web服务器和db服务器
I’ve recently installed the Apereo CAS server for a project based on the spring boot. I didn’t find any good tutorial which shows the step-by-step process to install and config it. All the tutorials were old and vague. Also, the main documentation is very confusing. I’ve spent a lot of hours to figure out how to install and config it. At this tutorial, I’m going to show you all the things you need to install and config the CAS server to use a DB as a user source. I’ll also show you how to integrate the CAS on your services based on spring boot (part 2).
我最近为基于弹簧启动的项目安装了Apereo CAS服务器。 我没有找到任何好的教程来显示安装和配置它的逐步过程。 所有的教程都是古老而模糊的。 另外,主要文档非常混乱。 我花了很多时间来弄清楚如何安装和配置它。 在本教程中,我将向您展示安装和配置CAS服务器以使用DB作为用户源所需的所有内容。 我还将向您展示如何基于Spring Boot将CAS集成到您的服务中(第2部分)。
什么是CAS服务器: (What is CAS server:)
If you have ever logged into Google services such as Gmail, Youtube, and etc, you maybe have noticed if you logged into one service, you will be logged-in to all others too. How this is possible?
如果您曾经登录过Gmail,Youtube等Google服务,则可能已经注意到,如果您登录了一项服务,那么您也将登录到所有其他服务。 这怎么可能?
This is an SSO (Single-Sign-On) system. A method which lets the users to login to a group of services centrally in one place. Apereo CAS (Central Authentication Service) is an open-source project which provides you an easy way to implement SSO. It means your users can login/logout to all of your services centrally at the CAS just once, then they will have access to all the secure services without using the username/password.
这是一个SSO(单点登录)系统。 一种使用户可以在一个地方集中登录一组服务的方法。 Apereo CAS(中央身份验证服务)是一个开源项目,为您提供了一种实现SSO的简便方法。 这意味着您的用户可以一次在CAS上集中登录/注销所有服务,然后他们无需使用用户名/密码即可访问所有安全服务。
如何开始: (How to start:)
To install CAS you can use a method called “War Overlay”.
要安装CAS,您可以使用一种称为“战争叠加”的方法。
“Overlays are a strategy to combat repetitive code and/or resources. Rather than downloading the CAS codebase and building from source, overlays allow you to download a pre-built vanilla CAS web application server provided by the project itself and override/insert specific behavior into it. At build time, the build installation process will attempt to download the provided binary artifact first. Then the tool will locate your configuration files and settings made available inside the same project directory and will merge those into the downloaded artifact in order to produce one wholesome archive (i.e.
cas.war) .”“覆盖图是一种与重复代码和/或资源作斗争的策略。 叠加层无需下载CAS代码库并从源代码进行构建,而是允许您下载项目本身提供的预构建的香草CAS Web应用程序服务器,并将特定行为覆盖/插入其中。 在构建时,构建安装过程将尝试首先下载提供的二进制工件。 然后,该工具将找到您在同一项目目录中可用的配置文件和设置,并将这些文件和设置合并到下载的工件中,以生成一个有益的存档(即
cas.war)。”
But before this, you need some requirements to run CAS:
但是在此之前,您需要运行CAS的一些要求:
Java — You need JDK 11+, Install if it’s not installed before and set JAVA_HOME to where Java has been installed (for ubuntu you can check this useful article)
Java —您需要JDK 11+,如果之前未安装JDK,请先安装,然后将JAVA_HOME设置为Java的安装位置(对于ubuntu,您可以查看此实用文章)
- Git — You need git to clone the CAS overlay template, It’s not required, but I suggest to use it. Git —您需要git来克隆CAS覆盖模板,这不是必需的,但我建议使用它。
Now you should clone this Github repository somewhere on your system:
现在,您应该在系统上的某个位置克隆此Github存储库:
git clone https://github.com/apereo/cas-overlay-templateAfter cloning, to run CAS we need to config some essential things. Start by editing the cas.properties file at {project_root}/etc/cast/config folder. Set “cas.server.name” to localhost (https), and add “server.ssl.key-store” and “server.ssl.key-store-password”. We are going to create “thekeystore” file next.
克隆后,要运行CAS,我们需要配置一些必要的东西。 首先编辑{project_root} / etc / cast / config文件夹中的cas.properties文件。 将“ cas.server.name”设置为localhost(https),然后添加“ server.ssl.key-store”和“ server.ssl.key-store-password”。 接下来,我们将创建“ thekeystore”文件。
cas.server.name=https://localhost:8443
cas.server.prefix=${cas.server.name}/cas
server.ssl.key-store=file:/etc/cas/config/thekeystore
server.ssl.key-store-password=changeitlogging.config=file:/etc/cas/config/log4j2.xml# cas.authn.accept.users=Open a terminal and go to the {project_root}/etc/cas/config. Run this command and enter localhost for first and last name question:
打开终端,然后转到{project_root} / etc / cas / config。 运行此命令,并为名字和姓氏问题输入本地主机:
keytool -genkey -keyalg RSA -alias thekeystore -keystore thekeystore -storepass changeit -validity 360 -keysize 2048This command will create a “thekeystore” file. Please note to enter “localhost” for the first and last name to prevent SSL error for running the CAS management and other client apps. Now we need to import this file into the JDK to use for client apps. (Note to JAVA_HOME environment variable, you must have set it before)
该命令将创建一个“ thekeystore”文件。 请注意,在名字和姓氏上输入“ localhost ”,以防止运行CAS管理和其他客户端应用程序时发生SSL错误。 现在,我们需要将此文件导入到JDK中以用于客户端应用程序。 (注意JAVA_HOME环境变量,您必须事先设置它)
keytool -importkeystore -srckeystore thekeystore -destkeystore $JAVA_HOME/lib/security/cacertsAfter importing, you must restart all Java instances that are running or restart the system.
导入后,必须重新启动所有正在运行的Java实例或重新启动系统。
Next, install all the dependencies and build CAS (this command will copy configuration files from {project_root}/etc/cas/config to /etc/cas/config folder in your OS, make sure you have permission to create and write in this folder.)
接下来,安装所有依赖项并构建CAS(此命令会将配置文件从{project_root} / etc / cas / config复制到操作系统中的/ etc / cas / config文件夹中,确保您具有创建和写入此文件夹的权限。 )
./gradlew clean copyCasConfiguration buildNow you can run the CAS and test it. Just type in terminal:
现在您可以运行CAS并对其进行测试。 只需输入终端:
./gradlew runAfter seeing this,
看到这个之后
Your CAS server is ready, you can access it at your local system: http://localhost:8443/cas/. Maybe you get an SSL error when open this URL. to ignore this error, in Chrome, when you are on the page, type “thisisunsafe”.
您的CAS服务器已准备就绪,您可以在本地系统上访问它: http:// localhost:8443 / cas / 。 打开此URL时,您可能会收到SSL错误。 要忽略此错误,请在Chrome浏览器中的页面上键入“ thisisunsafe”。
You can see the login page of the CAS. There is a default user that you can use to login. Enter “casuser” as the username and “Mellon” as the password.
您可以看到CAS的登录页面。 您可以使用默认用户登录。 输入“ casuser”作为用户名,输入“ M ellon”作为密码。
从数据库加载用户: (Load Users from a DataBase:)
CAS supports many different ways to authenticate users, for example, LDAP, X.509, Azure Active Directory, REST, Redis, Database, and many more. We are going to config a PostgreSQL DB as a source that will be used by CAS to authenticate the users.
CAS支持许多不同的方式来验证用户身份,例如LDAP,X.509,Azure Active Directory,REST,Redis,数据库等等。 我们将配置PostgreSQL数据库作为源,CAS将使用它来验证用户身份。
To enable the Database authentication, we must add the following dependency to the war overlay. For this edit the {project_root}/build.gradle and add this line in the dependencies section (where there is this line “// Other CAS dependencies/modules may be listed here…”):
要启用数据库身份验证,我们必须将以下依赖项添加到战争叠加层。 为此,请编辑{project_root} /build.gradle并将此行添加到“依赖项”部分(此行“ //其他CAS依赖项/模块可能在此处列出...”):
implementation "org.apereo.cas:cas-server-support-jdbc:${project.'cas.version'}"
implementation "org.apereo.cas:cas-server-support-jdbc-drivers:${project.'cas.version'}"We need to create a table in postgres to store the user information. You can use this query to create the table for testing. We Also insert a user for the test (email/username: ‘user1@test.com’, password: ‘testpass’ which encoded by bcrypt algorithm)
我们需要在postgres中创建一个表来存储用户信息。 您可以使用此查询来创建要测试的表。 我们还为测试插入一个用户(电子邮件/用户名:“ user1@test.com”,密码:“ testpass”,由bcrypt算法编码)
CREATE TABLE users
(
id bigint NOT NULL,
disabled boolean,
email character varying(40) COLLATE pg_catalog."default",
first_name character varying(40) COLLATE pg_catalog."default",
last_name character varying(40) COLLATE pg_catalog."default",
expired boolean,
password character varying(100) COLLATE pg_catalog."default",
CONSTRAINT users_pkey PRIMARY KEY (id),
CONSTRAINT uk6dotkott2kjsp8vw4d0m25fb7 UNIQUE (email)
)
WITH (
OIDS = FALSE
);INSERT INTO users(
id, disabled, email, first_name, last_name, expired, password)
VALUES (1, false, 'user1@test.com', 'test', 'user1', false, '$2y$12$7XQUDwK3QE7oBB0wmVpht.aT7gESI205SgWarj15Wz2Jt6OfglbQ.');Connecting CAS to the Database is really simple and straightforward, we just need to add some configurations to our cas.properties. So edit {project_root}/etc/cas/config/cas.properties file and add these lines (we just edit the project cas.properties file, then we run gradlew command, it will be copied to /etc/cas/config folder automatically, so don’t edit /etc/cas/config files directly):
将CAS连接到数据库确实非常简单明了,我们只需要在cas.properties中添加一些配置即可。 因此,编辑{project_root} /etc/cas/config/cas.properties文件并添加以下行(我们只需编辑项目cas.properties文件,然后运行gradlew命令,它将自动复制到/ etc / cas / config文件夹中,因此请勿直接编辑/ etc / cas / config文件):
cas.authn.accept.users=
cas.authn.jdbc.query[0].driver-class=org.postgresql.Driver
cas.authn.jdbc.query[0].url=jdbc:postgresql://localhost:5432/{db-name}
cas.authn.jdbc.query[0].dialect=org.hibernate.dialect.PostgreSQL95Dialect
cas.authn.jdbc.query[0].driver-class=org.postgresql.Driver
cas.authn.jdbc.query[0].user={db-username, default fo postgres is "postgres"}
cas.authn.jdbc.query[0].password={db-password, default for postgres is blank}cas.authn.jdbc.query[0].sql=SELECT * FROM users WHERE email = ?
cas.authn.jdbc.query[0].password-encoder.type=BCRYPT
cas.authn.jdbc.query[0].field-password=password
cas.authn.jdbc.query[0].field-expired=expired
cas.authn.jdbc.query[0].field-disabled=disabledReplace all the bold strings with your Database connection parameters. Please note to “cas.authn.jdbc.query[0].sql” config, it will be used to query the user by the username. Edit it based on your user’s table at the DB, for example, if you are using a username field, replace the email with the username. Also, you can specify the expired and disabled fields, they are the boolean fields in your user’s table which determine the user account is disabled/expired or not. If disabled/expired columns were true, CAS won’t let user login. Other important configs are password and password-encoder. You must set the field in your user table which stores the user password and let CAS know how the password is encoded. At this example, we are using the BCRYPT. You can see more options here.
用数据库连接参数替换所有粗体字符串。 请注意“ cas.authn.jdbc.query [0] .sql”配置,它将用于通过用户名查询用户。 例如,如果您使用的是用户名字段,则根据数据库中用户的表进行编辑,将电子邮件替换为用户名。 另外,您可以指定过期和禁用字段,它们是用户表中的布尔值字段,它们确定用户帐户是否已禁用/过期。 如果禁用/过期的列为true,则CAS将不允许用户登录。 其他重要的配置是密码和密码编码器。 您必须在用户表中设置存储用户密码的字段,并让CAS知道密码的编码方式。 在此示例中,我们正在使用BCRYPT。 您可以在此处看到更多选项。
There are more configurations you can use, please check this page for more information. Now you can build and run the CAS again (note it’s required to run copyCasConfiguration and build to install new dependencies and apply new configs):
您可以使用更多配置,请检查此页面以获取更多信息。 现在,您可以再次构建并运行CAS(请注意,需要运行copyCasConfiguration并进行构建以安装新的依赖项并应用新的配置):
./gradlew clean copyCasConfiguration build runNow you can login with the test user, go to https://localhost:8443/cas and use ‘user1@test.com’ as username and ‘testpass’ as password.
现在,您可以使用测试用户登录,转到https:// localhost:8443 / cas并使用“ user1@test.com”作为用户名,并使用“ testpass”作为密码。
安装CAS管理: (Install CAS Management:)
CAS management is an administrative interface for CAS. It is an independent software which you can deploy separately and lets you manage services and related configs. We are going to install and config it. First clone this repo:
CAS管理是CAS的管理界面。 它是一个独立的软件,可以单独部署,并可以管理服务和相关配置。 我们将要安装和配置它。 首先克隆此仓库:
git clone https://github.com/apereo/cas-management-overlayThen you can config it by editing {project_root}/etc/cas/configs/management.properties file. It’s important to “set cas.server.name” to the URL of the CAS server.
然后,您可以通过编辑{project_root} /etc/cas/configs/management.properties文件进行配置。 将cas.server.name设置为CAS服务器的URL很重要。
cas.server.name=https://localhost:8443
cas.server.prefix=${cas.server.name}/casmgmt.serverName=https://localhost:8444
mgmt.adminRoles[0]=ROLE_ADMIN
mgmt.userPropertiesFile=file:/etc/cas/config/users.json
server.port=8444server.ssl.key-store=file:/etc/cas/config/thekeystore
server.ssl.key-store-password=changeitlogging.config=file:/etc/cas/config/log4j2-management.xmlBecause we are using the 8443 port for the CAS server, we must change the CAS management server to something else to avoid the port conflict. We set “mgmt.serverName” and “server.port” for this purpose.
因为我们将8443端口用于CAS服务器,所以必须将CAS管理服务器更改为其他名称,以避免端口冲突。 为此,我们设置了“ mgmt.serverName”和“ server.port”。
There is a default user “casuser” at the users.json file. CAS Management will authenticate users by CAS server, so you need to map your user from the previous step at the users.json file. Change the “casuser” to “user1@test.com” (your defined user at the DB).
users.json文件中有一个默认用户“ casuser”。 CAS Management将通过CAS服务器对用户进行身份验证,因此您需要将上一步中的用户映射到users.json文件。 将“ casuser”更改为“ user1@test.com”(您在数据库中定义的用户)。
{
"user1@test.com" : {
"@class" : "org.apereo.cas.mgmt.authz.json.UserAuthorizationDefinition",
"roles" : [ "ROLE_ADMIN" ]
}
}We also need to define the CAS management as a service in our CAS server. CAS management will be used to manage CAS services, but for now, we need to add it manually. We are going to config CAS to use json service registry to load and persist the services. There are many storage options for persisting the services for CAS server, you can find more information here.
我们还需要在CAS服务器中将CAS管理定义为一项服务。 CAS管理将用于管理CAS服务,但是现在,我们需要手动添加它。 我们将配置CAS以使用json服务注册表加载和持久化服务。 有许多存储选项可用于持久保存CAS服务器的服务,您可以在此处找到更多信息。
Add a new dependency to “build.gradle” at CAS server overlay and also at “build.gradle” at CAS management overlay template:
在CAS服务器覆盖处的“ build.gradle”以及CAS管理覆盖模板的“ build.gradle”中添加新的依赖项:
implementation "org.apereo.cas:cas-server-support-json-service-registry:${project.'cas.version'}"Add this config to the cas.properties:
将此配置添加到cas.properties:
cas.service-registry.json.location=classpath:/servicesThis config tells to CAS to load service information from {project_root}src/main/resources/services/ path. We are going to config CAS management to use the same path to manage services. Add this config to the CAS management config file:
此配置告知CAS从{project_root} src / main / resources / services /路径加载服务信息。 我们将配置CAS管理以使用相同的路径来管理服务。 将此配置添加到CAS管理配置文件:
cas.service-registry.json.location=file:/{path-to-src-folder-of-cas-overlay-template}/main/resources/servicesTo register the CAS management itself as a service add a new JSON file name “casManagement-1001.json” to {project_root}/src/main/resources/services path (create it if doesn’t exist) with the below content. (casManagement is the name of the service and 1001 is an ID for it, you should follow this naming convention: serviceName + “-” + serviceNumericId + “.json”)
要将CAS管理本身注册为服务,请在以下内容的{project_root} / src / main / resources / services路径(如果不存在,请创建)中添加一个新的JSON文件名“ casManagement-1001.json”。 (casManagement是服务的名称,而1001是它的ID,您应遵循以下命名约定:serviceName +“-” + serviceNumericId +“ .json”)
{
"@class" : "org.apereo.cas.services.RegexRegisteredService",
"serviceId" : "https://localhost:8444/cas-management/",
"name" : "casManagement",
"id" : 1001,
"logoutType" : "BACK_CHANNEL",
"logoutUrl" : "https://localhost:8444/cas-management/logout"
}build and run the CAS server and CAS management.
构建并运行CAS服务器和CAS管理。
./gradlew clean copyCasConfiguration build runIncommon.pem错误: (Incommon.pem error:)
When I was running CAS management on Ubuntu 18.04, I encountered to this error:
在Ubuntu 18.04上运行CAS管理时,遇到此错误:
WARN [org.apereo.cas.support.saml.SamlUtils] — <Resource [class path resource [incommon.pem]] cannot be located> …
WARN [org.apereo.cas.support.saml.SamlUtils]-<无法找到资源[类路径资源[incommon.pem]]>…
I’ve fixed this by adding incommon.pem file to {cas-management-root}/src/main/resources folder with this content.
我已通过添加incommon.pem文件{CAS管理根} / src目录/主/资源文件夹与此修正了这个内容。
完成... (Done…)
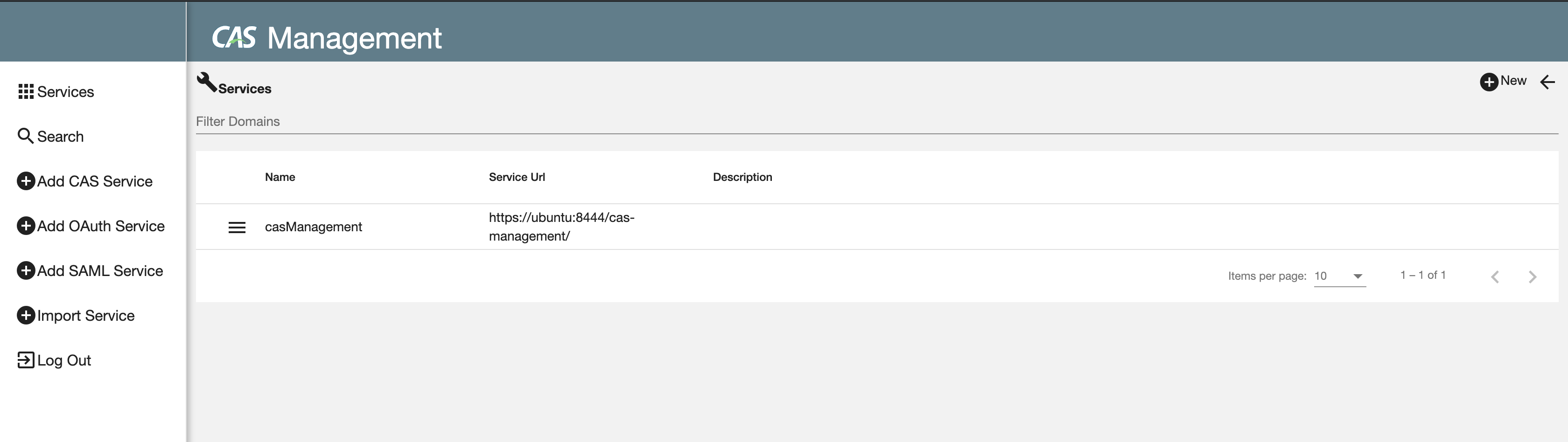
It’s done for now. You can access to CAS management at https://localhost:8444/cas-management. There are many supported options and protocols you can use with CAS. Check documentation for more information. I’m going to use the CAS server for an example Spring Boot app in the next tutorial.
现在完成了。 您可以通过https:// localhost:8444 / cas-management访问CAS管理。 CAS可使用许多受支持的选项和协议。 查看文档以获取更多信息。 在下一个教程中,我将使用CAS服务器作为示例Spring Boot应用程序。
翻译自: https://medium.com/@fathi.reza/install-cas-server-with-db-authentication-8ff52234f52
web服务器和db服务器





















 68
68

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








