8、部署CNI网络
8.1、node节点部署CNI
(1)下载地址
https://github.com/containernetworking/plugins/releases/download/v0.8.6/cni-plugins-linux-amd64-v0.8.6.tgz
#并将文件拷贝到虚拟机/opt目录;
(2) 文件准备
#创建文件夹
mkdir /opt/cni/bin
#解压文件
tar zxvf cni-plugins-linux-amd64-v0.8.6.tgz -C /opt/cni/bin
#集群会自动识别
8.2、master部署flannel
(1)方法一(在线):拉取官方镜像
wget https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml
如果默认镜像地址无法访问,通过sed命令修改为docker hub镜像仓库,执行命令如下:
kubectl apply -f https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml
#检查 Pod 的状态,可能存在ImagePullError(镜像拉取失败)
kubectl get pods -n kube-system
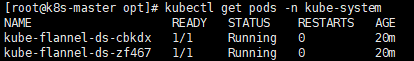
(2)方法二(离线):拉取国内镜像
- 通过https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml 链接将kube-flannel.yml文件下载到本地,并拷贝到Linux环境目录/opt/k8s.
- 从阿里云拉取flannel镜像
#当前最新版本
docker pull registry.cn-hangzhou.aliyuncs.com/k8sos/flannel:v0.13.1-rc2
- 将kube-flannel.yml文件中的镜像名称(image: quay.io/coreos/flannel:vxx)全部替换为:registry.cn-hangzhou.aliyuncs.com/k8sos/flannel:v0.13.1-rc2
- 重新应用kube-flannel.yaml
#执行命令
kubectl apply -f /opt/k8s/kube-flannel.yml
#检查Pod状态,执行命令:
kubectl get pods -n kube-system
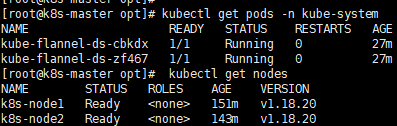
8.3、测试Kubernetes集群
在Kubernetes集群中创建一个Pod,验证是否正常运行:
#在k8s-master执行如下命令:
kubectl create deployment nginx --image=nginx #自动联网下载nginx镜像
#对外暴露80映射端口
kubectl expose deployment nginx --port=80 --type=NodePort
kubectl get pod,svc
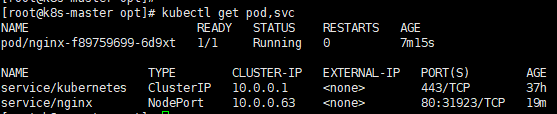
注意:会被调度到node1和node2节点,在node1和node2节点查看。访问地址:http://NodeIP:Port(此处为31923),或者通过命令curl GET http://nodeIP:31923访问,输出nginx默认页面如下:
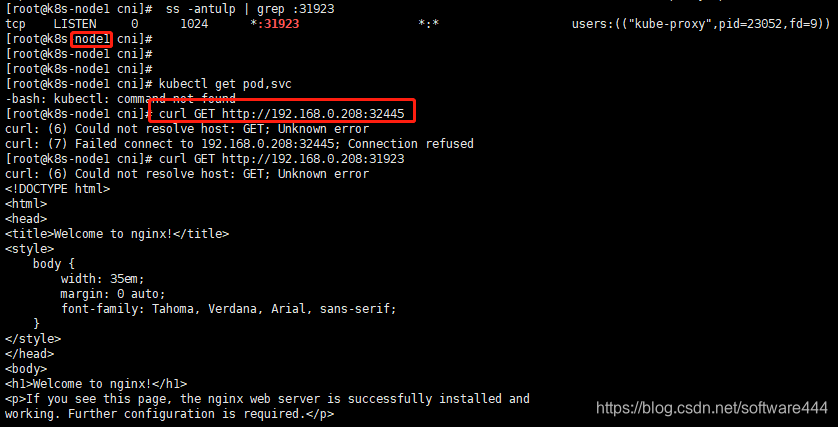
9、部署Dashboard
kubernetes Dashboard是kubernetes集群的Web UI,用于管理集群。
9.1、安装
Github地址:https://github.com/kubernetes/dashboard
创建 SSL 证书需要私钥和证书签名请求。这些可以通过一些简单的命令生成。当 openssl req 命令要求输入“挑战密码”时,只需按回车键,将密码留空。当证书颁发机构想要撤销其证书时,证书颁发机构使用此密码对证书所有者进行身份验证。由于这是一个自签名证书,因此无法通过 CRL(证书撤销列表)撤销它。
#进入服务器目录
cd /root/TLS/k8s
#生成自签证书
openssl genrsa -des3 -passout pass:over4chars -out dashboard.pass.key 2048
openssl rsa -passin pass:over4chars -in dashboard.pass.key -out dashboard.key
#写入 RSA 密钥
rm dashboard.pass.key
openssl req -new -key dashboard.key -out dashboard.csr
国家/地区名称(2 个字母代码)[CN]:中国
挑战密码 []:
#自签名 SSL 证书是从dashboard.key私钥和dashboard.csr文件生成的。
openssl x509 -req -sha256 -days 730 -in dashboard.csr -signkey dashboard.key -out dashboard.crt
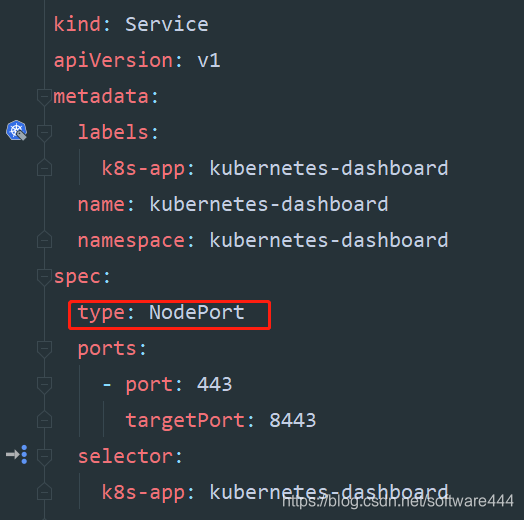
#在Service节出增加Type=NodePort
#ls-key-file=dashboard.key
#tls-cert-file=dashboard.crt
cat > recommend.yaml << EOF
apiVersion: v1
kind: Namespace
metadata:
name: kubernetes-dashboard
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
type: NodePort
ports:
- port: 443
targetPort: 8443
selector:
k8s-app: kubernetes-dashboard
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kubernetes-dashboard
type: Opaque
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-csrf
namespace: kubernetes-dashboard
type: Opaque
data:
csrf: ""
---
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-key-holder
namespace: kubernetes-dashboard
type: Opaque
---
kind: ConfigMap
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-settings
namespace: kubernetes-dashboard
---
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
rules:
# Allow Dashboard to get, update and delete Dashboard exclusive secrets.
- apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs", "kubernetes-dashboard-csrf"]
verbs: ["get", "update", "delete"]
# Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
- apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
# Allow Dashboard to get metrics.
- apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster", "dashboard-metrics-scraper"]
verbs: ["proxy"]
- apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:", "dashboard-metrics-scraper", "http:dashboard-metrics-scraper"]
verbs: ["get"]
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
rules:
# Allow Metrics Scraper to get metrics from the Metrics server
- apiGroups: ["metrics.k8s.io"]
resources: ["pods", "nodes"]
verbs: ["get", "list", "watch"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: kubernetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kubernetes-dashboard
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
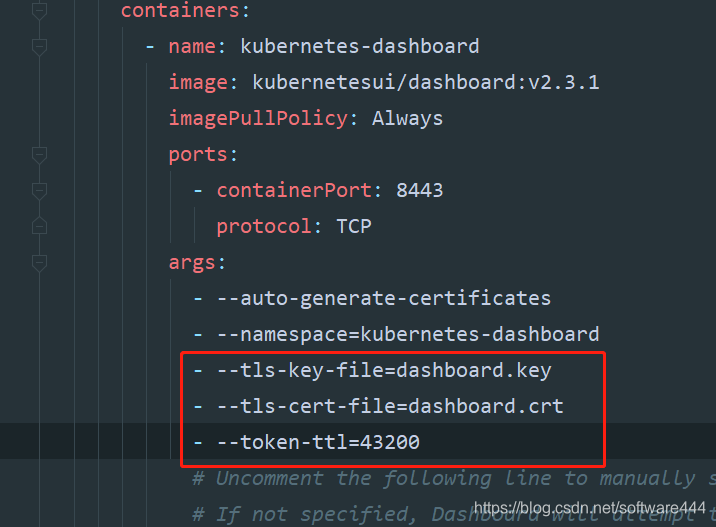
containers:
- name: kubernetes-dashboard
image: kubernetesui/dashboard:v2.3.1
imagePullPolicy: Always
ports:
- containerPort: 8443
protocol: TCP
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
- --tls-key-file=dashboard.key
- --tls-cert-file=dashboard.crt
- --token-ttl=43200
# Uncomment the following line to manually specify Kubernetes API server Host
# If not specified, Dashboard will attempt to auto discover the API server and connect
# to it. Uncomment only if the default does not work.
# - --apiserver-host=http://my-address:port
volumeMounts:
- name: kubernetes-dashboard-certs
mountPath: /certs
# Create on-disk volume to store exec logs
- mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
volumes:
- name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
---
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
ports:
- port: 8000
targetPort: 8000
selector:
k8s-app: dashboard-metrics-scraper
---
kind: Deployment
apiVersion: apps/v1
metadata:
labels:
k8s-app: dashboard-metrics-scraper
name: dashboard-metrics-scraper
namespace: kubernetes-dashboard
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: dashboard-metrics-scraper
template:
metadata:
labels:
k8s-app: dashboard-metrics-scraper
annotations:
seccomp.security.alpha.kubernetes.io/pod: 'runtime/default'
spec:
containers:
- name: dashboard-metrics-scraper
image: kubernetesui/metrics-scraper:v1.0.6
ports:
- containerPort: 8000
protocol: TCP
livenessProbe:
httpGet:
scheme: HTTP
path: /
port: 8000
initialDelaySeconds: 30
timeoutSeconds: 30
volumeMounts:
- mountPath: /tmp
name: tmp-volume
securityContext:
allowPrivilegeEscalation: false
readOnlyRootFilesystem: true
runAsUser: 1001
runAsGroup: 2001
serviceAccountName: kubernetes-dashboard
nodeSelector:
"kubernetes.io/os": linux
# Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
- key: node-role.kubernetes.io/master
effect: NoSchedule
volumes:
- name: tmp-volume
emptyDir: {}
EOF
#部署
kubectl apply -f recommend.yaml
#查看
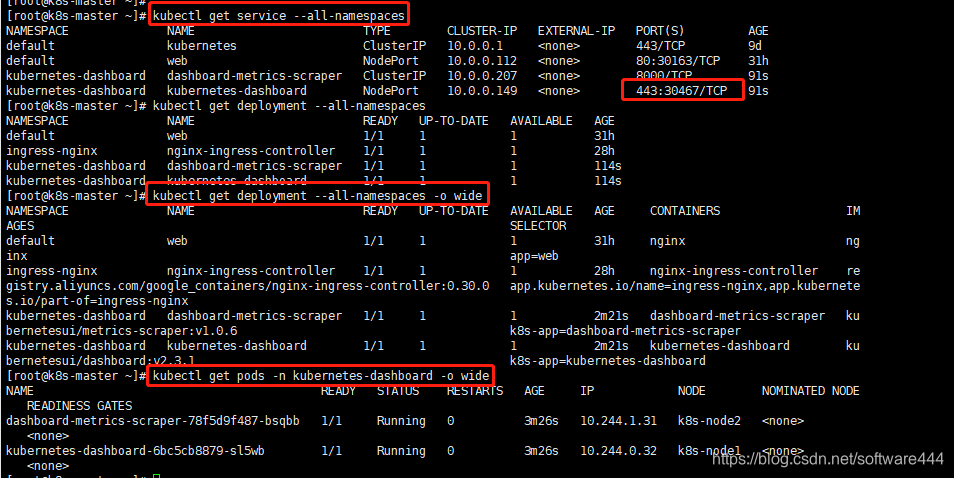
kubectl get pods -n kubernetes-dashboard -o wide
kubectl get svc -n kubernetes-dashboard -o wide
kubectl describe svc kubernetes-dashboard -n kubernetes-dashboard
#其他命令:查看所有
#kubectl get svc -A
#其他命令:编辑修改服务(Service)
#kubectl -n kubernetes-dashboard edit svc kubernetes-dashboard
9.2、配置证书
#查看所有secret
kubectl get secret -A
#删除默认创建的secret
kubectl delete secret kubernetes-dashboard-certs -n kubernetes-dashboard
#重新创建secret,主要用来指定证书的存放路径
kubectl create secret generic kubernetes-dashboard-certs --from-file=/root/TLS/k8s -n kubernetes-dashboard
#删除dashboard的pod,主要让它重新运行,加载证书
kubectl delete pod -n kubernetes-dashboard --all
(2)创建账户
cat > dashboard-adminuser.yaml << EOF
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
EOF
cat > dashboard-ClusterRoleBinding.yaml << EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
EOF
#创建服务账户
kubectl apply -f dashboard-adminuser.yaml
#创建一个ClusterRoleBinding
kubectl apply -f dashboard-ClusterRoleBinding.yaml
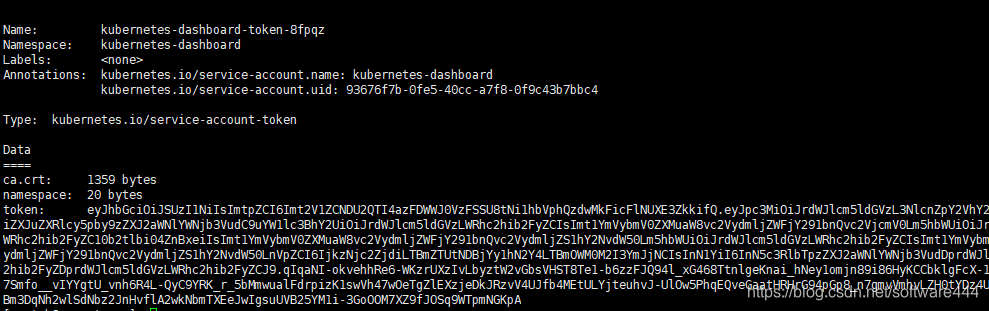
(3)获取登录token
#获取登录token,token粘贴登录
kubectl -n kubernetes-dashboard describe secret $(kubectl -n kubernetes-dashboard get secret | grep admin-user | awk '{print $1}')
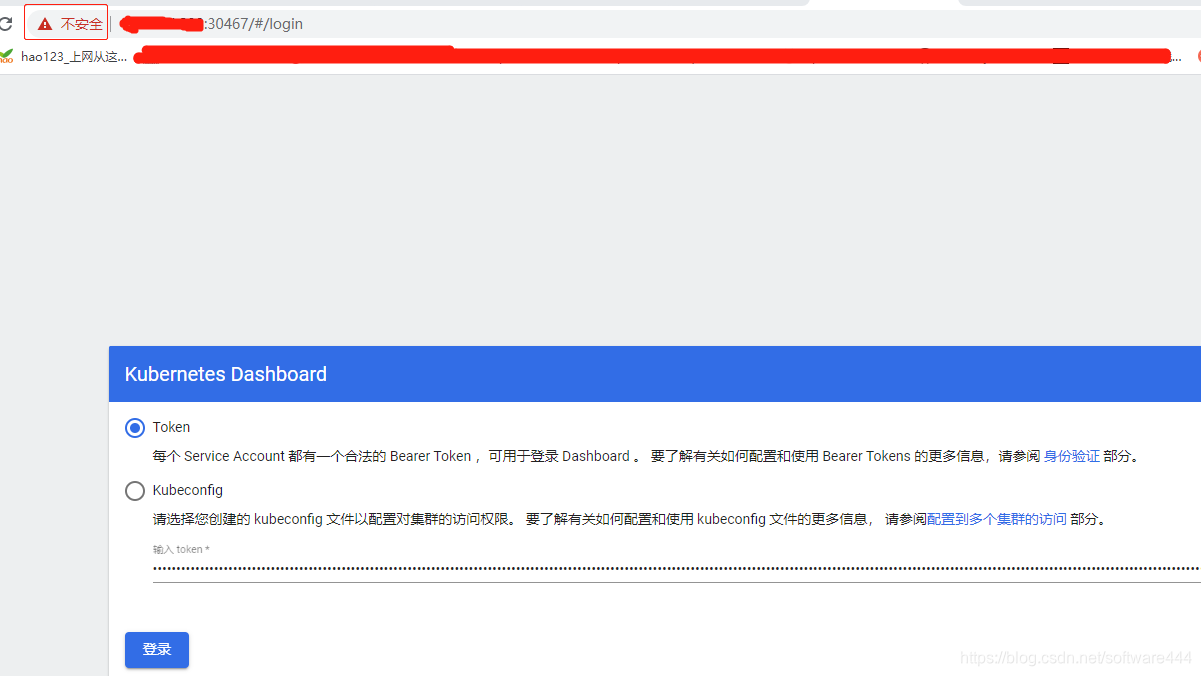
#登录地址(30467暴露NodePort端口)
https://ip:30467/#/login
























 648
648











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










