一:测试目标:
LDAP简介: LDAP(Lightweight Directory Access Protocol, 是轻量目录访问协议)是跨平台的和标准的协议,使用389号端口。因此应用程序就不用为LDAP目录放在什么样的服务器上操心了。实际上,LDAP得到了业界的广泛认可,因为它是Internet的标准。厂商都很愿意在产品中加入对LDAP的支持,因为他们根本不用考虑另一端(客户端或服务端)是怎么样的。
某企业内部使用Windows的域环境进行统一管理,随着企业移动设备的增多,企业内部需要使用无线网络来满足日益增加的移动性设备的连网需求,要求用户连接无线网络时,使用Windows AD database做认证。并且不同的group有不同的接入权限。
所有无线用户使用web portal方式进行认证,认证的用户帐号使windows AD中的数据库,并且根据AD中用户所处的group属性值进行授权。(不同的group做不同的权限处理)
例如:arubatest组:为企业内网员工,可以访问所有
Arubaguest组:为企业访客,只能访问公网,不能访问企业内网。
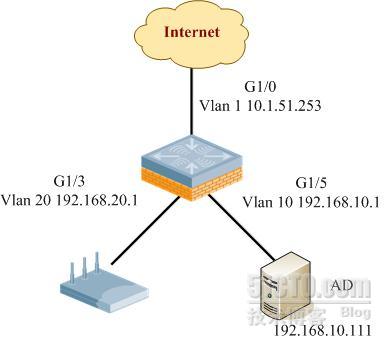
二:测试拓扑:
三:测试设备:
1:IMB T400
笔记本2台,一台安装AD(windows 2003),另一台做测试客户端(windows 7);
2:1
台Aruba 650 controller做NAS;
3:1
颗AP 125。
四:测试过程:
1:AD Server
的安装与配置;
2:controller
的配置;
3:
客户端结果测试。
五:测试总结
--------------------------------------------------------------------------------
|
四:测试过程:
|
|
1:AD Server的安装与配置:
(1):
配置Windows AD 2003 Server ,安装AD。 (域名为test.my3377.com)
(2):
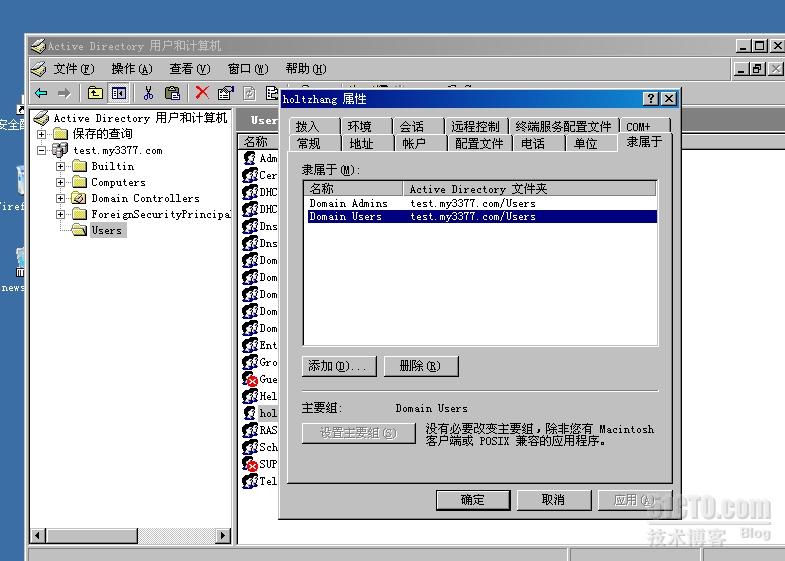
在AD上添加一个管理用户(也可以是用户原有的管理用户,测试为测试添加的管理帐户),添加用户holtzhang,密码123.com,将这个用户隶属于
”
域管理用户
”
。
(3):
在AD上Users新建一个用户组,arubatest和arubaguest。
(4):
在AD上Users新建一个用户
”
holtzhangtest
”
,将此用户隶属于arubatest组,
新建一个用户
”
holtzhangguest
”
,
将此用户隶属于arubaguest组。
属于arubatest组的用户可以访问所有
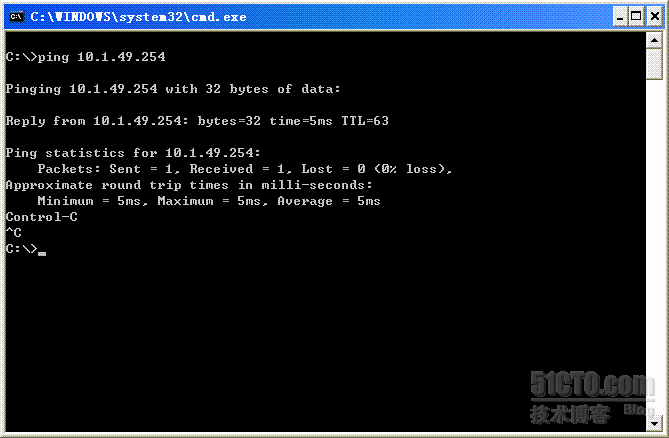
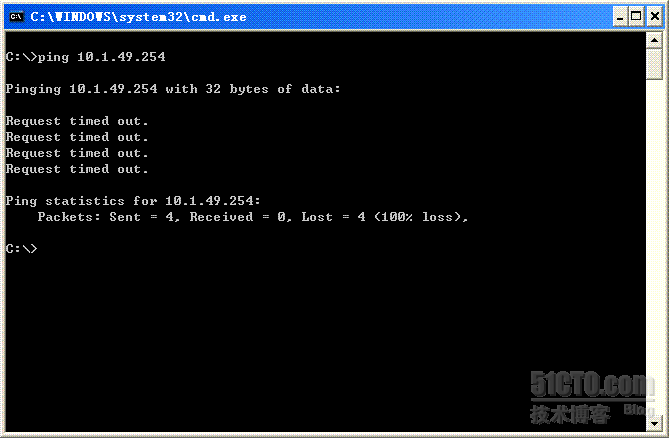
属于arubaguest组的用户不能访问内网,例如: 10.1.49.254,允许访问公网。
密码统一为
”
123.com
”
。
(5):
记住AD的域名(test.my3377.com),在AD端的配置基本完成。
|
|
2: Aruba controller的配置
|
|
|
|
|
|
(1):基础配置
(Aruba650) (config) #vlan 10
(Aruba650) (config) #vlan 20
(Aruba650) (config) #interface vlan 10
(Aruba650) (config-subif)#ip address 192.168.10.1 255.255.255.0
(Aruba650) (config-subif)#no sh
(Aruba650) (config-subif)#operstate up
(Aruba650) (config-subif)#interface vlan 20
(Aruba650) (config-subif)#ip address 192.168.20.1 255.255.255.0
(Aruba650) (config-subif)#no sh
(Aruba650) (config-subif)#operstate up
(Aruba650) #show ip interface brief
Interface IP Address / IP Netmask Admin Protocol
vlan 1 10.1.51.253 / 255.255.255.0 up up
vlan 10 192.168.10.1 / 255.255.255.0 up up
vlan 20 192.168.20.1 / 255.255.255.0 up up
loopback unassigned / unassigned up up
mgmt unassigned / unassigned down down
(Aruba650) (config) #ip default-gateway 10.1.51.254
(Aruba650) #show ip route
Gateway of last resort is 10.1.51.254 to network 0.0.0.0 at cost 1
S* 0.0.0.0/0 [1/0] via 10.1.51.254*
C 10.1.51.0 is directly connected, VLAN1
C 192.168.10.0 is directly connected, VLAN10
C 192.168.20.0 is directly connected, VLAN20
(Aruba650) (config) #interface gigabitethernet 1/3
(Aruba650) (config-if)#switchport access vlan 20
(Aruba650) (config-if)#interface gigabitethernet 1/5
(Aruba650) (config-if)#switchport access vlan 10
(Aruba650) (config-if)#
(Aruba650) #show vlan
VLAN CONFIGURATION
------------------
VLAN Description Ports AAA Profile
---- ----------- ----- -----------
1 Default GE1/0-2 GE1/4 GE1/6-7 Pc0-7 N/A
10 VLAN0010 GE1/5 N/A
20 VLAN0020 GE1/3 N/A
|
|
(Aruba650) (config) #interface vlan 10
(Aruba650) (config-subif)#ip nat inside NAT
的配置
(Aruba650) (config-subif)#interface vlan 20
(Aruba650) (config-subif)#ip nat inside
(Aruba650) (config) #ip dhcp pool vlan20 DHCP
的配置
(Aruba650) (config-dhcp)#network 192.168.20.0 255.255.255.0
(Aruba650) (config-dhcp)#default-router 192.168.20.1
(Aruba650) (config-dhcp)#dns-server 202.106.0.20
(Aruba650) (config-dhcp)#lease 1 1 1 1
(Aruba650) (config-dhcp)#exit
(Aruba650) (config) #service dhcp
启用DHCP服务
(Aruba650) #ping www.baidu.com
发现AC已经能够ping通公网
Press 'q' to abort.
Sending 5, 100-byte ICMP Echos to 127.0.0.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 0.57/0.6702/0.822 ms
|
|
(2)无线配置
<1>:LDAP
的配置
(Aruba650) (config) #aaa authentication-server ldap test-ldap-server
(Aruba650) (LDAP Server "test-ldap-server") #host 192.168.10.111
(Aruba650) (LDAP Server "test-ldap-server") #admin-dn "cn=holtzhang,cn=Users, dc=test,dc=my3377,dc=com"
(Aruba650) (LDAP Server "test-ldap-server") # admin-passwd 123.com
(Aruba650) (LDAP Server "test-ldap-server") # allow-cleartext
(Aruba650)(LDAPServer"test-ldap-server")#base-dn"cn=Users,dc=test,dc=my3377,dc=com"
(Aruba650) (LDAP Server "test-ldap-server") #preferred-conn-type clear-text
(Aruba650) (LDAP Server "test-ldap-server") #exit
|
|
(Aruba650) #show aaa authentication-server ldap test-ldap-server
LDAP Server "test-ldap-server"
------------------------------
Parameter Value
--------- -----
Host 192.168.10.111
Admin-DN cn=holtzhang,cn=Users, dc=test,dc=my3377,dc=com
Admin-Passwd ********
Allow Clear-Text Enabled
Auth Port 389
Base-DN cn=Users, dc=test,dc=my3377,dc=com
Filter (objectclass=*)
Key Attribute sAMAccountName
Timeout 20 sec
Mode Enabled
Preferred Connection Type clear-text
maximum number of non-admin connections 4
端口为默认389
普通名称标示符为sAMAccountName,不用管。
所谓“著名名称”即查询的起点 base_DN,可以在这指定搜索路径,也可以只指定根。
格式为DC=abc,DC=com,按照实际域名为准
注:Aruba controller对中文支持不好,不能识别带有中文字的base_DN。
通过aaa test-server测试在AD上添加的用户holtzhangtest能够通过认证测试。
(Aruba650) #
aaa test-server pap test-ldap-server holtzhangtest 123.com
Authentication Successful
<2>:aaa server-group
的配置
(Aruba650) (config) #aaa server-group captive-portal-server-group
(Aruba650) (Server Group "captive-portal-server-group") #auth-server test-ldap-server
(Aruba650) (Server Group "captive-portal-server-group") #set role condition role value-of
(Aruba650) (Server Group "captive-portal-server-group") #exit
<3>: aaa authentication
的相关配置
(Aruba650) (config) #aaa authentication captive-portal ht-captive-aaa-auth-profile
(Aruba650) (Captive Portal Authentication Profile "ht-captive-aaa-auth-pro#server-group captive-portal-server-group
(Aruba650) (Captive Portal Authentication Profile "ht-captive-aaa-auth-pro#exit
<4>: captive-portal
的初始化角色的配置
(Aruba650) (config) #user-role ht-captive-portal-role
(Aruba650) (config-role) #session-acl logon-control
(Aruba650) (config-role) #session-acl captiveportal
(Aruba650) (config-role) #session-acl ***logon
(Aruba650) (config-role) #captive-portal ht-captive-aaa-auth-profile
(Aruba650) (config-role) #exit
|
|
<5>:
aaa profile
的配置
(Aruba650) (config) #aaa profile ht-captive-aaa-profile
(Aruba650) (AAA Profile "ht-captive-aaa-profile") #initial-role ht-captive-portal-role
(Aruba650) (AAA Profile "ht-captive-aaa-profile") #exit
6:
wlan ssid profile
的配置
(Aruba650) (config) #wlan ssid-profile guest-ssid-profile
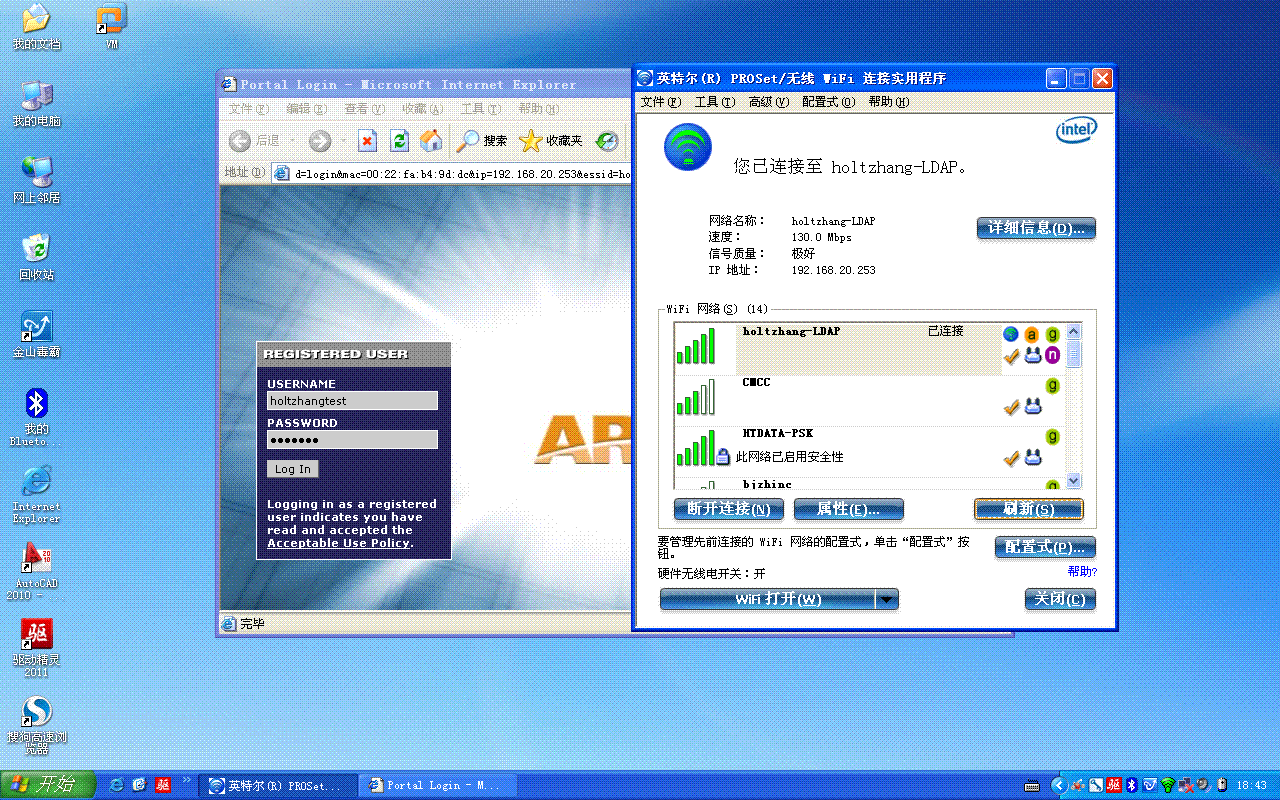
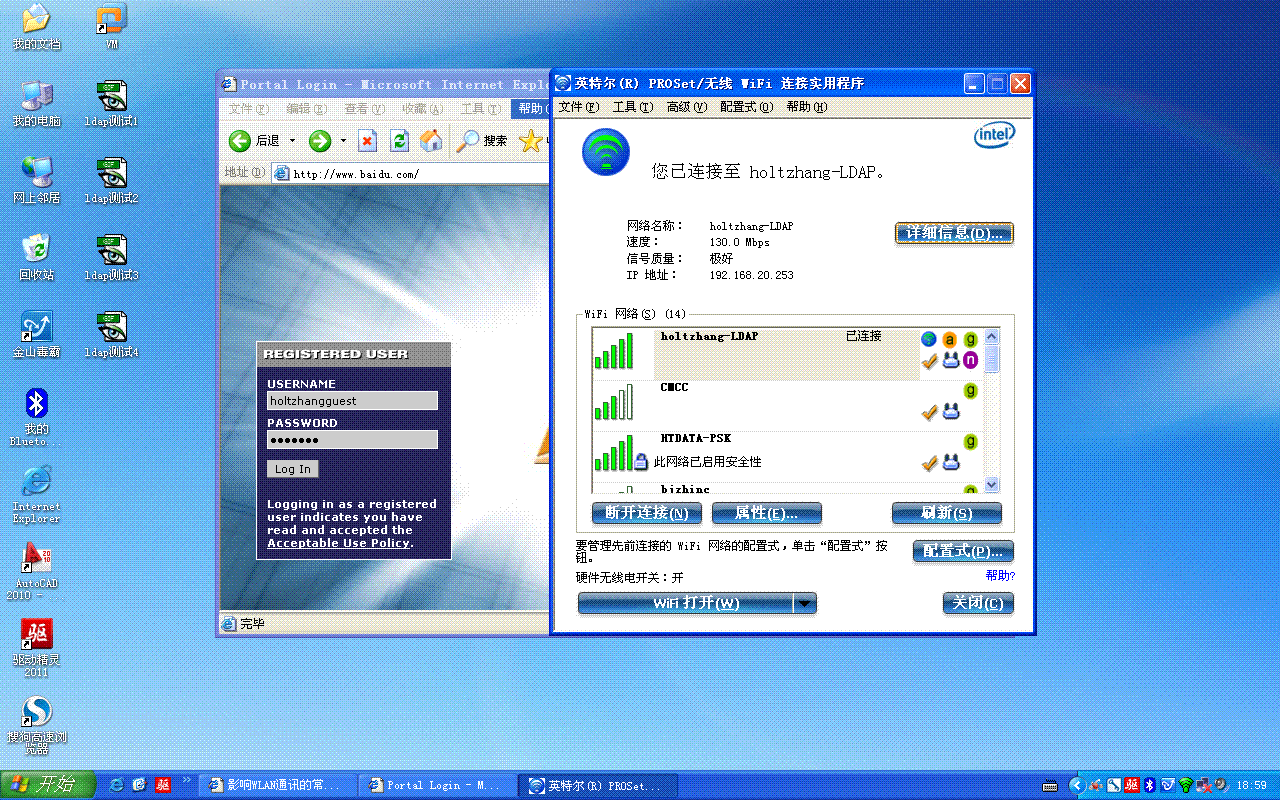
(Aruba650) (SSID Profile "guest-ssid-profile") #essid holtzhang-LDAP
(Aruba650) (SSID Profile "guest-ssid-profile") #exit
7:
wlan virtual-ap profile
的配置
(Aruba650) (config) #wlan virtual-ap guest-vap-profile
(Aruba650) (Virtual AP profile "guest-vap-profile") #aaa-profile ht-captive-aaa-profile
(Aruba650) (Virtual AP profile "guest-vap-profile") #ssid-profile guest-ssid-profile
(Aruba650) (Virtual AP profile "guest-vap-profile") #vlan 20
(Aruba650) (Virtual AP profile "guest-vap-profile") #exit
8:
将virtual-ap调用到ap-group使其生效
(Aruba650) (config) #ap-group default
(Aruba650) (AP group "default") #virtual-ap guest-vap-profile
(Aruba650) (AP group "default") #exit
定义用户拨入的role
(Aruba650) (config) #ip access-list session arubatest111
(Aruba650) (config-sess-arubatest111)#any any any permit
(Aruba650) (config-sess-arubatest111)#exit
(Aruba650) (config) #ip access-list session arubaguest111
(Aruba650) (config-sess-arubaguest111)#network 192.168.20.0 255.255.255.0 network 10.1.49.0 255.255.255.0 any deny
(Aruba650) (config-sess-arubaguest111)#network 192.168.20.0 255.255.255.0 any any permit
(Aruba650) (config-sess-arubaguest111)#exit
(config) #user-role arubatest
(Aruba650) (config-role) #access-list session arubatest111
(Aruba650) (config-role) #exit
(Aruba650) (config) #user-role arubaguest
(Aruba650) (config-role) #access-list session arubaguest111
(Aruba650) (config-role) #exit
|
|
(Aruba650) #aaa query-user test-ldap-server holtzhangtest
//查看用户从AD查询后返回的值
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: holtzhangtest
sn: holtzhangtest
distinguishedName: CN=holtzhangtest,CN=Users,DC=test,DC=my3377,DC=com
instanceType: 4
whenCreated: 20120222100800.0Z
whenChanged: 20120222100800.0Z
displayName: holtzhangtest
uSNCreated: 13931
memberOf: CN=arubatest,CN=Users,DC=test,DC=my3377,DC=com
(如果用户属于不同的组,则返回的改属性不同。)
uSNChanged: 13937
name: holtzhangtest
objectGUID: \324\344oP\261J\012H\203l\316\231\315\341w\361
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 129743788803116250
primaryGroupID: 513
objectSid: \001\005
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: holtzhangtest
sAMAccountType: 805306368
userPrincipalName: holtzhangtest@test.my3377.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=test,DC=my3377,DC=com
|
|
(Aruba650) #aaa query-user test-ldap-server holtzhangguest
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: holtzhangguest
sn: holtzhangguest
distinguishedName: CN=holtzhangguest,CN=Users,DC=test,DC=my3377,DC=com
instanceType: 4
whenCreated: 20120222100819.0Z
whenChanged: 20120222100819.0Z
displayName: holtzhangguest
uSNCreated: 13939
memberOf: CN=arubaguest,CN=Users,DC=test,DC=my3377,DC=com
uSNChanged: 13945
name: holtzhangguest
objectGUID: '\366Z\256x\005\212O\266B5\020i\0262]
userAccountControl: 66048
badPwdCount: 0
codePage: 0
countryCode: 0
badPasswordTime: 0
lastLogoff: 0
lastLogon: 0
pwdLastSet: 129743788993272500
primaryGroupID: 513
objectSid: \001\005
accountExpires: 9223372036854775807
logonCount: 0
sAMAccountName: holtzhangguest
sAMAccountType: 805306368
userPrincipalName: holtzhangguest@test.my3377.com
objectCategory: CN=Person,CN=Schema,CN=Configuration,DC=test,DC=my3377,DC=com
|
|
可以观察上述返回属性,通过选取在AD上各个组不同的属性来给controller进行role的匹配。在本次测试中选用了红色字体的部分,即使用返回不同的组属性做为条件让controller进行权限的分配。
//在AC上通过用户返回的组数属性进行授权
(Aruba650) (config) #aaa server-group captive-portal-server-group
(Aruba650)(ServerGroup"captive-portal-server-group")
#
set role condition memberof equals CN=arubatest,CN=Users,DC=test,DC=my3377,DC=com set-value
arubatest
(Aruba650) (Server Group "captive-portal-server-group")
#
set role condition memberof equals CN=arubaguest,CN=Users,DC=test,DC=my3377,DC=com set-value
arubaguest
(Aruba650) (Server Group "captive-portal-server-group") #exit
(Aruba650) #show aaa server-group captive-portal-server-group
1 role value-of String set role No
2 memberof equals CN=arubaguest,CN=Users,DC=test,DC=my3377,DC=com String set role arubaguest No
3 memberof equals CN=arubatest,CN=Users,DC=test,DC=my3377,DC=com String set role arubatest No
|
|
|
|
发现holtzhangguest用户可以访问公网,但不可以访问内网。(跟我们在AC上配置的role权限完全匹配。)
|
五:测试总结
测试时间:2012.2.23号
|
其它无线厂家
|
Aruba
|
|
其它无线厂家controller可以做到基于LDAP认证,但不能通过LDAP返回的用户属性值进行权限的分配。
|
其它无线厂家可以做到基于LDAP认证,可以通过LDAP返回的用户属性值进行权限的分配。
|
|
|
但此处注意,不支持中文OU,不支持中文group,不支持中文user。
|
目前各大厂家controller基本都支持LDAP认证,但不能基于LADP做授权,Aruba目前可以基于LADP做认证和授权,但只支持英文认证和授权.
六:参考资料:
转载于:https://blog.51cto.com/holtzhang/789672





















 911
911











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








