When I was reading one of the
last FireEye's post, I was struck by the binary they said it came in the form of phished email (MD5:7c00ba0fcbfee6186994a8988a864385) purportedly from Armani regarding an order. I believe it is interesting to analyze because it could be a real example of an APT or maybe just another spread malware campaign. The techniques used in this real case, could be used in both scenarios...
But FireEye shared the mail's MD5 checksum and they didn't provide us with a copy of the message. Thanks to the
last ContagioDump post, we are able to download all samples and a little more FireEye previously mentioned.
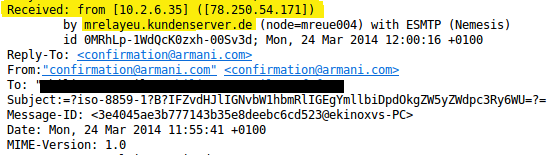
After downloading and opening the message, we can see the details of this mail in the picture bellow. It appears to have been sent by confirmation(at)armani[.]com and contains what appears to be an order with a file attached.

Analysing the SMTP headers
Before opening the file attached, let's see the mail headers to get deep into who really sent the message.We can see the IP (which sent the mail) comes from Paris and the WHOIS description tells us that this IP belongs to a "Wifi Address Pool". Maybe it is a free Wifi or a hacked Wifi where the hackers were connected to send the email, or maybe the host which delivered the mail was infected and was connected to this Wifi when the mail was sent...
By reading the mail headers, we can get more information like the mail's hops. Notice the second one has been blacklisted.
If we continue analyzing the headers we can see something weird...
In the pictures above we can see that the X-sender and the Return-Path belong to a hotel mail account. These fields mean:
- X-Sender: Tell us the real sender directly in the message headers.
- Return-Path: Denotes the real sender but only "post factum".
I've checked that the SMTP servers from which the mail was sent need authorization to send e-mails. Also, the hotel mail account which delivered the mails used the SMTP servers which are hosted in the same hosting provider that the hotel web site is hosted on. So we could assume that this hotel is using these servers to send mail and the mail account could have been stolen. The hackers sent the phished mail from the hotel account but changing the "from" to confirmation(at)armani[.]com
Also we can see that the domain name of the company spoofed doesn't have a
SPF record. That means that it is easier to send an email with the "from" faked. A SPF record prevent spammers from sending messages with forged From addresses. Here you can get more valuable
info about SPF.
Tricking the end user
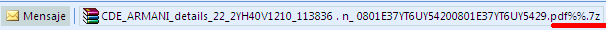
After spending some time digging into the SMTP headers to have further information about the sender, is time to focus on the attachment.It seems an attempt has been made to disguise this file as a PDF file but we noticed that the extension is actually ".7z". If we unzip the file inside the ".7z" file to our Desktop...
...we see that the icon appears to be a PDF file with a weird extension: "pdf%%". We can't see the .exe extension because the "hide extensions for known file types" option is enabled in our Windows. FireEye said that this this file is using RTLO to trick the user but we can't see this technique in the attachment, at least the extension doesn't change... By using RTLO it would be expected to have an extension "exe.pdf" instead of "pdf.exe" which runs as an application, but the attachment doesn't work in this way in our Windows 7. But it doesn't matter, maybe in my next post I will talk about how easy is using RTLO and icon changing to trick a user into opening a file which appears to be a valid document but it is actually malware. That kind of techniques are really used in really attacks like in Siesta Campaign or others ones used like WinRar File extension spoofing.
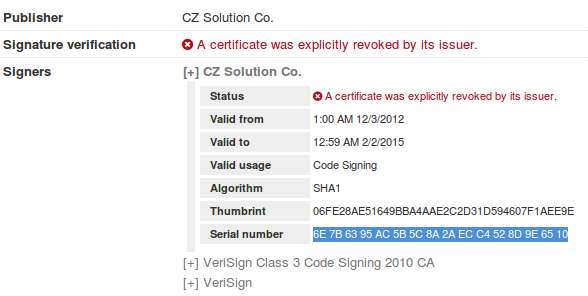
I would like to look at the executable before continuing about how the hackers are trying to trick the user. We notice that this executable is signed with a certificate which has been revoked.
This stolen certificate has been used to bypass the security system of so many security software and devices. Some of them, the first check they do is to discover if the executable is signed, and if it is with a valid certificate, no more security actions are made and the executable is allowed to get into the network. Of course, after the company realized this problem, they revoked the certificate...
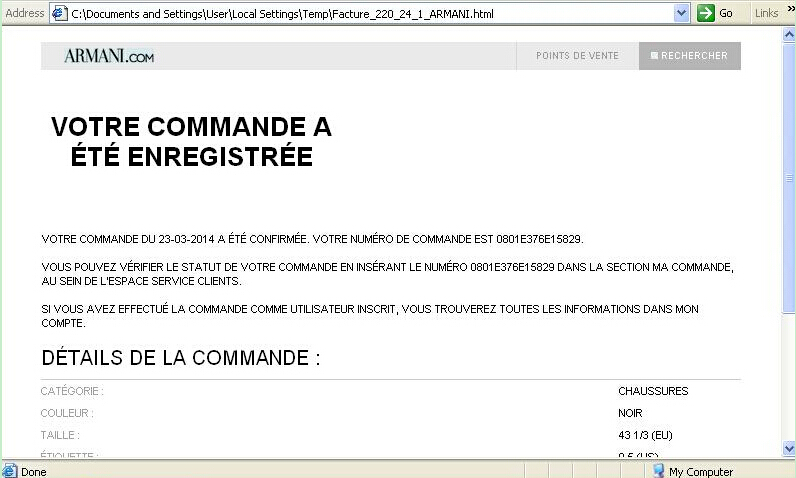
So, what happens if we execute the file which looks like a PDF file?
While the malware is doing evil actions, a web browser is open with the supposed Armani order.
For security guys, these techniques do not go unnoticed to a trained eye, but we can see how it happens every day to the layman.
Also, we have observed how the hacker has tried to disguised the malicious executable as PDF by changing the icon to a PDF picture and maybe using RTLO. Also, after opening the file, a web browser is opened with the apparent order while the malware is doing evil actions.
So, what happens if we execute the file which looks like a PDF file?
While the malware is doing evil actions, a web browser is open with the supposed Armani order.
For security guys, these techniques do not go unnoticed to a trained eye, but we can see how it happens every day to the layman.
Conclusion
Thanks to Fireye and Contagiodump who shared their analysis and samples, we have been able to see how the hacker probably got access to a hotel mail account to start a SPAM campaign and sent a spear phishing attack. They spoofed a mail account of a well know clothes brand. That company doesn't have a SPF record to prevent from being spoofed.Also, we have observed how the hacker has tried to disguised the malicious executable as PDF by changing the icon to a PDF picture and maybe using RTLO. Also, after opening the file, a web browser is opened with the apparent order while the malware is doing evil actions.
Moreover, I've been researching a little more about that case and I've found an advertisement in Facebook https://www.facebook.com/Marnaque/posts/491122357681969 which talks about a similar phished mail. Notice that now they are trying to spoof another clothes brand and they are using a similar body mail using the same order number: 0801E376E15829. We can suspect the same guys are behind that...
VIA:http://www.behindthefirewalls.com/2014/08/have-i-bought-these-clothes-another.html


























 954
954

 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








