前两天有个帖子提到这个问题,并且说只要加入隧道分离列表就可以实现,这个案例以前从来没有见过,很有挑战意味。通过本人仔细分析,发现那位朋友的说法站不住脚,并且实际配置也不能实现。按照我对隧道分离列表的理解,那个是为了远程客户端拨入用的,也就是说对站点的配置不起作用,如果更深入探讨隧道分离列表,其实该列表的作用并不是在防火墙上,而是作用在客户端上,也就是对客户端加了敏感流量,其它的流量还是从客户端本地网关上网,所以那位朋友的提法根本就是理解上的偏差,那是对客户端上总部的方法,而并非分部通过site to site到总部上网。
这个问题有两个关键点
1.敏感流量是不是可以用any,这个问题有一个朋友专门提出来了,这是成败的关键,如果不支持any,那么对于互联网来说肯定只能是any,就无法成立。幸好可以用any。
2.就是对于NAT的运用,这个用法也是我自己琢磨出来的,因为如果不能实现设计的NAT,虽然可以any了,流量可以送到总部,然而还是无法上网。这个问题困扰了我很久。
这个问题有两个关键点
1.敏感流量是不是可以用any,这个问题有一个朋友专门提出来了,这是成败的关键,如果不支持any,那么对于互联网来说肯定只能是any,就无法成立。幸好可以用any。
2.就是对于NAT的运用,这个用法也是我自己琢磨出来的,因为如果不能实现设计的NAT,虽然可以any了,流量可以送到总部,然而还是无法上网。这个问题困扰了我很久。
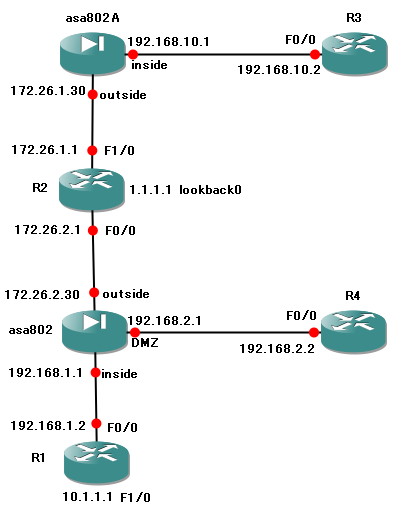
理论说明
总部asa802,分部asa802A
分部通过总部上网,就需要从分布的IP访问任意IP地址的流量都要加密后送到总部,所以建立了一条敏感流量的ACL,access-list sts extended permit ip 192.168.10.0 255.255.255.0 any
另外因为分部也不通过自己的网关上网,所以,分部的inside接口根本不配置NAT的任何配置,全路由。
这样,从分布的流量到达总部,下面,该数据怎么继续下去我思考了很久,从outside接口解密之后,该数据那个接口都不在,目的1.1.1.1,根据总部的路由,它应该被依照默认路由发送,如果不做NAT处理,那么将会以源地址192.168.10.2发送,但是R2里面并没有该地址的路由,所以无法回包,数据到R2就会停止,所以通信不能接通。
那么需要把源地址192.168.10.2转换为总部outside接口IP,我们一般配都是有两个接口,一个进,一个出,而且NAT是挂在进接口上的,而从分部过来的数据应该是在内存里,并没有从那个接口进来,但是我们知道它的出口是outside,那么我们只有唯一的选择,在outside接口上做NAT,这个地方的确有些乱,我们一般就是从进的接口做NAT的敏感流量表,这次我们在outside上做,幸好asa比较智能的理解了我们的意图,转换了源地址192.168.10.2。
分部通过总部上网,就需要从分布的IP访问任意IP地址的流量都要加密后送到总部,所以建立了一条敏感流量的ACL,access-list sts extended permit ip 192.168.10.0 255.255.255.0 any
另外因为分部也不通过自己的网关上网,所以,分部的inside接口根本不配置NAT的任何配置,全路由。
这样,从分布的流量到达总部,下面,该数据怎么继续下去我思考了很久,从outside接口解密之后,该数据那个接口都不在,目的1.1.1.1,根据总部的路由,它应该被依照默认路由发送,如果不做NAT处理,那么将会以源地址192.168.10.2发送,但是R2里面并没有该地址的路由,所以无法回包,数据到R2就会停止,所以通信不能接通。
那么需要把源地址192.168.10.2转换为总部outside接口IP,我们一般配都是有两个接口,一个进,一个出,而且NAT是挂在进接口上的,而从分部过来的数据应该是在内存里,并没有从那个接口进来,但是我们知道它的出口是outside,那么我们只有唯一的选择,在outside接口上做NAT,这个地方的确有些乱,我们一般就是从进的接口做NAT的敏感流量表,这次我们在outside上做,幸好asa比较智能的理解了我们的意图,转换了源地址192.168.10.2。
asa802
ASA Version 8.0(2)
!
command-alias exec c conf t
hostname asa802
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 172.26.2.30 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/2
nameif DMZ
security-level 50
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list acl_outside extended permit icmp any any
access-list sts extended permit ip any 192.168.10.0 255.255.255.0
access-list acl_DMZ extended permit icmp any any
access-list acl_inside extended permit icmp any any
access-list NONAT extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
access-list NONAT extended permit ip 192.168.1.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list NONAT extended permit ip 10.1.1.0 255.255.255.0 192.168.10.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
mtu DMZ 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm p_w_picpath disk0:/asdm-602.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (outside) 1 192.168.10.0 255.255.255.0
nat (inside) 0 access-list NONAT
nat (inside) 1 10.1.1.0 255.255.255.0
nat (inside) 1 192.168.1.0 255.255.255.0
access-group acl_outside in interface outside
access-group acl_inside in interface inside
access-group acl_DMZ in interface DMZ
route outside 0.0.0.0 0.0.0.0 172.26.2.1 1
route inside 10.1.1.0 255.255.255.0 192.168.1.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set freeset esp-des esp-md5-hmac
crypto map mymap 1 match address sts
crypto map mymap 1 set peer 172.26.1.30
crypto map mymap 1 set transform-set freeset
crypto map mymap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
username ronsun password arAvk/QGvhiRdea6 encrypted
tunnel-group 172.26.1.30 type ipsec-l2l
tunnel-group 172.26.1.30 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:46ea0a8d5ffcf31356b9464f43069b9b
: end
asa802#
!
command-alias exec c conf t
hostname asa802
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 172.26.2.30 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/2
nameif DMZ
security-level 50
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
access-list acl_outside extended permit icmp any any
access-list sts extended permit ip any 192.168.10.0 255.255.255.0
access-list acl_DMZ extended permit icmp any any
access-list acl_inside extended permit icmp any any
access-list NONAT extended permit ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
access-list NONAT extended permit ip 192.168.1.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list NONAT extended permit ip 10.1.1.0 255.255.255.0 192.168.10.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
mtu DMZ 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm p_w_picpath disk0:/asdm-602.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (outside) 1 192.168.10.0 255.255.255.0
nat (inside) 0 access-list NONAT
nat (inside) 1 10.1.1.0 255.255.255.0
nat (inside) 1 192.168.1.0 255.255.255.0
access-group acl_outside in interface outside
access-group acl_inside in interface inside
access-group acl_DMZ in interface DMZ
route outside 0.0.0.0 0.0.0.0 172.26.2.1 1
route inside 10.1.1.0 255.255.255.0 192.168.1.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set freeset esp-des esp-md5-hmac
crypto map mymap 1 match address sts
crypto map mymap 1 set peer 172.26.1.30
crypto map mymap 1 set transform-set freeset
crypto map mymap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
username ronsun password arAvk/QGvhiRdea6 encrypted
tunnel-group 172.26.1.30 type ipsec-l2l
tunnel-group 172.26.1.30 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:46ea0a8d5ffcf31356b9464f43069b9b
: end
asa802#
asa802A
ASA Version 8.0(2)
!
command-alias exec c conf t
hostname asa802A
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 172.26.1.30 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.10.1 255.255.255.0
!
interface Ethernet0/2
nameif DMZ
security-level 50
ip address 192.168.3.1 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list acl_outside extended permit icmp any any
access-list sts extended permit ip 192.168.10.0 255.255.255.0 any
access-list acl_DMZ extended permit icmp any any
access-list acl_inside extended permit icmp any any
access-list acl_inside extended permit tcp any any eq telnet
pager lines 24
mtu outside 1500
mtu inside 1500
mtu DMZ 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm p_w_picpath disk0:/asdm-602.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
access-group acl_outside in interface outside
access-group acl_inside in interface inside
access-group acl_DMZ in interface DMZ
route outside 0.0.0.0 0.0.0.0 172.26.1.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set freeset esp-des esp-md5-hmac
crypto map mymap 1 match address sts
crypto map mymap 1 set peer 172.26.2.30
crypto map mymap 1 set transform-set freeset
crypto map mymap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
username ronsun password arAvk/QGvhiRdea6 encrypted
tunnel-group 172.26.2.30 type ipsec-l2l
tunnel-group 172.26.2.30 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:0301e954fd6f3ae1f067ae6d10d221d5
: end
asa802A#
R1
Current configuration : 597 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 10.1.1.1 255.255.255.0
duplex auto
speed auto
!
ip http server
!
ip route 0.0.0.0 0.0.0.0 192.168.1.1
!
control-plane
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
!
!
end
R2
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 172.26.2.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 172.26.1.1 255.255.255.0
duplex auto
speed auto
!
ip http server
!
!
control-plane
!
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
password cisco
login
!
!
end
R3
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.10.2 255.255.255.0
duplex auto
speed auto
!
ip http server
!
ip route 0.0.0.0 0.0.0.0 192.168.10.1
!
!
control-plane
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
!
!
end
R4
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R4
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex auto
speed auto
!
ip http server
!
ip route 0.0.0.0 0.0.0.0 192.168.2.1
!
control-plane
!
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
!
!
end
ASA Version 8.0(2)
!
command-alias exec c conf t
hostname asa802A
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 172.26.1.30 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 192.168.10.1 255.255.255.0
!
interface Ethernet0/2
nameif DMZ
security-level 50
ip address 192.168.3.1 255.255.255.0
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list acl_outside extended permit icmp any any
access-list sts extended permit ip 192.168.10.0 255.255.255.0 any
access-list acl_DMZ extended permit icmp any any
access-list acl_inside extended permit icmp any any
access-list acl_inside extended permit tcp any any eq telnet
pager lines 24
mtu outside 1500
mtu inside 1500
mtu DMZ 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
asdm p_w_picpath disk0:/asdm-602.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
access-group acl_outside in interface outside
access-group acl_inside in interface inside
access-group acl_DMZ in interface DMZ
route outside 0.0.0.0 0.0.0.0 172.26.1.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 0.0.0.0 0.0.0.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set freeset esp-des esp-md5-hmac
crypto map mymap 1 match address sts
crypto map mymap 1 set peer 172.26.2.30
crypto map mymap 1 set transform-set freeset
crypto map mymap interface outside
crypto isakmp identity address
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect netbios
inspect rsh
inspect rtsp
inspect skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect tftp
inspect sip
inspect xdmcp
!
service-policy global_policy global
username ronsun password arAvk/QGvhiRdea6 encrypted
tunnel-group 172.26.2.30 type ipsec-l2l
tunnel-group 172.26.2.30 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:0301e954fd6f3ae1f067ae6d10d221d5
: end
asa802A#
R1
Current configuration : 597 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
interface FastEthernet0/0
ip address 192.168.1.2 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 10.1.1.1 255.255.255.0
duplex auto
speed auto
!
ip http server
!
ip route 0.0.0.0 0.0.0.0 192.168.1.1
!
control-plane
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
!
!
end
R2
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface FastEthernet0/0
ip address 172.26.2.1 255.255.255.0
duplex auto
speed auto
!
interface FastEthernet1/0
ip address 172.26.1.1 255.255.255.0
duplex auto
speed auto
!
ip http server
!
!
control-plane
!
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
password cisco
login
!
!
end
R3
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.10.2 255.255.255.0
duplex auto
speed auto
!
ip http server
!
ip route 0.0.0.0 0.0.0.0 192.168.10.1
!
!
control-plane
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
!
!
end
R4
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R4
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
!
!
!
!
!
interface FastEthernet0/0
ip address 192.168.2.2 255.255.255.0
duplex auto
speed auto
!
ip http server
!
ip route 0.0.0.0 0.0.0.0 192.168.2.1
!
control-plane
!
!
!
alias exec c conf t
!
line con 0
line aux 0
line vty 0 4
!
!
end
检测验证
为了验证效果我们打开R3和R2上的debug
在R3上ping R2上的1.1.1.1,从而模拟互联网上的IP
R3#ping 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 56/77/112 ms
R3#
*Mar 2 23:57:56.124: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
*Mar 2 23:57:56.184: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
*Mar 2 23:57:56.260: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
*Mar 2 23:57:56.324: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
R3#
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 56/77/112 ms
R3#
*Mar 2 23:57:56.124: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
*Mar 2 23:57:56.184: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
*Mar 2 23:57:56.260: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
*Mar 2 23:57:56.324: ICMP: echo reply rcvd, src 1.1.1.1, dst 192.168.10.2
R3#
R2#
*Mar 2 23:57:56.520: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
*Mar 2 23:57:56.648: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
*Mar 2 23:57:56.692: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
*Mar 2 23:57:56.768: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
R2#
可以看到源地址已经变成了172.26.2.30说明已经NAT替换成功。
*Mar 2 23:57:56.520: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
*Mar 2 23:57:56.648: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
*Mar 2 23:57:56.692: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
*Mar 2 23:57:56.768: ICMP: echo reply sent, src 1.1.1.1, dst 172.26.2.30
R2#
可以看到源地址已经变成了172.26.2.30说明已经NAT替换成功。
再测试一下其它类型的程序
R3#1.1.1.1
Trying 1.1.1.1 ... Open
R3#1.1.1.1
Trying 1.1.1.1 ... Open
User Access Verification
Password:
R2>
可以看到telnet没问题的从R3接入R2
R2>
可以看到telnet没问题的从R3接入R2
转载于:https://blog.51cto.com/xushen/676978





















 3126
3126











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








