1、psnuffle 口令嗅探
msf > search name:psnuffle
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/sniffer/psnuffle normal pSnuffle Packet Sniffer
msf > use auxiliary/sniffer/psnuffle
msf auxiliary(psnuffle) > run
[*] Auxiliary module execution completed
msf auxiliary(psnuffle) >
[*] Loaded protocol FTP from /usr/share/metasploit-framework/data/exploits/psnuffle/ftp.rb...
[*] Loaded protocol IMAP from /usr/share/metasploit-framework/data/exploits/psnuffle/imap.rb...
[*] Loaded protocol POP3 from /usr/share/metasploit-framework/data/exploits/psnuffle/pop3.rb...
[*] Loaded protocol SMB from /usr/share/metasploit-framework/data/exploits/psnuffle/smb.rb...
[*] Loaded protocol URL from /usr/share/metasploit-framework/data/exploits/psnuffle/url.rb...
[*] Sniffing traffic.....
注意:等待嗅探成功
2、OpenVAS漏洞扫描器
1)配置OpenVAS
2)为OpenVAS创建用户并生成密码
root@kali:/var/log# openvasmd --create-user admin --role Admin
User created with password '4e8624ad-dd97-47e9-b8ee-95814645d6b8'.
注意:如原先有用户可以用以下命令进行删除
root@kali:/var/log# openvasmd --delete-user admin --role Admin
User deleted.
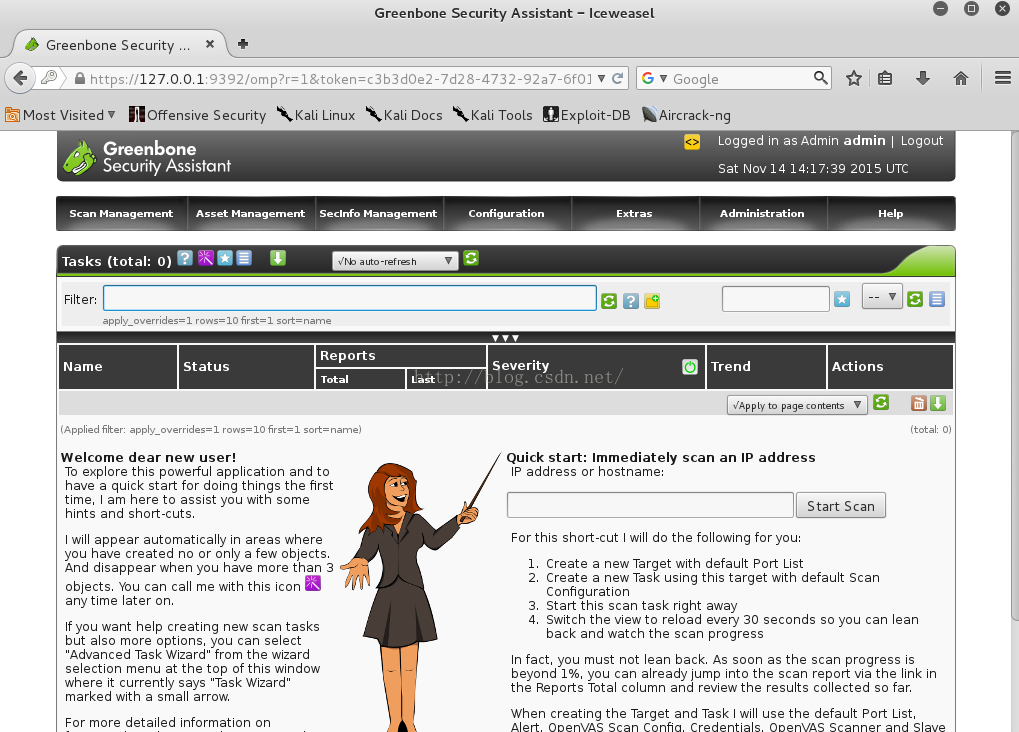
1)配置扫描策略
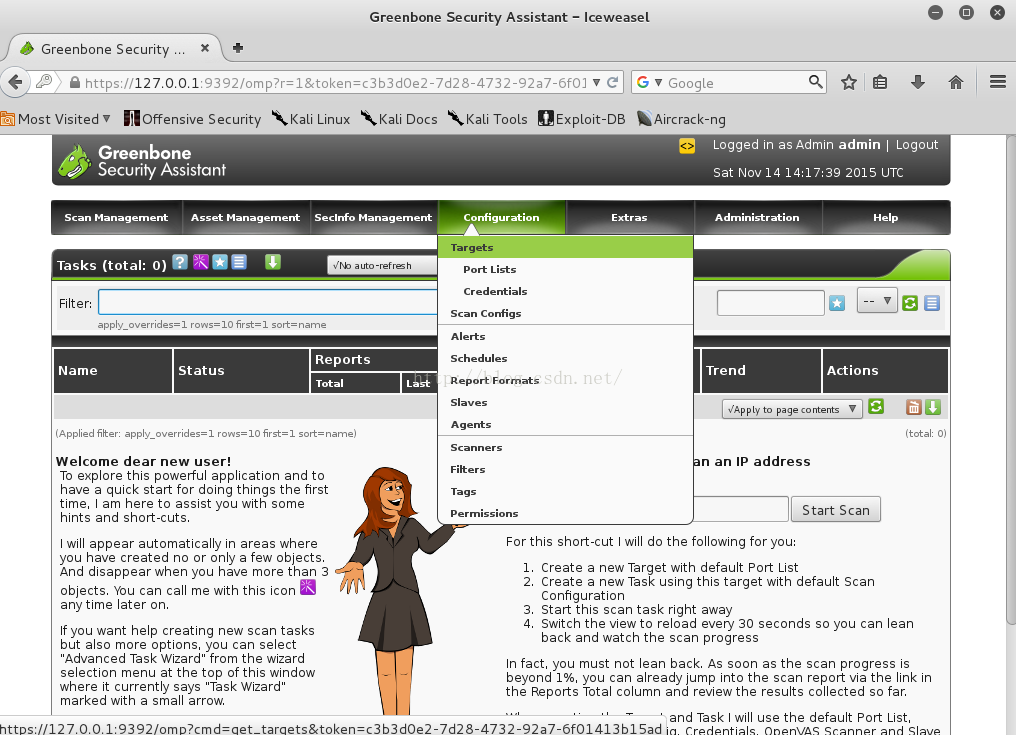
2)进行扫描
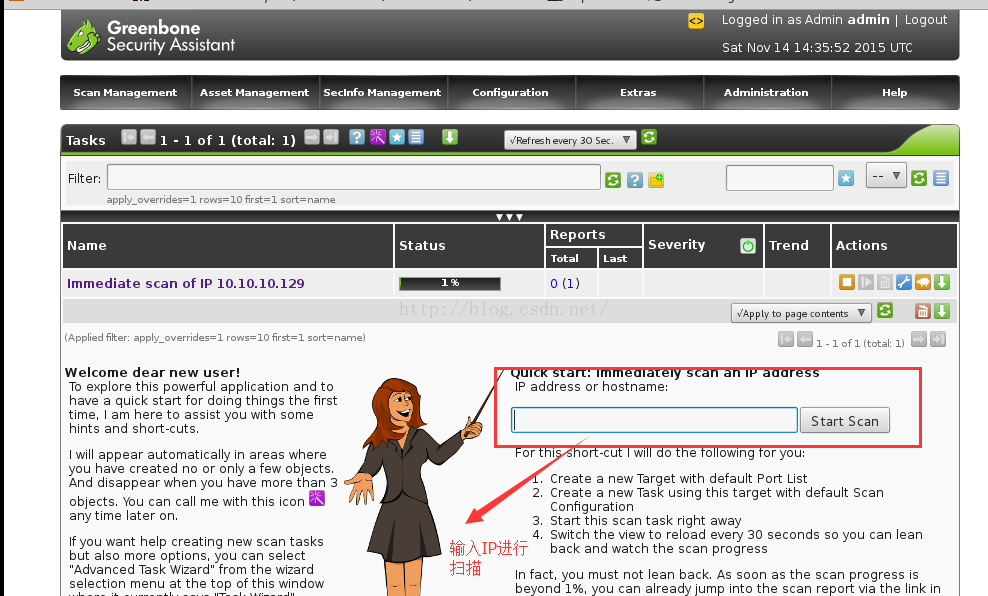
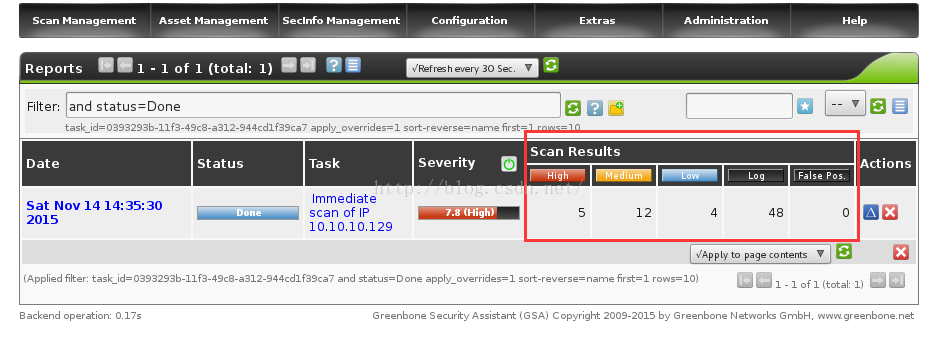
3)扫描结果查询
3、在Metasploit内部使用OpenVAS
msf > db_connect msfstrom:msfstrom@127.0.0.1/pentester --链接数据库
[*] Rebuilding the module cache in the background...
msf > load openvas --链接openvas模块
[*] Welcome to OpenVAS integration by kost and averagesecurityguy.
[*]
[*] OpenVAS integration requires a database connection. Once the
[*] database is ready, connect to the OpenVAS server using openvas_connect.
[*] For additional commands use openvas_help.
[*]
[*] Successfully loaded plugin: OpenVAS
msf > openvas_help ---查看帮助信息
[*] openvas_help Display this help
[*] openvas_debug Enable/Disable debugging
[*] openvas_version Display the version of the OpenVAS server
[*]
[*] CONNECTION
[*] ==========
[*] openvas_connect Connects to OpenVAS
[*] openvas_disconnect Disconnects from OpenVAS
[*]
[*] TARGETS
[*] =======
[*] openvas_target_create Create target
[*] openvas_target_delete Deletes target specified by ID
[*] openvas_target_list Lists targets
[*]
[*] TASKS
[*] =====
[*] openvas_task_create Create task
[*] openvas_task_delete Delete a task and all associated reports
[*] openvas_task_list Lists tasks
[*] openvas_task_start Starts task specified by ID
[*] openvas_task_stop Stops task specified by ID
[*] openvas_task_pause Pauses task specified by ID
[*] openvas_task_resume Resumes task specified by ID
[*] openvas_task_resume_or_start Resumes or starts task specified by ID
[*]
[*] CONFIGS
[*] =======
[*] openvas_config_list Lists scan configurations
[*]
[*] FORMATS
[*] =======
[*] openvas_format_list Lists available report formats
[*]
[*] REPORTS
[*] =======
[*] openvas_report_list Lists available reports
[*] openvas_report_delete Delete a report specified by ID
[*] openvas_report_import Imports an OpenVAS report specified by ID
[*] openvas_report_download Downloads an OpenVAS report specified by ID
1) 管理openvas引擎
msf > load openvas
[*] Welcome to OpenVAS integration by kost and averagesecurityguy.
[*]
[*] OpenVAS integration requires a database connection. Once the
[*] database is ready, connect to the OpenVAS server using openvas_connect.
[*] For additional commands use openvas_help.
[*]
[*] Successfully loaded plugin: OpenVAS
msf > openvas_connect admin admin 127.0.0.1 9390 ok
[*] Connecting to OpenVAS instance at 127.0.0.1:9390 with username admin...
[+] OpenVAS connection successful
2)创建一个扫描目标
msf > openvas_target_create ubuntu 10.10.10.129 OWASP
[*] OK, resource created: 522f61b5-d546-4671-bb41-f29fcd40090f
[+] OpenVAS list of targets
ID Name Hosts Max Hosts In Use Comment
-- ---- ----- --------- ------ -------
0 Localhost localhost 1 0
1 Target for immediate scan of IP 10.10.10.129 10.10.10.129 1 1
2 test 10.10.10.129 1 0
3 ubuntu 10.10.10.129 1 0 OWASP
3)创建扫描任务
3.1 扫描类型
msf > openvas_config_list
[+] OpenVAS list of configs
ID Name
-- ----
0 Discovery
1 empty
2 Full and fast
3 Full and fast ultimate
4 Full and very deep
5 Full and very deep ultimate
6 Host Discovery
7 System Discovery
3.2 扫描策略
msf > openvas_task_create ubuntu-scan "Scan of OWASP" 0 2
[*] OK, resource created: 31a60258-94de-41a3-9007-8dc2221d66c9
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Immediate scan of IP 10.10.10.129 Done -1
1 ubuntu-scan Scan of OWASP New -1
3.3启动扫描任务
msf > openvas_task_start 1
[*] OK, request submitted
3.4 查看扫描进度
msf > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Immediate scan of IP 10.10.10.129 Done -1
1 ubuntu-scan Scan of OWASP Running 4
3.5 下载扫描报告
msf > openvas_report_list
[+] OpenVAS list of reports
ID Task Name Start Time Stop Time
-- --------- ---------- ---------
0 Immediate scan of IP 10.10.10.129 2015-11-14T14:35:33Z 2015-11-14T14:53:19Z
1 ubuntu-scan 2015-11-14T15:46:51Z
msf > openvas_format_list
[+] OpenVAS list of report formats
ID Name Extension Summary
-- ---- --------- -------
0 Anonymous XML xml Anonymous version of the raw XML report
1 ARF xml Asset Reporting Format v1.0.0.
2 CPE csv Common Product Enumeration CSV table.
3 CSV Hosts csv CSV host summary.
4 CSV Results csv CSV result list.
5 HTML html Single page HTML report.
6 ITG csv German "IT-Grundschutz-Kataloge" report.
7 LaTeX tex LaTeX source file.
8 NBE nbe Legacy OpenVAS report.
9 PDF pdf Portable Document Format report.
10 Topology SVG svg Network topology SVG image.
11 TXT txt Plain text report.
12 Verinice ISM vna Greenbone Verinice ISM Report, v1.1.10.
13 XML xml Raw XML report.
msf > openvas_report_download 2 1 /root ubuntu.html
4、查找特定服务器漏洞
msf > nmap -P0 --script=smb-check-vulns 10.10.10.130
[*] exec: nmap -P0 --script=smb-check-vulns 10.10.10.130
5、在Metasploit 中使用PostgreSQL
msf > db_status
[*] postgresql connected to pentester
5.1通过Nmap扫描结果输出一个文件
msf > nmap -Pn -sV -oX dmz 10.10.10.0/24
[*] exec: nmap -Pn -sV -oX dmz 10.10.10.0/24
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-14 11:01 EST
Stats: 0:01:42 elapsed; 250 hosts completed (5 up), 5 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 68.68% done; ETC: 11:03 (0:00:46 remaining)
Nmap scan report for 10.10.10.1
Host is up (0.00036s latency).
Not shown: 990 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows 98 netbios-ssn
443/tcp open ssl/http VMware VirtualCenter Web service
445/tcp open microsoft-ds (primary domain: WORKGROUP)
902/tcp open ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
912/tcp open vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
2869/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open upnp Portable SDK for UPnP devices 1.6.17 (Windows 6.2.9200 2; UPnP 1.0)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port445-TCP:V=6.49BETA4%I=7%D=11/14%Time=56475BB7%P=x86_64-pc-linux-gnu
SF:%r(SMBProgNeg,77,"\0\0\0s\xffSMBr\0\0\0\0\x88\x01@\0\0\0\0\0\0\0\0\0\0\
SF:0\0\0\0@\x06\0\0\x01\0\x11\x07\0\x032\0\x01\0\x04\x11\0\0\0\0\x01\0\0\0
SF:\0\0\xfc\xe3\x01\0,\x16\xa8,\xb3\x1e\xd1\x01\x20\xfe\x08\.\0\xc9n#\x9a\
SF:n\x19\xf6\x83W\0O\0R\0K\0G\0R\0O\0U\0P\0\0\0S\0T\0R\0O\0M\0-\0P\0C\0\0\
SF:0");
MAC Address: 00:50:56:C0:00:08 (VMware)
Service Info: Host: STROM-PC; OSs: Windows, Windows 98; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_98
Nmap scan report for 10.10.10.2
Host is up (0.00017s latency).
All 1000 scanned ports on 10.10.10.2 are closed
MAC Address: 00:50:56:E6:0A:6D (VMware)
Nmap scan report for 10.10.10.129
Host is up (0.00033s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.2.2
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.5 with Suhosin-Patch mod_python/3.3.1 Python/2.6.5 mod_perl/2.0.4 Perl/v5.10.1)
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
5001/tcp open java-rmi Java RMI
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=6.49BETA4%I=7%D=11/14%Time=56475BAF%P=x86_64-pc-linux-gn
SF:u%r(NULL,4,"\xac\xed\0\x05");
MAC Address: 00:0C:29:A1:89:51 (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.10.10.130
Host is up (0.0043s latency).
Not shown: 984 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
23/tcp open telnet Microsoft Windows XP telnetd
80/tcp open http Microsoft IIS httpd 6.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows 98 netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 2003 or 2008 microsoft-ds
777/tcp open multiling-http?
1025/tcp open msrpc Microsoft Windows RPC
1026/tcp open msrpc Microsoft Windows RPC
1027/tcp open msrpc Microsoft Windows RPC
1031/tcp open msrpc Microsoft Windows RPC
1521/tcp open oracle-tns Oracle TNS Listener 10.2.0.1.0 (for 32-bit Windows)
6002/tcp open http SafeNet Sentinel Protection Server httpd 7.3
7001/tcp open afs3-callback?
7002/tcp open http SafeNet Sentinel Keys License Monitor httpd 1.0 (Java Console)
8099/tcp open http Microsoft IIS httpd 6.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port777-TCP:V=6.49BETA4%I=7%D=11/14%Time=56475BEC%P=x86_64-pc-linux-gnu
SF:%r(Kerberos,5,"\x01\0\t\xe0\x06")%r(SMBProgNeg,5,"\x01\0\t\xe0\x06")%r(
SF:TerminalServer,A,"\x01\0\t\xe0\x06\x01\0\t\xe0\x06")%r(WMSRequest,5,"\x
SF:01\0\t\xe0\x06");
MAC Address: 00:0C:29:09:18:C6 (VMware)
Service Info: OSs: Windows, Windows XP, Windows 98; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp, cpe:/o:microsoft:windows_98, cpe:/o:microsoft:windows_server_2003
Nmap scan report for 10.10.10.254
Host is up (0.000056s latency).
All 1000 scanned ports on 10.10.10.254 are filtered
MAC Address: 00:0C:29:79:92:14 (VMware)
Nmap scan report for 10.10.10.128
Host is up (0.0000020s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 256 IP addresses (6 hosts up) scanned in 368.27 seconds
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-14 10:56 EST
Nmap scan report for 10.10.10.130
Host is up (0.00015s latency).
Not shown: 984 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
777/tcp open multiling-http
1025/tcp open NFS-or-IIS
1026/tcp open LSA-or-nterm
1027/tcp open IIS
1031/tcp open iad2
1521/tcp open oracle
6002/tcp open X11:2
7001/tcp open afs3-callback
7002/tcp open afs3-prserver
8099/tcp open unknown
MAC Address: 00:0C:29:09:18:C6 (VMware)
Host script results:
| smb-check-vulns:
| MS08-067: CHECK DISABLED (add '--script-args=unsafe=1' to run)
| Conficker: Likely CLEAN
| regsvc DoS: CHECK DISABLED (add '--script-args=unsafe=1' to run)
| SMBv2 DoS (CVE-2009-3103): CHECK DISABLED (add '--script-args=unsafe=1' to run)
| MS06-025: CHECK DISABLED (add '--script-args=unsafe=1' to run)
|_ MS07-029: CHECK DISABLED (add '--script-args=unsafe=1' to run)
Nmap done: 1 IP address (1 host up) scanned in 2.50 seconds
5.2 输出的文件进行导入数据库
msf > db_import /root/dmz
[*] Importing 'Nmap XML' data
[*] Import: Parsing with 'Nokogiri v1.6.6.2'
[*] Importing host 10.10.10.1
[*] Importing host 10.10.10.129
[*] Importing host 10.10.10.130
[*] Importing host 10.10.10.128
[*] Successfully imported /root/dmz
5.3 导入数据库的信息查看
msf > hosts
Hosts
=====
address mac name os_name os_flavor os_sp purpose info comments
------- --- ---- ------- --------- ----- ------- ---- --------
10.10.10.1 00:50:56:c0:00:08 Unknown device
10.10.10.2 00:50:56:e6:0a:6d
10.10.10.128 00:0c:29:a0:70:4e Unknown device
10.10.10.129 00:0c:29:a1:89:51 Unknown device
10.10.10.130 00:0c:29:09:18:c6 Unknown device
10.10.10.254 00:0c:29:79:92:14
121.120.80.215 Unknown device
192.168.144.1 00:50:56:C0:00:08 Unknown device
192.168.144.130 Unknown device
192.168.144.135 00:0c:29:84:5d:10 Linux 3.X server
msf > search name:psnuffle
Matching Modules
================
Name Disclosure Date Rank Description
---- --------------- ---- -----------
auxiliary/sniffer/psnuffle normal pSnuffle Packet Sniffer
msf > use auxiliary/sniffer/psnuffle
msf auxiliary(psnuffle) > run
[*] Auxiliary module execution completed
msf auxiliary(psnuffle) >
[*] Loaded protocol FTP from /usr/share/metasploit-framework/data/exploits/psnuffle/ftp.rb...
[*] Loaded protocol IMAP from /usr/share/metasploit-framework/data/exploits/psnuffle/imap.rb...
[*] Loaded protocol POP3 from /usr/share/metasploit-framework/data/exploits/psnuffle/pop3.rb...
[*] Loaded protocol SMB from /usr/share/metasploit-framework/data/exploits/psnuffle/smb.rb...
[*] Loaded protocol URL from /usr/share/metasploit-framework/data/exploits/psnuffle/url.rb...
[*] Sniffing traffic.....
注意:等待嗅探成功
2、OpenVAS漏洞扫描器
1)配置OpenVAS
2)为OpenVAS创建用户并生成密码
root@kali:/var/log# openvasmd --create-user admin --role Admin
User created with password '4e8624ad-dd97-47e9-b8ee-95814645d6b8'.
注意:如原先有用户可以用以下命令进行删除
root@kali:/var/log# openvasmd --delete-user admin --role Admin
User deleted.

1)配置扫描策略

2)进行扫描

3)扫描结果查询
3、在Metasploit内部使用OpenVAS
msf > db_connect msfstrom:msfstrom@127.0.0.1/pentester --链接数据库
[*] Rebuilding the module cache in the background...
msf > load openvas --链接openvas模块
[*] Welcome to OpenVAS integration by kost and averagesecurityguy.
[*]
[*] OpenVAS integration requires a database connection. Once the
[*] database is ready, connect to the OpenVAS server using openvas_connect.
[*] For additional commands use openvas_help.
[*]
[*] Successfully loaded plugin: OpenVAS
msf > openvas_help ---查看帮助信息
[*] openvas_help Display this help
[*] openvas_debug Enable/Disable debugging
[*] openvas_version Display the version of the OpenVAS server
[*]
[*] CONNECTION
[*] ==========
[*] openvas_connect Connects to OpenVAS
[*] openvas_disconnect Disconnects from OpenVAS
[*]
[*] TARGETS
[*] =======
[*] openvas_target_create Create target
[*] openvas_target_delete Deletes target specified by ID
[*] openvas_target_list Lists targets
[*]
[*] TASKS
[*] =====
[*] openvas_task_create Create task
[*] openvas_task_delete Delete a task and all associated reports
[*] openvas_task_list Lists tasks
[*] openvas_task_start Starts task specified by ID
[*] openvas_task_stop Stops task specified by ID
[*] openvas_task_pause Pauses task specified by ID
[*] openvas_task_resume Resumes task specified by ID
[*] openvas_task_resume_or_start Resumes or starts task specified by ID
[*]
[*] CONFIGS
[*] =======
[*] openvas_config_list Lists scan configurations
[*]
[*] FORMATS
[*] =======
[*] openvas_format_list Lists available report formats
[*]
[*] REPORTS
[*] =======
[*] openvas_report_list Lists available reports
[*] openvas_report_delete Delete a report specified by ID
[*] openvas_report_import Imports an OpenVAS report specified by ID
[*] openvas_report_download Downloads an OpenVAS report specified by ID
1) 管理openvas引擎
msf > load openvas
[*] Welcome to OpenVAS integration by kost and averagesecurityguy.
[*]
[*] OpenVAS integration requires a database connection. Once the
[*] database is ready, connect to the OpenVAS server using openvas_connect.
[*] For additional commands use openvas_help.
[*]
[*] Successfully loaded plugin: OpenVAS
msf > openvas_connect admin admin 127.0.0.1 9390 ok
[*] Connecting to OpenVAS instance at 127.0.0.1:9390 with username admin...
[+] OpenVAS connection successful
2)创建一个扫描目标
msf > openvas_target_create ubuntu 10.10.10.129 OWASP
[*] OK, resource created: 522f61b5-d546-4671-bb41-f29fcd40090f
[+] OpenVAS list of targets
ID Name Hosts Max Hosts In Use Comment
-- ---- ----- --------- ------ -------
0 Localhost localhost 1 0
1 Target for immediate scan of IP 10.10.10.129 10.10.10.129 1 1
2 test 10.10.10.129 1 0
3 ubuntu 10.10.10.129 1 0 OWASP
3)创建扫描任务
3.1 扫描类型
msf > openvas_config_list
[+] OpenVAS list of configs
ID Name
-- ----
0 Discovery
1 empty
2 Full and fast
3 Full and fast ultimate
4 Full and very deep
5 Full and very deep ultimate
6 Host Discovery
7 System Discovery
3.2 扫描策略
msf > openvas_task_create ubuntu-scan "Scan of OWASP" 0 2
[*] OK, resource created: 31a60258-94de-41a3-9007-8dc2221d66c9
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Immediate scan of IP 10.10.10.129 Done -1
1 ubuntu-scan Scan of OWASP New -1
3.3启动扫描任务
msf > openvas_task_start 1
[*] OK, request submitted
3.4 查看扫描进度
msf > openvas_task_list
[+] OpenVAS list of tasks
ID Name Comment Status Progress
-- ---- ------- ------ --------
0 Immediate scan of IP 10.10.10.129 Done -1
1 ubuntu-scan Scan of OWASP Running 4
3.5 下载扫描报告
msf > openvas_report_list
[+] OpenVAS list of reports
ID Task Name Start Time Stop Time
-- --------- ---------- ---------
0 Immediate scan of IP 10.10.10.129 2015-11-14T14:35:33Z 2015-11-14T14:53:19Z
1 ubuntu-scan 2015-11-14T15:46:51Z
msf > openvas_format_list
[+] OpenVAS list of report formats
ID Name Extension Summary
-- ---- --------- -------
0 Anonymous XML xml Anonymous version of the raw XML report
1 ARF xml Asset Reporting Format v1.0.0.
2 CPE csv Common Product Enumeration CSV table.
3 CSV Hosts csv CSV host summary.
4 CSV Results csv CSV result list.
5 HTML html Single page HTML report.
6 ITG csv German "IT-Grundschutz-Kataloge" report.
7 LaTeX tex LaTeX source file.
8 NBE nbe Legacy OpenVAS report.
9 PDF pdf Portable Document Format report.
10 Topology SVG svg Network topology SVG image.
11 TXT txt Plain text report.
12 Verinice ISM vna Greenbone Verinice ISM Report, v1.1.10.
13 XML xml Raw XML report.
msf > openvas_report_download 2 1 /root ubuntu.html
4、查找特定服务器漏洞
msf > nmap -P0 --script=smb-check-vulns 10.10.10.130
[*] exec: nmap -P0 --script=smb-check-vulns 10.10.10.130
5、在Metasploit 中使用PostgreSQL
msf > db_status
[*] postgresql connected to pentester
5.1通过Nmap扫描结果输出一个文件
msf > nmap -Pn -sV -oX dmz 10.10.10.0/24
[*] exec: nmap -Pn -sV -oX dmz 10.10.10.0/24
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-14 11:01 EST
Stats: 0:01:42 elapsed; 250 hosts completed (5 up), 5 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 68.68% done; ETC: 11:03 (0:00:46 remaining)
Nmap scan report for 10.10.10.1
Host is up (0.00036s latency).
Not shown: 990 filtered ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows 98 netbios-ssn
443/tcp open ssl/http VMware VirtualCenter Web service
445/tcp open microsoft-ds (primary domain: WORKGROUP)
902/tcp open ssl/vmware-auth VMware Authentication Daemon 1.10 (Uses VNC, SOAP)
912/tcp open vmware-auth VMware Authentication Daemon 1.0 (Uses VNC, SOAP)
2869/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
5357/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open upnp Portable SDK for UPnP devices 1.6.17 (Windows 6.2.9200 2; UPnP 1.0)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port445-TCP:V=6.49BETA4%I=7%D=11/14%Time=56475BB7%P=x86_64-pc-linux-gnu
SF:%r(SMBProgNeg,77,"\0\0\0s\xffSMBr\0\0\0\0\x88\x01@\0\0\0\0\0\0\0\0\0\0\
SF:0\0\0\0@\x06\0\0\x01\0\x11\x07\0\x032\0\x01\0\x04\x11\0\0\0\0\x01\0\0\0
SF:\0\0\xfc\xe3\x01\0,\x16\xa8,\xb3\x1e\xd1\x01\x20\xfe\x08\.\0\xc9n#\x9a\
SF:n\x19\xf6\x83W\0O\0R\0K\0G\0R\0O\0U\0P\0\0\0S\0T\0R\0O\0M\0-\0P\0C\0\0\
SF:0");
MAC Address: 00:50:56:C0:00:08 (VMware)
Service Info: Host: STROM-PC; OSs: Windows, Windows 98; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_98
Nmap scan report for 10.10.10.2
Host is up (0.00017s latency).
All 1000 scanned ports on 10.10.10.2 are closed
MAC Address: 00:50:56:E6:0A:6D (VMware)
Nmap scan report for 10.10.10.129
Host is up (0.00033s latency).
Not shown: 992 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.2.2
22/tcp open ssh OpenSSH 5.3p1 Debian 3ubuntu4 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.2.14 ((Ubuntu) mod_mono/2.4.3 PHP/5.3.2-1ubuntu4.5 with Suhosin-Patch mod_python/3.3.1 Python/2.6.5 mod_perl/2.0.4 Perl/v5.10.1)
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
143/tcp open imap Courier Imapd (released 2008)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
5001/tcp open java-rmi Java RMI
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port5001-TCP:V=6.49BETA4%I=7%D=11/14%Time=56475BAF%P=x86_64-pc-linux-gn
SF:u%r(NULL,4,"\xac\xed\0\x05");
MAC Address: 00:0C:29:A1:89:51 (VMware)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Nmap scan report for 10.10.10.130
Host is up (0.0043s latency).
Not shown: 984 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
23/tcp open telnet Microsoft Windows XP telnetd
80/tcp open http Microsoft IIS httpd 6.0
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows 98 netbios-ssn
445/tcp open microsoft-ds Microsoft Windows 2003 or 2008 microsoft-ds
777/tcp open multiling-http?
1025/tcp open msrpc Microsoft Windows RPC
1026/tcp open msrpc Microsoft Windows RPC
1027/tcp open msrpc Microsoft Windows RPC
1031/tcp open msrpc Microsoft Windows RPC
1521/tcp open oracle-tns Oracle TNS Listener 10.2.0.1.0 (for 32-bit Windows)
6002/tcp open http SafeNet Sentinel Protection Server httpd 7.3
7001/tcp open afs3-callback?
7002/tcp open http SafeNet Sentinel Keys License Monitor httpd 1.0 (Java Console)
8099/tcp open http Microsoft IIS httpd 6.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port777-TCP:V=6.49BETA4%I=7%D=11/14%Time=56475BEC%P=x86_64-pc-linux-gnu
SF:%r(Kerberos,5,"\x01\0\t\xe0\x06")%r(SMBProgNeg,5,"\x01\0\t\xe0\x06")%r(
SF:TerminalServer,A,"\x01\0\t\xe0\x06\x01\0\t\xe0\x06")%r(WMSRequest,5,"\x
SF:01\0\t\xe0\x06");
MAC Address: 00:0C:29:09:18:C6 (VMware)
Service Info: OSs: Windows, Windows XP, Windows 98; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_xp, cpe:/o:microsoft:windows_98, cpe:/o:microsoft:windows_server_2003
Nmap scan report for 10.10.10.254
Host is up (0.000056s latency).
All 1000 scanned ports on 10.10.10.254 are filtered
MAC Address: 00:0C:29:79:92:14 (VMware)
Nmap scan report for 10.10.10.128
Host is up (0.0000020s latency).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 256 IP addresses (6 hosts up) scanned in 368.27 seconds
Starting Nmap 6.49BETA4 ( https://nmap.org ) at 2015-11-14 10:56 EST
Nmap scan report for 10.10.10.130
Host is up (0.00015s latency).
Not shown: 984 closed ports
PORT STATE SERVICE
21/tcp open ftp
23/tcp open telnet
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
777/tcp open multiling-http
1025/tcp open NFS-or-IIS
1026/tcp open LSA-or-nterm
1027/tcp open IIS
1031/tcp open iad2
1521/tcp open oracle
6002/tcp open X11:2
7001/tcp open afs3-callback
7002/tcp open afs3-prserver
8099/tcp open unknown
MAC Address: 00:0C:29:09:18:C6 (VMware)
Host script results:
| smb-check-vulns:
| MS08-067: CHECK DISABLED (add '--script-args=unsafe=1' to run)
| Conficker: Likely CLEAN
| regsvc DoS: CHECK DISABLED (add '--script-args=unsafe=1' to run)
| SMBv2 DoS (CVE-2009-3103): CHECK DISABLED (add '--script-args=unsafe=1' to run)
| MS06-025: CHECK DISABLED (add '--script-args=unsafe=1' to run)
|_ MS07-029: CHECK DISABLED (add '--script-args=unsafe=1' to run)
Nmap done: 1 IP address (1 host up) scanned in 2.50 seconds
5.2 输出的文件进行导入数据库
msf > db_import /root/dmz
[*] Importing 'Nmap XML' data
[*] Import: Parsing with 'Nokogiri v1.6.6.2'
[*] Importing host 10.10.10.1
[*] Importing host 10.10.10.129
[*] Importing host 10.10.10.130
[*] Importing host 10.10.10.128
[*] Successfully imported /root/dmz
5.3 导入数据库的信息查看
msf > hosts
Hosts
=====
address mac name os_name os_flavor os_sp purpose info comments
------- --- ---- ------- --------- ----- ------- ---- --------
10.10.10.1 00:50:56:c0:00:08 Unknown device
10.10.10.2 00:50:56:e6:0a:6d
10.10.10.128 00:0c:29:a0:70:4e Unknown device
10.10.10.129 00:0c:29:a1:89:51 Unknown device
10.10.10.130 00:0c:29:09:18:c6 Unknown device
10.10.10.254 00:0c:29:79:92:14
121.120.80.215 Unknown device
192.168.144.1 00:50:56:C0:00:08 Unknown device
192.168.144.130 Unknown device
192.168.144.135 00:0c:29:84:5d:10 Linux 3.X server
























 1422
1422

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?










