Lab Overview
In this lab, you’ll explore how to defeat the protection mechanisms introduced to counter buffer overflows. The first type of countermeasure is nonexecutable stack, which will mark the stack memory segment, along with other segments, nonexecutable. Thus, even the shellcode jumps back to the stack, it has no chance to execute. To defeat this protection mechanism, you will study and use a specific technique called returntolibc, a special and easy form of returnoriented programming. By using returntolibc, shellcode can jump to any library code (or any executable code).
The second type of countermeasure is memory address layout randomization (ASLR). The key idea of ASLR is to set random addresses for specific memory segments of a given process. Thus, it will be very difficult for an adversary to know the exact address of a buffer. To defeat this protection mechanism, the adversay can guess the starting address of a buffer and attack the server bruteforcely. This is rather realistic, because the range of the stack is relatively small.
The third type of countermeasure is a canary. In its simplest form, a canary is an integer on the stack (after the buffer), by checking whether or not a canary is altered, one can check whether or not the buffer is over flowed, just before the function returns. To defeat this, an adversary can just guess the value of the canary. At a first glance, this will be very hard, if not impossible, because the value space is dramatically huge: 232. However, you will understand that under some circumstance, say a web server like Touchstone, it will be very practical. An adversary only need to guess just 1024 times to succeed.
This lab consists of three parts:
Part A: you will defeat the Nonexecutable stack protection, by using returntolic attack.
Part B: you will defeat the Touchstone web server in a realistic environment: the ASLR is enabled.
Exercise 1
不能成功,提示程序中断。
因为开启non-executable stack后,栈是不可执行的。当返回地址为栈地址时,程序将中断。
Exercise 2
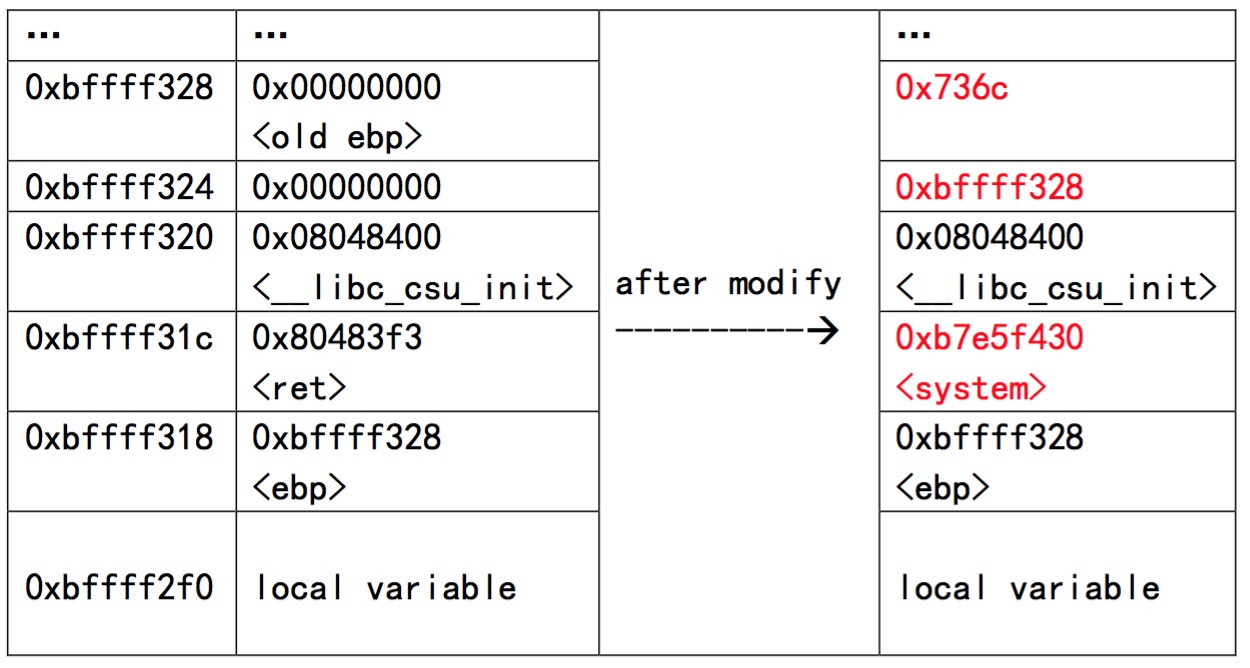
使用gdb调试在fun函数处设断点并运行,打印出栈内情况。然后根据实验步骤修改栈,结果如下图所示。
从图中可看到,我们把fun的返回地址修改为system函数的地址,把old ebp修改为字符数组”ls”,并把old ebp下一个地址修改为字符数组”ls”的地址。这里,我们就制造了一个system(“ls”)函数的调用:
1. 参数入栈:*0xbffff324=0xbffff328 2. 返回地址入栈:*0xbffff320=0x08048400当fun函数执行完后返回时,会调用system函数,system函数从栈中获取参数地址。
而当system执行完后返回时,esp指向0xbffff320调用__libc_csu_init,而它上方两个地址的内容已发生改变,因此不能正常进行调用,从而导致Segmentation fault。
为使进程能够正常退出,只需进行如下操作:(gdb) set *0xbffff320=0x80483f3使system函数执行完后能继续执行main函数从而正常退出。








 最低0.47元/天 解锁文章
最低0.47元/天 解锁文章














 862
862











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








