网络攻防渗透测试之信息收集
主机探测
主机探测指识别目标及其是否可用。这个探测过程中,需要得到目标主机是否Online等信息。由于IDS和IPS的存在,在测试过程中还要考虑对各种保护设施的探测,如WAF。
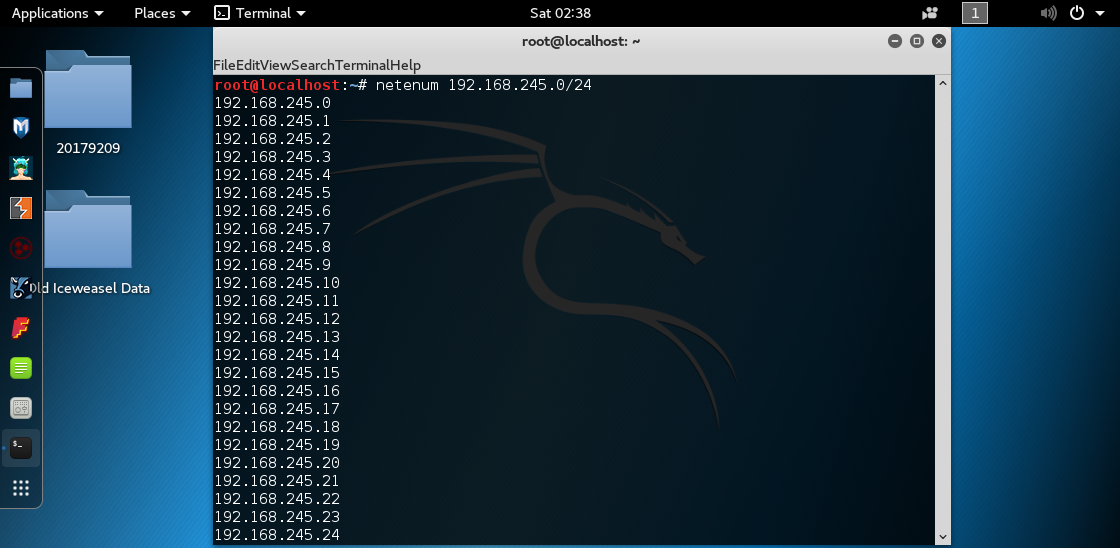
使用netenum获得ip列表
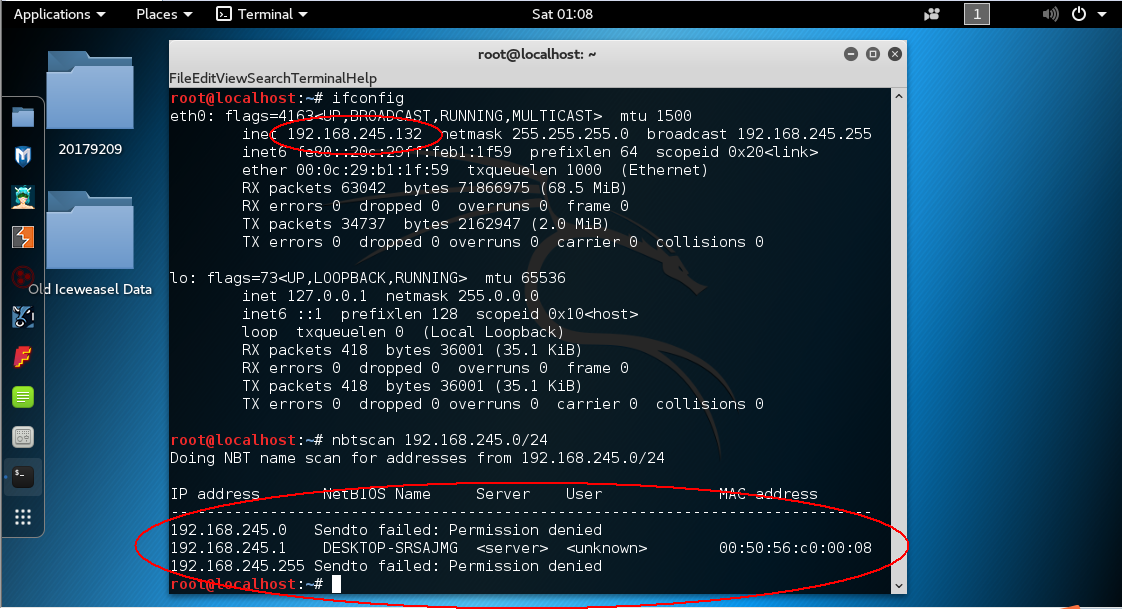
nbtscan扫描某网段存活主机
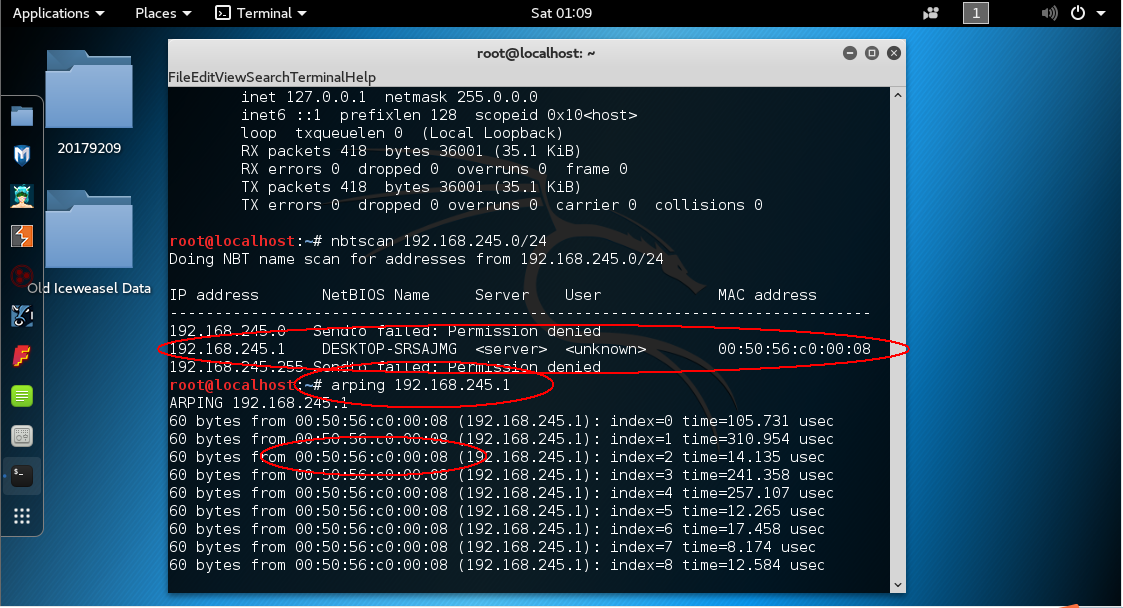
arping 得到目标MAC地址
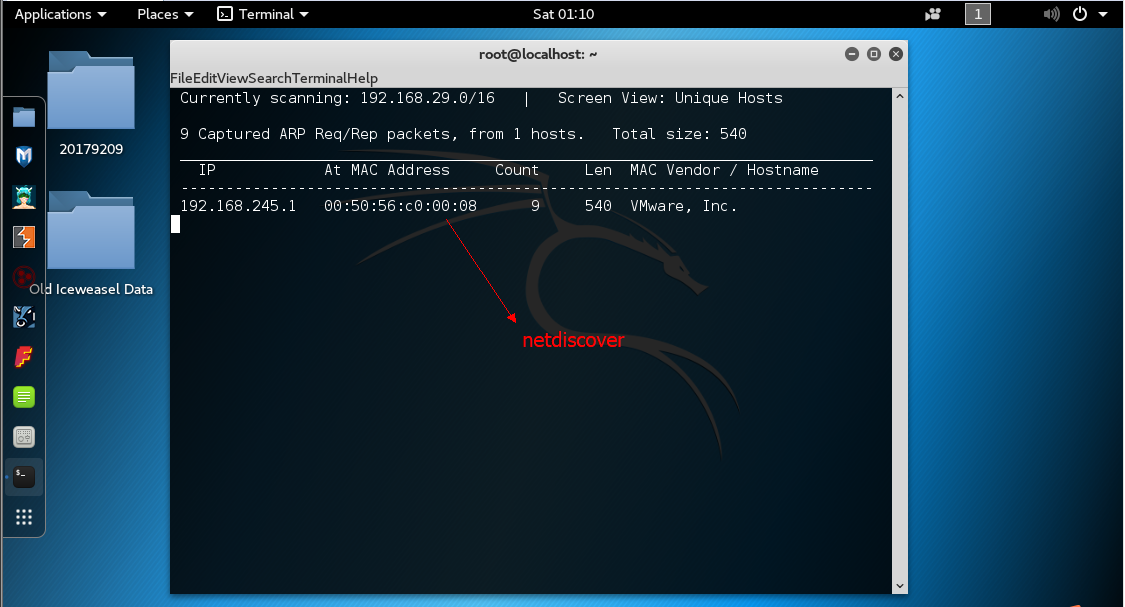
netdiscover探测主机所在网段的存活主机
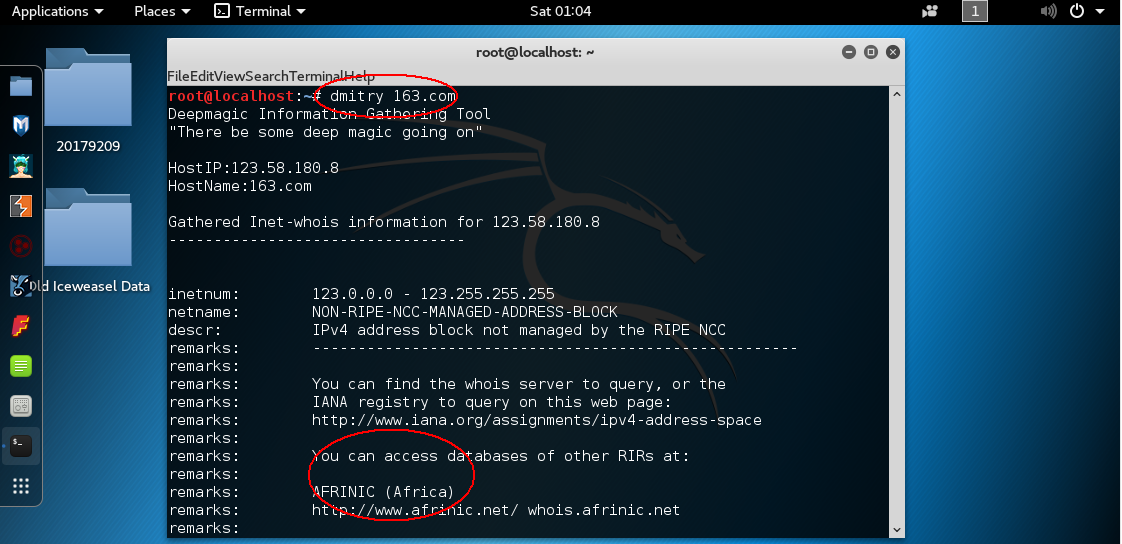
dmitry 收集目标网站信息
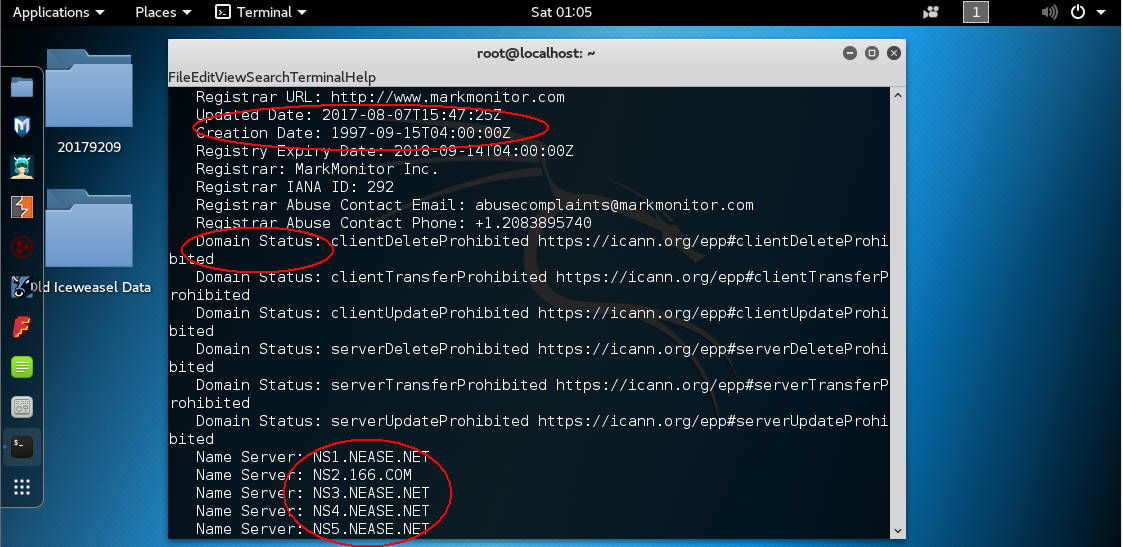
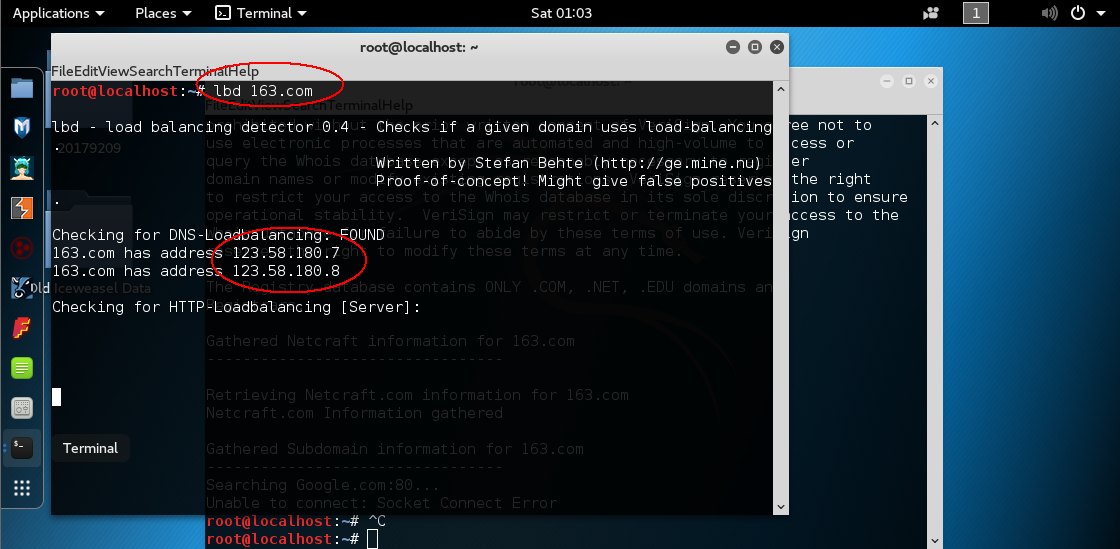
lbd探测目标网站所有ip地址
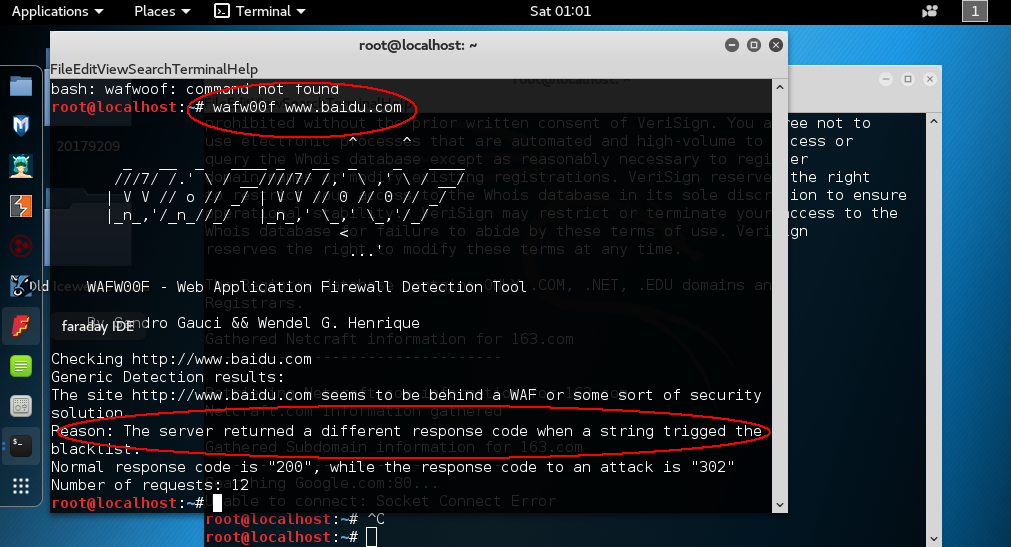
waf检测
主机扫描
通过主机探测,确定测试目标地址后,往往需要对主机信息做更完整的扫描。这个过程需要获取目标主机开放的端口、服务以及主机名、主机操作系统等信息。在Kali中nmap是最典型的主机扫描工具,它有如下功能:
- 主机探测:探测网络上的主机,例如列出响应TCP和ICMP请求、开放特别端口的主机。
- 端口扫描:探测目标主机所开放的端口。
- 版本检测:探测目标主机的网络服务,判断其服务名称及版本号。
- 系统检测:探测目标主机的操作系统及网络设备硬件特性。
- 支持探测脚本的编写:使用Nmap的脚本引擎NSE和 Lua编程语言。
nmap -p端口号 host :扫描特定主机所指定的端口
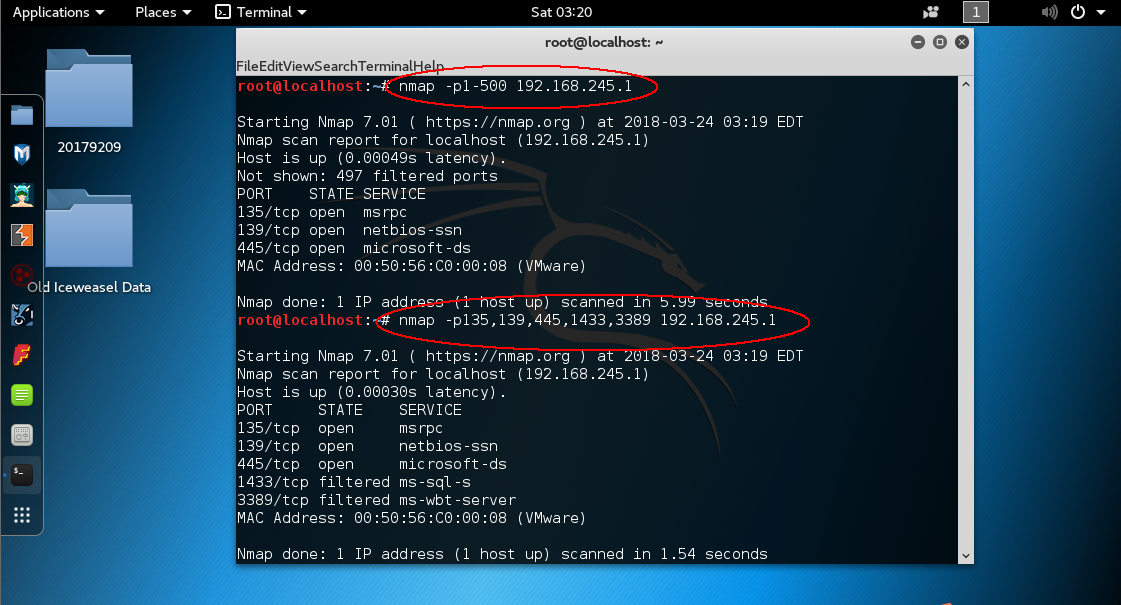
nmap -sV host:扫描目标主机服务及其版本号
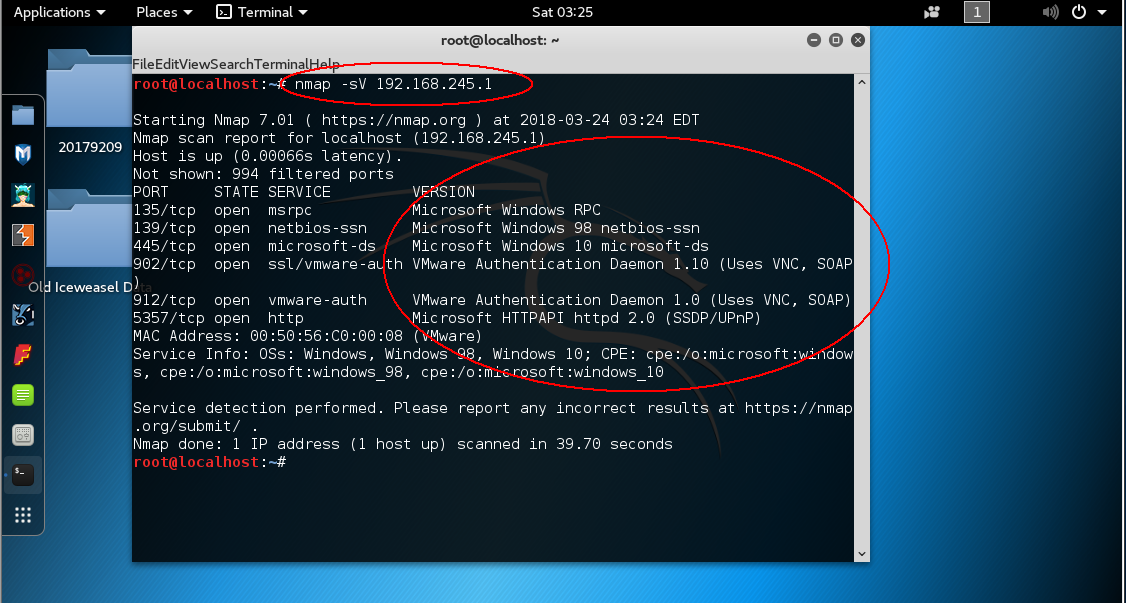
nmap -O host:扫描目标主机操作系统
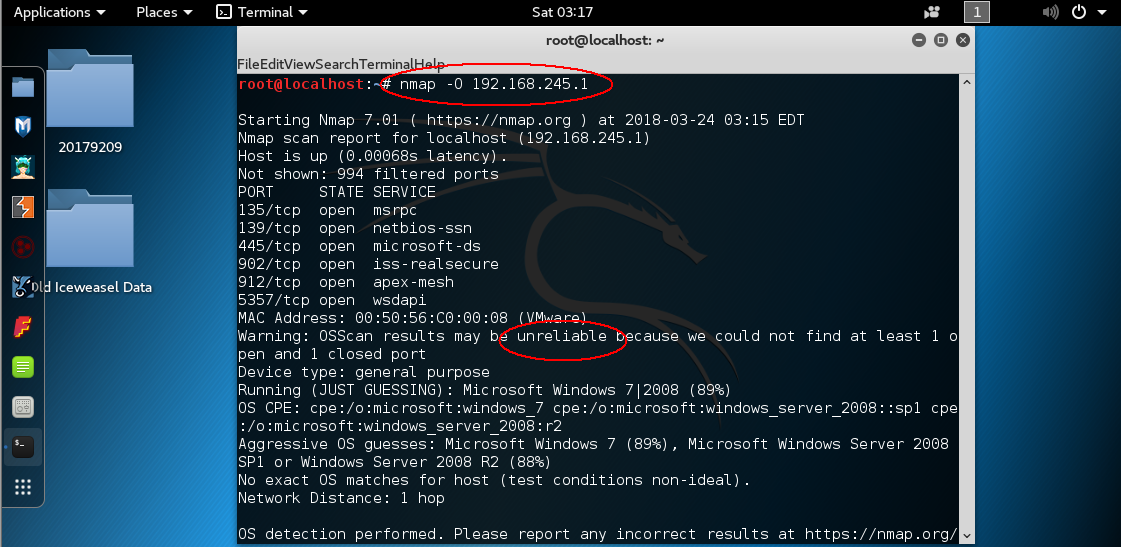
nmap -iL filename:扫描filename文件中的所有地址
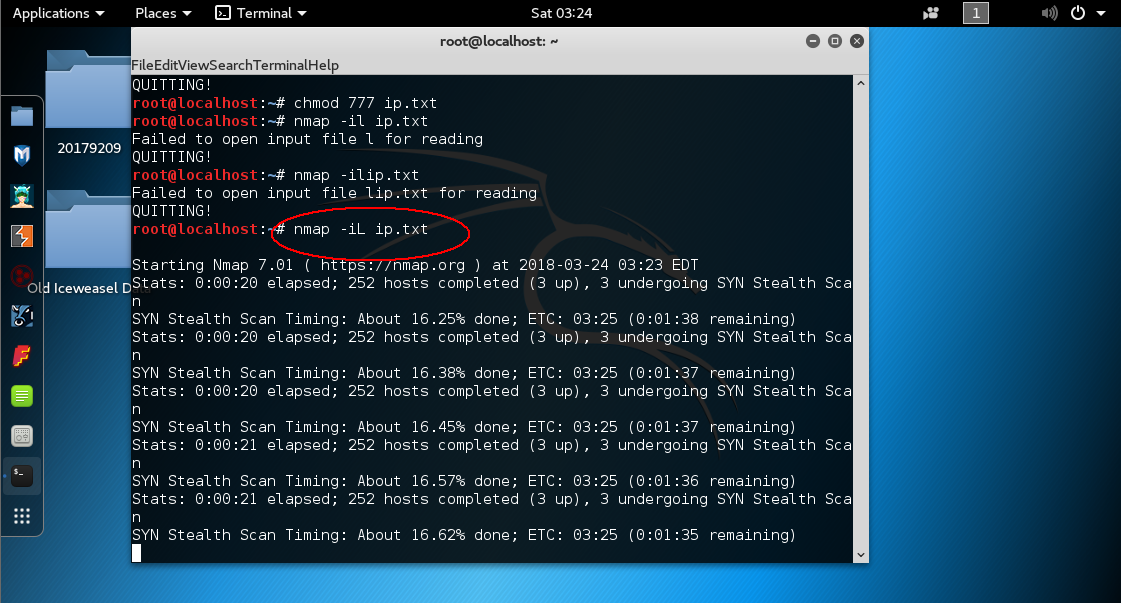
nmap -sT host:全开放扫描
nmap -sS host:半开放扫描
namp -sU host:UDP扫描
nmap -sF host:FIN扫描
nmap -sX host:圣诞树扫描
指纹识别
识别目标主机的操作系统与应用版本,可以帮助我们进一步探测操作系统与应用级别的漏洞。从这些级别进行渗透测试。指纹识别技术多种多样,kali下指纹识别工具有:
- Banner抓取
- 常规主动指纹识别
- 被动指纹识别
- CMS识别
Banner抓取——应用程序指纹识别
Banner抓取是最基础、最简单的指纹识别,不需要专门的工具就可以完成。操作简单,通常获取的信息也相对准确。banner抓取是应用程序指纹识别而不是操作系统识别。
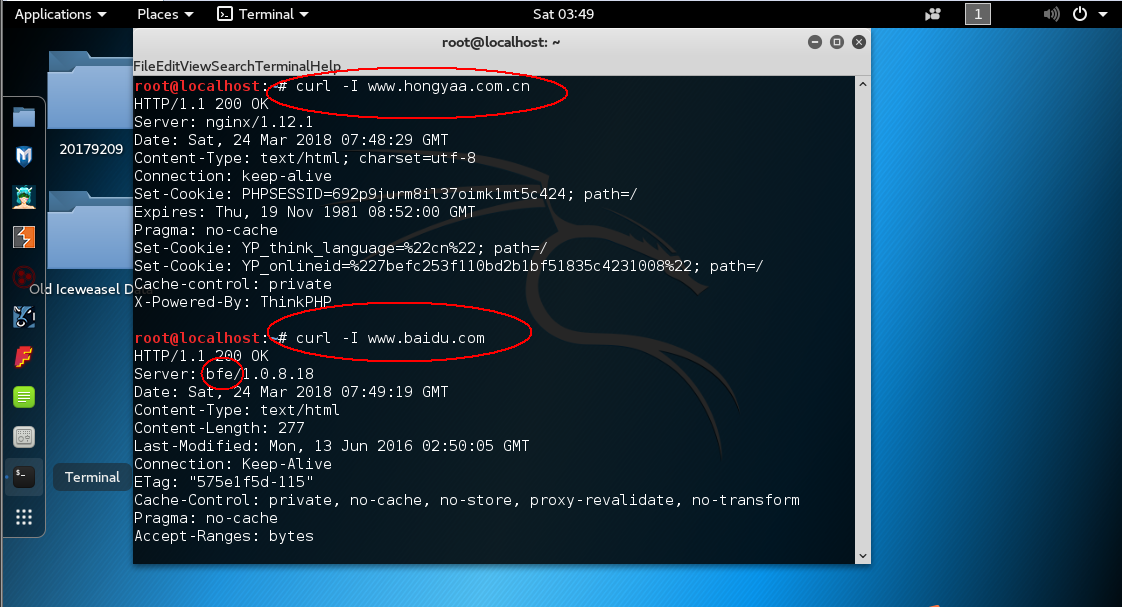
nmap主动探测目标网站指纹信息
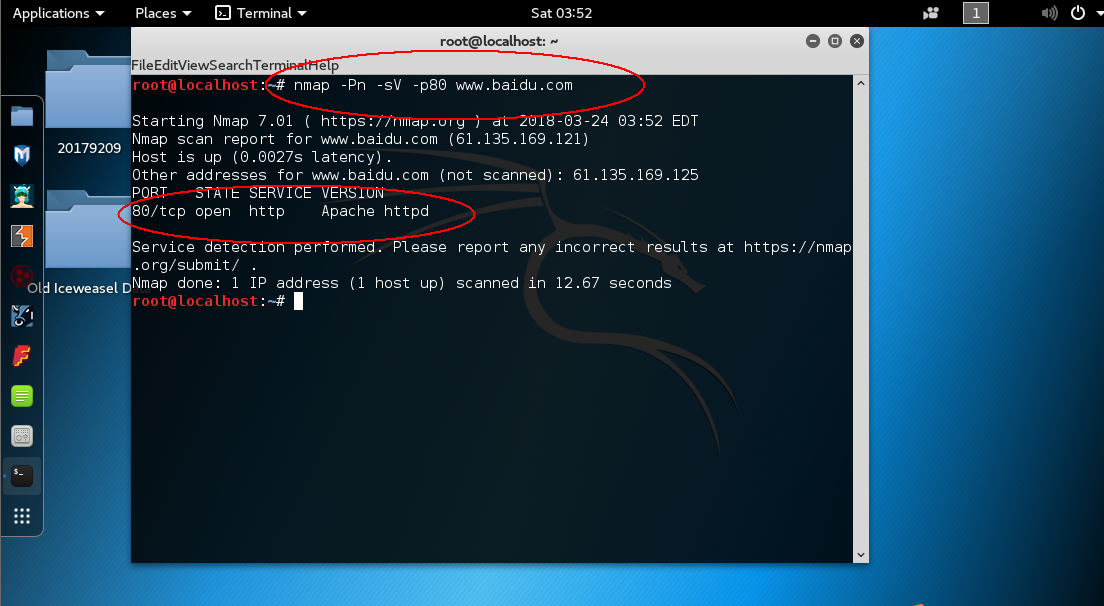
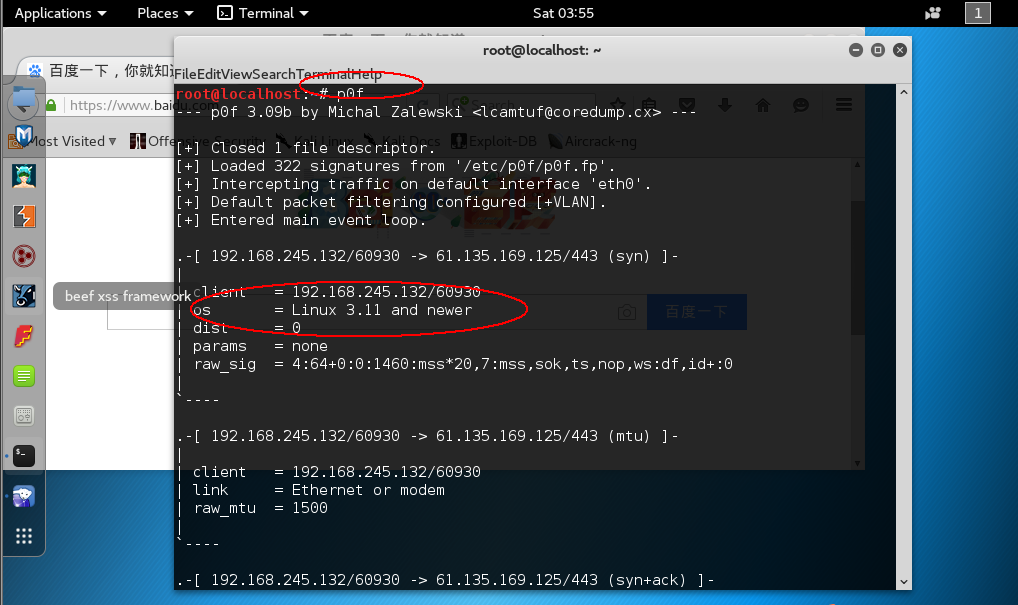
p0f截取网络数据包,分析目标网站信息
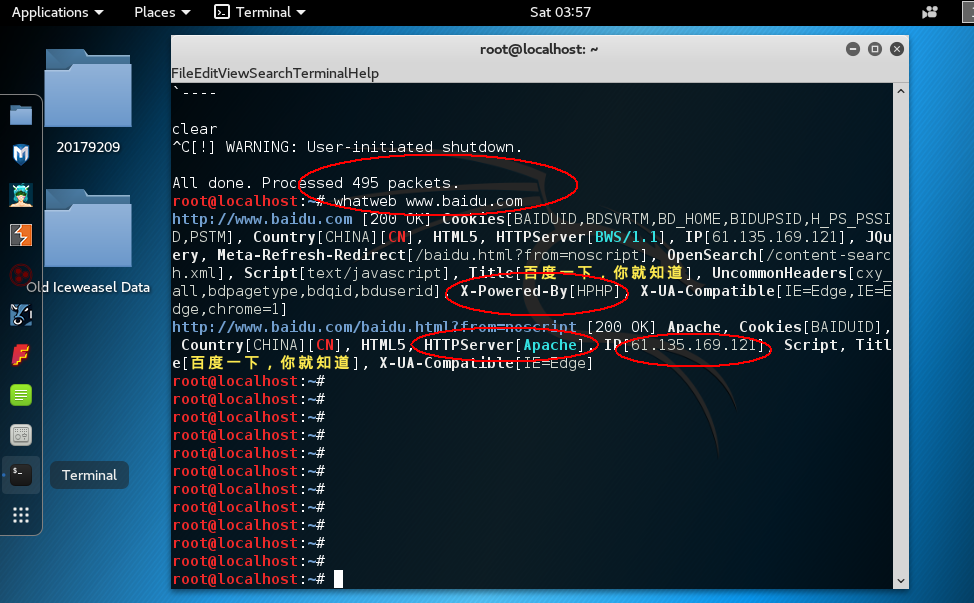
whatweb 命令探测目标网站信息
协议分析
在完成主机探测和扫描,并对主机指纹进行探测分析后,可能还要涉及对具体服务的具体分析。kali提供了很多协议分析工具:
- SMB分析
- SMTP分析
- SNMP分析
- SSL分析
- VoIP分析
- VPN分析
wireshark ,数据包分析必备
Wireshark 是一个网络封包分析软件,网络封包分析软件的功能是获取网络封包,并尽可能显示出最为详细的网络封包信息。wireshark使用WinPCAP作为接口,直接与网卡进行数据报文源文交换。分析wireshark抓取的封包能够帮助使用者对于网络行为有更清楚的了解。wireshark不会对网络封包产生内容的修改,它只会反映出目前流通的封包资讯。wireshark本身也不会送出封包至网络上。
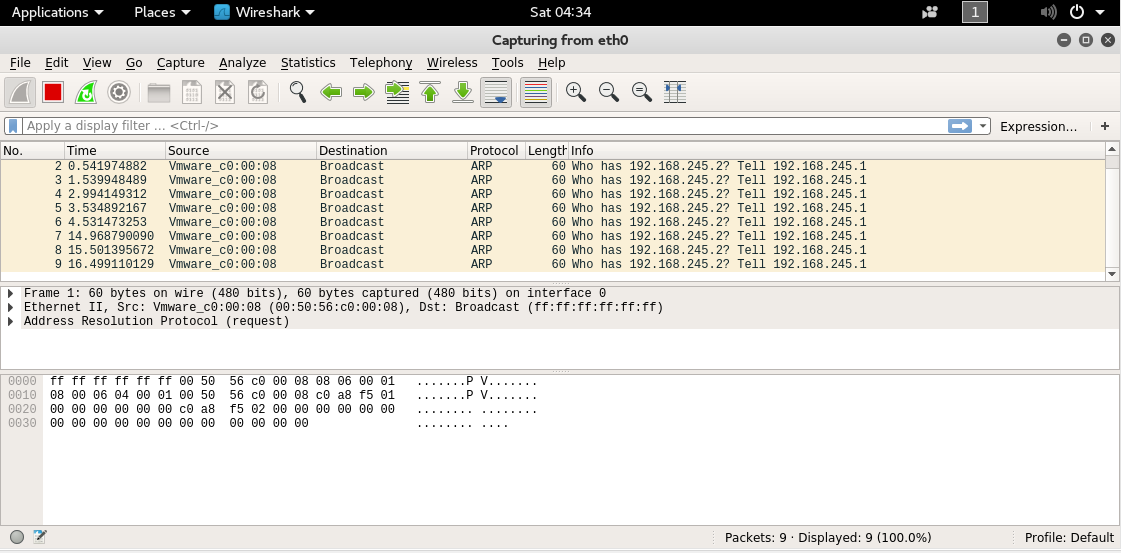
有关wireshark的详细介绍,可以参考之前博客——网络攻防之绪论。里面有关于wireshark的详细介绍,还有抓包以及分析示例。
漏洞分析之OpenVAS
完成前期信息搜集工作后,需要针对性的实施漏洞分析与扫描过程。OpenVAS是kali 下自带的一款综合漏洞扫描器,是一款免费的开放式风险评估工具,可以检测远程系统和应用程序中的安全问题。最初作为Nessus一个子工具,称为GNessus。其特点就是允许继续免费开发。最早由Portcullis Computer Security公司的渗透测试人员发布。
OpenVAS包括一个中央服务器和一个图形化的前端。这个服务器准许用户运行几种不同的网络漏洞测试(以Nessus攻击脚本语言编写),而且OpenVAS可以经常对其进行更新,OpenVAS所有的代码都符合GPL规范。
课后习题:使用nmap和Nessus扫描特定靶机,并给出配置情况、网络服务和漏洞情况
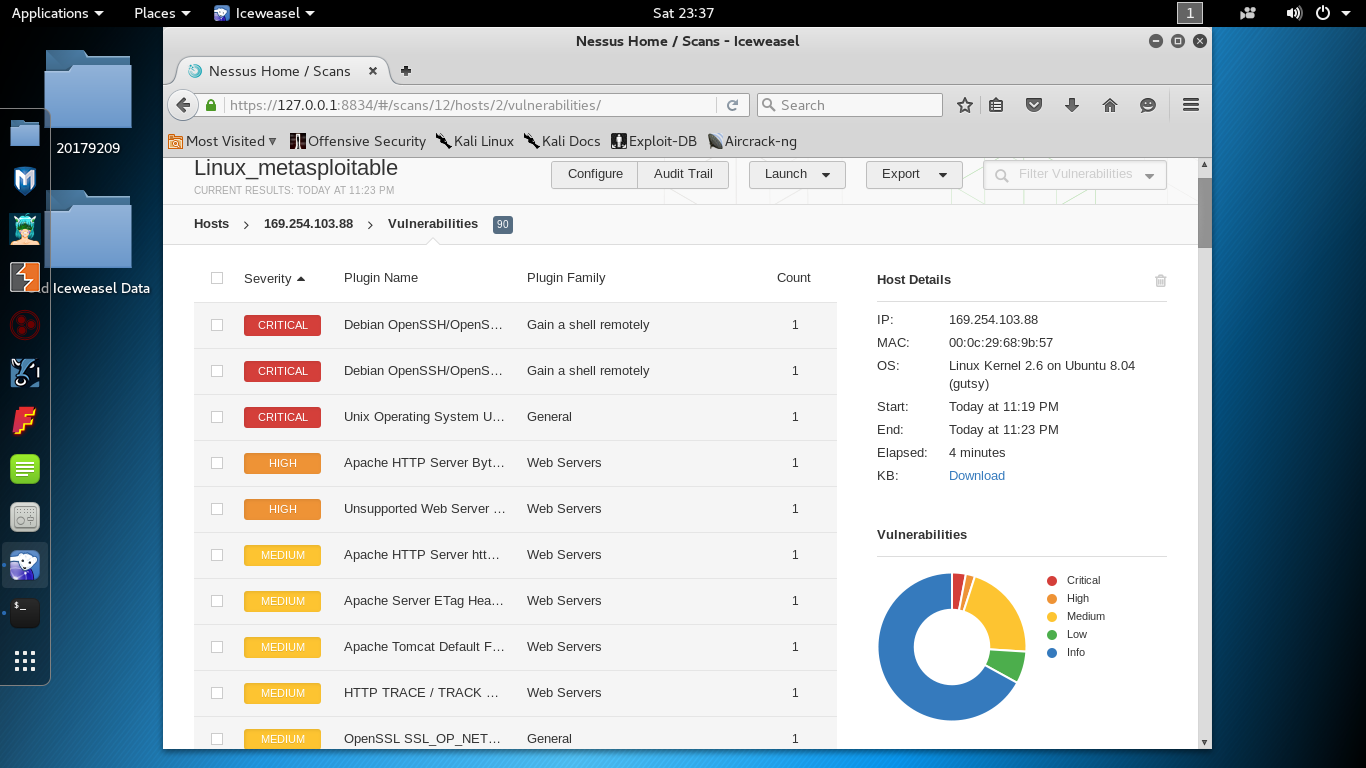
扫描Linux靶机 (ip:169.254.103.88)
nmap扫描结果(nmap -A 169.254.103.88)
Starting Nmap 7.01 ( https://nmap.org ) at 2018-03-24 22:58 EDT
Nmap scan report for 169.254.103.88
Host is up (0.0010s latency).
Not shown: 988 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD 1.3.1
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2018-03-25T02:59:06+00:00; +9s from scanner time.
53/tcp open domain ISC BIND 9.4.2
| dns-nsid:
|_ bind.version: 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) PHP/5.2.4-2ubuntu5.10 with Suhosin-Patch)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.2.8 (Ubuntu) PHP/5.2.4-2ubuntu5.10 with Suhosin-Patch
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 53
| Version: .0.51a-3ubuntu5
| Thread ID: 8
| Capabilities flags: 43564
| Some Capabilities: Speaks41ProtocolNew, Support41Auth, SupportsTransactions, LongColumnFlag, ConnectWithDatabase, SwitchToSSLAfterHandshake, SupportsCompression
| Status: Autocommit
|_ Salt: z54C7(a2snO~PS06]Sh3
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/5.5
MAC Address: 00:0C:29:68:9B:57 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Network Distance: 1 hop
Service Info: Host: metasploitable.localdomain; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| NetBIOS computer name:
| Workgroup: WORKGROUP
|_ System time: 2018-03-24T22:59:05-04:00
TRACEROUTE
HOP RTT ADDRESS
1 1.04 ms 169.254.103.88
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 39.28 seconds从上面可以看到目标主机端口开放情况,开放的服务情况以及服务的详细信息,还有操作系统以及内核版本。
nessus扫描结果
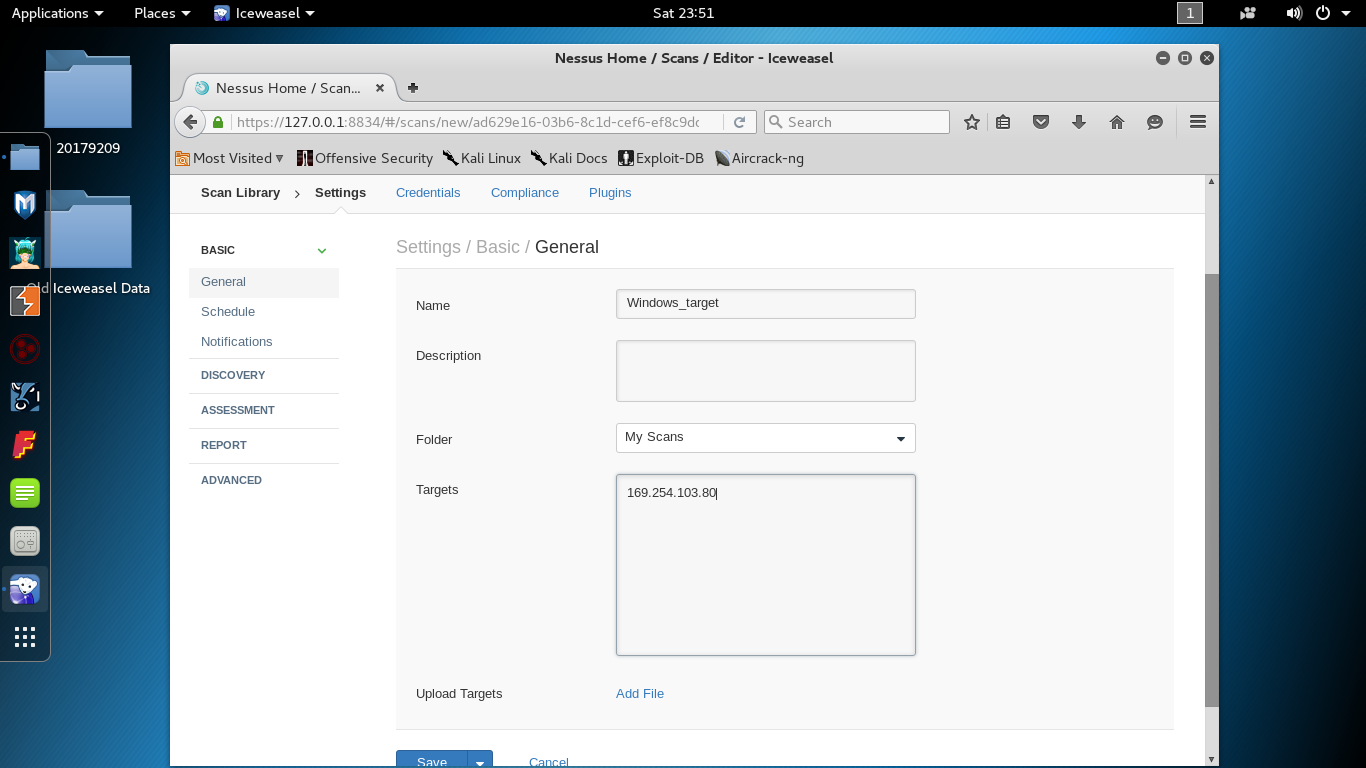
扫描Windows靶机(ip:169.254.103.80)
nmap扫描结果(nmap -A 169.254.103.80)
Starting Nmap 7.01 ( https://nmap.org ) at 2018-03-24 23:44 EDT
Nmap scan report for 169.254.103.80
Host is up (0.00043s latency).
Not shown: 964 closed ports
PORT STATE SERVICE VERSION
7/tcp open echo
9/tcp open discard?
13/tcp open daytime?
17/tcp open qotd Windows qotd (English)
19/tcp open chargen
21/tcp open ftp Microsoft ftpd 5.0
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
25/tcp open smtp Microsoft ESMTP 5.0.2172.1
| smtp-commands: icst-win2k-s Hello [169.254.103.79], AUTH GSSAPI NTLM LOGIN, AUTH=LOGIN, TURN, ATRN, SIZE 2097152, ETRN, PIPELINING, DSN, ENHANCEDSTATUSCODES, 8bitmime, BINARYMIME, CHUNKING, VRFY, OK,
|_ This server supports the following commands: HELO EHLO STARTTLS RCPT DATA RSET MAIL QUIT HELP AUTH TURN ATRN ETRN BDAT VRFY
42/tcp open wins Microsoft Windows Wins
53/tcp open domain Microsoft DNS
80/tcp open http Microsoft IIS httpd 5.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
|_http-server-header: Microsoft-IIS/5.0
|_http-title: \xD5\xFD\xD4\xDA\xBD\xA8\xC1\xA2
| http-webdav-scan:
| WebDAV type: Unkown
| Server Type: Microsoft-IIS/5.0
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_ Server Date: Sun, 25 Mar 2018 03:46:54 GMT
119/tcp open nntp Microsoft NNTP Service 5.00.0984
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows 98 netbios-ssn
443/tcp open https?
445/tcp open microsoft-ds Microsoft Windows 2000 microsoft-ds
515/tcp open printer Microsoft lpd
548/tcp open afp (name: ICST-WIN2K-S; protocol 2.2; MS2.0)
|_afp-serverinfo: ERROR: Script execution failed (use -d to debug)
563/tcp open snews?
1002/tcp open ldap (Anonymous bind OK)
1025/tcp open msrpc Microsoft Windows RPC
1028/tcp open msrpc Microsoft Windows RPC
1029/tcp open msrpc Microsoft Windows RPC
1033/tcp open msrpc Microsoft Windows RPC
1035/tcp open msrpc Microsoft Windows RPC
1038/tcp open msrpc Microsoft Windows RPC
1039/tcp open msrpc Microsoft Windows RPC
1755/tcp open wms?
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
3372/tcp open msdtc Microsoft Distributed Transaction Coordinator
3389/tcp open tcpwrapped
6666/tcp open nsunicast Microsoft Windows Media Unicast Service (nsum.exe)
|_irc-info: Unable to open connection
7007/tcp open tcpwrapped
7778/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port13-TCP:V=7.01%I=7%D=3/24%Time=5AB71B12%P=x86_64-pc-linux-gnu%r(NULL
SF:,13,"11:44:30\x202018-3-25\n");
MAC Address: 00:0C:29:9D:CA:DB (VMware)
Device type: general purpose
Running: Microsoft Windows 2000|XP|Me
OS CPE: cpe:/o:microsoft:windows_2000::- cpe:/o:microsoft:windows_2000::sp2 cpe:/o:microsoft:windows_2000::sp4 cpe:/o:microsoft:windows_xp::- cpe:/o:microsoft:windows_xp::sp1 cpe:/o:microsoft:windows_me
OS details: Microsoft Windows 2000 SP0/SP2/SP4 or Windows XP SP0/SP1, Microsoft Windows 2000 SP1, Microsoft Windows 2000 SP2, Microsoft Windows Millennium Edition (Me)
Network Distance: 1 hop
Service Info: Host: icst-win2k-s; OSs: Windows, Windows 2000, Windows 98; CPE: cpe:/o:microsoft:windows, cpe:/o:microsoft:windows_2000, cpe:/o:microsoft:windows_98
Host script results:
|_nbstat: NetBIOS name: ICST-WIN2K-S, NetBIOS user: ADMINISTRATOR, NetBIOS MAC: 00:0c:29:9d:ca:db (VMware)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
TRACEROUTE
HOP RTT ADDRESS
1 0.43 ms 169.254.103.80
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
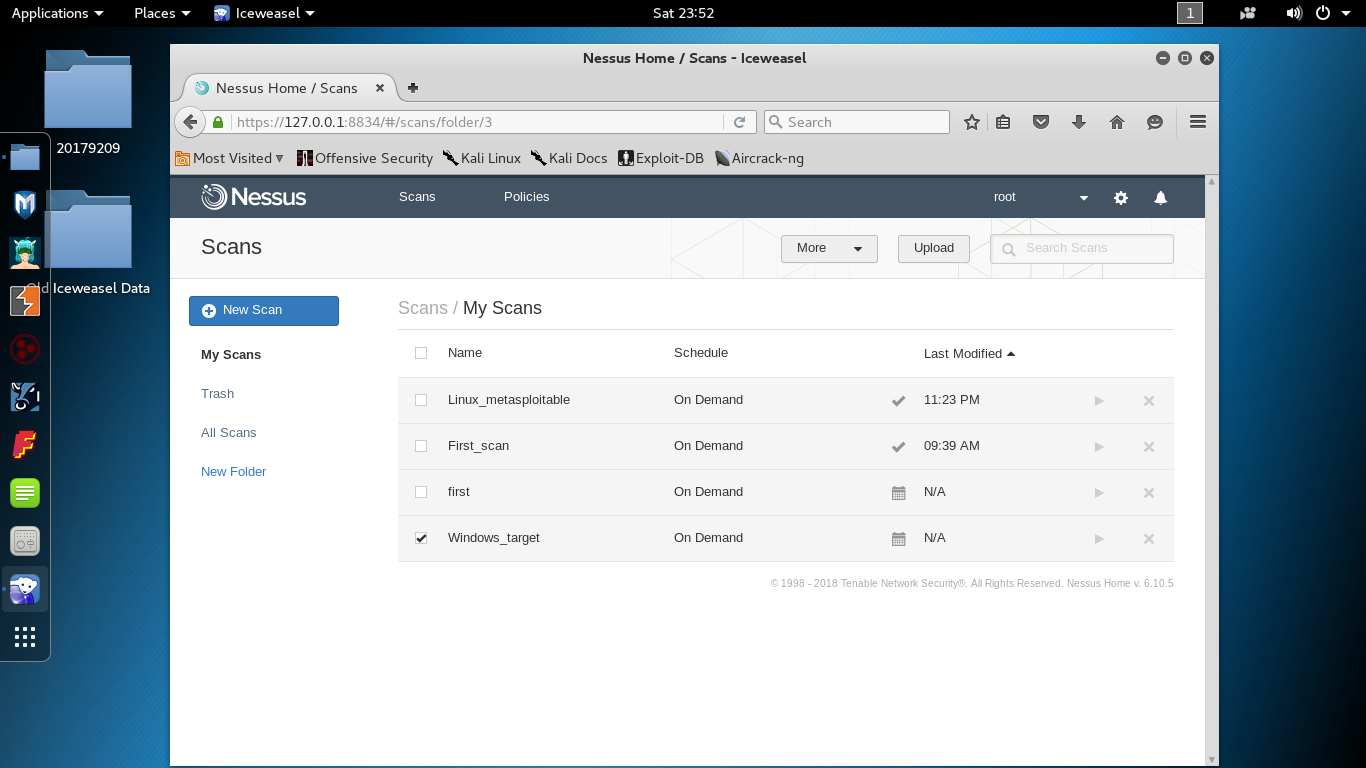
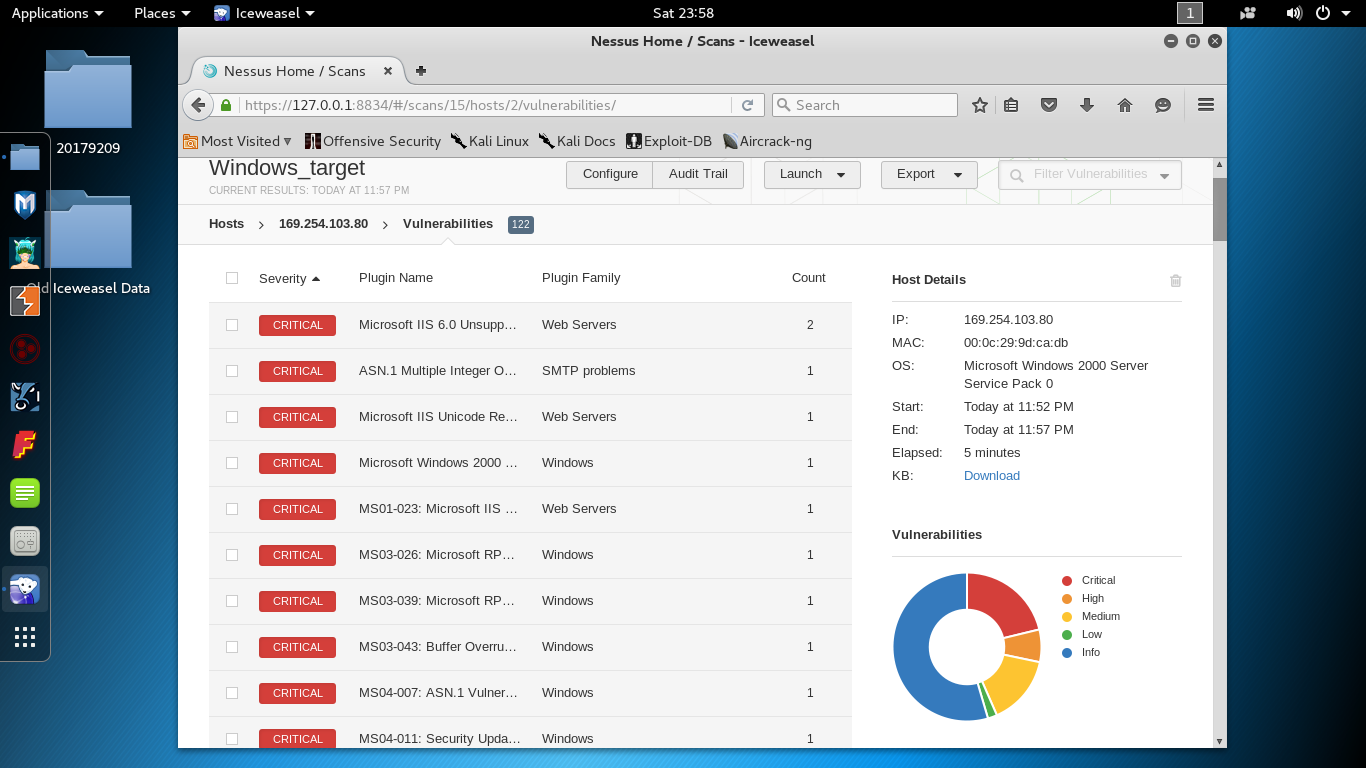
Nmap done: 1 IP address (1 host up) scanned in 222.27 secondsNessus扫描结果




















 1879
1879











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








