web服务器json
In this article, I answer the following questions:
在本文中,我回答以下问题:
- What is a JWT? 什么是JWT?
- What are the different parts of a JWT? JWT有哪些不同部分?
- What is the main use of a JWT? JWT的主要用途是什么?
定义 (Definition)
JSON Web Token, also known as JWT (pronounced “jot”), is a standard that defines a URL-safe way to transfer information between parties. This standard follows the RFC-7519 specification.
JSON Web令牌,也称为JWT(发音为“ jot”),是一种定义URL安全的方式在各方之间传输信息的标准。 该标准遵循RFC-7519规范。
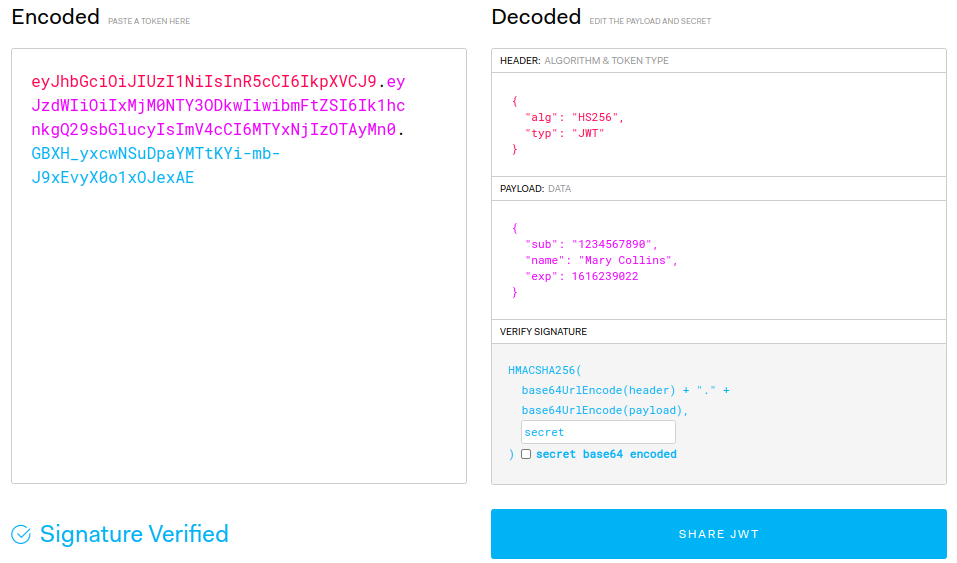
Here is an example of a JWT (newlines and colors inserted for readability):
这是JWT的示例(为了便于阅读而插入了换行符和颜色):

Actually, the JWT is just the concatenation of three strings separated by dots. Each of these strings is a different part of the token.
实际上,JWT只是由点分隔的三个字符串的串联。 这些字符串中的每一个都是令牌的不同部分。
Let’s see how we got to this final version of the token.
让我们看看如何获得令牌的最终版本。
智威汤逊的结构 (Structure of a JWT)
The three parts of a JWT are:
JWT的三个部分是:
- Header 标头
- Payload 有效载荷
- Signature 签名

The signature is optional. If a token does not have this part, it is an unsecured JWT. Because unsecured JWTs are rarely used, I will only address signed JWTs in this article.
签名是可选的。 如果令牌不包含此部分,则它是不安全的JWT。 由于很少使用不安全的JWT,因此在本文中,我将仅介绍签名的JWT。
Besides the signature, the token has two other parts: the header and the payload. Both of them are originally written in JSON, hence the name JSON Web Token.
除签名外,令牌还有其他两个部分:标头和有效负载。 两者最初都是用JSON编写的,因此名称为JSON Web令牌。
To achieve the final version of the token I showed before, the header and the payload need to be individually encoded using Base64Url.
为了实现我之前显示的令牌的最终版本,需要使用Base64Url对报头和有效负载进行单独编码。
Base64 is an encoding algorithm that allows you to encode any characters into Latin letters, digits, plus, and slash.
Base64是一种编码算法,允许您将任何字符编码为拉丁字母,数字,加号和斜杠。
Base64Url is a modified version of the Base64 algorithm. The original Base64 includes characters that are invalid for filenames and URLs. In contrast, Base64Url fixes that and allows the JWT to be URL-safe.
Base64Url是Base64算法的修改版本。 原始Base64包含对文件名和URL无效的字符。 相反,Base64Url对此进行了修复,并允许JWT是URL安全的。
标头 (Header)
The header contains information about the token itself. It is also known as the JOSE header.
标头包含有关令牌本身的信息。 也称为JOSE标头。
For the header, the following header parameters are available:
对于标题,可以使用以下标题参数:
alg: The algorithm used in the signature. This field is mandatory. In the case of an unsecured JWT, this value should be set tonone.alg:签名中使用的算法。 此字段是必填字段。 对于不安全的JWT,此值应设置为none。typ: The media type of the token. In our case, it should beJWT. This field is optional.typ:令牌的媒体类型 。 在我们的情况下,应该是JWT。 该字段是可选的。cty: The content type. This claim must only be present if the payload contains a nested token. If the nested token is a JWT, then the parameter should be set toJWT. This field is optional.cty:内容类型。 仅当有效负载包含嵌套令牌时,才可以提出此声明。 如果嵌套令牌是JWT,则应将参数设置为JWT。 该字段是可选的。
This is the header for our example:
这是我们的示例的标头:

After it is encoded using Base64Url, we get:
使用Base64Url对其进行编码后,我们得到:

有效载荷 (Payload)
The payload is a group of JWT claims that are name/value pairs giving information about a party. The name of a claim is called the Claim Name, and the value is called the Claim Value.
有效负载是一组JWT声明,它们是提供有关一方信息的名称/值对。 索赔的名称称为“索赔名称”,该值称为“索赔值”。
There are three types of JWT claims:
JWT声明有以下三种类型:
- Registered claims 登记的索赔
- Public claims 公开声明
- Private claims 私人索赔
Registered claims are claims whose claim names are registered in the IANA JSON Web Token Claims registry and defined in the specification. None of these claims are mandatory.
登记的索赔 是声明名称已在IANA JSON Web令牌声明注册表中注册并在规范中定义的声明。 这些要求都不是强制性的。
The registered claim names are:
注册的索赔名称为:
iss(Issuer Claim): The issuer of the JWT.iss(发行方声明):JWT的发行方。sub(Subject Claim): The subject of the JWT.sub(主题声明):JWT的主题。aud(Audience Claim): The audience (recipients) of the JWT.aud(听众要求):JWT的听众(收件人)。exp(Expiration Time Claim): The expiration time of the JWT. This date/time is a UNIX timestamp. The given date/time must be after the current date/time.exp(到期时间声明):JWT的到期时间。 此日期/时间是UNIX时间戳记 。 给定的日期/时间必须在当前日期/时间之后。nbf(Not Before Claim): Before the time defined in this claim, the JWT is not accepted for processing.nbf(不在声明之前):在此声明中定义的时间之前,不接受JWT进行处理。iat(Issued At Claim): The time at which the JWT was issued.iat(在索赔时发出):JWT的发布时间。jti(JWT ID Claim): A string representing a unique identifier for the JWT.jti(JWT ID声明):表示JWT的唯一标识符的字符串。
Public claims are claims that are either registered in the IANA JSON Web Token Claims registry without being defined in the specification or named using a collision-resistant name (e.g. by including a namespace).
公开声明 是未在规范中定义或在IANA JSON Web令牌声明注册表中注册的声明,或使用抗冲突名称(例如,通过包含名称空间)命名的声明。
Private claims are claims defined by consumers and producers of the JWTs that aren’t registered. Because of this, there is the possibility of name collision.
私人索赔是由未注册的JWT的消费者和生产者定义的索赔。 因此,存在名称冲突的可能性。
This is the payload for our example:
这是我们示例的有效负载:

After it is encoded using Base64Url, we get:
使用Base64Url对其进行编码后,我们得到:

签名 (Signature)
The signature is useful to validate the token. In other words, it allows parties to establish and verify the authenticity of the token. However, this does not prevent other parties from reading its content. To prevent that from happening, the token would need to be encrypted.
签名对于验证令牌很有用。 换句话说,它允许各方建立和验证令牌的真实性。 但是,这并不妨碍其他方阅读其内容。 为防止这种情况发生,令牌需要进行加密。
JSON Web Signatures (JWS) follow the RFC-7515 specification.
JSON Web签名(JWS)遵循RFC-7515规范。
This is how we obtain the signature in pseudocode:
这是我们以伪代码获取签名的方式:

algis the algorithm defined in the header. In our case, it is HMAC + SHA256.secretis the shared secret required by HMAC signatures. It is usually held by the server and used to verify the signature’s authenticity. In our example, we use the wordsecret.secret是HMAC签名所需的共享秘密。 它通常由服务器保存,并用于验证签名的真实性。 在我们的示例中,我们使用单词secret。
The final version of our signature looks like this:
我们签名的最终版本如下:

After this step, all the token parts are concatenated with dots separating them to form the final version of our token.
在此步骤之后,所有令牌部分都用点连接起来,将它们分开,以形成令牌的最终版本。
JWT的作用是什么? (What Is a JWT Used For?)
There are several uses for JWTs. The most common use is authentication.
JWT有多种用途。 最常见的用途是身份验证。
Here’s how it works:
运作方式如下:
- The user logs into the server for the first time. 用户首次登录服务器。
- A token is generated in the server for that user. 在服务器中为该用户生成一个令牌。
- The token is stored in the user’s browser. 令牌存储在用户的浏览器中。
- Any subsequent requests the user makes will include the token. 用户随后发出的任何请求都将包含令牌。
- If the user logs out or the token becomes invalid (e.g. it expires), the token is destroyed. The user would have to log in again to acquire a new token. 如果用户注销或令牌变得无效(例如,令牌已过期),则令牌将被销毁。 用户将不得不再次登录以获取新令牌。
结论 (Conclusion)
I hope this article helped you better understand what JSON Web Tokens are. Thank you for reading!
我希望本文能帮助您更好地了解什么是JSON Web令牌。 感谢您的阅读!
翻译自: https://medium.com/better-programming/what-exactly-is-a-json-web-token-678e8a8a5fe4
web服务器json





















 577
577

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








