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (3, 1, 4, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (4, 1, 2, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (5, 1, 6, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (6, 2, 3, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (7, 2, 1, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (8, 2, 4, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (9, 2, 2, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (10, 2, 6, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (11, 3, 5, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (12, 3, 3, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (13, 3, 1, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (14, 4, 3, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (15, 4, 1, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (16, 4, 4, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (17, 4, 2, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (18, 4, 6, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (19, 3, 2, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (20, 3, 4, '2021-09-29 11:39:18', '2021-09-29 11:39:18', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (21, 1, 7, '2021-09-29 11:39:19', '2021-09-29 11:39:19', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (22, 2, 7, '2021-09-29 11:39:19', '2021-09-29 11:39:19', 1, 1, 1);
INSERT INTO x_user_module_perm (id, user_id, module_id, create_time, update_time, added_by_id, upd_by_id, is_allowed) VALUES (23, 4, 7, '2021-09-29 11:39:19', '2021-09-29 11:39:19', 1, 1, 1);
INSERT INTO x_ranger_global_state (id, create_time, update_time, added_by_id, upd_by_id, version, state_name, app_data) VALUES (1, '2021-09-29 11:39:19', '2021-09-29 11:39:19', 1, 1, 1, 'RangerRole', '{"Version":"1"}');
INSERT INTO x_ranger_global_state (id, create_time, update_time, added_by_id, upd_by_id, version, state_name, app_data) VALUES (2, '2021-09-29 11:39:19', '2021-09-29 11:39:19', 1, 1, 1, 'RangerUserStore', '{"Version":"1"}');
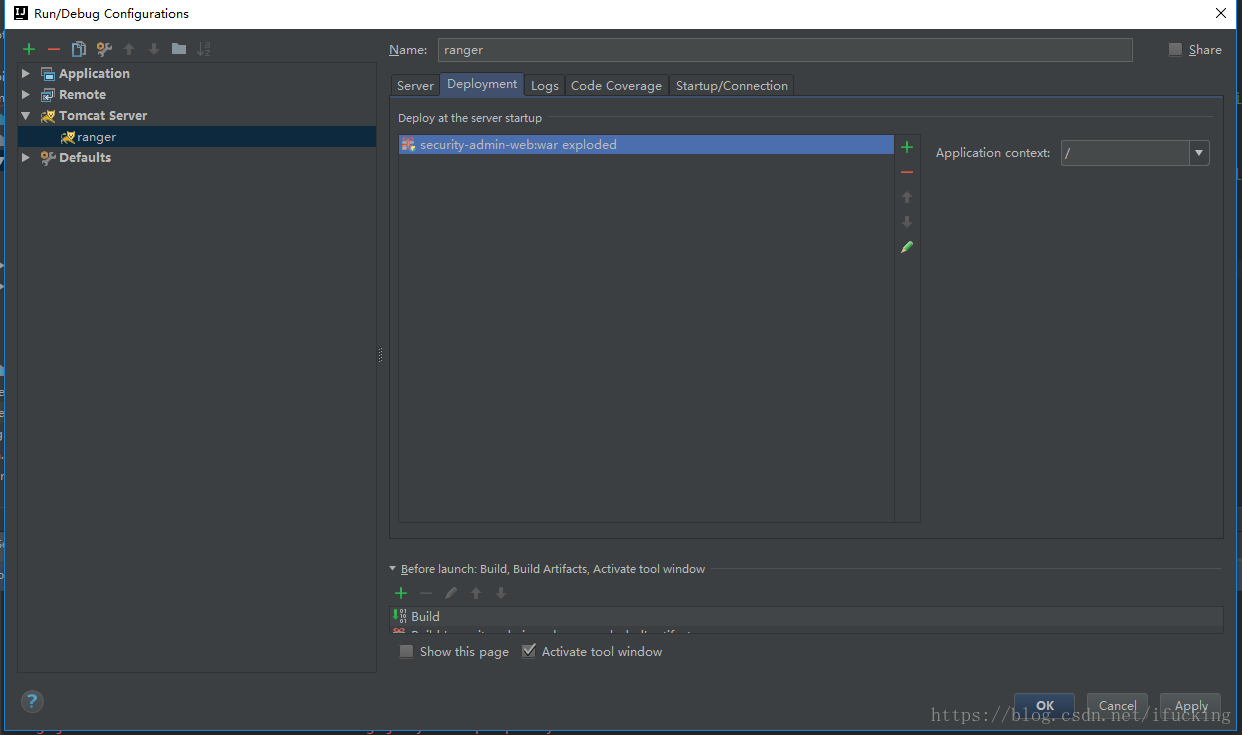
INSERT INTO x_ranger_global_state (id, create_time, update_time, added_by_id, upd_by_id, version, state_name, app_data) VALUES (3, '2021-09-29 11:39:19', '2021-09-29 11:39:19', 1, 1, 1, 'RangerSecurityZone', '{"Version":"1"}');添加tomcat
然后就可以运行调试了,尽情的debug调试吧。
访问问题
1.admin/admin访问,Sign in一直转圈圈

2.通过调试发现“No suitable driver”

3.在ranger/security-admin/target/security-admin-web-2.2.0/WEB-INF/lib
或ranger/security-admin/target/ranger-2.1.0/WEB-INF/lib(不同版本这里对应的路径不同)
中添加上“mysql-connector-java-5.1.31.jar”(关于mysql-connector-java的版本号未有定论,一劳永逸的fix也未有定论)

4.一顿瞎操作后重启tomcat,正常访问

调试Hive Policy
如图所示,在目录 ranger/security-admin/target/security-admin-web-2.1.0/WEB-INF/classes/ranger-plugins/hive 下放上了hive plugin,其他插件雷同
调试xuser和policy所用postman:
{
"info": {
"_postman_id": "91f4e58b-e727-48ae-a960-1f405c8c8beb",
"name": "ranger",
"schema": "https://schema.getpostman.com/json/collection/v2.1.0/collection.json"
},
"item": [
{
"name": "/service/xusers/secure/users",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "POST",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"name\": \"test111034\",\n \"password\": \"Aa123456\",\n \"firstName\": \"test1110\",\n \"lastName\": \"\",\n \"emailAddress\": \"\",\n \"userRoleList\": [\n \"ROLE_USER\"\n ],\n \"groupIdList\": null,\n \"status\": 1\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/xusers/secure/users",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"xusers",
"secure",
"users"
]
}
},
"response": []
},
{
"name": "/service/xusers/users/userName/{userName}",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "GET",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"url": {
"raw": "http://localhost:8080/service/xusers/users/userName/test11102",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"xusers",
"users",
"userName",
"test11102"
]
}
},
"response": []
},
{
"name": "/service/xusers/users/userName/{userName}",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "DELETE",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"url": {
"raw": "http://localhost:8080/service/xusers/users/userName/test11102?forceDelete=true",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"xusers",
"users",
"userName",
"test11102"
],
"query": [
{
"key": "forceDelete",
"value": "true"
}
]
}
},
"response": []
},
{
"name": "/service/xusers/secure/users/{userName}",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "DELETE",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"url": {
"raw": "http://localhost:8080/service/xusers/secure/users/test11102?forceDelete=true",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"xusers",
"secure",
"users",
"test11102"
],
"query": [
{
"key": "forceDelete",
"value": "true"
}
]
}
},
"response": []
},
{
"name": "/service/plugins/policies",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "POST",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"policyType\": \"0\",\n \"name\": \"test1110_pol2\",\n \"isEnabled\": true,\n \"policyPriority\": 0,\n \"policyLabels\": [],\n \"description\": \"description\",\n \"isAuditEnabled\": true,\n \"resources\": {\n \"database\": {\n \"values\": [\n \"db1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"table\": {\n \"values\": [\n \"tb1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"column\": {\n \"values\": [\n \"*\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n }\n },\n \"isDenyAllElse\": false,\n \"policyItems\": [\n {\n \"users\": [\n \"test11102\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n },\n {\n \"type\": \"read\",\n \"isAllowed\": true\n }\n ]\n }\n ],\n \"allowExceptions\": [],\n \"denyPolicyItems\": [],\n \"denyExceptions\": [],\n \"service\": \"hive_ser\"\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/plugins/policies",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"plugins",
"policies"
]
}
},
"response": []
},
{
"name": "/service/plugins/policies/9",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "PUT",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"id\": 9,\n \"guid\": \"7c44b325-c4a8-4cda-9e0d-8230efd02baf\",\n \"isEnabled\": true,\n \"createdBy\": \"Admin\",\n \"updatedBy\": \"Admin\",\n \"createTime\": 1636490859000,\n \"updateTime\": 1636490859000,\n \"version\": 1,\n \"service\": \"hive_ser\",\n \"name\": \"test1110_pol\",\n \"policyType\": 0,\n \"policyPriority\": 0,\n \"description\": \"description\",\n \"resourceSignature\": \"9679f30b678a5e1e2013be629c0fbc8c3e29ba9949375e9c16e5b9431f67c0af\",\n \"isAuditEnabled\": true,\n \"resources\": {\n \"database\": {\n \"values\": [\n \"db1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"table\": {\n \"values\": [\n \"tb1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"column\": {\n \"values\": [\n \"*\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n }\n },\n \"policyItems\": [\n {\n \"users\": [\n \"test11102\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n },\n {\n \"type\": \"read\",\n \"isAllowed\": true\n }\n ]\n },\n {\n \"users\": [\n \"test11103\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n }\n ]\n }\n ],\n \"denyPolicyItems\": [],\n \"allowExceptions\": [],\n \"denyExceptions\": [],\n \"dataMaskPolicyItems\": [],\n \"rowFilterPolicyItems\": [],\n \"serviceType\": \"hive\",\n \"options\": {},\n \"validitySchedules\": [],\n \"policyLabels\": [],\n \"zoneName\": \"\",\n \"isDenyAllElse\": false\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/plugins/policies/9",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"plugins",
"policies",
"9"
]
}
},
"response": []
},
{
"name": "/service/plugins/policies/9 精简版",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "PUT",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"id\": 9,\n \"isEnabled\": true,\n \"service\": \"hive_ser\",\n \"name\": \"test1110_pol\",\n \"policyType\": 0,\n \"policyPriority\": 0,\n \"description\": \"description\",\n \"isAuditEnabled\": true,\n \"resources\": {\n \"database\": {\n \"values\": [\n \"db1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"table\": {\n \"values\": [\n \"tb1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"column\": {\n \"values\": [\n \"*\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n }\n },\n \"policyItems\": [\n {\n \"users\": [\n \"test11102\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n },\n {\n \"type\": \"read\",\n \"isAllowed\": true\n }\n ]\n },\n {\n \"users\": [\n \"test11103\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n }\n ]\n }\n ],\n \"denyPolicyItems\": [],\n \"allowExceptions\": [],\n \"denyExceptions\": [],\n \"policyLabels\": [],\n \"isDenyAllElse\": false\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/plugins/policies/9",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"plugins",
"policies",
"9"
]
}
},
"response": []
},
{
"name": "/service/public/v2/api/service/hive_ser/policy/{policyname}",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "GET",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"url": {
"raw": "http://localhost:8080/service/public/v2/api/service/hive_ser/policy/test1110_pol",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"public",
"v2",
"api",
"service",
"hive_ser",
"policy",
"test1110_pol"
]
}
},
"response": []
},
{
"name": "/service/public/v2/api/service/hive_ser/policy/test1110_pol",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "PUT",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"id\": 9,\n \"isEnabled\": true,\n \"service\": \"hive_ser\",\n \"name\": \"test1110_pol\",\n \"policyType\": 0,\n \"policyPriority\": 0,\n \"description\": \"description\",\n \"isAuditEnabled\": true,\n \"resources\": {\n \"database\": {\n \"values\": [\n \"db1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"table\": {\n \"values\": [\n \"tb1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"column\": {\n \"values\": [\n \"*\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n }\n },\n \"policyItems\": [\n {\n \"users\": [\n \"test11102\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n },\n {\n \"type\": \"read\",\n \"isAllowed\": true\n }\n ]\n },\n {\n \"users\": [\n \"test11103\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n }\n ]\n },\n {\n \"users\": [\n \"123456\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n }\n ]\n }\n ],\n \"denyPolicyItems\": [],\n \"allowExceptions\": [],\n \"denyExceptions\": [],\n \"policyLabels\": [],\n \"isDenyAllElse\": false\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/public/v2/api/service/{servicename}/policy/{policyname}",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"public",
"v2",
"api",
"service",
"{servicename}",
"policy",
"{policyname}"
]
}
},
"response": []
},
{
"name": "/service/public/v2/api/policy?servicename=hive_ser&policyname=d",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "DELETE",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"id\": 9,\n \"isEnabled\": true,\n \"service\": \"hive_ser\",\n \"name\": \"test1110_pol\",\n \"policyType\": 0,\n \"policyPriority\": 0,\n \"description\": \"description\",\n \"isAuditEnabled\": true,\n \"resources\": {\n \"database\": {\n \"values\": [\n \"db1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"table\": {\n \"values\": [\n \"tb1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"column\": {\n \"values\": [\n \"*\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n }\n },\n \"policyItems\": [\n {\n \"users\": [\n \"test11102\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n },\n {\n \"type\": \"read\",\n \"isAllowed\": true\n }\n ]\n },\n {\n \"users\": [\n \"test11103\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n }\n ]\n },\n {\n \"users\": [\n \"123456\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n }\n ]\n }\n ],\n \"denyPolicyItems\": [],\n \"allowExceptions\": [],\n \"denyExceptions\": [],\n \"policyLabels\": [],\n \"isDenyAllElse\": false\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/public/v2/api/policy?servicename=hive_ser&policyname=d",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"public",
"v2",
"api",
"policy"
],
"query": [
{
"key": "servicename",
"value": "hive_ser"
},
{
"key": "policyname",
"value": "d"
}
]
}
},
"response": []
},
{
"name": "/service/public/v2/api/policy",
"request": {
"auth": {
"type": "basic",
"basic": [
{
"key": "password",
"value": "admin",
"type": "string"
},
{
"key": "username",
"value": "admin",
"type": "string"
}
]
},
"method": "POST",
"header": [
{
"key": "Accept",
"value": "application/json",
"type": "text"
}
],
"body": {
"mode": "raw",
"raw": "{\n \"policyType\": \"0\",\n \"name\": \"test1110_pol23\",\n \"isEnabled\": true,\n \"policyPriority\": 0,\n \"policyLabels\": [],\n \"description\": \"description\",\n \"isAuditEnabled\": true,\n \"resources\": {\n \"database\": {\n \"values\": [\n \"db1110\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"table\": {\n \"values\": [\n \"tb111022\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n },\n \"column\": {\n \"values\": [\n \"*\"\n ],\n \"isRecursive\": false,\n \"isExcludes\": false\n }\n },\n \"isDenyAllElse\": false,\n \"policyItems\": [\n {\n \"users\": [\n \"test11102\"\n ],\n \"accesses\": [\n {\n \"type\": \"select\",\n \"isAllowed\": true\n },\n {\n \"type\": \"read\",\n \"isAllowed\": true\n }\n ]\n }\n ],\n \"allowExceptions\": [],\n \"denyPolicyItems\": [],\n \"denyExceptions\": [],\n \"service\": \"hive_ser\"\n}",
"options": {
"raw": {
"language": "json"
}
}
},
"url": {
"raw": "http://localhost:8080/service/public/v2/api/policy",
"protocol": "http",
"host": [
"localhost"
],
"port": "8080",
"path": [
"service",
"public",
"v2",
"api",
"policy"
]
}
},
"response": []
}
]
}





















 6618
6618











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








