-
-
Which of the following is(are) true about providing security to database servers ? Select all that apply.
-
-
- A、Do not host a database server on the same server as your web server
- B、Do not host a database server on a server based system
- C、Do not use blank password for SA account
- D、Employ a centralized administration model
-
-
A table CANNOT have one or more of the following index configurations.
-
-
- A、No indexes
- B、A clustered index
- C、clustered index and many non-clustered indexes
- D、Many clustered index
-
-
Which of the following can be referred to as attack method(s)? Select all that apply.
-
-
- A、Vulnerability scan
- B、SQL Injection
- C、Drive-by downloading
- D、Brute force
-
-
To speed up data access , we build cache system. In one system , The L1 cache access time is 5 ns , the L2 cache access time is 50 ns and the memory access time is 400 ns. The L1 cache miss rate is 50% , the L2 cache miss rate is 10%. The average data access time of this system is:
-
-
- A、5
- B、30
- C、45
- D、50
- E、55
-
-
In which case(s) would you use an outer join?
-
-
- A、The table being joined have NOT NULL columns.
- B、The table being joined have only matched data.
- C、The columns being joined have NULL values.
- D、The table being joined have only unmatched data.
- E、The table being joined have both matched and unmatched data.
-
-
When a dll is loaded into memory, which part(s) can be shared between processes?
-
-
- A、code segment
- B、static variable
- C、global variable
- D、external difinitions and references for linking
- E、BSS segment
-
-
-
In the image below , if the function is designed to multiply two positive numbers which line number in the image contains the biggest functional bug(assume no overflow)?
-
-
- A、Line 1
- B、Line 2
- C、Line 3
- D、Line 4
- E、Line 5
-
-
Which statement(s) is(are) correct about thread and process?Select all that apply.
-
-
- A、Threads share the same address space of the parent process;Processes share the same address space of the parent process.
- B、Changes to the main thread(cancellation,priority change,etc.) may affect the behavior of the other threads of the process; Changes to the parent process does not affect child processes.
- C、Multiple threads mar cause deadlock,while multiple processes won't cause deadlock.
- D、Threads can directly communicate with other threads of its process; Processes must use inter-process communication to communicate with sibling processes.
- E、None of the above.
-
-
Which regular expression(s) matches the sentence "www.microsoft.com" ?
-
-
- A、^\w+\.\w+\.\w+$
- B、[w]{0,3}.[a-z]*.[a-z]+
- C、.[c-w.]{3,10}[.][c-w.][.][a]|.+
- D、[w][w][w][microsoft]+[com]+
- E、\w*
-
-
Which of the following method(s) could be used to optimize the speed of a program ?
-
-
- A、Improve memory access pattern to decrease cache misses.
- B、Use special instructions(e.g. vector instructions) to replace compiler generated assembly code.
- C、Change an algorithm from recursive implementation to iterative implementation.
- D、Loop unwinding.
-
-
Which is(are) valid function pointer declaration(s) below ? Select all that apply.
-
-
- A、void* f(int);
- B、int (*f)();
- C、void (*f(int , void(*)(int)))(int);
- D、void (*(*f)(int))();
-
-
Which of the following method(s) CANNOT be used for Text-encryption:
-
-
- A、MD5
- B、RSA
- C、RC4
- D、DES
-
-
The best time complexity of quick sort algorithm is:
-
-
- A、O(lgn)
- B、O(n)
- C、O(nlgn)
- D、O(n*n)
-
-
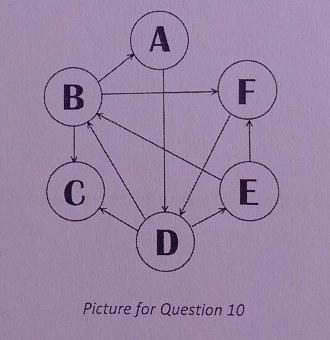
As shown in the graph , start from node B , traverse the nodes on a Depth-First Search(DFS) algorithm , which is(are) the possible traversa sequence(s)? Select all that apply.
-
-
- A、BADECF
- B、BADEFC
- C、BCAFDE
- D、BCFDEA
- E、BFDECA
-
-
Let's assume one type of cancer may be mis-diagnosed in the examination. 5 out of 100 people with this cancer will be diagnosed as not having it , and 1 out of 100 people without this cancer will be diagnosed as having it. We know the chance of getting this cancer is around 0.1%. One person was examined and diagnosed of having this cancer, which of the following value if the closest to the chance of is really having it?
-
-
- A、90%
- B、50%
- C、30%
- D、10%
-
-
Asume you have an object to describe customer data:
{
ID(7 digit numeric)
Family Name(string)
Account Balance(currency)
}
If you have 500,000 Chinese customers records represented by instances of this object type , what set of data structures is best to get fast retrieval of customers (1) get IDs from Name and (2) get Name from ID?
-
-
- A、(1) Tree with Hash(100 bucket) at leaves(2) Tree with linked list at leaves.
- B、(1) Tree with linked list at leaves(2) Array.
- C、(1) Tree with linked list at leaves(2) Hash(10,000 buckets)
- D、(1) Sort linked list(2) Array.
-
-
How many times is f() called when calculating f(10)?
int f(int x)
{
if(x <= 2)
return 1;
return f(x – 2) + f(x – 4) +1;
}
-
-
- A、14
- B、18
- C、20
- D、24
- E、None of the above.
-
-
Which of the follwing sequence(s) could not be a postorder tree walk result of a binary search tree?
-
-
- A、1,2,3,4,5
- B、3,5,1,4,2
- C、1,2,5,4,3
- D、5,4,3,2,1
-
-
Initialize integer i as 0, what's the value of i after the following operation?
i += i > 0 ? i++ : i –;
-
-
- A、-2
- B、-1
- C、0
- D、1
- E、2
-
-
Which statement(s) below regarding TCP(Transmission Control Protocol) is(are) correct? Select all that apply.
-
-
- A、TCP provides a way for applications to send encapsulated IP datagrams and send them without having to establish a connection.
- B、TCP supports multicasting.
- C、Port numbers below 1024 are called well-known ports and are reserved for standard services. For example,port 21 is reserved for FTP protocol, and port 25 is for SMTP protocol.
- D、TCP handles package loss reliably.
- E、None of the above.
-






















 3万+
3万+

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








