Lab 31: Configuring Dynamic NAT and Using Non−Standard FTP Port
Numbers
Numbers
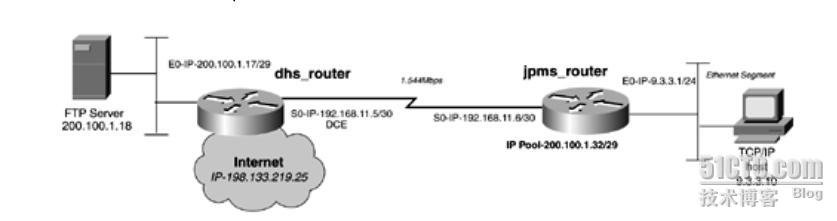
Configure the network so that the workstations on the subnet 9.3.3.0/24 can access to the Internet, while restricting access to the 200.100.1.16/29 subnet.
Control access so that NAT works to the Internet, but only NAT ICMP and FTP when traffic is destined toward the host 200.100.1.18.
Use the CIDR block of 200.100.1.32/29 for your address pool.
Optional: Configure FTP to work on port 2021 instead of port 21.
Optional: Configure FTP to work on port 2021 instead of port 21.
只需在Jpms_router上配置
Jpms_router
conf t
host Jpms_router
conf t
host Jpms_router
ip route 0.0.0.0 0.0.0.0 192.168.11.5
int f 0/0
ip ad 9.3.3.1 255.255.255.0
ip nat inside
no shut
int l 0
ip ad 200.100.1.33 255.255.255.248
int s 2/0
ip ad 192.168.11.6 255.255.255.252
ip nat outside
no shut
exit
ip nat service list 1 ftp tcp port 2001
access-list 1 permit 200.100.1.18
access-list 100 deny ip 9.3.3.0 0.0.0.255 200.100.1.16 0.0.0.7
access-list 100 permit ip 9.3.3.0 0.0.0.255 any
access-list 100 permit icmp 9.3.3.0 0.0.0.255 host 200.100.1.18
access-list 100 permit tcp 9.3.3.0 0.0.0.255 host 200.100.1.18 eq 2001
int f 0/0
ip ad 9.3.3.1 255.255.255.0
ip nat inside
no shut
int l 0
ip ad 200.100.1.33 255.255.255.248
int s 2/0
ip ad 192.168.11.6 255.255.255.252
ip nat outside
no shut
exit
ip nat service list 1 ftp tcp port 2001
access-list 1 permit 200.100.1.18
access-list 100 deny ip 9.3.3.0 0.0.0.255 200.100.1.16 0.0.0.7
access-list 100 permit ip 9.3.3.0 0.0.0.255 any
access-list 100 permit icmp 9.3.3.0 0.0.0.255 host 200.100.1.18
access-list 100 permit tcp 9.3.3.0 0.0.0.255 host 200.100.1.18 eq 2001
route-map NAT permit 10
match ip ad 100
exit
ip nat inside source route-map NAT pool POOL
ip nat pool POOL 200.100.1.33 200.100.1.38 netmask 255.255.255.248
end
match ip ad 100
exit
ip nat inside source route-map NAT pool POOL
ip nat pool POOL 200.100.1.33 200.100.1.38 netmask 255.255.255.248
end
Lab 32: Configuring Static NAT
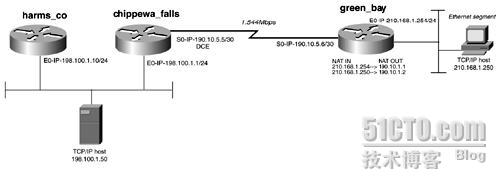
Configure the network as depicted in Figure 15−7. Configure the network with EIGRP as the routing
protocol. Use an autonomous System ID of 7.
Configure green_bay so that the router does not circulate the new subnet of 210.168.1.0/24 in EIGRP.
Configure static translations as follows:
− 210.168.1.254 translates to 190.10.1.1
− 210.168.1.250 translates to 190.10.1.2
− 210.168.1.254 translates to 190.10.1.1
− 210.168.1.250 translates to 190.10.1.2
Green_bay
conf t
host Green_bay
int f 0/0
ip ad 210.168.1.254 255.255.255.0
no shut
ip nat inside
int s2/0
ip ad 190.10.5.6 255.255.255.252
no shut
ip nat outside
exit
router eigrp 7
no au
net 190.10.5.6 0.0.0.0
exit
ip nat inside source static 210.168.1.254 190.10.1.1
ip nat inside source static 210.168.1.250 190.10.1.2
end
conf t
host Green_bay
int f 0/0
ip ad 210.168.1.254 255.255.255.0
no shut
ip nat inside
int s2/0
ip ad 190.10.5.6 255.255.255.252
no shut
ip nat outside
exit
router eigrp 7
no au
net 190.10.5.6 0.0.0.0
exit
ip nat inside source static 210.168.1.254 190.10.1.1
ip nat inside source static 210.168.1.250 190.10.1.2
end
本文出自 “
穿过地狱去看海” 博客,谢绝转载!
本文出自 51CTO.COM技术博客
转载于:https://blog.51cto.com/290083365/94462




















 64
64











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








