先决条件
已经部署好redis服务端 tls环境。如未部署好,可参考:Redis 6.0 Docker容器使用TLS加密
已知redis服务端 tls环境使用的证书:

其中:
ca.crt : CA根证书,用于验证证书是否合法
ca.key: CA根证书私钥
redis.crt: ca.crt根证书签发的证书
redis.key:ca.crt根证书签发的证书私钥
证书处理
生成证书p12文件,.p12证书可能既包含公钥也包含私钥,方便统一管理。我们这里redis服务端和redis客户端使用的是同一份证书(redis.crt)。
openssl pkcs12 -export -in redis.crt -certfile ca.crt -inkey redis.key -out certificate_for_red.p12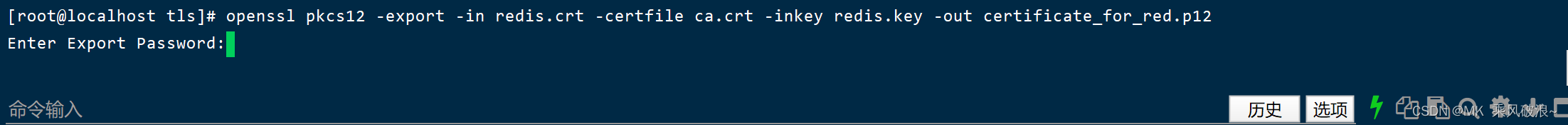
记住输入的密码,后面解析证书时要用到。
注意:因为redis tls默认开启双向认证,所以客户端连接也需要提供证书,且是同一根证书(ca.crt)签发。
将certificate_for_red.p12拷贝到src/main/resources 目录下
Spring-Data-Redis TLS连接
基于Spring-Data-Redis2.5.5
@Configuration
public class SSLJedisConnectionFactory extends JedisConnectionFactory {
@Value("${spring.redis.host}")
private String host;
@Value("${spring.redis.port}")
private String port;
@Value("${spring.redis.password}")
private String password;
@Value("${spring.redis.ssl}")
private Boolean sslEnable;
// 为创建.p12文件时输入的密码
@Value("${spring.redis.keyStorePassword}")
private String keyStorePassword;
/**
* 重写createRedisPool方法,让其使用SslSocketFactory创建连接池
*
* @return
*/
protected Pool<Jedis> createRedisPool() {
SSLSocketFactory sslSocketFactory=null;
if (sslEnable) {
InputStream fileStream = getClass().getClassLoader().getResourceAsStream("certificate_for_red.p12");
Optional<SSLSocketFactory> sslSocketFactoryOptional = SSLUtil.getSslSocketFactory(fileStream, keyStorePassword);
sslSocketFactory = sslSocketFactoryOptional
.orElseThrow(() -> new RuntimeException("Can't create SSLSocketFactory"));
}
GenericObjectPoolConfig genericObjectPoolConfig = new GenericObjectPoolConfig();
//with ssl config jedis pool
JedisPool pool = new JedisPool(
genericObjectPoolConfig,
host,
Integer.parseInt(port),
2000,
password,
sslEnable,
sslSocketFactory,
new SSLParameters(),
null);
return pool;
}
/**
* create SslSocketFactory
* @param fileStream
* @param password
* @return
*/
private static Optional<SSLSocketFactory> getSslSocketFactory(InputStream fileStream, String password) {
try {
KeyStore clientStore = KeyStore.getInstance("PKCS12");
clientStore.load(fileStream, password.toCharArray());
SSLContext sslContext = SSLContext.getInstance("TLS");
KeyManagerFactory factory = KeyManagerFactory.getInstance("SunX509");
factory.init(clientStore, password.toCharArray());
sslContext.init(factory.getKeyManagers(), new TrustManager[]{new MockTrustManager()}, new SecureRandom());
SSLSocketFactory sslSocketFactory = sslContext.getSocketFactory();
return Optional.of(sslSocketFactory);
} catch (UnrecoverableKeyException | CertificateException | KeyStoreException | IOException
| NoSuchAlgorithmException | KeyManagementException ex) {
return Optional.empty();
}
}
}public class MockTrustManager implements X509TrustManager {
public MockTrustManager() {
}
public void checkClientTrusted(X509Certificate[] arg0, String arg1) {
}
public void checkServerTrusted(X509Certificate[] arg0, String arg1) {
}
public X509Certificate[] getAcceptedIssuers() {
return null;
}
}Redisson 连接
在Pom.xml引入
<dependency>
<groupId>org.redisson</groupId>
<artifactId>redisson</artifactId>
<version>3.20.0</version>
</dependency>@Configuration
public class RedissonConfig {
@Value("${spring.redis.host}")
private String host;
@Value("${spring.redis.port}")
private String port;
@Value("${spring.redis.password}")
private String password;
// 为创建.p12文件时输入的密码
@Value("${spring.redis.keyStorePassword}")
private String keyStorePassword;
@Value("${spring.redis.ssl}")
private Boolean sslEnable;
@Bean
public RedissonClient getRedisson() {
Config config = new Config();
if (sslEnable) {
ClassLoader classLoader = getClass().getClassLoader();
URL keyStoreUrl = classLoader.getResource("certificate_for_red.p12");
config.useSingleServer().setSslProvider(SslProvider.OPENSSL).setSslKeystore(keyStoreUrl).
setSslKeystorePassword(keyStorePassword).
//不校验域名 Unverified domain name
setSslEnableEndpointIdentification(false).
setAddress("rediss://" + host + ":" + port).setPassword(password);
}else {
// non-SSL
config.useSingleServer().setAddress("redis://" + host + ":" + port).setPassword(password);
}
return Redisson.create(config);
}
}异常No subject alternative names present
17:05:07.187 siteServer [redisson-netty-2-4] ERROR o.r.c.handler.ErrorsLoggingHandler - Exception occured. Channel: [id: 0x85cfe859, L:0.0.0.0/0.0.0.0:49234 ! R:192.169.1.101/192.169.1.101:6379]
io.netty.handler.codec.DecoderException: javax.net.ssl.SSLHandshakeException: General OpenSslEngine problem
at io.netty.handler.codec.ByteToMessageDecoder.callDecode(ByteToMessageDecoder.java:477)
at io.netty.handler.codec.ByteToMessageDecoder.channelRead(ByteToMessageDecoder.java:276)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:379)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:365)
at io.netty.channel.AbstractChannelHandlerContext.fireChannelRead(AbstractChannelHandlerContext.java:357)
at io.netty.channel.DefaultChannelPipeline$HeadContext.channelRead(DefaultChannelPipeline.java:1410)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:379)
at io.netty.channel.AbstractChannelHandlerContext.invokeChannelRead(AbstractChannelHandlerContext.java:365)
at io.netty.channel.DefaultChannelPipeline.fireChannelRead(DefaultChannelPipeline.java:919)
at io.netty.channel.nio.AbstractNioByteChannel$NioByteUnsafe.read(AbstractNioByteChannel.java:166)
at io.netty.channel.nio.NioEventLoop.processSelectedKey(NioEventLoop.java:719)
at io.netty.channel.nio.NioEventLoop.processSelectedKeysOptimized(NioEventLoop.java:655)
at io.netty.channel.nio.NioEventLoop.processSelectedKeys(NioEventLoop.java:581)
at io.netty.channel.nio.NioEventLoop.run(NioEventLoop.java:493)
at io.netty.util.concurrent.SingleThreadEventExecutor$4.run(SingleThreadEventExecutor.java:986)
at io.netty.util.internal.ThreadExecutorMap$2.run(ThreadExecutorMap.java:74)
at io.netty.util.concurrent.FastThreadLocalRunnable.run(FastThreadLocalRunnable.java:30)
at java.lang.Thread.run(Thread.java:748)
Caused by: javax.net.ssl.SSLHandshakeException: General OpenSslEngine problem
at io.netty.handler.ssl.ReferenceCountedOpenSslEngine.handshakeException(ReferenceCountedOpenSslEngine.java:1892)
at io.netty.handler.ssl.ReferenceCountedOpenSslEngine.wrap(ReferenceCountedOpenSslEngine.java:813)
at javax.net.ssl.SSLEngine.wrap(SSLEngine.java:509)
at io.netty.handler.ssl.SslHandler.wrap(SslHandler.java:1040)
at io.netty.handler.ssl.SslHandler.wrapNonAppData(SslHandler.java:926)
at io.netty.handler.ssl.SslHandler.unwrap(SslHandler.java:1408)
at io.netty.handler.ssl.SslHandler.decodeJdkCompatible(SslHandler.java:1235)
at io.netty.handler.ssl.SslHandler.decode(SslHandler.java:1284)
at io.netty.handler.codec.ByteToMessageDecoder.decodeRemovalReentryProtection(ByteToMessageDecoder.java:507)
at io.netty.handler.codec.ByteToMessageDecoder.callDecode(ByteToMessageDecoder.java:446)
... 17 common frames omitted
Caused by: java.security.cert.CertificateException: No subject alternative names present
at sun.security.util.HostnameChecker.matchIP(HostnameChecker.java:145)
at sun.security.util.HostnameChecker.match(HostnameChecker.java:94)
at sun.security.ssl.X509TrustManagerImpl.checkIdentity(X509TrustManagerImpl.java:455)
at sun.security.ssl.X509TrustManagerImpl.checkIdentity(X509TrustManagerImpl.java:436)
at sun.security.ssl.X509TrustManagerImpl.checkTrusted(X509TrustManagerImpl.java:252)
at sun.security.ssl.X509TrustManagerImpl.checkServerTrusted(X509TrustManagerImpl.java:136)
at io.netty.handler.ssl.ReferenceCountedOpenSslClientContext$ExtendedTrustManagerVerifyCallback.verify(ReferenceCountedOpenSslClientContext.java:234)
at io.netty.handler.ssl.ReferenceCountedOpenSslContext$AbstractCertificateVerifier.verify(ReferenceCountedOpenSslContext.java:748)
at io.netty.internal.tcnative.CertificateVerifierTask.runTask(CertificateVerifierTask.java:36)
at io.netty.internal.tcnative.SSLTask.run(SSLTask.java:48)
at io.netty.internal.tcnative.SSLTask.run(SSLTask.java:42)
at io.netty.handler.ssl.ReferenceCountedOpenSslEngine$TaskDecorator.run(ReferenceCountedOpenSslEngine.java:1455)
at io.netty.handler.ssl.SslHandler.runDelegatedTasks(SslHandler.java:1548)
at io.netty.handler.ssl.SslHandler.unwrap(SslHandler.java:1394)出现这个问题是因为我们自签的证书,没有设置域名。因此不是本地访问时,校验不通过。
设置不校验域名就可以:setSslEnableEndpointIdentification(false)
config.useSingleServer().
//不校验域名 Unverified domain name
setSslEnableEndpointIdentification(false)























 5775
5775











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








