The malware specifically aims to target those who are looking for cartographic presentations of the spread of COVID-19 on the Internet. In light of Johns Hopkins University releasing the official COVID-19 tracker, hackers have quickly bolted together another malicious application that, on its front-end, shows a map loaded from a legitimate online source but in the background compromises the computer by stealing user passwords and credentials.
该恶意软件专门针对那些正在寻找Internet上COVID-19传播的制图展示的人。 鉴于约翰·霍普金斯大学发布了官方的COVID-19跟踪器,黑客Swift将另一个恶意应用程序捆绑在一起,该应用程序的前端显示了从合法的在线来源加载的地图,但在后台却通过窃取用户密码而危害了计算机。和凭据。
恶意软件故障 (Malware Breakdown)
The latest threat, designed to steal information from unwitting victims, was first spotted by the MalwareHunterTeam last week. They concluded that whilst this is a new threat it contains a number of old components.
上周,MalwareHunterTeam首次发现了最新的威胁,旨在从不知情的受害者那里窃取信息。 他们得出结论,虽然这是一种新威胁,但其中包含许多旧组件。
It was identified that the underlying malware was the AZORult, an information-stealing malicious software discovered in 2016. AZORult malware collects information stored in web browsers, particularly cookies, browsing histories, user IDs, passwords, and even cryptocurrency keys.
已确定潜在的恶意软件是AZORult,这是2016年发现的一种窃取信息的恶意软件。AZORult恶意软件收集存储在Web浏览器中的信息,特别是cookie,浏览历史记录,用户ID,密码,甚至是加密货币密钥。

样品分析 (Sample Analysis)
Shai Alfasi, a cybersecurity researcher at Reason Labs. Provides a full technical write up of the malware. Shai reported that the application is named ‘Corona-virus-Map.com.exe’ and that its a small Win32 EXE file with a payload size of only around 3.26 MB.
Reason Labs的网络安全研究员Shai Alfasi。 提供恶意软件的完整技术说明。 Shai报告说,该应用程序名为“ Corona-virus-Map.com.exe ”,它是一个很小的Win32 EXE文件,有效载荷大小仅为3.26 MB。
Double-clicking the file opens a window that shows various information about the spread of COVID-19. The centerpiece is a “map of infections” similar to the one hosted by Johns Hopkins University, a legitimate online source to visualize and track reported coronavirus cases in real-time.
双击该文件将打开一个窗口,该窗口显示有关COVID-19传播的各种信息。 核心是类似于约翰霍普金斯大学 ( Johns Hopkins University)主办的“感染地图”,这是一个合法的在线资源,可以实时可视化和跟踪报告的冠状病毒病例。
To be noted, the original coronavirus map hosted online by Johns Hopkins University or ArcGIS is not infected or backdoored in any way and are safe to visit.
值得注意的是,约翰·霍普金斯大学或ArcGIS在线托管的原始冠状病毒图丝毫没有被感染或后门,可以安全访问。
感染迹象 (Signs of Infection)
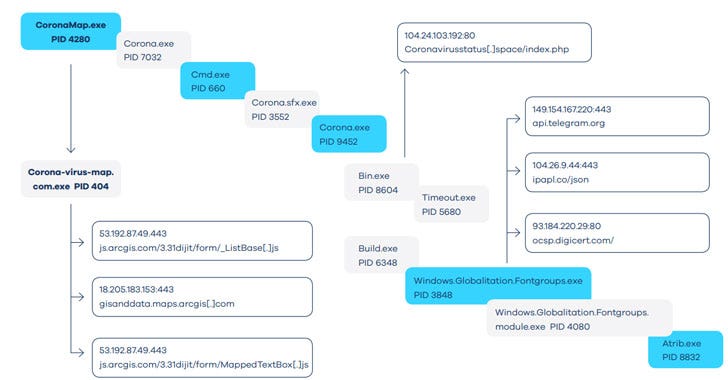
Executing the Corona-virus-Map.com.exe results in the creation of duplicates of the Corona-virus-Map.com.exe file and multiple Corona.exe, Bin.exe, Build.exe, and Windows.Globalization.Fontgroups.exe files. This is highly suspicious and irregular of normal program execution.
执行Corona-virus-Map.com.exe将导致重复创建Corona-virus-Map.com.exe文件以及多个Corona.exe,Bin.exe,Build.exe和Windows.Globalization.Fontgroups。 exe文件。 这是高度可疑的,并且不正常地执行程序。

Execution of the malware activates the following processes: Bin.exe, Windows.Globalization.Fontgroups.exe, and Corona-virus-Map.com.exe. These attempt to connect to several URLs which will act as Command and Control addresses for the malware.
恶意软件的执行将激活以下过程:Bin.exe,Windows.Globalization.Fontgroups.exe和Corona-virus-Map.com.exe。 这些尝试连接到多个URL,这些URL将充当恶意软件的命令和控制地址。
Within the write up by Alfasi he presented a detailed account of how he dissected the malware in a blog post on the Reason Security blog. One highlight detail is his analysis of the Bin.exe process with Ollydbg. Accordingly, the process wrote some dynamic link libraries (DLL). The DLL “nss3.dll” caught his attention as it is something he was acquainted with from different actors.
在Alfasi撰写的文章中,他在Reason Security博客上的博客文章中详细介绍了如何剖析该恶意软件。 一个重要的细节是他对Ollydbg的Bin.exe进程的分析。 因此,该过程编写了一些动态链接库(DLL)。 DLL“ nss3.dll”引起了他的注意,因为这是他从不同的演员那里认识的。
Alfasi observed a static loading of APIs associated with nss3.dll. These APIs appeared to facilitate the decryption of saved passwords as well as the generation of output data.
Alfasi观察到与nss3.dll相关的API的静态加载。 这些API似乎有助于解密已保存的密码以及生成输出数据。
清洁与预防 (Cleaning and Prevention)
It should be noted that the age of this malware is old and dated and so whilst it may sound mundane antivirus software with the latest patch will be all it takes to stop you from getting infected — well and maybe some hand sanitizer.
应当指出,该恶意软件的年龄已经过时且过时了,因此尽管听起来听起来像是带有最新补丁的平凡的杀毒软件,但它可以阻止您被感染,并且还可以使用一些手消毒剂。
Other security firms are likely to have already learned about this threat, since Reason made it public on March 9. Their antiviruses or malware protection tools are sure to be updated over time.
自从Reason在3月9日公开以来,其他安全公司可能已经了解到了这种威胁。他们的防病毒或恶意软件保护工具肯定会随着时间的推移而更新。
As such, they may be similarly capable of detecting and preventing this new threat.
因此,它们可能具有类似的检测和预防这种新威胁的能力。
翻译自: https://medium.com/swlh/coronavirus-maps-a-malware-infecting-pcs-worldwide-d4b8654b9a6e





















 66
66











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








