基于PKI的IPSec LAN-TO-LAN ×××
概述... 2
两个对等体之间的认证:... 2
一.实验目的... 3
二.实验拓扑... 3
三.实验要求... 4
四.实验步骤... 4
1.基本配置... 4
2.准备工作... 6
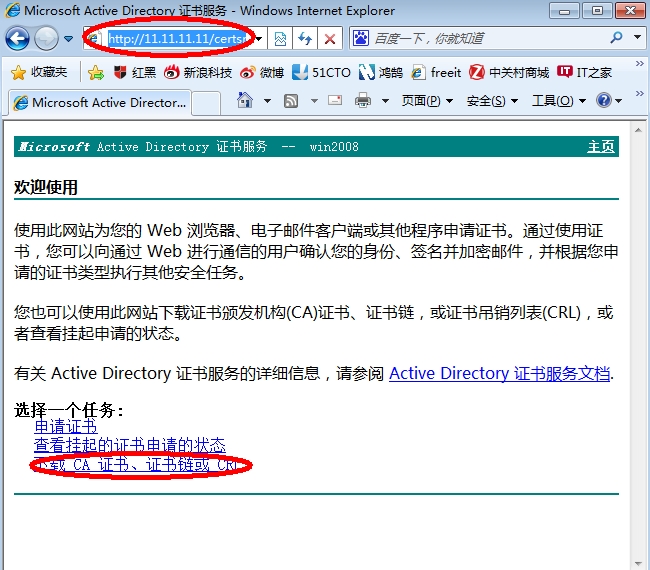
3.CA搭建... 6
4.证书申请... 12
5.IPSec ×××配置... 26
五.实验总结... 31
概述
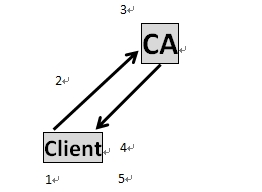
利用PKI,即证书加密实现的IPSec ×××被视为最安全的×××认证加密方式。那么,Client是怎样向CA申请证书的呢?
步骤:
客户端产生一对RSA密钥(申请证书时系统要求);
客户端把个人信息(客户端标示、所属部门、邮箱、电话等)和公钥一起打包发给CA-
CA拿到“个人”信息+Pub之后,进行HASH算法,得到一个HASH值,然后加上自己的信息生成一个证书,最后用自己的私钥对这个证书进行加密(数字签名);
CA把加密后的证书发送给客户端;
客户端收到证书(已经用CA的私钥进行加密),然后下载CA的根证书进行解密,得到自己申请的证书。
注:客户端下载根证书有三个作用
验证CA是否可信;
使用CA的公钥解密私钥;
对等体身份验证时,A可以下载B的CA的根证书,验证B的IPSec证书。
注:私钥加密公钥解密属于数字签名
公钥加密私钥解密属于非对称加密算法
两个对等体之间的认证:
在使用PSK(预共享密钥)进行对等体认证时,两边的PSK设置一样就能认证成功。那么使用PKI时怎样进行认证的呢?
每台设备都要向CA申请自己的IPSec证书,然后进行认证加密。但是甲、乙两个对等体的证书是不一样的,要怎样认证呢?此时,乙方就需要向甲方的CA申请其根证书,用于验证甲方的证书,对其信任并成功完成认证。
一. 实验目的
理解IPSec ×××使用PKI加密的意义;
理解PKI加密后的×××安全特性;
掌握PKI加密的×××的实施与配置;
理清实验过程中的重难点(证书的申请),并学会解决遇到的问题。
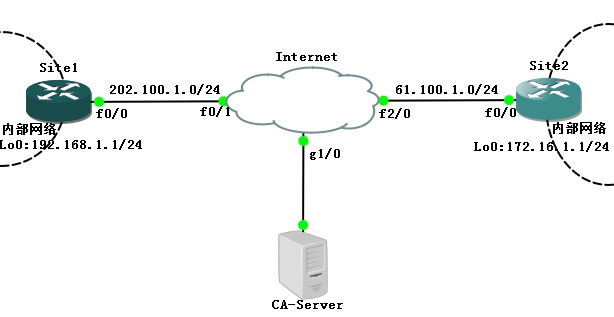
二.实验拓扑
说明:本实验利用GNS3完成,所有路由器包括Internet都使用7200的镜像。Site1和site2模拟两个公司。两个站点利用×××技术,可以实现内部网络(site1与site2的Lo0接口)的互通。当然Internet上不能有两个site内部网络的路由(因为真实环境中ISP的路由器上是不可能出现私有IP的)。配置完成之前,两个站点之间的内部网络是不能通信的,完成之后可以实现通信。当然,本实验的×××加密不再使用PSK(预共享密钥)的加密方式,而是使用更加安全的PKI(证书加密)的方式。当然,实现证书要有证书服务器。所以我们桥接一台win 2008服务器来模拟证书办法机构。
三.实验要求
最终的实验要求是:两个站点的内部网络能够彼此通信(即私网网段之间可以通信)。
四.实验步骤
1.基本配置
实验开始前,先把基本的IP配好,做好准备工作
Site1配置
Site1(config)#inter fa0/0 Site1(config-if)#ip add 202.100.1.1 255.255.255.0 Site1(config-if)#no shut Site1(config-if)#inter loo0 Site1(config-if)#ip add 192.168.1.1 255.255.255.0 Site1(config-if)#no shut Site1(config-if)#exit Site1(config)#ip route 0.0.0.0 0.0.0.0 202.100.1.254 //此缺省路由指向Internet。 |
Site2配置
Site2(config)#inter fa0/0 Site2(config-if)#ip add 61.100.1.1 255.255.255.0 Site2(config-if)#no shut Site2(config-if)#inter loo0 Site2(config-if)#ip add 172.16.1.1 255.255.255.0 Site2(config-if)#no shut Site2(config-if)#exit Site2(config)#ip route 0.0.0.0 0.0.0.0 61.100.1.254 |
Internet配置
Internet(config)#inter fa0/1 Internet(config-if)#ip add 202.100.1.254 255.255.255.0 Internet(config-if)#no shut Internet(config-if)#inter fa2/0 Internet(config-if)#ip add 61.100.1.254 255.255.255.0 Internet(config-if)#no shut Internet(config)#inter g1/0 Internet(config-if)#ip add 11.11.11.254 255.255.255.0 Internet(config-if)#no shut Internet(config-if)#exit |
CA-Server配置
C:\>ipconfig
Windows IP 配置
以太网适配器 本地连接:
连接特定的 DNS 后缀 . . . . . . . : IPv4 地址 . . . . . . . . . . . . : 11.11.11.11 子网掩码 . . . . . . . . . . . . : 255.0.0.0 默认网关. . . . . . . . . . . . . : 11.11.11.254 |
验证两个站点到CA-server的连通性
Site1#ping 11.11.11.11
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 11.11.11.11, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 32/52/80 ms
Site2#ping 11.11.11.11
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 11.11.11.11, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 28/56/92 ms |
注:site在ping用win2008模拟的ca服务器时,服务器的防火墙记得关闭,否则ping不通。
2.准备工作
×××应用PKI加密模式,加密站点路由器要申请证书。而向CA申请证书要保证client与server之间时区一致,时间一样(当然可以差别十几秒的范围),否则申请证书不能成功。
eg:Site1配置
Site1#clock set 20:27:25 Oct 15 2014 Site1(config)#clock timezone GTM +8 |
3.CA搭建
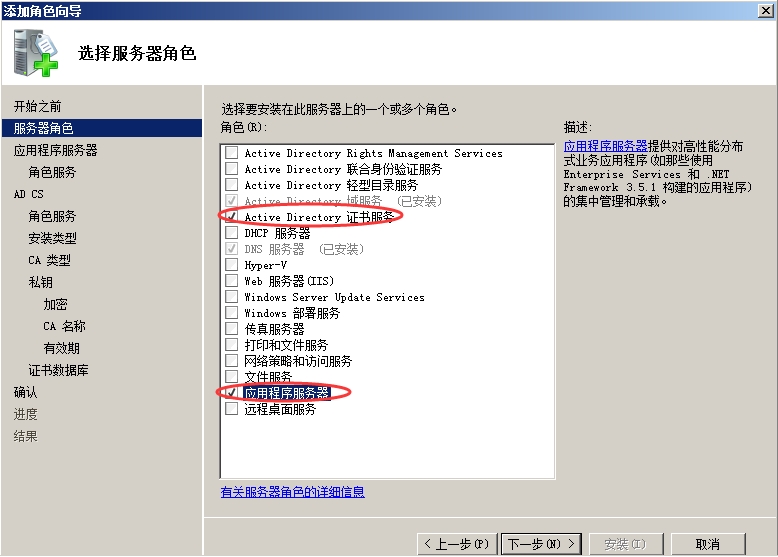
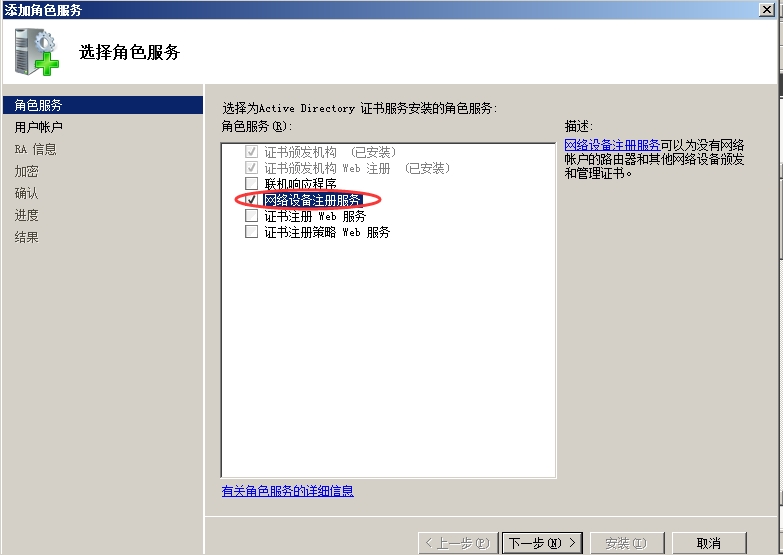
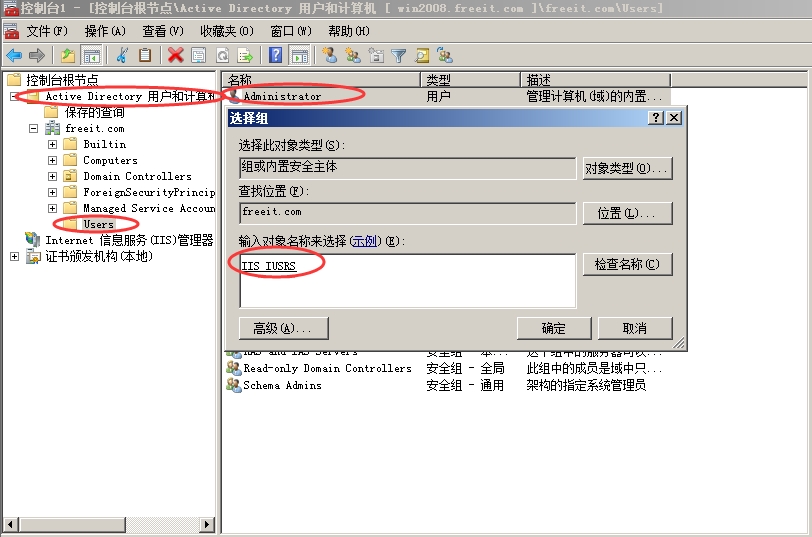
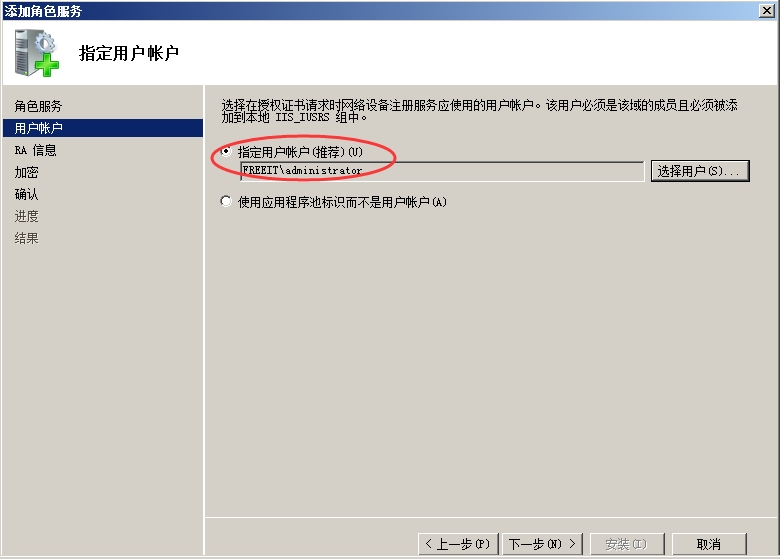
我们要用到CA服务器的一个网络设备注册服务。路由器申请证书时要用到一个MSCEP的协议(微软简单证书申请协议)。所以搭建完CA,还要加上网络设备注册服务。
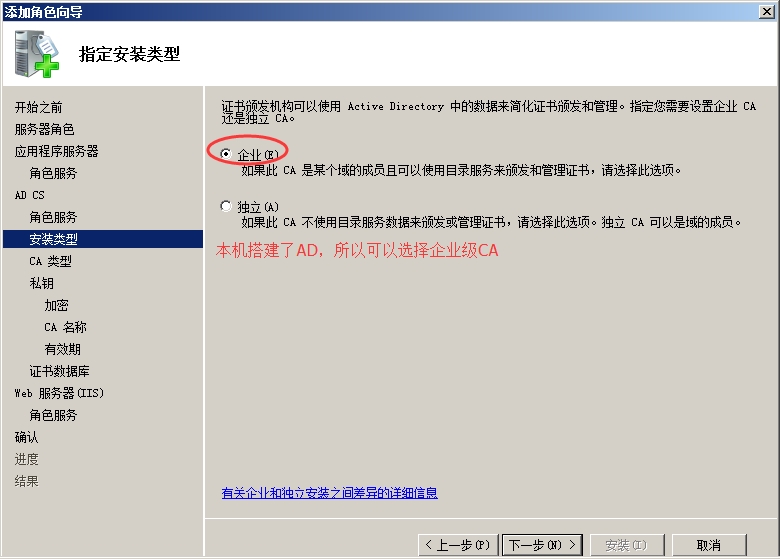
服务器管理器---角色---右键【添加角色】
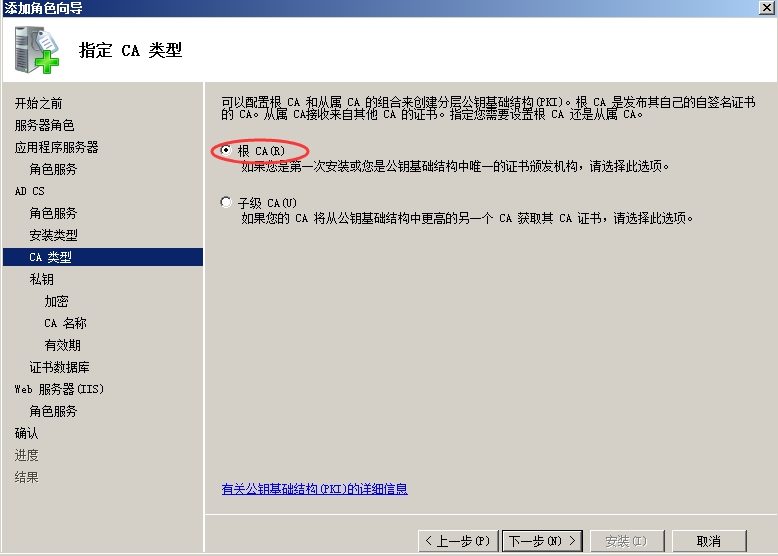
一路下一步,到此
一路下一步,点击安装。
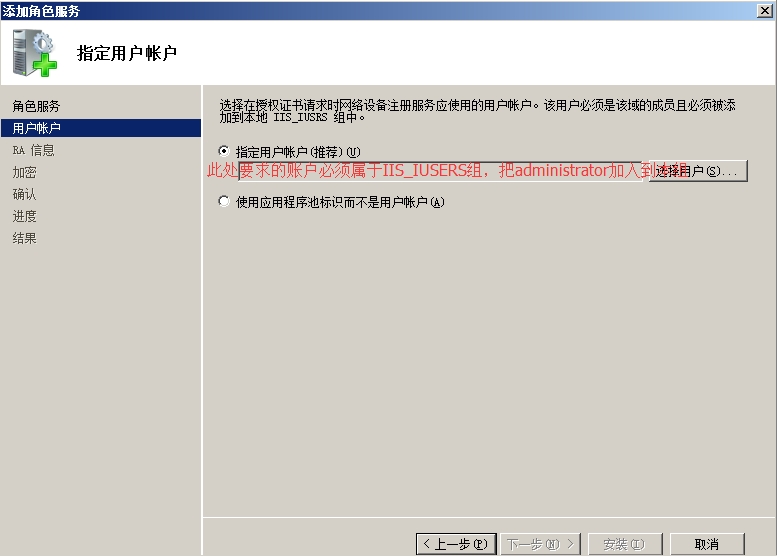
然后右键点击AD证书服务—添加角色
一路下一步,安装
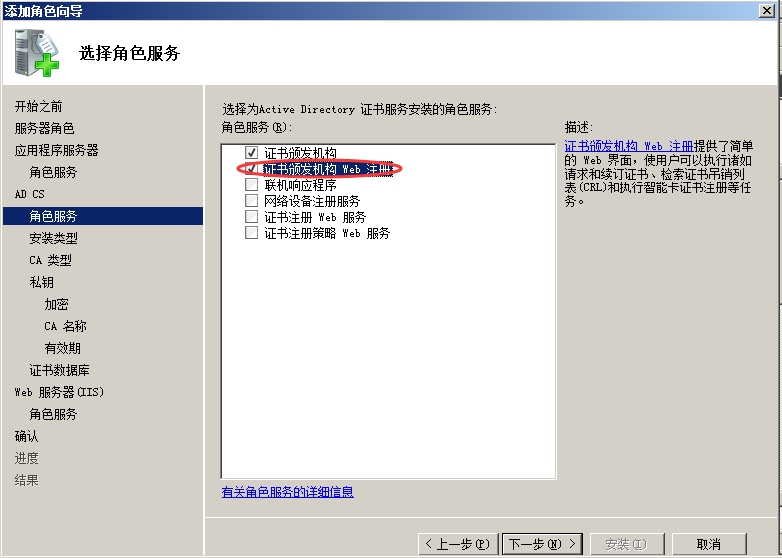
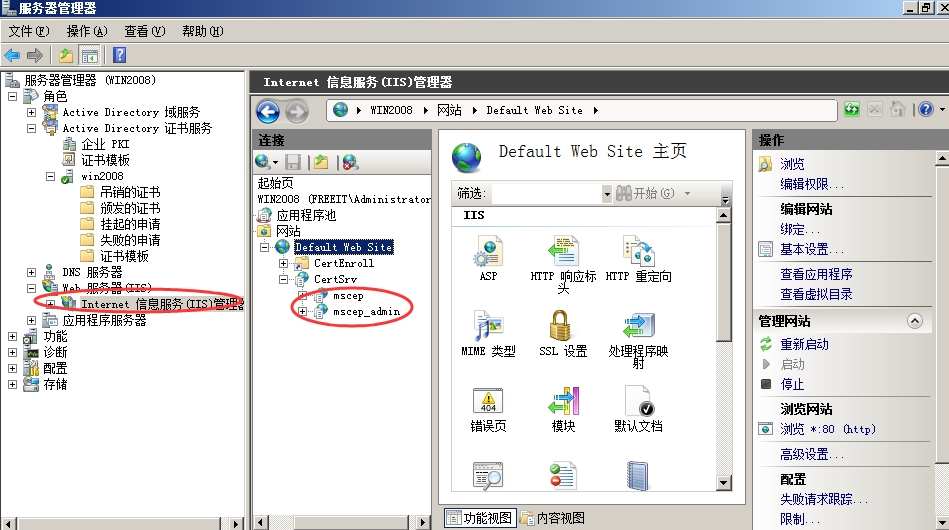
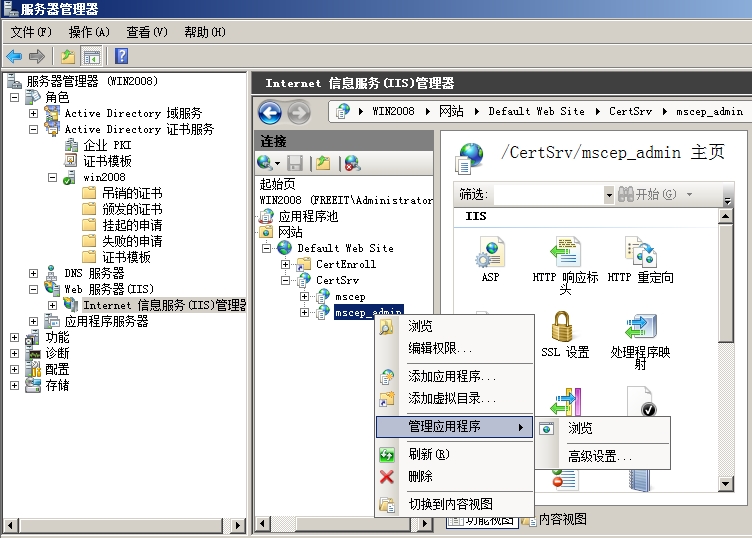
安装完成之后可以查看IIS管理器,能够找到Mscep
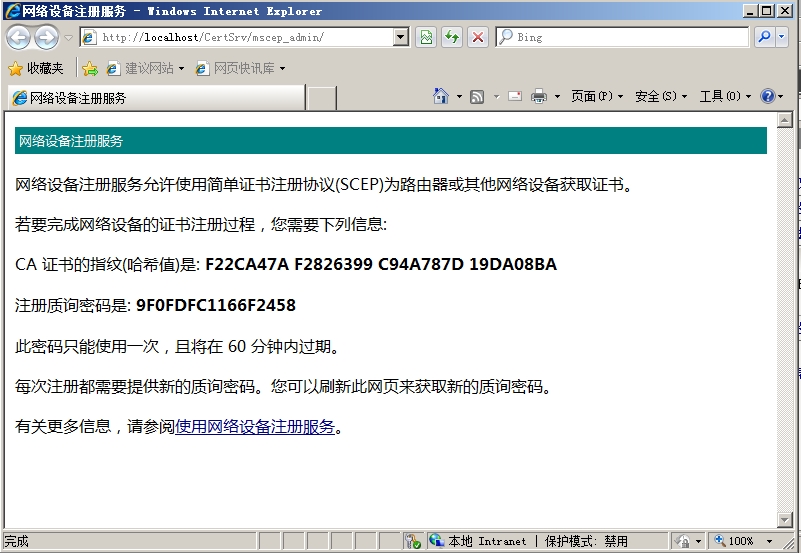
点击右键可以浏览测试
访问成功。不要关闭本页,路由申请证书时要用到注册质询密码。
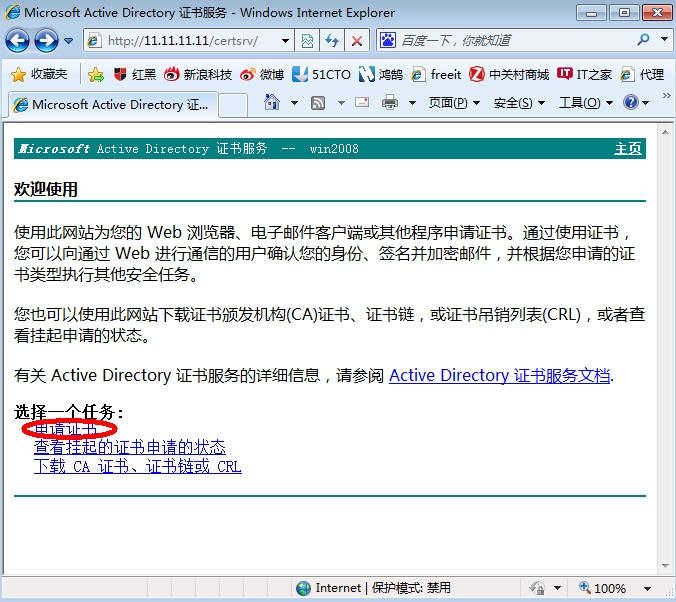
4.证书申请
每台路由器要申请两个证书,一个是CA根证书,用于验证CA颁发机构是否合法,是否可信任,更重要的是对CA颁发下来的IPSec证书解密(CA用自己的私钥把证书加密了)。另一个是自己使用的IPSec证书,用于×××数据加密。
4.1.Site1申请证书
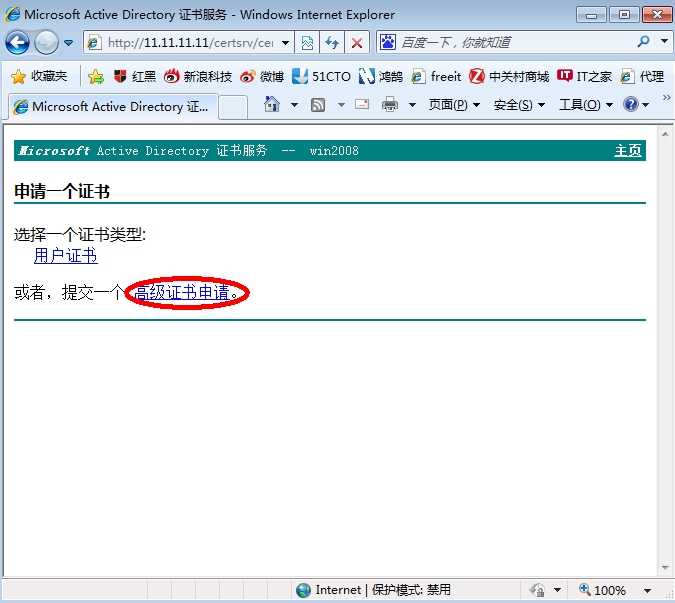
首先申请根证书,然后在申请个人的IPSec证书(要提交个人信息)。这里介绍两种申请证书的方式,在线申请(R1)和离线申请(R2)。
申请证书之前要先生成一对密钥
Site1(config)#crypto key generate rsa modulus 1024 The name for the keys will be: Site1.lab.local
% The key modulus size is 1024 bits % Generating 1024 bit RSA keys, keys will be non-exportable...[OK] |
申请根证书
Site1(config)#crypto pki trustpoint CA //设置信任点,取名CA。 Site1(ca-trustpoint)#subject-name cn=r1.freeit.com, ou=WL, o=yinhe, c=cn, e=freeitgyh@qq.com //向CA提交个人申请信息,包含地区、邮箱、申请名及组织、部门 Site1(ca-trustpoint)# enrollment url http://11.11.11.11/certsrv/mscep/mscep.dll //设置申请的地址
Site1(config)#crypto pki authenticate CA Certificate has the following attributes: Fingerprint MD5: F22CA47A F2826399 C94A787D 19DA08BA Fingerprint SHA1: A5BE009C 6041EC72 45B6A448 38C9DB21 A81271AF
% Do you accept this certificate? [yes/no]: yes //问是否接受证书,当然是了。 Trustpoint CA certificate accepted. //根证书申请成功。 |
根证书申请成功之后,会自动产生一条命令,如下:
crypto pki trustpoint CA enrollment mode ra enrollment url http://11.11.11.11:80/certsrv/mscep/mscep.dll subject-name cn=r1.freeit.com, ou=WL, o=yinhe, c=cn, e=freeitgyh@qq.com revocation-check crl |
revocation-checkcrl这条命令的意思就是检查CA证书吊销列表。
检查吊销列表,是为了检查CA颁发的证书是否有效,如果证书已经被吊销了,客户端还不知道,那后果就可想而知,对等体之间的验证是不会成功的。
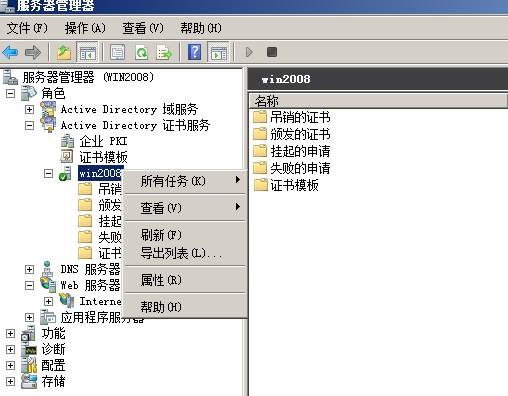
为配合客户端对证书吊销列表的检查,CA服务器也要进行相关设置
打开【服务器管理器】---角色---AD证书服务---win2008—右键属性
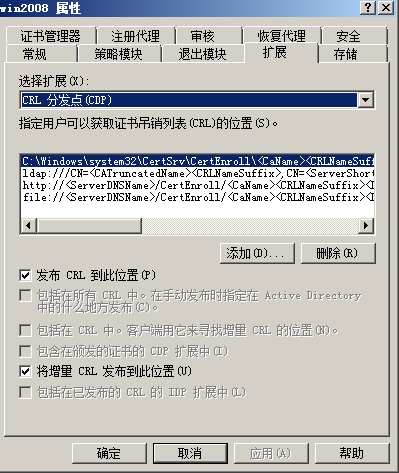
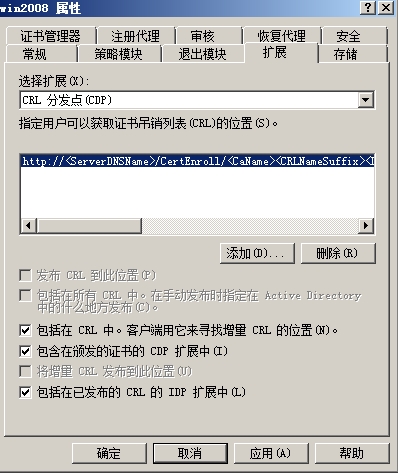
找到扩展选项卡
申请IPSec证书
在线申请(要用到注册质询密码)
Site1(config)#crypto pki en CA //申请自己的 Ipsec证书 % % Start certificate enrollment .. % Create a challenge password. You will need to verbally provide this password to the CA Administrator in order to revoke your certificate. For security reasons your password will not be saved in the configuration. Please make a note of it.
Password: //输入注册质询密码,输入时不显示,最好复制粘贴防止出错 Re-enter password: //再次输入
% The subject name in the certificate will include: cn=r1.freeit.com, ou=WL, o=yinhe, c=cn, e=freeitgyh@qq.com % The subject name in the certificate will include: Site1.lab.local % Include the router serial number in the subject name? [yes/no]: n //询问是否要序列号,n-不要 % Include an IP address in the subject name? [no]: n //询问是否要IP地址,n-不要 Request certificate from CA? [yes/no]: yes //询问是否接受证书,yes-接受。 % Certificate request sent to Certificate Authority % The 'show crypto pki certificate CA verbose' commandwill show the fingerprint.
Site1(config)# *Oct 16 11:21:47.551: CRYPTO_PKI: Certificate Request Fingerprint MD5: E826AE2F 0E4CF5B6 B7953425 3672F901 *Oct 16 11:21:47.551: CRYPTO_PKI: Certificate Request Fingerprint SHA1: 5C813687 7248D382 8C9D8B49 DC88D470 D47961C0 Site1(config)# *Oct 16 11:21:50.687: %PKI-6-CERTRET: Certificate received from Certificate Authority //接收证书成功 |
注:申请IPSec证书时,CA可能会拒绝,应该是win2008系统的不稳定造成的。此时有两种方法解决,1、卸载网络设备注册服务,重新安装(此方法可能会成功);2、离线申请证书(将在R2申请时介绍)。
到此,两个证书都申请成功了。
查看证书
Site1#show crypto pki certificates Certificate Status: Available Certificate Serial Number (hex): 6152866F000000000006 Certificate Usage: General Purpose Issuer: cn=win2008 dc=freeit dc=com Subject: Name: Site1.lab.local e=freeitgyh@qq.com cn=r1.freeit.com ou=WL o=yinhe c=cn hostname=Site1.lab.local CRL Distribution Points: ldap:///CN=win2008,CN=win2008,CN=CDP,CN=Public%20Key%20Services,CN=Services,CN=Configuration,DC=freeit,DC=com?certificateRevocationList?base?objectClass=cRLDistributionPoint Validity Date: start date: 11:11:50 GTM Oct 16 2014 end date: 11:11:50 GTM Oct 15 2016 Associated Trustpoints: CA //以上是设备自己的IPSec证书
CA Certificate Status: Available Certificate Serial Number (hex): 143E86D7130AF5814B9EF80E39A67AD9 Certificate Usage: Signature Issuer: cn=win2008 dc=freeit dc=com Subject: cn=win2008 dc=freeit dc=com Validity Date: start date: 21:13:49 GTM Oct 15 2014 end date: 21:23:48 GTM Oct 15 2019 Associated Trustpoints: CA //以上是CA的根证书。 |
也可以show配置查看(只截取证书部分内容)
crypto pki certificate chain CA certificate 6152866F000000000006 308204CC 308203B4 A0030201 02020A61 52866F00 00000000 06300D06 092A8648 86F70D01 01050500 303F3113 3011060A 09922689 93F22C64 01191603 636F6D31 16301406 0A099226 8993F22C 64011916 06667265 65697431 10300E06 03550403 13077769 6E323030 38301E17 0D313431 30313630 33313135 305A170D 31363130 31353033 31313530 5A308183 311E301C 06092A86 4886F70D 01090213 0F536974 65312E6C 61622E6C 6F63616C 310B3009 06035504 06130263 6E310E30 0C060355 040A1305 79696E68 65310B30 09060355 040B1302 574C3116 30140603 55040313 0D72312E 66726565 69742E63 6F6D311F 301D0609 2A864886 F70D0109 01161066 72656569 74677968 4071712E 636F6D30 5C300D06 092A8648 86F70D01 01010500 034B0030 48024100 DC1D650F F8AA84C4 0E04B90F 6C3AC5C1 3596F334 0019B8AC 5073428B 530473A0 DC269D37 CFDB1EAD 59966643 3B5D89CE C9EB4043 5BB1F631 8B82BDB9 E45B6605 02030100 01A38202 4B308202 47300E06 03551D0F 0101FF04 04030205 A0301D06 03551D0E 04160414 8D927F6B 39709FA5 B9630516 7FEFAA54 1A1C9AF4 301F0603 551D2304 18301680 14C0DB34 6723FE2E EFFE4E0C 501A9365 D1BF4E96 F13081C4 0603551D 1F0481BC 3081B930 81B6A081 B3A081B0 8681AD6C 6461703A 2F2F2F43 4E3D7769 6E323030 382C434E 3D77696E 32303038 2C434E3D 4344502C 434E3D50 75626C69 63253230 4B657925 32305365 72766963 65732C43 4E3D5365 72766963 65732C43 4E3D436F 6E666967 75726174 696F6E2C 44433D66 72656569 742C4443 3D636F6D 3F636572 74696669 63617465 5265766F 63617469 6F6E4C69 73743F62 6173653F 6F626A65 6374436C 6173733D 63524C44 69737472 69627574 696F6E50 6F696E74 3081B806 082B0601 05050701 010481AB 3081A830 81A50608 2B060105 05073002 8681986C 6461703A 2F2F2F43 4E3D7769 6E323030 382C434E 3D414941 2C434E3D 5075626C 69632532 304B6579 25323053 65727669 6365732C 434E3D53 65727669 6365732C 434E3D43 6F6E6669 67757261 74696F6E 2C44433D 66726565 69742C44 433D636F 6D3F6341 43657274 69666963 6174653F 62617365 3F6F626A 65637443 6C617373 3D636572 74696669 63617469 6F6E4175 74686F72 69747930 1D060355 1D110101 FF041330 11820F53 69746531 2E6C6162 2E6C6F63 616C303F 06092B06 01040182 37140204 321E3000 49005000 53004500 43004900 6E007400 65007200 6D006500 64006900 61007400 65004F00 66006600 6C006900 6E006530 13060355 1D25040C 300A0608 2B060105 05080202 300D0609 2A864886 F70D0101 05050003 82010100 0B11147A 870D47DF 822C2371 A93DE6FE 76C73C6A 377EC15D B61E9A02 B3E02BE8 34908DE8 1AB0A2F7 5D6601C5 A4694065 D20885FC 1765945B D9171BF7 0091A2D2 F1DB42B4 F3513563 C9D56406 360442F7 CF8D7196 CCBACCC9 2E1046FF 1A9771F1 C0AB2B19 59D67313 9A884279 1CDA6CD0 D7328BD2 66E5DAF8 3F576397 6C184147 090C0BF3 54D70CEC 0CF93665 C477A7CB 7411F8F6 CD8859F7 69A17830 D99E11E4 8C317175 84CB6B7F 82C635AB 7765A817 CB2606C8 DC146996 74313DF4 90F351D8 DBBC2A66 D782DE70 0897A29F 7AB4D947 742D4C18 D784E2F0 465D8EA7 01E480FE CA1718A3 0A417610 FCCC5920 02579774 39B59B1C 4B653C5C 6173845A 7F8A2694 Quit //以上是根证书 certificate ca 143E86D7130AF5814B9EF80E39A67AD9 30820359 30820241 A0030201 02021014 3E86D713 0AF5814B 9EF80E39 A67AD930 0D06092A 864886F7 0D010105 0500303F 31133011 060A0992 268993F2 2C640119 1603636F 6D311630 14060A09 92268993 F22C6401 19160666 72656569 74311030 0E060355 04031307 77696E32 30303830 1E170D31 34313031 35313331 3334395A 170D3139 31303135 31333233 34385A30 3F311330 11060A09 92268993 F22C6401 19160363 6F6D3116 3014060A 09922689 93F22C64 01191606 66726565 69743110 300E0603 55040313 0777696E 32303038 30820122 300D0609 2A864886 F70D0101 01050003 82010F00 3082010A 02820101 009FB225 3E7AD5B6 7AC30EEC 1B91A6A9 3C068A3E 25895FFD 0684526C DB3213E4 F4198C07 D35CC030 71BDE0D9 0212A127 79E93B14 E2EECA57 862FC201 B968E148 4F190D1D 6644CD0E B1CF97A3 AC8EC9B7 D454E549 151287C6 CA4ECA71 7C261BC7 ADBF380A 6C94B7EE B3D39B59 36AE0D37 3340BC11 18A19385 2CB6266D 42DF0940 DD05E5DB 08C45D55 8D4C8883 435381B1 C0DED349 26199D07 E62DCE02 8422E10F 5F0CBCAD E7B54410 29C47C7C BB5E04AE 25C767BE F9160D7E 204BB825 683B92D6 D889762E 5E0B7ADE DBE63A70 183D61A9 F6A542F0 5E3DCB40 3DC621FC EEA0C3F5 E7EC251C 12A65C50 B833D893 45863C1A 29E00C76 EEC9AEE1 5EA77F32 6B018216 1B020301 0001A351 304F300B 0603551D 0F040403 02018630 0F060355 1D130101 FF040530 030101FF 301D0603 551D0E04 160414C0 DB346723 FE2EEFFE 4E0C501A 9365D1BF 4E96F130 1006092B 06010401 82371501 04030201 00300D06 092A8648 86F70D01 01050500 03820101 0003AE27 9ABDEEAC 5FE00BEE 82A09B7E 4B55A032 64BAD9BD 84C06A51 FBCA545A 57A28CED B1C5427D 9D8D2BC6 6C338EB2 FE9B2334 CBB352A7 A2F77937 221A0BC3 FAEE92A0 361F4F7E 420378D8 D37D768C B096438E 53F7306B BAC453FC 8297F17C 3E092E7C 4C0C0921 6F08B3B7 964C4161 96711834 2131AC65 9DAB0C18 D5E9AA76 C0F6E1F1 874A86C8 DDA5E47C 0D367BD7 F78BE1FD 60D01A88 5E74E9BD 811A28D8 F2C42587 B7FA3603 EA3635D6 B074A0CD C4578495 F60D8EE3 22D1B433 3B1666C0 680E39DB 53723E2F 4DEF1E9A 4F6DFE6A 35958F7D BD6CA15A 00B5CE05 B7CC2800 D57A4E4C 7F416379 E71C14FD C9DE8A36 F9F44609 C5F1AED1 E7E9D28D 395C0A29 53 Quit //以上是IPSec证书内容 |
4.2.Site2证书申请
产生密钥对
Site2(config)#crypto key gen rsa mod 1024 The name for the keys will be: Site2.lab.local
% The key modulus size is 1024 bits % Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
Site2(config)# *Oct 16 11:33:56.163: %SSH-5-ENABLED: SSH 1.99 has been enabled |
设置信任点
Site2(config)#crypto pki trustpoint CA Site2(ca-trustpoint)#subject-name cn=r2.freeit.com, ou=XT, o=baidu, c=cn Site2(ca-trustpoint)#enrollment terminal //在终端申请 Site2(ca-trustpoint)#exit |
根证书申请
Site2(config)#crypto pki authenticate CA
Enter the base 64 encoded CA certificate. End with a blank line or the word "quit" on a line by itself
//要求输入根证书的base64码。 |
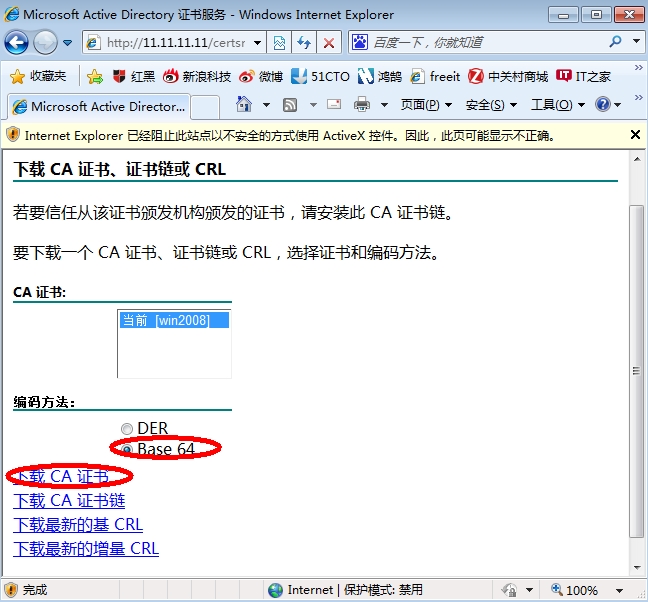
下面我们web连接CA,申请证书
下载后用记事本打开,复制所有内容并粘贴到路由申请界面,如下:
Site2(config)#crypto pki authenticate CA
Enter the base 64 encoded CA certificate. End with a blank line or the word "quit" on a line by itself
-----BEGIN CERTIFICATE----- MIIDWTCCAkGgAwIBAgIQFD6G1xMK9YFLnvgOOaZ62TANBgkqhkiG9w0BAQUFADA/ MRMwEQYKCZImiZPyLGQBGRYDY29tMRYwFAYKCZImiZPyLGQBGRYGZnJlZWl0MRAw DgYDVQQDEwd3aW4yMDA4MB4XDTE0MTAxNTEzMTM0OVoXDTE5MTAxNTEzMjM0OFow PzETMBEGCgmSJomT8ixkARkWA2NvbTEWMBQGCgmSJomT8ixkARkWBmZyZWVpdDEQ MA4GA1UEAxMHd2luMjAwODCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB AJ+yJT561bZ6ww7sG5GmqTwGij4liV/9BoRSbNsyE+T0GYwH01zAMHG94NkCEqEn eek7FOLuyleGL8IBuWjhSE8ZDR1mRM0Osc+Xo6yOybfUVOVJFRKHxspOynF8JhvH rb84CmyUt+6z05tZNq4NNzNAvBEYoZOFLLYmbULfCUDdBeXbCMRdVY1MiINDU4Gx wN7TSSYZnQfmLc4ChCLhD18MvK3ntUQQKcR8fLteBK4lx2e++RYNfiBLuCVoO5LW 2Il2Ll4Let7b5jpwGD1hqfalQvBePctAPcYh/O6gw/Xn7CUcEqZcULgz2JNFhjwa KeAMdu7JruFep38yawGCFhsCAwEAAaNRME8wCwYDVR0PBAQDAgGGMA8GA1UdEwEB /wQFMAMBAf8wHQYDVR0OBBYEFMDbNGcj/i7v/k4MUBqTZdG/TpbxMBAGCSsGAQQB gjcVAQQDAgEAMA0GCSqGSIb3DQEBBQUAA4IBAQADrieave6sX+AL7oKgm35LVaAy ZLrZvYTAalH7ylRaV6KM7bHFQn2djSvGbDOOsv6bIzTLs1Knovd5NyIaC8P67pKg Nh9PfkIDeNjTfXaMsJZDjlP3MGu6xFP8gpfxfD4JLnxMDAkhbwizt5ZMQWGWcRg0 ITGsZZ2rDBjV6ap2wPbh8YdKhsjdpeR8DTZ71/eL4f1g0BqIXnTpvYEaKNjyxCWH t/o2A+o2NdawdKDNxFeElfYNjuMi0bQzOxZmwGgOOdtTcj4vTe8emk9t/mo1lY99 vWyhWgC1zgW3zCgA1XpOTH9BY3nnHBT9yd6KNvn0RgnF8a7R5+nSjTlcCilT -----END CERTIFICATE----- quit Certificate has the following attributes: Fingerprint MD5: F22CA47A F2826399 C94A787D 19DA08BA Fingerprint SHA1: A5BE009C 6041EC72 45B6A448 38C9DB21 A81271AF
% Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted. % Certificate successfully imported //根证书成功导入 |
申请IPSec证书
Site2(config)#crypto pki enroll CA //申请证书 % Start certificate enrollment ..
% The subject name in the certificate will include: cn=r2.freeit.com, ou=XT, o=baidu, c=cn % The subject name in the certificate will include: Site2.lab.local % Include the router serial number in the subject name? [yes/no]: n % Include an IP address in the subject name? [no]: n Display Certificate Request to terminal? [yes/no]: y //显示证书申请请求 Certificate Request follows:
MIIBwzCCASwCAQAwYjELMAkGA1UEBhMCY24xDjAMBgNVBAoTBWJhaWR1MQswCQYD VQQLEwJYVDEWMBQGA1UEAxMNcjIuZnJlZWl0LmNvbTEeMBwGCSqGSIb3DQEJAhYP U2l0ZTIubGFiLmxvY2FsMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDNoZkl +mcVVIDcj2W1mg6YFOdaUrre6bPZA2wSn+fAwCvzL69sICZAbaPQzh4tPFMsYXWb VszQQdLeaFMxtbOTWqqc305aOQnFy/A3SxaXrIgL8bi4NXzdT2U7KSXGFfs7aBFB gV3YweRYPlBNRxYfFJUN7Qyw/HGXlHA1bb/OuwIDAQABoCEwHwYJKoZIhvcNAQkO MRIwEDAOBgNVHQ8BAf8EBAMCBaAwDQYJKoZIhvcNAQEEBQADgYEAVRIrN8XXNdB9 DXdTSxCdDXUPc5yud/dny8zrU9GwaoWcgTwDT/wKbVEyzRGaq0D4kOY+meJ7Cvp7 foGWDKbGtYr+Zuxq+4padrPScjtUkPYcwf2HG8YImWk2ZybGNocNsGiU/hhF8/Mw n/h1cxgPFKf1pZfN9vRKVkwUtH79VUs=
---End - This line not part of the certificate request---
Redisplay enrollment request? [yes/no]: |
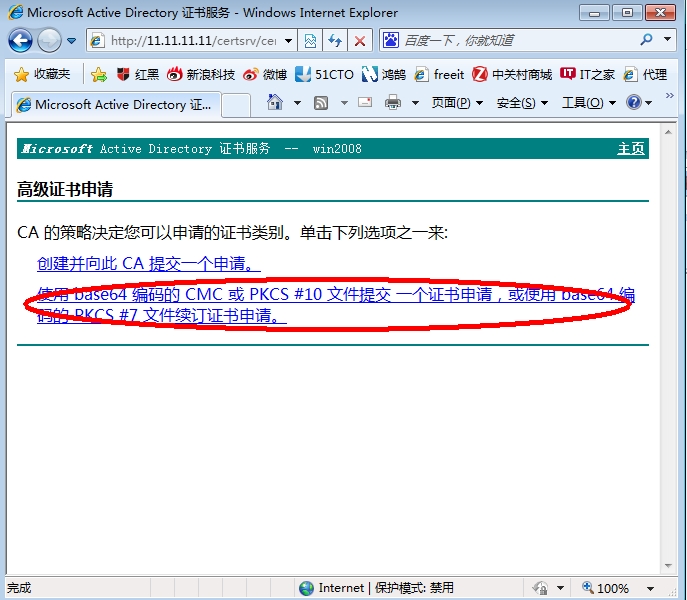
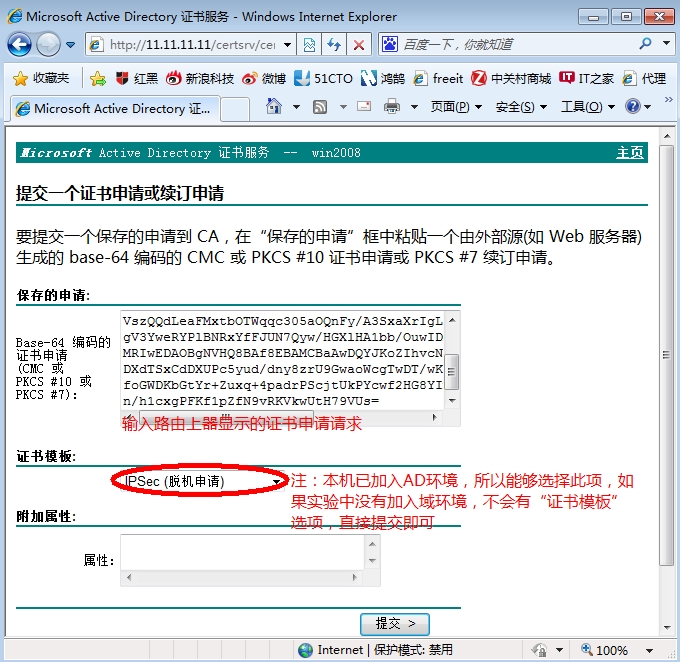
把上图的证书申请请求(加粗字体)复制,然后web连接到CA申请证书
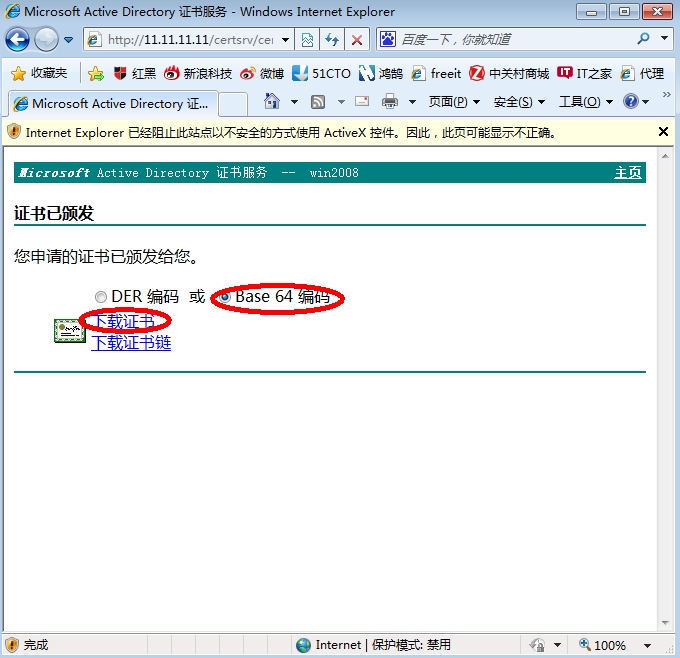
下载,用记事本打开,复制内容,粘贴到路由器命令行。
接下来导入证书
Site2(config)#crypto pki import CA certificate //导入证书 Enter the base 64 encoded certificate. End with a blank line or the word "quit" on a line by itself //在下面粘贴上去证书的base 64码,输入quit完成导入 -----BEGIN CERTIFICATE----- MIIESzCCAzOgAwIBAgIKYZj1hwAAAAAABzANBgkqhkiG9w0BAQUFADA/MRMwEQYK CZImiZPyLGQBGRYDY29tMRYwFAYKCZImiZPyLGQBGRYGZnJlZWl0MRAwDgYDVQQD Ewd3aW4yMDA4MB4XDTE0MTAxNjA0Mjg0NloXDTE2MTAxNTA0Mjg0NlowYjEeMBwG CSqGSIb3DQEJAhMPU2l0ZTIubGFiLmxvY2FsMQswCQYDVQQGEwJjbjEOMAwGA1UE ChMFYmFpZHUxCzAJBgNVBAsTAlhUMRYwFAYDVQQDEw1yMi5mcmVlaXQuY29tMIGf MA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDNoZkl+mcVVIDcj2W1mg6YFOdaUrre 6bPZA2wSn+fAwCvzL69sICZAbaPQzh4tPFMsYXWbVszQQdLeaFMxtbOTWqqc305a OQnFy/A3SxaXrIgL8bi4NXzdT2U7KSXGFfs7aBFBgV3YweRYPlBNRxYfFJUN7Qyw /HGXlHA1bb/OuwIDAQABo4IBqDCCAaQwDgYDVR0PAQH/BAQDAgWgMB0GA1UdDgQW BBTaB+E1OVJA+kQCyn8Xy3YWOKWcazAfBgNVHSMEGDAWgBTA2zRnI/4u7/5ODFAa k2XRv06W8TBBBgNVHR8EOjA4MDagNKAyhjBodHRwOi8vd2luMjAwOC5mcmVlaXQu Y29tL0NlcnRFbnJvbGwvd2luMjAwOC5jcmwwgbgGCCsGAQUFBwEBBIGrMIGoMIGl BggrBgEFBQcwAoaBmGxkYXA6Ly8vQ049d2luMjAwOCxDTj1BSUEsQ049UHVibGlj JTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixE Qz1mcmVlaXQsREM9Y29tP2NBQ2VydGlmaWNhdGU/YmFzZT9vYmplY3RDbGFzcz1j ZXJ0aWZpY2F0aW9uQXV0aG9yaXR5MD8GCSsGAQQBgjcUAgQyHjAASQBQAFMARQBD AEkAbgB0AGUAcgBtAGUAZABpAGEAdABlAE8AZgBmAGwAaQBuAGUwEwYDVR0lBAww CgYIKwYBBQUIAgIwDQYJKoZIhvcNAQEFBQADggEBAGr+yv+JANme2p6tfpGXxx8b z0PXbEGvhoix5IQt7pBU/hpzl1vqULGCBl3BvhzDaKR8q9vkYErfXe7d+0mpPNC0 Ybic3TveCbpnj9NIZlzNnOmU70uUFsQGZh49MPGeMkcp1o8bzQbks/h9mhmcD6SO ZlW5qQnI0A/w/Km0nqvgDrqK9ocI0X6lZMttZfcvk62LrCnqvEtQTCFxsHbkPP/D b9wttQaw0PIHr7f+afvWhkQ7UKf8SHunwXxIUoTKfYN3HarqSe1fu6kUxrl0tmMz tmXqClB6pDJq8QDXCX6wr+fwvJx9FPcG56gRbBdmrY9pWYHIunGqTld9kYTOc5w= -----END CERTIFICATE----- quit % Router Certificate successfully imported //导入成功 |
两台设备证书申请都已经OK!下面我们就开始IPSec ×××配置
5.IPSec ×××配置
证书的申请只是准备工作,但是也是最重要的,也是实验中的难点。申请完证书,可以开始IPSec ×××配置
Site1配置
第一阶段配置: Site1(config)#crypto isakmp policy 1 Site1(config-isakmp)#authentication rsa-sig //采用rsa签名(即PKI)认证方式 Site1(config-isakmp)#encryption 3des Site1(config-isakmp)#group 2 Site1(config-isakmp)#hash md5 Site1(config-isakmp)#exit
第二阶段配置: Site1(config)#crypto ipsec transform-set l2l-ipsec esp-3des esp-sha-hmac Site1(cfg-crypto-trans)#exit Site1(config)#ip access-list extended ××× Site1(config-ext-nacl)#permit ip 192.168.1.0 0.0.0.255 172.16.1.0 0.0.0.255 Site1(config-ext-nacl)#exit //配置感兴趣流量 Site1(config)#crypto map l2l 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. Site1(config-crypto-map)#set peer 61.100.1.1 Site1(config-crypto-map)#set transform-set l2l-ipsec Site1(config-crypto-map)#match address ××× Site1(config-crypto-map)#exit Site1(config)#inter fa0/0 Site1(config-if)#crypto map l2l Site1(config-if)#exit //接口调用crypto map *Oct 16 12:52:10.231: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON |
Site2配置
Site2(config)#crypto isakmp policy 1 Site2(config-isakmp)# encr 3des Site2(config-isakmp)# hash md5 Site2(config-isakmp)# group 2 Site2(config-isakmp)#auth rsa-sig Site2(config-isakmp)#exit Site2(config)#ip access-list extended ××× Site2(config-ext-nacl)#permit ip 172.16.1.0 0.0.0.255 192.168.1.0 0.0.0.255 Site2(config-ext-nacl)#exit Site2(config)#crypto map l2l 10 ipsec-isakmp % NOTE: This new crypto map will remain disabled until a peer and a valid access list have been configured. Site2(config-crypto-map)#set peer 202.100.1.1 Site2(config-crypto-map)#set transform-set l2l-ipsec Site2(config-crypto-map)# match address ××× Site2(config-crypto-map)#exit Site2(config)#inter fa0/0 Site2(config-if)#cry map l2l Site2(config-if)#exit Site2(config)# *Oct 16 12:59:02.243: %CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON |
IPSec ×××配置完成。
尽管配置完成,现在还是不能通信。因为site之间要检查证书吊销列表(由于自动生成了revocation-check crl命令),但是在site路由器上没有证书吊销列表,所以检查不了,也就不能成功通信,如下:
Site1向site2发出ICMP包
Site1#ping 172.16.1.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 ..... Success rate is 0 percent (0/5)
Site2的回应: Site2# *Oct 16 13:02:59.119: %CRYPTO-3-IKMP_QUERY_KEY: Querying key pair failed. Site2# Site2# *Oct 16 13:03:00.799: %CRYPTO-3-IKMP_QUERY_KEY: Querying key pair failed. Site2# *Oct 16 13:03:02.531: %CRYPTO-3-IKMP_QUERY_KEY: Querying key pair failed. Site2# *Oct 16 13:03:04.187: %CRYPTO-3-IKMP_QUERY_KEY: Querying key pair failed. Site2# *Oct 16 13:03:05.851: %CRYPTO-3-IKMP_QUERY_KEY: Querying key pair failed. |
解决办法由两种:1.设置DNS,通过DNS查寻到CA的证书吊销列表(事先要设置好DNS server,做好映射);2.关闭对证书吊销列表的查询。
方法一:指向DNS
由于本实验中DNS就设置在CA上,所以,我们只需把site的DNS指向CA即可,然后向DNS请求证书吊销列表
Site1(config)#ip domain lookup //开启域名解析 Site1(config)#ip name-server 11.11.11.11 //设置DNS服务器 Site1(config)#crypto pki crl request CA //向CA请求吊销证书列表 Site1(config)# Translating "win2008.freeit.com"...domain server (11.11.11.11) [OK] //成功接收
查看: Site2(config)#do sho cry pki crl CRL Issuer Name: cn=win2008,dc=freeit,dc=com LastUpdate: 13:14:11 UTC Oct 15 2014 NextUpdate: 01:34:11 UTC Oct 23 2014 Retrieved from CRL Distribution Point: CRL DER is 896 bytes CRL is stored in parsed CRL cache
Parsed CRL cache current size is 896 bytes Parsed CRL cache maximum size is 65536 bytes |
Site2上同样的配置。
方法二:关闭证书吊销列表查询
Site1(config)#crypto pki trustpoint CA Site1(ca-trustpoint)#revocation-check none Site1(ca-trustpoint)#exit
Site2(config)#crypto pki trustpoint CA Site2(ca-trustpoint)#revocation-check none Site2(ca-trustpoint)#exit |
验证:
Site1向site2发出ICMP包
Site1#ping 172.16.1.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.1.1, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 84/102/128 ms |
Site2向site1发出ICMP包
Site2#ping 192.168.1.1 source loo0
Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds: Packet sent with a source address of 172.16.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 44/94/132 ms Site2# |
查看两个SA
Site1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id slot status 61.100.1.1 202.100.1.1 QM_IDLE 1005 0 ACTIVE
IPv6 Crypto ISAKMP SA
Site1#show crypto ipsec sa
interface: FastEthernet0/0 Crypto map tag: l2l, local addr 202.100.1.1
protected vrf: (none) local ident (addr/mask/prot/port): (192.168.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (172.16.1.0/255.255.255.0/0/0) current_peer 61.100.1.1 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9 #pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9 #pkts compressed: 0, #pkts decompressed: 0 #pkts not compressed: 0, #pkts compr. failed: 0 #pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 11, #recv errors 0 //匹配了9个包,就是site1与site2互ping的9个包。
local crypto endpt.: 202.100.1.1, remote crypto endpt.: 61.100.1.1 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0 current outbound spi: 0xA1822E7E(2709663358)
inbound esp sas: spi: 0x159D885A(362645594) transform: esp-3des esp-sha-hmac , in use settings ={Tunnel, } conn id: 1, flow_id: SW:1, crypto map: l2l sa timing: remaining key lifetime (k/sec): (4567062/3513) IV size: 8 bytes replay detection support: Y Status: ACTIVE //状态为激活
inbound ah sas:
inbound pcp sas:
outbound esp sas: spi: 0xA1822E7E(2709663358) transform: esp-3des esp-sha-hmac , in use settings ={Tunnel, } conn id: 2, flow_id: SW:2, crypto map: l2l sa timing: remaining key lifetime (k/sec): (4567062/3513) IV size: 8 bytes replay detection support: Y Status: ACTIVE
outbound ah sas:
outbound pcp sas: |
五.实验总结
基于PKI的IPSec ×××是比PSK更加安全的对等体身份验证方式;
要理清非对称加密的概念:私钥加密公钥解密属于数字签名,公钥加密私钥解密属于非对称加密算法;
证书申请时,要保证客户端与CA服务器的时区一致,时间一致;
转载于:https://blog.51cto.com/380531251/1579225





















 204
204











 被折叠的 条评论
为什么被折叠?
被折叠的 条评论
为什么被折叠?








